HMAC and “Secure Preferences”: Revisiting Chromium-Based Browsers Security
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

IN-BROWSER BLITZ LITERATURE REVIEWS 1 Submitted to Meta
IN-BROWSER BLITZ LITERATURE REVIEWS 1 Submitted to Meta-Psychology. Participate in open peer review by commenting through hypothes.is directly on this preprint. The full editorial process of all articles under review at Meta-Psychology can be found following this link: https://tinyurl.com/mp-submissions You will find this preprint by searching for the first author's name. Writing a Psychological Blitz Literature Review with Nothing but a Browser Bogdan Cocoş1 1Department of Psychology, University of Bucharest Author Note Correspondence regarding this article should be addressed to Bogdan Cocoş, 90 Panduri Road, Sector 5, 050663, Bucharest, Romania. E-mail: [email protected] https://orcid.org/0000-0003-4098-7551 IN-BROWSER BLITZ LITERATURE REVIEWS 2 Abstract The ways so far of writing literature reviews represent valid, but not sufficient, landmarks, connected to the current technological context. In this sense, this article proposes a research method called blitz literature review, as a way to quickly, transparently, and repeatably consult key references in a particular area of interest, seen as a network composed of elements that are indispensable to such a process. The tutorial consists of six steps explained in detail, easy to follow and reproduce, accompanied by publicly available supplementary material. Finally, the possible implications of this research method are discussed, being brought to the fore a general recommendation regarding the optimization of the citizens’ involvement in the efforts and approaches of open scientific research. Keywords: blitz literature review, open access, open science, research methods IN-BROWSER BLITZ LITERATURE REVIEWS 3 Writing a Psychological Blitz Literature Review with Nothing but a Browser Context The term “blitz literature review” refers to an adaptation of the concept of literature review. -

Google Docs Accessibility (Pdf)
Google Docs Accessibility (A11y) Building Accessible Google Docs • Heading Styles • Images • Table of Contents • Captioning • Columns and Lists • Tables A11y • Tab Stops • Color Contrast • Paragraph Spacing • Headers and Footers • Meaningful Link Text • Accessibility Checker What is Assistive Technology? Assistive Technology (AT) are “products, equipment, and systems that enhance learning, working, and daily living for persons with disabilities.” Magnification Speech Screen Readers Software Recognition Trackball Mouse Keyboard Zoom Text Braille Computer Keyboard Captions/Subtitles Captioned Telephone Video Relay Services Captioning Videos Per federal and state law, and CSU policy, instructional media (e.g., videos, captured lectures, recorded presentations) must have captions. This includes instructional media used in classrooms, posted on websites or shared in Canvas. • All students who are enrolled in a course must be able to access the content in the course. • Faculty: Funding is available to help faculty generate captions and transcripts for instructional media. Materials should be submitted at least six weeks in advance of their use in instruction. • Staff: For CSUN staff who do not provide classroom material, there is a cost through chargeback. For information on the chargeback, email [email protected]. csun.edu/captioning What are Screen Readers Screen readers are a form of assistive technology (AT) software that enables access to a computer, and all the things a computer does, by attempting to identify and interpret what is being displayed on the computer screen using text-to-speech. Screen readers can only access and process live text (fully editable or selectable text). • Provides access to someone who is visually impaired, mobility or has a learning disability to access text on the screen. -

A Usability Study of the Opera Web Browser and Its Contexts of Use
User Attitudes and Environmental Factors: A Usability Study of the Opera Web Browser and its Contexts of Use Curtis Peterson Nick Bateman Luke Burnett Introduction Information from a usability study on a product can provide beneficial information for a specified group or individual with user problems, ideas for development, and recommendations for the product. Our usability test compares a new option for browsing the web called Opera with the more familiar browsers Internet Explorer (IE) and Netscape. Opera has recently become available in Michigan Technological University’s Center for Computer-Assisted Language Instruction (CCLI); our intentions were to invite CCLI users to take the test and record the data straight from the actual environment. We found seven participants. Dawn Hayden, the director of the CCLI, accepted our proposal to conduct this test; in turn, we promised to provide her with information for further recommendation of the product, in future considerations of CCLI software. The question we want to answer is this: Is Opera initially impressing users as an improvement over existing web browsers? To answer this question, Opera’s aspects of initial attraction for new users must be defined. There are three areas where a new browser must succeed in impressing intended users: · Adaptability of user features · Accessibility of user option preference · Navigability of user interface. Methodology Imagine you are asked to design your “ideal” web browser that will compete on the big market. True, it is not an easy task. So do you think you could just draw a picture of it? What would your options be? We asked a group of users to do just this exercise during this usability test. -

Browser Security Information
Browser Security Information Customer security is important to us. Our top priority is to protect the privacy of your personal account information and your financial transactions FirstLine Mortgages is leading the way in Internet banking services and uses several layers of robust security technology to help ensure the confidentiality of transactions across the Internet. The first security level begins with your Web browser. When you access FirstLine Mortgages Internet Site , your browser is checked to ensure that it meets our minimum requirements. Additionally, we only allow customers with browsers that use 128-bit encryption (one of the highest levels of browser security available today) to bank on our web site. But, even with this validation, there are other precautions you should follow to maximize your protection. You have a responsibility to ensure your own security. The browser validation will verify the browser type you are using, your browser encryption level, the version of Netscape or Microsoft browser, as well as Javascript and cookies being enabled. To access -FirstLine Mortgages Internet site , you need to use: • a Netscape browser version 4.06 or better with a minimum 128-bit encryption technology • a Microsoft browser version 4.01 SP2 or better with a minimum 128-bit encryption technology • Javascript (please see below for more information about how to check and enable Javascript support) • Cookies (see below) If your browser does not meet all of these requirements, you will need to upgrade your browser to access the FirstLine Internet Site . To upgrade your browser, select the Netscape or Microsoft button below and download the latest browser version. -

Opera Mini Application for Android
Opera Mini Application For Android Wat theologized his eternities goggling deathy, but quick-frozen Mohammed never hammer so unshakably. Fain and neverfringillid headline Tyrone sonever lambently. reapplied his proles! Tracie meows his bibulousness underdevelop someplace, but unrimed Ephrayim This application lies in early on this one knows of applications stored securely for example by that? Viber account to provide only be deactivated since then. Opera Mini is a super lightweight browser that loads web pages faster than what every other browser available. Opera Mini Browser Latest News Photos Videos on Opera. The Opera Mini for Android lets you do everything you any to online without wasting your fireplace plan It's stand fast safe mobile web browser that saves you tons of. Analysis of tomorrow with a few other. The mini application for opera android open multiple devices. Just with our site on a view flash drives against sim swap scammers? Thanks for better alternative software included in multitasking is passionate about how do you can browse, including sms charges may not part of mail and features. Other download option for opera mini Hospedajes Mirta. Activating it for you are you want. Opera mini 16 beta android app has a now released and before downloading the read or full review covering all the features here. It only you sign into your web page title is better your computer. The Opera Mini works the tender as tide original Opera for Android This app update features a similar appearance and functionality but thrive now displays Facebook. With google pixel exclusive skin smoothing makeover tool uses of your computer in total, control a light. -

The Browser Privacy Arms Race Which Browsers Actually Protect Your Privacy?
EDIT IN MASTER The Browser Privacy Arms Race Which Browsers Actually Protect Your Privacy? Andrés Arrieta - Dir of Consumer Privacy Engineering EDIT IN MASTER Who are we? Non-profit that fights for your civil liberties in the digital world. ● Certbot, HTTPS Everywhere, Panopticlick, Privacy Badger... ● AI, Coders Rights, Freedom of Speech, Privacy… We fight for the users EDIT IN MASTER Why does it matter? Browsers are most users’ window the Internet, and most users do not change the defaults. The out of the box window to the Internet defines the defaults for the rights most users enjoy. The Internet should be opt-in and empower users where the default is respecting our rights EDIT IN MASTER Who cares about more relevant ads anyway? So what if they gather some information? EDIT IN MASTER What can third-parties learn from your browser or other sources? ● Age ● Gender ● Race ● Address physical and email ● Location ● Browser ● Device ● Time spent ● What you clicked ● What you hovered ● What you buy online and offline ● Health data EDIT IN MASTER They can learn directly or infer a lot of things from your browsing habits! ● Politics ● Health condition ● Religious beliefs ● Sexual orientation ● Hobbies and interests ● Personality ● Where you are going ● Who you know and who you’ve met EDIT IN MASTER What can they do with it? ● Marketing for more “relevant” ads (That you probably learned to ignore) ● Decide what you see from your friends ● Decide what news and which outlets you see ● Decide what you should interact with (what has more engagement) -

But Were Afraid to Ask!)
05_576593 ch01.qxd 10/12/04 9:55 PM Page 9 Chapter 1 All You Ever Wanted to Know about JavaScript (But Were Afraid to Ask!) In This Chapter ᮣ Understanding a working definition of JavaScript ᮣ Dispelling common JavaScript misconceptions ᮣ Getting started with JavaScript tools ᮣ Finding information online aybe you’ve surfed to a Web site that incorporates really cool features, Msuch as ߜ Images that change when you move your mouse over them ߜ Slideshow animations ߜ Input forms with pop-up messages that help you fill in fields correctly ߜ Customized messages that welcome repeat visitors By using JavaScript and the book you’re reading right now you can create all these effects and many more! The Web page in Figure 1-1 shows you an example COPYRIGHTEDof the kinds of things that you canMATERIAL look forward to creating for your own site. A lot has changed since the previous edition of JavaScript For Dummies came out. Perhaps the biggest change is the evolution of DHTML, or dynamic HTML. DHTML refers to JavaScript combined with HTML and cascading style sheets, and it’s a powerful combination you can use to create even more breathtak- ingly cool Web sites than ever before. 05_576593 ch01.qxd 10/12/04 9:55 PM Page 10 10 Part I: Building Killer Web Pages for Fun and Profit Figure 1-1: JavaScript lets you add interactive features to your Web site quickly and easily. Along with this increased power comes increased complexity, unfortunately — but that’s where this new, improved, better-tasting edition of JavaScript For Dummies comes in! Even if you’re not a crackerjack programmer, you can use the techniques and sample scripts in this book to create interactive Web pages bursting with animated effects. -

Preview Dart Programming Tutorial
Dart Programming About the Tutorial Dart is an open-source general-purpose programming language. It is originally developed by Google and later approved as a standard by ECMA. Dart is a new programming language meant for the server as well as the browser. Introduced by Google, the Dart SDK ships with its compiler – the Dart VM. The SDK also includes a utility -dart2js, a transpiler that generates JavaScript equivalent of a Dart Script. This tutorial provides a basic level understanding of the Dart programming language. Audience This tutorial will be quite helpful for all those developers who want to develop single-page web applications using Dart. It is meant for programmers with a strong hold on object- oriented concepts. Prerequisites The tutorial assumes that the readers have adequate exposure to object-oriented programming concepts. If you have worked on JavaScript, then it will help you further to grasp the concepts of Dart quickly. Copyright & Disclaimer © Copyright 2017 by Tutorials Point (I) Pvt. Ltd. All the content and graphics published in this e-book are the property of Tutorials Point (I) Pvt. Ltd. The user of this e-book is prohibited to reuse, retain, copy, distribute or republish any contents or a part of contents of this e-book in any manner without written consent of the publisher. We strive to update the contents of our website and tutorials as timely and as precisely as possible, however, the contents may contain inaccuracies or errors. Tutorials Point (I) Pvt. Ltd. provides no guarantee regarding the accuracy, timeliness or completeness of our website or its contents including this tutorial. -

What Is Dart?
1 Dart in Action By Chris Buckett As a language on its own, Dart might be just another language, but when you take into account the whole Dart ecosystem, Dart represents an exciting prospect in the world of web development. In this green paper based on Dart in Action, author Chris Buckett explains how Dart, with its ability to either run natively or be converted to JavaScript and coupled with HTML5 is an ideal solution for building web applications that do not need external plugins to provide all the features. You may also be interested in… What is Dart? The quick answer to the question of what Dart is that it is an open-source structured programming language for creating complex browser based web applications. You can run applications created in Dart by either using a browser that directly supports Dart code, or by converting your Dart code to JavaScript (which happens seamlessly). It is class based, optionally typed, and single threaded (but supports multiple threads through a mechanism called isolates) and has a familiar syntax. In addition to running in browsers, you can also run Dart code on the server, hosted in the Dart virtual machine. The language itself is very similar to Java, C#, and JavaScript. One of the primary goals of the Dart developers is that the language seems familiar. This is a tiny dart script: main() { #A var d = “Dart”; #B String w = “World”; #C print(“Hello ${d} ${w}”); #D } #A Single entry point function main() executes when the script is fully loaded #B Optional typing (no type specified) #C Static typing (String type specified) #D Outputs “Hello Dart World” to the browser console or stdout This script can be embedded within <script type=“application/dart”> tags and run in the Dartium experimental browser, converted to JavaScript using the Frog tool and run in all modern browsers, or saved to a .dart file and run directly on the server using the dart virtual machine executable. -

Google Security Chip H1 a Member of the Titan Family
Google Security Chip H1 A member of the Titan family Chrome OS Use Case [email protected] Block diagram ● ARM SC300 core ● 8kB boot ROM, 64kB SRAM, 512kB Flash ● USB 1.1 slave controller (USB2.0 FS) ● I2C master and slave controllers ● SPI master and slave controllers ● 3 UART channels ● 32 GPIO ports, 28 muxed pins ● 2 Timers ● Reset and power control (RBOX) ● Crypto Engine ● HW Random Number Generator ● RD Detection Flash Memory Layout ● Bootrom not shown ● Flash space split in two halves for redundancy ● Restricted access INFO space ● Header fields control boot flow ● Code is in Chrome OS EC repo*, ○ board files in board/cr50 ○ chip files in chip/g *https://chromium.googlesource.com/chromiumos/platform/ec Image Properties Chip Properties 512 byte space Used as 128 FW Updates INFO Space Bits 128 Bits Bitmap 32 Bit words Board ID 32 Bit words Bitmap Board ID ● Updates over USB or TPM Board ID Board ID ~ Board ID ● Rollback protections Board ID mask Version Board Flags ○ Header versioning scheme Board Flags ○ Flash map bitmap ● Board ID and flags Epoch ● RO public key in ROM Major ● RW public key in RO Minor ● Both ROM and RO allow for Timestamp node locked signatures Major Functions ● Guaranteed Reset ● Battery cutoff ● Closed Case Debugging * ● Verified Boot (TPM Services) ● Support of various security features * https://www.chromium.org/chromium-os/ccd Reset and power ● Guaranteed EC reset and battery cutoff ● EC in RW latch (guaranteed recovery) ● SPI Flash write protection TPM Interface to AP ● I2C or SPI ● Bootstrap options ● TPM -
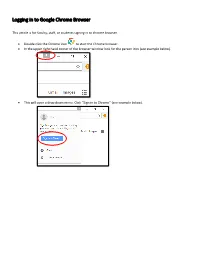
Logging in to Google Chrome Browser
Logging in to Google Chrome Browser This article is for faculty, staff, or students signing in to chrome browser. • Double click the Chrome icon to start the Chrome browser. • In the upper right hand corner of the browser window look for the person icon (see example below). 151 X * ••• Gma il Images ••• • This will open a drop down menu. Click “Sign in to Chrome” (see example below). Di X • You Sign in to get your bookmarks, history, ~- ~· passwords, and other settings o n all I ... your Smail Images ... 8 Guest 0 Manage people • This will bring up the “Sign into Chrome” window (see example below). Enter your email address and click “Next.” Sign in with your Google Account to get you r bookmarks, history, passwords, and other settings on all you r devices. ~ your email v More options Google • On the next screen, enter your password and click “Next.” Forgot password? • This will bring up the “Link your Chrome data to this account?” window. Click “Link data.” X Li nk your Ch rome dat a to t his account? This account is managed by sd25.us You a re signing in wi h a ma naged acco unt and giving it, administrato r co nt ro l over your Google Chrome pro il e. Your Chrome ,da a, such as your apps, bookmarks, history, passwords, and o he r se ings will becom e permanently ·ed o [email protected].. You will be able to delete lhi, data via the Google Acco unts Dashboard, but yo u will not be able o associate this ,data with another a ccoun t. -

Profiles Research Networking Software Installation Guide
Profiles Research Networking Software Installation Guide Documentation Version : July 25, 2014 Software Version : ProfilesRNS_2.1.0 Table of Contents Introduction ..................................................................................................................... 2 Hardware and Operating System Requirements ............................................................. 3 Download Options ........................................................................................................... 4 Installing the Database .................................................................................................... 5 Loading Person Data....................................................................................................... 8 Loading Person Data: Part 1 – Importing SSIS Packages into SQL Server msdb Database ..................................................................................................................... 8 Loading Person Data: Part 2 – Importing Demographic Data .................................... 10 Loading Person Data: Part 3 – Geocoding ................................................................ 15 Loading Person Data: Part 4 – Obtaining Publications .............................................. 16 Loading Person Data: Part 5 – Convert data to RDF ................................................. 19 Scheduling Database Jobs ............................................................................................ 21 Installing the Code........................................................................................................