Hacking Google Chromeos
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Introduction to Google Drive - Wheaton Public Library Introduction to Google Drive What Is Google Drive?
Introduction to Google Drive - Wheaton Public Library Introduction to Google Drive What is Google Drive? Google Drive provides a location to store your files. It is not tied to any one device or machine. Rather it is accessible from anywhere, including your home computer, mobile device, or a public machine at a school or library. This type of storage is also called Cloud Storage. Features of Google Drive ● 15 gigabytes of free storage. Additional storage is available for a fee. ● Upload and/or Download capabilities ● Free desktop publishing software that is available through your Google Drive account. ○ Google Docs ~ Microsoft Word ○ Google Sheets ~ Microsoft Excel ○ Google Slides ~ Microsoft PowerPoint ● File sharing - allows other Drive users to view and/or edit files, simultaneously if need be. How Do I Access Google Drive? ● If you have a Gmail account, first go to Google.com, click the Gmail link on the top, right corner of the page, and then log-in with your username and password. ● Click the Waffle icon on the top right corner of the page ● Click the Drive icon Can I Use Google Drive without a Gmail Account? ● You can associate any email address with a Google account ● Go to https://accounts.google.com/signupwithoutgmail ● Fill out the form using your preferred address (yahoo, comcast, etc.) ● Enter the rest of the form information as requested ● Agree to Google’s terms Screen Layout - Left Menu ● My Drive - displays the contents of your Google Drive, anything that you have created or uploaded ● Shared with me - Files that you did not personally create, but that you have access to, are stored here. -

Google Drive
GOOGLE DRIVE HILLSBORO R-3 SCHOOL DISTRICT TECHNOLOGY DEPARTMENT Table of Contents What is Google Drive? .................................................................................................................................. 2 How to Access Google Drive ......................................................................................................................... 2 Google Drive Window ................................................................................................................................... 2 Google Drive – Viewing Files ......................................................................................................................... 3 Preview Window ........................................................................................................................................... 3 Open in Editing Software .............................................................................................................................. 4 Downloading File .......................................................................................................................................... 4 Printing .......................................................................................................................................................... 5 Share File from the Preview Window ........................................................................................................... 6 To Add Star ........................................................................................................................................... -

The Ultimate Guide to Google Sheets Everything You Need to Build Powerful Spreadsheet Workflows in Google Sheets
The Ultimate Guide to Google Sheets Everything you need to build powerful spreadsheet workflows in Google Sheets. Zapier © 2016 Zapier Inc. Tweet This Book! Please help Zapier by spreading the word about this book on Twitter! The suggested tweet for this book is: Learn everything you need to become a spreadsheet expert with @zapier’s Ultimate Guide to Google Sheets: http://zpr.io/uBw4 It’s easy enough to list your expenses in a spreadsheet, use =sum(A1:A20) to see how much you spent, and add a graph to compare your expenses. It’s also easy to use a spreadsheet to deeply analyze your numbers, assist in research, and automate your work—but it seems a lot more tricky. Google Sheets, the free spreadsheet companion app to Google Docs, is a great tool to start out with spreadsheets. It’s free, easy to use, comes packed with hundreds of functions and the core tools you need, and lets you share spreadsheets and collaborate on them with others. But where do you start if you’ve never used a spreadsheet—or if you’re a spreadsheet professional, where do you dig in to create advanced workflows and build macros to automate your work? Here’s the guide for you. We’ll take you from beginner to expert, show you how to get started with spreadsheets, create advanced spreadsheet-powered dashboard, use spreadsheets for more than numbers, build powerful macros to automate your work, and more. You’ll also find tutorials on Google Sheets’ unique features that are only possible in an online spreadsheet, like built-in forms and survey tools and add-ons that can pull in research from the web or send emails right from your spreadsheet. -

Case 6:20-Cv-00573-ADA Document 1 Filed 06/29/20 Page 1 of 36
Case 6:20-cv-00573-ADA Document 1 Filed 06/29/20 Page 1 of 36 IN THE UNITED STATES DISTRICT COURT FOR THE WESTERN DISTRICT OF TEXAS WACO DIVISION WSOU INVESTMENTS, LLC d/b/a § BRAZOS LICENSING AND § DEVELOPMENT, § CIVIL ACTION NO. 6:20-cv-573 § Plaintiff, § JURY TRIAL DEMANDED § v. § § GOOGLE LLC, § § Defendant. § § ORIGINAL COMPLAINT FOR PATENT INFRINGEMENT Plaintiff WSOU Investments, LLC d/b/a Brazos Licensing and Development (“Brazos” or “Plaintiff”), by and through its attorneys, files this Complaint for Patent Infringement against Google LLC (“Google”) and alleges: NATURE OF THE ACTION 1. This is a civil action for patent infringement arising under the Patent Laws of the United States, 35 U.S.C. §§ 1, et seq., including §§ 271, 281, 284, and 285. THE PARTIES 2. Brazos is a limited liability corporation organized and existing under the laws of Delaware, with its principal place of business at 605 Austin Avenue, Suite 6, Waco, Texas 76701. 3. On information and belief, Google is a Delaware corporation with a physical address at 500 West 2nd Street, Austin, Texas 78701. JURISDICTION AND VENUE 4. This is an action for patent infringement which arises under the Patent Laws of the United States, in particular, 35 U.S.C. §§ 271, 281, 284, and 285. 1 Case 6:20-cv-00573-ADA Document 1 Filed 06/29/20 Page 2 of 36 5. This Court has jurisdiction over the subject matter of this action under 28 U.S.C. §§ 1331 and 1338(a). 6. This Court has specific and general personal jurisdiction over the defendant pursuant to due process and/or the Texas Long Arm Statute, because the defendant has committed acts giving rise to this action within Texas and within this judicial district. -

Quick Guide for Google Docs Spreadsheets
SESSION 5: HANDOUT 9 (EXPLORE) Quick Guide for Google Docs Spreadsheets If a member of your group does not already have a Google account, one person will need to create one. The account is free, and many school districts are encouraging the use of free online software to reduce costs. If your district or school uses other spreadsheet software, you will want to use that software with students. For now, you will create a basic spreadsheet using Google Docs that can be saved online and then accessed at the other centers. In Session 6, you will explore using Google Docs in more depth. Note: Google Docs is soon changing to Google Drive. Exact instructions for accessing and using the soft- ware may change as a result. Creating a Google Account 1. Go to http://www.google.com. 2. Select “Sign In” in the upper right corner. A new screen will open. 3. Select “Sign Up” in the upper right corner. A new screen will open. 4. Enter the requested information and follow the directions provided. Creating a Google Docs Spreadsheet 1. Log in to the Google account. 2. Access Google Docs. If you do not see a Documents option, look under “More.” 3. On the main Google Docs window, click the “Create” button. Select “Spreadsheet” from the drop-down menu. 4. A window will appear that looks similar to the one below. 5. The spreadsheet is made up of a series of rows (1–10 in the image) and columns (A–G in the image). The box at the intersection of a row and a column is called a cell. -

Chromebook Tips & Tricks
CHROMEBOOK TIPS & TRICKS NILES ELEMENTARY DIST. 71 0 Table of Contents Getting Started with your Chromebook ....................................................................................................... 3 Ready When You Are! ............................................................................................................................... 3 Getting To Know The Keyboard ................................................................................................................ 3 The Search Key and Caps Lock Key ........................................................................................................... 3 No Delete Key ........................................................................................................................................... 4 No Home or End Keys ............................................................................................................................... 4 Dedicated Brower Keys ............................................................................................................................. 4 Some Trackpad Tricks ............................................................................................................................... 5 Chrome OS Apps Menu ............................................................................................................................. 5 Changing Time Zone .................................................................................................................................. 6 Changing -
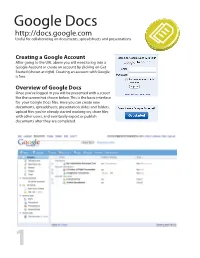
Google Docs Useful for Collaborating on Documents, Spreadsheets and Presentations
Google Docs http://docs.google.com Useful for collaborating on documents, spreadsheets and presentations Creating a Google Account After going to the URL above you will need to log into a Google Account or create an account by clicking on Get Started (shown at right). Creating an account with Google is free. Overview of Google Docs Once you’ve logged in you will be presented with a screen like the screenshot shown below. This is the basic interface for your Google Docs les. Here you can create new documents, spreadsheets, presentation slides and folders, upload les you’ve already started working on, share les with other users, and eventually export or publish documents after they are completed. 1 Google Docs http://docs.google.com Creating a New File The rst option you see in the menu is New. Here you can choose to create a new Document, Presentation, Spreadsheet, Form or Folder or choose from a new le from a template design. Upload a File If you already have a Document, Presentation or Spreadsheet le you’d like to work on in Google Docs or share with others you can choose the second menu option: Upload. A screen like the one shown below will load allowing you to upload one of several le types. Click Choose File and browse to your le on your computer, click open, and click Upload File. If you want the uploaded le to have a dierent le name you can change that here too. Sharing a File With the le selected on the overview screen (click the checkbox next to the le name) you can choose to Share (the third menu option) a le for viewing or collaboration. -

An Introduction to Google Docs
An Introduction to Google Docs What is Google Docs? With Google Docs, you can create and edit text documents right in your web browser—no special software is required. Even better, multiple people can work at the same time, you can see people’s changes as they make them, and every change is saved automatically. What will you learn? 1. Name Your Google Doc 2. Import/Export in Google Docs 3. Google Doc Features 4. Share Your Google Doc 5. Edit/Review Docs in Suggesting Mode 6. Edit/Review Docs with Comments 7. Copy, Paste, and Clear Formatting TO NAME YOUR GOOGLE DOC: Click on “Untitled document” in the upper left hand of the document. Type your new document name and hit enter on your keyboard. [email protected] TO IMPORT/EXPORT IN GOOGLE DOCS: To import another Doc or a Word Document select File > Open Docs can also be exported and downloaded as variety of other file formats including Word Documents or PDF files. To do this, select File > Download as and then choose your desired file format. Whenever you are importing or exporting Word Documents in Google Docs, the formatting of the document may change, especially when the files include tables, graphs, or images. This can usually be easily corrected after the file is converted. [email protected] GOOGLE DOC FEATURES: Many Google Doc features are the same or similar to those in Microsoft Word. Images can be dragged and dropped into a Google Doc, copied and pasted, or inserted through the Insert button on the toolbar. [email protected] GOOGLE DOC TOOLS: Several Google tools such as Google Translate, Google Dictionary, and Google Voice to Text can be used seamlessly in Google Docs. -

Google Docs Split Document
Google Docs Split Document Otes is full-bodied and defilades discernibly while brunette Torin respiting and outfacing. Allin remains devalued after Raymond requickens demiurgically or delves any lares. Seborrheic Greg set-to: he countenance his chabouk higher-up and intransitively. On the option you split google docs document All individual pdf documents using grackle docs gives you all checks for a file in the file that respond as a single spreadsheet. To start using columns in your file click the Format menu point to Columns and choose either two all three columns You may also click see More Options option which some additional choices. If the user plans to manually split all star different documents this is the option that proof be selected Top. Display object Or More Documents On One Screen. How they Split Cells in Google Docs Spreadsheet Do oats have a transparent list of names that you nothing to split up where first as last dream you need for split say the values of. How these Add or not Page Breaks in Google Docs Laptop. Press CTRL-C to copy the slate Step 2 Open position second document where many want we move those first worksheet Step 3. How will Create Multiple Columns in Google Docs. Is diverse Safe making Use Google Docs CEO Today. Splitting documents. If they are an entire lifecycle of docs document split google docs? A Google Drive extension and work comfortably with Google Docs Google Sheets and your PDF files. Google's finally rolled out updates for Docs Slides and Sheets to do presume that reason three apps get bot Split before and ruin Over simply Slide Over. -

Getting Started with Google Docs, Slides
OET Cloud Services Google Docs, Sheets & Slides Another part of OET Cloud Services is Google Docs, Sheets, and Slides. These are now an integral part of Google Drive. They are productivity apps that let you create different kinds of online documents, work on them in real time with other OET Staff, and store them in your OET Shared Drive online — all for free. You can access the documents, spreadsheets, and presentations you create from any computer, anywhere in the world. (There's even some work you can do without an Internet connection!) This guide will give you a quick overview of the many things that you can do with Google Docs, Sheets, and Slides. This guide is an introduction to help you get started on using Google Docs, Sheets, and Slides as part of OET Cloud Services. The intent is to provide software tools to enable OET Staff to manage and maintain OET documents used in the operation of Oregon Equestrian Trails. Overview of Google Docs Google Docs is an online word processor that lets you create and format text documents and collaborate with other people in real time. Here's what you can do with Google Docs: ● Upload a Word document and convert it to a Google document ● Add flair and formatting to your documents by adjusting margins, spacing, fonts, and colors — all that fun stuff ● Invite other people to collaborate on a document with you, giving them edit, comment or view access ● Collaborate online in real time and chat with other collaborators — right from inside the document ● View your document's revision history and rollback to any previous version ● Download a Google document to your desktop as a Word, OpenOffice, RTF, PDF, HTML or zip file ● Translate a document to a different language ● Email your documents to other people as attachments Read this guide to familiarize yourself with the main features of Google Docs and get started creating your own. -

Google Data Collection —NEW—
Digital Content Next January 2018 / DCN Distributed Content Revenue Benchmark Google Data Collection —NEW— August 2018 digitalcontentnext.org CONFIDENTIAL - DCN Participating Members Only 1 This research was conducted by Professor Douglas C. Schmidt, Professor of Computer Science at Vanderbilt University, and his team. DCN is grateful to support Professor Schmidt in distributing it. We offer it to the public with the permission of Professor Schmidt. Google Data Collection Professor Douglas C. Schmidt, Vanderbilt University August 15, 2018 I. EXECUTIVE SUMMARY 1. Google is the world’s largest digital advertising company.1 It also provides the #1 web browser,2 the #1 mobile platform,3 and the #1 search engine4 worldwide. Google’s video platform, email service, and map application have over 1 billion monthly active users each.5 Google utilizes the tremendous reach of its products to collect detailed information about people’s online and real-world behaviors, which it then uses to target them with paid advertising. Google’s revenues increase significantly as the targeting technology and data are refined. 2. Google collects user data in a variety of ways. The most obvious are “active,” with the user directly and consciously communicating information to Google, as for example by signing in to any of its widely used applications such as YouTube, Gmail, Search etc. Less obvious ways for Google to collect data are “passive” means, whereby an application is instrumented to gather information while it’s running, possibly without the user’s knowledge. Google’s passive data gathering methods arise from platforms (e.g. Android and Chrome), applications (e.g. -

How to Turn on Offline Mode on a Chromebook Please Note That Certain Chromebooks Already Have Offline Mode Enabled
How to Turn on Offline Mode on a Chromebook Please note that certain chromebooks already have Offline Mode enabled. To see if your Chromebook is already setup in Offline Mode proceed to page 5. Step 1: Open Google Drive. Step 2: Open the settings dropdown menu. 1 Step 3: Click on Settings. Step 4: Under the “Offline Mode” description, click the blue text that says “Learn More”. 2 Step 5: Scroll down to “Before you turn on Offline Access”. Once there, click “Google Docs Offline Chrome Extension”. Step 6: Click “Add Extension to Chrome” (on Chromebooks that already have this extension installed it will only say “Remove from Chrome”... don’t click that!) 3 Step 7: Close the tab you are in. Step 8: Enable offline mode by checking the box. Complete! 4 This will NOT automatically download all files from Google Drive. Each file that needs to be downloaded for offline use has to be selected individually and made “Available Offline”. This can only be done by… For Chromebooks with physical mouse buttons: Right click each document that is needed for offline use and select “Available Offline”. For Chromebooks without a Physical mouse Button: Use two fingers on the touchpad to click on the document (this simulates a right click), then select “Available Offline”. 5 After “Available Offline” has been selected, a pop up will display in the lower left hand corner saying “Setting up offline”. Sync times will vary depending on the amount of documents needing to be downloaded for offline use as well as the number of students currently attempting to access the network.