Topics in International Relations: Contemporary Security Issues
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Course Syllabus
The University of Oklahoma College of Continuing Education Advanced Programs – Course Syllabus Course Title: National Security Leadership Course Number: IAS 5940-108 Course Description: National Security Leadership is a course designed to focus the student both on the policy process and its substance. To that end, we will look at how the national security policymaking process developed from the National Security Act of 1947 through the Goldwater-Nichols DOD Reorganization Act of 1986 to the present. This will entail a thorough examination of the US interagency process both in theory and how it works in practice. In terms of substance, we will consider the products beginning with NSC 68 and continuing up to the current National Security Strategy of the United States. We will also examine a series of case studies beginning with the 1989 invasion of Panama up to and including the current conflicts in Iraq and Afghanistan. In this regard, we will pay particular attention to the Iraq situation from 2006 to the present with a hard look at the “surge” strategy and how it came into being. As a counterpoint to the major cases we will consider the variety of “low intensity” national security conflicts that have involved the US since the end of World War II. The culminating exercise of the course will be a day long crisis action simulation that will take place in real time. Class Dates, Location and Hours: Dates: August 14 – 20, 2017 Location: Hurlburt Field, Florida. Class will be held in Bldg. 90220, 221 Lukasik Ave. Hours: Monday - Friday 6:00 p.m.-9:30 p.m.; Saturday 8:00 a.m.-4:30 p.m.; Sunday 8:00 a.m.-12:00 p.m. -

Security Studies
SECURITY STUDIES POSTGRADUATE CERTIFICATE POSTGRADUATE DIPLOMA MASTER OF SCIENCE INVESTIGATING THE KEY ISSUES AND EMERGING PARADIGMS OF SECURITY, INTELLIGENCE ANALYSIS AND CRIMINOLOGY AT LOCAL, NATIONAL AND INTERNATIONAL LEVELS In Partnership with www.security-studies.com [email protected] UK +44 (0)20 7017 4483 INTRODUCTION Dear Prospective Student, Security is one of the fastest growing areas of concern in the academic, corporate and public domains. This is due not only to the threats of war and terrorism but also issues related to crime, safety, global strategy and political upheaval. More than ever before, national governments, international agencies and major corporations recognise the need for personnel with a strong grasp of intelligence and security issues who can also demonstrate exceptional skills of research and analysis. This postgraduate Security Studies programme will give you a solid understanding of the many problems facing the international community today, with flexible study options of a PGCert, PGDip and MSc. The programme examines key themes and debates shaping the concepts of security and security studies. It addresses critical areas of contemporary concern within security studies, covering issues stretching from foreign policy through to the role of radicalisation in international politics to the evolving dangers of financial crime all within and including the background of the cyber or digital dimension. The Security Studies programme will not only equip you to analyse these types of problems but will also help you to place them in the context of broader military, strategic and political considerations. You will gain a solid academic grounding in criminology, terrorism studies and intelligence studies. -

Department of Security Studies 1
Department of Security Studies 1 DEPARTMENT OF SECURITY STUDIES About Chair: Nadav Morag ([email protected]) Contact Information: (936) 294-1646; Vivian Carlson ([email protected]) Website: Department of Security Studies (http://www.shsu.edu/academics/criminal-justice/departments/security-studies/) Mission Homeland Security (HS) is an emerging and evolving discipline that continues to have a significant impact on the public and private sectors. Terrorism, natural disasters, cyber-attacks against critical infrastructures, public health emergencies, and large-scale organized crime, and similar issues all present challenges in terms of the ability of society, the economy, and the government to function when such events occur. Moreover, despite the fact that these are very different types of threats, they will require many of the same tools in order to cope with them. For example, prevention of terrorism and prevention of cyber-attacks require that law enforcement and intelligence agencies cooperate, share information, and design integrated strategies to track down and apprehend such threats domestically (or in concert with the military when the threat is based overseas). Similarly, critical infrastructure targets and industries must share information and engage in joint planning across their respective industries, with governmental authorities. This same type of information-sharing and joint planning is important in preparing for, and responding to, natural disasters such as Hurricane Harvey and environmental disasters such as Deepwater Horizon. -

International Security Studies After the Cold War: an Agenda for the Future
INTERNATIONAL SECURITY STUDIES AFTER THE COLD WAR: AN AGENDA FOR THE FUTURE SEAN M. LYNN-JONES 91-11 DECEMBER 1991 CITATION AND REPRODUCTION This document appears as Discussion Paper 91-11 of the Center for Science and International Affairs. CSIA Discussion papers are works in progress. Comments are welcome and may be directed to the author in care of the Center. This paper may be cited as: Sean M. Lynn-Jones, International Security Studies after the Cold War: An Agenda for the Future. CSIA Discussion Paper 91-11, Kennedy School of Government, Harvard University, December 1991. The views expressed in this paper are those of the authors and publication does not imply their endorsement by CSIA and Harvard University. This paper may be reproduced for personal and classroom use. Any other reproduction is not permitted without written permission of the Center for Science and International Affairs, Publications, 79 JFK Street, Cambridge, MA 02138, telephone (617) 495-3745 or telefax (617) 495-5776. Introduction* The field of international security studies has always examined important public policy problems, and its scholars and analysts often have been drawn to prominent current issues. At the dawn of the atomic age, scholars tried to understand the implications of "the absolute weapon" for the United States and the world. In the 1950s, the thermonuclear revolution led to an explosion of work on deterrence theory and the conundrum of how to make the hydrogen bomb militarily and politically useful. In the 1970s, the Vietnam War and U.S.-Soviet détente reduced interest in military questions. Later in that decade strategic parity prompted increased attention to problems of conventional deterrence and defense. -

Nils W. Metternich: Curriculum Vitae
Curriculum Vitae Nils W. Metternich University College London Department of Political Science Phone: +44 20-7679-4974 The Rubin Building Mobile: +44 79-6424-5536 29-31 Tavistock Square Email: [email protected] London, WC1H 9QU Website: ucl.ac.uk/∼uctqnm0 United Kingdom Research Interests Civil Wars, Military Interventions, Rebel Organizations, Democratization, Health and Civil War, Priva- tization of Warfare, Formal Modeling, Quantitative Methods, Forecasting. Positions October 2017-Current. Reader in International Relations. Department of Political Science, University College London. October 2015-September 2017. Senior Lecturer in International Relations. Department of Political Science, University College London. January 2013-September 2015. Lecturer in International Relations. Department of Political Science, University College London. January 2011-December 2012. Visiting Assistant Professor/Post-doc. Department of Political Science, Duke University, Prof. Michael Ward. August 2008-September 2010. Research Officer. Department of Government, University of Essex, "Disaggregating Civil Wars" funded by the European Science Foundation, Prof. Han Dorussen and Prof. Kristian Skrede Gleditsch. February-December 2007. Research Associate. Free University of Berlin, Research Centre "Governance in Areas of Limited Statehood", Project "Armed Conflict and (In-)Security in Areas of Limited State- hood", Prof. Sven Chojnacki. August 2005-January 2007. Student Research Assistant. Free University of Berlin, Department for Peace and Security Studies, Prof. Sven Chojnacki. June 2004-August 2004. Student Research Assistant. Social Science Research Centre Berlin, Department for International Politics, Prof. Sven Chojnacki. Education Degree coursework October 2007- January 2011. PhD Political Science, University of Essex. October 2003-December 2006. Diplom (equivalent to M.Sc.) Political Science, Free University of Berlin. Nils W. -

Security Studies • This Is General Advising Information for Security Studies Majors
The BA/BS in Multidisciplinary Studies: Security Studies • This is general advising information for Security Studies majors. Please consult with your academic advisor regarding any questions or concerns you have about major requirements and your specific situation. Faculty Advisor Dr. Armin Krishnan Director of the Security Studies Program [email protected] What Is Security Studies? Wars, insurgency, terrorism, transnational organized crime, WMD, arms races, weapons proliferation, cyberwar, diminishing resources, climate change, peacekeeping, conflict resolution, economic collapse, genocide, and pandemics – these are all complex security issues that shape international politics today. ECU’s Security Studies program explores all of the aforementioned security challenges from an interdisciplinary perspective and it equips our students with the knowledge and analytical skills for a career in national security, law enforcement, and foreign affairs. We offer courses in: • Homeland Security • International Relations • National and International Security What Is Security Studies? • Security Studies started out as a specialization in the discipline of International Relations, which is itself a specialization in the discipline of Political Science. • It is now an interdisciplinary field that seeks to develop analytical tools for understanding the problem of security. • In its essence, security is about survival. Career Options With a Security Studies Degree • Armed Forces • Law Enforcement • Intelligence Agencies • Private Security Sector • International -

IAS 5940-240: Topics in International Studies: Western Hemispheric Security - an American Dilemma
IAS 5940-240: Topics in International Studies: Western Hemispheric Security - An American Dilemma Course Description: The world has changed tremendously since the end of the Cold War in many respects, security being chief among them. The relative global stability that the Cold War brought to the West has evolved over the past three decades to become an inherently unstable and volatile one. The Western Hemisphere, traditionally comprised of Western Europe, North America and certain Pacific allies, has seen traditional threats to security change in nature and increase in complexity. The Cold War threat of the Soviet nuclear missile has been effectively replaced by a long list of smaller security problems, which are proving a significant challenge to counter. How has America chosen to manage security in the Western Hemisphere amidst all this change? The resulting dilemma for America is whether to “go it alone” or engage a myriad of international partners to ensure global stability that ultimately affects life at home. Course Dates and Format Information: Dates: January 26 - 31, 2021 Format: Hybrid Zoom-based classes, online discussion topic posts and recorded lectures. Zoom meeting times listed under Detailed Course Schedule below. Last day to enroll or drop without penalty: December 28, 2020 Site Director and information for VA Benefits: Site Director: Rachel Draper Location: Vilseck, Germany. (Rose Barracks: Buidling 223, Room 2.2, 92249 Vilseck ) Hours: Course adjusted to hybrid format; synchronous hours listed below. Email: [email protected]. DSN: 476-2069 or CIV 09962-83-2069 (use email for contact purposes, as site director is in telework status.) Professor Contact Information: Course Professor: Bruce P Barnes (Lieutenant-Colonel, RCAF, retired) Email Address: [email protected] Virtual Office Hours: By appointment Professor availability: The professor will be available via email to students during the above listed Virtual Office Hours and other methods by arrangement. -

Security: Dialogue Across Disciplines
Security: Dialogue across Disciplines Edited by Philippe Bourbeau Security: Dialogue across Disciplines Security is one of the most daunting subjects of the 21st century. This edited volume provides a comparative analysis of the ways in which the concept of security is theorised and studied across several disciplines. This book has two objectives: first, to explore the growing diversity of theories, paradigms and methods developed to study security; second, to initiate a multidisciplinary dialogue about the ontological, epistemological, paradigmatic, and normative aspects of security studies in social sciences. Drawing content from a wide range of international scholars, this volume examines the study and theorisation of security across several disciplines and issue areas. Readers from different fields are invited to reflect on their conceptualisations of security and to consider how an interdisciplinary dialogue can stimulate and enrich the understanding of security in our contemporary world. Philippe Bourbeau is Temporary University Lecturer in the Department of Politics and International Studies at the University of Cambridge. He is the author of The Securitization of Migration. A study of movement and order (2011) and of La diaspora chinoise et l’État chinois (2002). His articles have been published in Millennium: Journal of International Studies, Resilience: International Policies, Practices and Discourses, Critique internationale, and Revue européenne des migrations internationales. ii Contents Notes on the contributors Acknowledgements 1 A Multidisciplinary Dialogue on Security Philippe Bourbeau 2 Liberty, Fear and the State: Philosophical Perspectives on Security Jonathan Herington 3 Anthropologies of Security: Beyond Disciplinary Frameworks Daniel M. Goldstein 4 Security: A Geography Perspective Philippe Le Billon 5 Sociology and Security Lisa Stampnitzky and Greggor Mattson 6. -

The Evolution of International Security Studies
THE EVOLUTION OF INTERNATIONAL SECURITY STUDIES BARRY BUZAN Department of International Relations London School of Economics and Political Science LENE HANSEN Department of Political Science University of Copenhagen 1568BB 12975 75 ,1297509D59B.19/B1BC2:5BBB85,12975,5 B56C51D191251B8BB 12975 75B5 8BB9 7 ,/ cambridge university press Cambridge, New York, Melbourne, Madrid, Cape Town, Singapore, Sao˜ Paulo, Delhi Cambridge University Press The Edinburgh Building, Cambridge CB2 8RU, UK Published in the United States of America by Cambridge University Press, New York www.cambridge.org Information on this title: www.cambridge.org/9780521694223 c Barry Buzan and Lene Hansen 2009 ⃝ This publication is in copyright. Subject to statutory exception and to the provisions of relevant collective licensing agreements, no reproduction of any part may take place without the written permission of Cambridge University Press. First published 2009 Printed in the United Kingdom at the University Press, Cambridge AcataloguerecordforthispublicationisavailablefromtheBritishLibrary Library of Congress Cataloguing in Publication data Buzan, Barry. The evolution of international security studies / Barry Buzan, Lene Hansen. p. cm. Includes bibliographical references and index. ISBN 978-0-521-87261-4 1. Security, International – Study and teaching. 2. Security, International – Research. 3. Security, International – History. I. Hansen, Lene. II. Title. JZ5588.B887 2009 355′.033 – dc22 2009025609 ISBN 978-0-521-87261-4 hardback ISBN 978-0-521-69422-3 paperback Cambridge University Press has no responsibility for the persistence or accuracy of URLs for external or third-party internet websites referred to in this publication, and does not guarantee that any content on such websites is, or will remain, accurate or appropriate. 1568BB 12975 75 ,1297509D59B.19/B1BC2:5BBB85,12975,5 B56C51D191251B8BB 12975 75B5 8BB9 7 ,/ THE EVOLUTION OF INTERNATIONAL SECURITY STUDIES International Security Studies (ISS) has changed and diversified in many ways since 1945. -
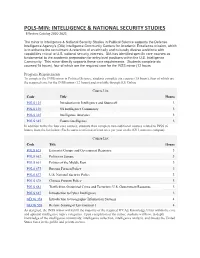
Pols-Min: Intelligence & National Security Studies
POLS-MIN: INTELLIGENCE & NATIONAL SECURITY STUDIES Effective Catalog 2020-2021 The minor in Intelligence & National Security Studies in Political Science supports the Defense Intelligence Agency's (DIA) Intelligence Communtiy Centers for Academic Excellence mission, which is to enhance the recruitment & retention of an ethically and culturally diverse workforce with capabilities critical to U.S. national security interests. DIA has identified specific core courses as fundamental to the academic preparation for entry-level positions within the U.S. Intelligence Community. This minor directly supports these core requirements. Students complete six courses(18 hours), four of which are the required core for the INSS minor (12 hours Program Requirements To complete the INSS minor in Political Science, students complete six courses (18 hours), four of which are the required core for the INSS minor (12 hours) and available through KU Online Course List Code Title Hours POLS 125 Introduction to Intelligence and Statecraft 3 POLS 130 US Intelligence Community 3 POLS 325 Intelligence Analytics 3 POLS 345 Counterintelligence 3 In addition to the the four core courses, students then complete two additional courses related to INSS (6 hours) from the list below (Each course is offered at least once per year on the KU Lawrence campus): Course List Code Title Hours POLS 625 Extremist Groups and Government Response 3 POLS 652 Politics in Europe 3 POLS 661 Politics of the Middle East 3 POLS 675 Russian Foreign Policy 3 POLS 677 U.S. National Security Policy 3 POLS 678 Chinese Foreign Policy 3 POLS 682 Trafficking, Organized Crime and Terrorism: U.S. -

Political Economy in Security Studies After the Cold War Author(S): Jonathan Kirshner Source: Review of International Political Economy, Vol
Political Economy in Security Studies after the Cold War Author(s): Jonathan Kirshner Source: Review of International Political Economy, Vol. 5, No. 1 (Spring, 1998), pp. 64-91 Published by: Taylor & Francis, Ltd. Stable URL: http://www.jstor.org/stable/4177257 . Accessed: 10/11/2014 10:11 Your use of the JSTOR archive indicates your acceptance of the Terms & Conditions of Use, available at . http://www.jstor.org/page/info/about/policies/terms.jsp . JSTOR is a not-for-profit service that helps scholars, researchers, and students discover, use, and build upon a wide range of content in a trusted digital archive. We use information technology and tools to increase productivity and facilitate new forms of scholarship. For more information about JSTOR, please contact [email protected]. Taylor & Francis, Ltd. is collaborating with JSTOR to digitize, preserve and extend access to Review of International Political Economy. http://www.jstor.org This content downloaded from 128.197.140.161 on Mon, 10 Nov 2014 10:11:52 AM All use subject to JSTOR Terms and Conditions Reviewof InternationalPolitical Economy 5:1 Spring1998: 64-91 Political economy in security studies after the cold war Jonathan Kirshner Department of Government,Cornell University ABSTRACT In contemporary International Relations theory, there exists a sharp distinction between internationalpolitical economy and security studies. However, this is largely a false distinction,a product of peculiar circum- stancesassociated with the cold war, and one which is becomingincreasingly anachronisticin the post-cold war era. In order to understand inter- nationalrelations in this era, a reintegrationof the disciplineis necessary. This articleconsiders three sets of issue areasin which appeals to themes normally associated with political economy are necessary to understand national security concerns. -

BA Government: National Security Studies
Bachelor of Arts in Government National Security Studies Concentration 2019-2020 Degree Completion Plan Important: This degree plan is effective for those starting this degree program in fall 2019 through summer 2020. This degree plan will remain in effect for students who do not break enrollment or who do not change degree programs, concentrations or cognates. GENERAL EDUCATION/ FOUNDATIONAL SKILLS REQUIREMENTS (62-65 hours) Course Hrs Sem Grade Course Hrs Sem Grade Communication & Information Literacy (16 hours)1 Major Foundational Courses (3-6 hours) ENGL 101 Composition & Rhetoric 3 GOVT 200 Constitutional Govt. & Free Enterprise5 3 INQR 101 Inquiry 101 1 GOVT 220 American Government5 3 ___________ Communications Elective 3 ___________ Composition Elective 3 MAJOR ___________ Information Literacy Elective 3 Core (15 hours) ___________ Information Literacy Elective 3 GOVT 330 Introduction to Comparative Politics 3 GOVT 350 Political Economy & Public Policy 3 Technological Solutions & Quantitative Reasoning (4-7 hours)1 GOVT 421 American Constitutional History 3 UNIV 101 University Core Competencies 1 GOVT 425 American Foreign Policy 3 MATH Math Elective (MATH 114 or higher) 3 GOVT 490 Political Theory 3 ___________ Technology Competency2 0-3 Concentration (33 hours) Critical Thinking (8 hours)1 CJUS 380 Introduction to Homeland Security6 3 RLGN 105 Intr Bwvw/Contemp Moral Issues3 2 CJUS 382 Critical Infrastructure Protection6 3 RSCH 201 Research 201 3 GOVT 376 Resilient Nations 3 ___________ Critical Thinking Elective 3 GOVT 380 Intro.