Malta Identity Card Reader Device Windows Installation and User Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Instalación Y Administración De Servicios De Correo Electrónico
Servicios de red e internet Instalación y administración de servicios de correo electrónico Raquel Castellanos Crespo Instalación y administración de servicios de correo electrónico Servicios de red e internet Raquel Castellanos Crespo INDICE Características del servicio de correo electrónico Elementos del servicio de correo electrónico -Agentes de correo electrónico. - Servidores de correo electrónico. Open relay y Smart host - Clientes de correo electrónico: entorno-DOS, gráficos y navegadores. - Direcciones, cuentas de correo y servidores DNS - Protocolos y servicios de descarga de correo: SMPT, ESMTP, POP, IMAP. Funcionamiento del servicio de correo electrónico Cuentas de correo, alias y buzones de correo Estructura de mensajes de correo electrónico - Cabecera, cuerpo, MIME Monitorización y registros del servicio de correo electrónico Servicio de correo electrónico vía web Correo seguro - Firma digital y cifrado de mensajes Veracidad del correo - Correo basura ("SPAM”) fraude, engaño, cadenas y virus informáticos 2 Servicios de red e internet | Instalación y administración de servicios de correo electrónico Servicios de red e internet Raquel Castellanos Crespo Características del servicio de correo electrónico Correo electrónico (correo-e, conocido también como e-mail ), es un servicio de red que permite a los usuarios enviar y recibir mensajes y archivos rápidamente (también denominados mensajes electrónicos o cartas electrónicas) mediante sistemas de comunicación electrónicos. Principalmente se usa este nombre para denominar al sistema que provee este servicio en Internet, mediante el protocolo SMTP, aunque por extensión también puede verse aplicado a sistemas análogos que usen otras tecnologías. Por medio de mensajes de correo electrónico se puede enviar, no solamente texto, sino todo tipo de documentos digitales. -

Suositus Verkkopalvelun Kävijöiden, Sivupyyntöjen Ja Vierailujen Mittaamiseksi
TIETOTEKNIIKKA Suositus verkkopalvelun kävijöiden, sivupyyntöjen ja vierailujen mittaamiseksi Dokumentin tila: ehdotus suositukseksi 9.9.1999 Tekijät • Hannele Antikainen • Vesa Kautto • Markku Kylänpää • Heikki Nikulin Alkusanat Nämä suositukset on laadittu Suomen Mediatarkastuksen vetämässä hankkeessa, jossa VTT Tietotekniikka on toiminut asiantuntijaorganisaationa. Projektiin osallistuivat: • Alma Media Oyj • Sanoma-WSOY • Grey Interactive Oy • Saunalahden Serveri • Mainostajien Liitto • Sonera • Mainostoimistojen Liitto • Suomen Gallup Web Oy • Nedecon Network Development • Taloustutkimus Oy Consulting Oyj • Telia Finland Oy/Netpool Finland Oy Hankkeessa laadittiin suositus, joiden mukaan verkkopalvelujen mittaamisen keskeiset tunnusluvut voidaan laskea. Suositus on parhaillaan (syksy 1999) Suomen Mediatarkastuksen käsiteltävänä. Verkko- palvelujen mittaamisen keskeiset tunnusluvut ovat kävijä, sivupyyntö ja vierailu. Näiden suositusten toivotaan yhtenäistävän termistöä, jota verkkopalvelujen mittaamisessa käytetään. Ne toimivat myös lähtökohtana verkkopalvelujen mittausjärjestelmien kehittämisessä. Tavoitteena on, että mainostajille voitaisiin esittää eri verkkopalveluista samoilla mittausperiaatteilla saatuja tunnuslukuja. Tämä on yksi verkkomainontakampanjoiden suunnittelun perusedellytyksistä. Sisällys 1. JOHDANTO 2 2. KÄSITTEET 2 2.1 KÄVIJÄ 2 2.2 SIVUPYYNTÖ 3 2.3 VIERAILU 6 2.4 MUUT KÄSITTEET 6 LÄHTEET 7 SANASTO 7 LIITE 1. MITTAUSJÄRJESTELMÄT LIITE 2. LUETTELO HAKUKONEISTA JA HENKILÖKOHTAISISTA ROBOTEISTA 1. Johdanto Verkkopalvelun -

Scinterface 12/2019
Technical Data Sheet SCinterface 12/2019 Powerful and secure Smart Credential Middleware SCinterface connects a smart card or token to virtually any PKI-enabled application. It is a user-friendly and convenient universal middleware supporting dozens of smart cards, virtual smart cards, security tokens in different form factors and all major desktop operating systems. • Higher security level with smart cards or tokens • Convenient lifecycle management for PINs, keys and certificates • PIN management includes: • PIN change • unlocking User-PINs • offline PIN reset • PIN cache mode • PACE-PIN and -PUK • Session-PIN according to Minidriver Spec. version 7.06 • Key & certificate management: • Generation of key pairs and secret keys, secure storage of secret keys Functions • Import of keys and certificates (PKCS#12) • Generation of certificate requests (PKCS#10) • Registration of certificates in Microsoft Windows Certificate Store • Certificate update for Windows 2008 / 2012 / 2016 • Initialization & rollout functions: • Generation of smart card profiles (PKCS#15, PKCS#15 with PACE, PKCS#15 biometric profile, third party profiles) • Biometric Match-on-Card for Java Card with Neurotechnology™, Precise BioMatch™ Flex* • Other token management functions: • Configuration of default smart card container for MS-CAPI • Creation, storage and administration of data on smart card • Support of multiple keys per card with separate PINs * Legacy support only Technical Data Sheet - SCinterface • Support of numerous smart cards and profiles, a wide range of -

Kurzbeschreibung Des
Einführung neuer Formulare mit qualifizierter elektronischer Signatur beim Bundessortenamt Technische Details (Stand: 21.10.2019) Betriebssysteme Für die Arbeit mit dem Produkt OpenLimit CC Sign 2.10 benötigen Sie einen 1-GHz- Prozessor oder höher, mindestens 260 MB freien Festplattenplatz und mindestens 1 GB frei verfügbaren RAM. Auf dem Rechner muss mindestens der Internet Explorer ab Version 11 installiert sein und darüber hinaus die Java Virtual Machine mit dem zugehörigen JRE (Java Runtime Environment). Wenn Sie nicht über die Java Virtual Machine verfügen, können Sie diese unter https://java.com/de/download/ herunterladen. Außerdem werden der Adobe Reader oder Adobe Acrobat ab Version 10 benötigt. Den kostenlosen Adobe Reader können Sie unter folgender Webadresse herunterladen: https://get.adobe.com/de/reader/ Die folgenden Betriebssysteme werden von diesem Produkt unterstützt (Client bzw. Terminalserver): - Windows 7 32 Bit und 64 Bit - Windows 8.1 32 Bit und 64 Bit - Windows 10 32 Bit und 64 Bit - Windows Server 2008 R2 Terminalserver - Windows Server 2012 R2 Terminalserver Signaturkarten und Kartenlesegeräte Bitte entnehmen Sie detaillierte Informationen zu unterstützten Signaturkarten und Karten- lesegeräten der Herstellererklärung der OpenLimit SignCubes Basiskomponenten Version 2.10 in der Version 1.0. externer Link: https://www.openlimit.com/assets/files/produkte/de/OpenLimit_Herstellererklaerung_CC- Sign-2-10.pdf Nachfolgend finden Sie eine kurze Übersicht der unterstützten Signaturkarten: Bundesnotarkammer - STARCOS 3.4 -

Sc/Interface Powerful and Secure Smart Credential Middleware Sc/Interface Connects the Smart Card Or Token to Virtually Any PKI Enabled Application
www.cryptovision.com sc/interface Powerful and Secure Smart Credential Middleware sc/interface connects the smart card or token to virtually any PKI enabled application. It is a sophisticated universal middleware with support for dozens of smart cards, virtual smart cards, security tokens of several different form factors, and all major desktop operating systems. Functions • Increasing the level of security with smart cards or tokens • Comfortable functionality for managing the lifecycle of PINs, keys and certificates • PIN management: • PIN change • unlocking User-PINs • offline PIN reset • PIN Cache Mode • PACE-PIN and -PUK • Session-PIN according to Minidriver Spec. version 7.06 • Key & certificate management: • Generation of key pairs and secret keys, secure storage of secret keys • Import of keys and certificates (PKCS#12) • Generation of certificate requests (PKCS#10) • Registration of certificates in Microsoft Windows Certificate Store • Certificate update for Windows 2008 / 2012 • Initialization & rollout functions: • Generation of smart card profiles (PKCS#15, PKCS#15 with PACE, PKCS#15 biometric profile, cv profile, third party profiles) • Biometric Match-on-Card for Java Card with Precise BioMatch™ Flex and Digital Persona™ • Other Token management functions: • Configuration of default smart card container for MS-CAPI • Creation, storage, and administration of data on smart card • PKCS#11 Virtual slots enable multiple keys per card with unique PINs used per key cryptovision – Technical Data Sheet 1 www.cryptovision.com Features -
The Mass Hypnotist
THE MASS HYPNOTIST "A RED DRUM CALLED KHAT: A FISTORY" "THE DOLDRUMS" "BOBBY MILK" (Three interlinking stories about a lonely and confused guy, his Ubiquitous Orb, a four-finger bag of Qat, pussy juice shooters, Muslims bikers, h-words, a bunch of Boole ... and a really, really big fish!) "He offered no apologies, no excuses or compromise, and had no regrets. It is what it is. Deal with it." - HE Written by Steven G. Rhodes (nom de plume: C. L. Burke) Copyright Reg. # TXu 2-016-423 Date: July 26, 2016 Steven G. Rhodes 1830 NW 1st Ave., Apt D_______________ NOVEL (TENTH DRAFT) Gainesville, FL 32603____________________December 10, 2016 Cell: 305-766-5734 magicJack: 941-227-5997 (leave messages) E-mail: [email protected] FADE IN: WRITTEN ON SCREEN: “Vanity ! There are no countries left. All I see from pole to pole are tyrants and slaves.” - HE PROLOGUE (O.S.) NARRATOR: If they could just sit him down -- you know, talk to him in glib, nebulous, polysyllabic terms -- they just knew he could be convinced. BOOLE: After all, he watches his phone. THE ORB: And, reads your every conjured word. Too many bombs. Too much linking of so-called social networks. That equals unbridled libel, slander and spying. BOOLE: Commercials synchronized to ensure captivity. Commercial volumes increased without consent to near deafening levels. Commercials, after tasered teasers, after propaganda, after commercials, after more propaganda, after more commercials. THE ORB: Television networks that repeat the same propaganda every hour in a different format. NARRATOR: ESPN ex-machina. BOOLE: It didn’t work for Euripides or Menander. -

MULTIWEB Banking Installation and Update in Windows
MULTIWEB Banking Installation and Update in Windows Manual Version: 1.0 Status: released 21/08/2018 MULTIWEB Banking Installation and Update in Windows Manual The greatest care has been taken in the writing of this manual. However, any formal or content-related mistakes cannot be excluded. Protected trademarks are not always identified as such in this documentation. Therefore, the absence of any identification of a product name as a trademark cannot be deemed to mean that this name is not a trademark or registered trademark. This document must be treated confidentially. All representations, copies or other reproductions which are not directed to the offeree can only take place with the agreement of CoCoNet. This applies also to the transmission of this document towards a third party. All rights of the document remain with CoCoNet. © 2018, CoCoNet Computer-Communication Networks GmbH CoCoNet Computer-Communication Networks GmbH Steinhof 5 D-40699 Erkrath Phone: +49 (0)2 11 / 2 49 02 - 0 Fax: +49 (0)2 11 / 2 49 02 - 200 Internet: http://www.coconet.de E-Mail: [email protected] CoCoNet GmbH Page 2 of 29 Contents 1 Introduction ........................................................................................................................................... 6 2 Preconditions ........................................................................................................................................ 6 3 New installation ................................................................................................................................... -
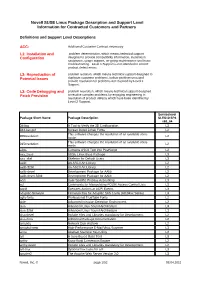
Novell SUSE Linux Package Description and Support Level Information for Contracted Customers and Partners
Novell SUSE Linux Package Description and Support Level Information for Contracted Customers and Partners Definitions and Support Level Descriptions ACC: Additional Customer Contract necessary L1: Installation and problem determination, which means technical support Configuration designed to provide compatibility information, installation assistance, usage support, on-going maintenance and basic troubleshooting. Level 1 Support is not intended to correct product defect errors. L2: Reproduction of problem isolation, which means technical support designed to Potential Issues duplicate customer problems, isolate problem area and provide resolution for problems not resolved by Level 1 Support. L3: Code Debugging and problem resolution, which means technical support designed Patch Provision to resolve complex problems by engaging engineering in resolution of product defects which have been identified by Level 2 Support. Servicelevel Package Short Name Package Description SLES10 SP4 x86_64 3ddiag A Tool to Verify the 3D Configuration L3 844-ksc-pcf Korean 8x4x4 Johab Fonts L2 This software changes the resolution of an available vbios 855resolution L2 mode. This software changes the resolution of an available vbios 915resolution L2 mode. a2ps Converts ASCII Text into PostScript L2 aaa_base SUSE Linux Base Package L3 aaa_skel Skeleton for Default Users L3 aalib An ASCII Art Library L2 aalib-32bit An ASCII Art Library L2 aalib-devel Development Package for AAlib L2 aalib-devel-32bit Development Package for AAlib L2 acct User-Specific Process Accounting L3 acl Commands for Manipulating POSIX Access Control Lists L3 acpid Executes Actions at ACPI Events L3 adaptec-firmware Firmware files for Adaptec SAS Cards (AIC94xx Series) L3 agfa-fonts Professional TrueType Fonts L2 aide Advanced Intrusion Detection Environment L2 alsa Advanced Linux Sound Architecture L3 alsa-32bit Advanced Linux Sound Architecture L3 alsa-devel Include Files and Libraries mandatory for Development. -

A-Sign Client Developers Manual
a-sign Client Developers Manual Version: 1.8 Author: Franz Brandl Table of Content Table of Content................................................................................................................... 2 1 About this Document.................................................................................................. 4 1.1 Purpose.................................................................................................................... 4 1.2 Abbreviations......................................................................................................... 4 1.3 Bibliography........................................................................................................... 4 1.4 Document History................................................................................................ 5 1.5 Client History......................................................................................................... 5 2 Overview ......................................................................................................................... 7 2.1 Installation ............................................................................................................. 9 2.1.1 Supported Operating Systems........................................................ 9 2.1.2 Supported Netscape Products ......................................................... 9 2.1.3 Prerequisites..................................................................................... 10 3 Microsoft CryptoAPI 2.0 ......................................................................................... -

Software Tools for the World-Wide Web
Software Tools for the World-Wide Web A Survey October 1995–May 1996 Tony McDonald David Surtees Janet Wheeler Computing Service University of Newcastle Contents Introduction 1 Browsers 1 HTML Tools 2 Servers 3 Other Tools 5 Conclusions 6 Appendix: Summary of Tools 7 Browsers 7 HTML Tools 8 Servers 9 Other Tools 10 On-line Tools 12 1 Introduction The aim of this project was to perform a cross-platform (Macintosh, UNIX and Windows) survey of World-Wide Web (WWW) software tools and to report briefly on as many as possible under the constraints of time, software costs and equipment available. It was not within the remit of the project to make specific recommendations. The market is very volatile and there is a huge number of tools with more appearing literally every day. Because of this we have mainly concentrated on servers, browsers and HTML tools; coverage of other areas has of necessity been somewhat patchy due to time constraints. In the course of the survey we have identified 33 servers, 38 browsers, 82 HTML tools and 61 miscellaneous others, including log analysis, helpers, graphics, imagemaps and bookmark managers, plus 12 online tools, mainly HTML validation services. Details are available at http://www.ncl.ac.uk/wwwtools/ The World-Wide Web provides an unusual business model, whereby companies offer software with very attractive pricing, or sometimes even free of charge. This tends to be done as an attempt to set standards or to "increase market share" (although what this means in this environment is quite a different matter). Some shareware and freeware tools written by individuals are either very much under development or have been abandoned by their authors. -

Openlimit Base Components 2.5
Datasheet System requirements OpenLimit Base components 2.5 Date: 26.05.2009 Datasheet - OpenLimit base components 2.5 Content 1 System requirements 3 1.1 Operating systems 3 1.2 Hardware 3 1.3 Software 4 1.4 Smartcards 4 OpenLimit CC Sign 4 OpenLimit Batch25 5 1.5 Smartcard terminals 5 Smartcard terminal drivers 6 2 Datasheet - OpenLimit base components 2.5 1 System requirements 1.1 Operating systems Windows NT 4.0 from Service Pack 6 * Windows 2000 from Service Pack 4 Windows 2003 Windows 2003 64Bit Edition Windows XP from Service Pack 2 Windows XP 64Bit Edition Windows XP Tablet PC Edition Windows Vista Windows Vista 64Bit Edition Windows 2008 Windows 2008 64Bit Edition * OpenLimit Batch25 cannot be used under Windows NT. plus Windows 2000 Terminal Server with Citrix Meta-Frame Windows 2003 Terminal Server with and without Citrix Meta-Frame Windows 2008 Terminal Server (for the operation in a Terminal Server environment a special license key is necessary) 1.2 Hardware at least an Intel 586 compatible processor at least 200 MB free disk space at least 256 MB free available RAM 3 Datasheet - OpenLimit base components 2.5 1.3 Software Internet Explorer from Version 5.01 Mozilla from Version 1.6 (corresponds to Netscape from Version 7.1, Firefox from Version 1.0.4) JRE (Java Runtime Environment) from Version 1.4.2_08 JAI (Java Advanced Imaging) Adobe Reader / Adobe Acrobat 7.0.8 (for the OpenLimit PDF Plug-In) In order to use the OpenLimit PDF Plug-In for Adobe the Adobe Reader or Adobe Acrobat from version 7.0.8 has to be installed on the computer. -

Novell SUSE Linux Package Description and Support Level Information for Contracted Customers and Partners
Novell SUSE Linux Package Description and Support Level Information for Contracted Customers and Partners Definitions and Support Level Descriptions ACC: Additional Customer Contract necessary L1: Installation and problem determination, which means technical support Configuration designed to provide compatibility information, installation assistance, usage support, on-going maintenance and basic troubleshooting. Level 1 Support is not intended to correct product defect errors. L2: Reproduction of problem isolation, which means technical support designed to Potential Issues duplicate customer problems, isolate problem area and provide resolution for problems not resolved by Level 1 Support. L3: Code Debugging and problem resolution, which means technical support designed Patch Provision to resolve complex problems by engaging engineering in resolution of product defects which have been identified by Level 2 Support. Servicelevel Package Short Name Package Description SLES10 SP4 x86 3ddiag A Tool to Verify the 3D Configuration L3 844-ksc-pcf Korean 8x4x4 Johab Fonts L2 This software changes the resolution of an available vbios 855resolution L2 mode. This software changes the resolution of an available vbios 915resolution L2 mode. a2ps Converts ASCII Text into PostScript L2 aaa_base SUSE Linux Base Package L3 aaa_skel Skeleton for Default Users L3 aalib An ASCII Art Library L2 aalib-devel Development Package for AAlib L2 acct User-Specific Process Accounting L3 acl Commands for Manipulating POSIX Access Control Lists L3 acpid Executes Actions at ACPI Events L3 adaptec-firmware Firmware files for Adaptec SAS Cards (AIC94xx Series) L3 agfa-fonts Professional TrueType Fonts L2 aide Advanced Intrusion Detection Environment L2 alsa Advanced Linux Sound Architecture L3 alsa-devel Include Files and Libraries mandatory for Development.