The Eyes Have It on the Iris in Terms of Being Used for Identi- Tation in Another New Jersey District in 2003, Continued from Page 1 with a Single Pulse of Light
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27
Case 4:13-md-02420-YGR Document 2321 Filed 05/16/18 Page 1 of 74 1 2 3 4 5 6 7 8 UNITED STATES DISTRICT COURT 9 NORTHERN DISTRICT OF CALIFORNIA 10 OAKLAND DIVISION 11 IN RE: LITHIUM ION BATTERIES Case No. 13-md-02420-YGR ANTITRUST LITIGATION 12 MDL No. 2420 13 FINAL JUDGMENT OF DISMISSAL This Document Relates To: WITH PREJUDICE AS TO LG CHEM 14 DEFENDANTS ALL DIRECT PURCHASER ACTIONS 15 AS MODIFIED BY THE COURT 16 17 18 19 20 21 22 23 24 25 26 27 28 FINAL JUDGMENT OF DISMISSAL WITH PREJUDICE AS TO LG CHEM DEFENDANTS— Case No. 13-md-02420-YGR Case 4:13-md-02420-YGR Document 2321 Filed 05/16/18 Page 2 of 74 1 This matter has come before the Court to determine whether there is any cause why this 2 Court should not approve the settlement between Direct Purchaser Plaintiffs (“Plaintiffs”) and 3 Defendants LG Chem, Ltd. and LG Chem America, Inc. (together “LG Chem”), set forth in the 4 parties’ settlement agreement dated October 2, 2017, in the above-captioned litigation. The Court, 5 after carefully considering all papers filed and proceedings held herein and otherwise being fully 6 informed, has determined (1) that the settlement agreement should be approved, and (2) that there 7 is no just reason for delay of the entry of this Judgment approving the settlement agreement. 8 Accordingly, the Court directs entry of Judgment which shall constitute a final adjudication of this 9 case on the merits as to the parties to the settlement agreement. -

Zerohack Zer0pwn Youranonnews Yevgeniy Anikin Yes Men
Zerohack Zer0Pwn YourAnonNews Yevgeniy Anikin Yes Men YamaTough Xtreme x-Leader xenu xen0nymous www.oem.com.mx www.nytimes.com/pages/world/asia/index.html www.informador.com.mx www.futuregov.asia www.cronica.com.mx www.asiapacificsecuritymagazine.com Worm Wolfy Withdrawal* WillyFoReal Wikileaks IRC 88.80.16.13/9999 IRC Channel WikiLeaks WiiSpellWhy whitekidney Wells Fargo weed WallRoad w0rmware Vulnerability Vladislav Khorokhorin Visa Inc. Virus Virgin Islands "Viewpointe Archive Services, LLC" Versability Verizon Venezuela Vegas Vatican City USB US Trust US Bankcorp Uruguay Uran0n unusedcrayon United Kingdom UnicormCr3w unfittoprint unelected.org UndisclosedAnon Ukraine UGNazi ua_musti_1905 U.S. Bankcorp TYLER Turkey trosec113 Trojan Horse Trojan Trivette TriCk Tribalzer0 Transnistria transaction Traitor traffic court Tradecraft Trade Secrets "Total System Services, Inc." Topiary Top Secret Tom Stracener TibitXimer Thumb Drive Thomson Reuters TheWikiBoat thepeoplescause the_infecti0n The Unknowns The UnderTaker The Syrian electronic army The Jokerhack Thailand ThaCosmo th3j35t3r testeux1 TEST Telecomix TehWongZ Teddy Bigglesworth TeaMp0isoN TeamHav0k Team Ghost Shell Team Digi7al tdl4 taxes TARP tango down Tampa Tammy Shapiro Taiwan Tabu T0x1c t0wN T.A.R.P. Syrian Electronic Army syndiv Symantec Corporation Switzerland Swingers Club SWIFT Sweden Swan SwaggSec Swagg Security "SunGard Data Systems, Inc." Stuxnet Stringer Streamroller Stole* Sterlok SteelAnne st0rm SQLi Spyware Spying Spydevilz Spy Camera Sposed Spook Spoofing Splendide -

Palm Zire 31
Palm zire 31 Continue PalmOne 31ManufacterpalmOneTypePDALifespan2004-04-28'MediaSD/SDIO/MMC SlotPerative SystemPalm OS Garnet 5.2.8CPU200 MHz Intel Xscale PXA255 Processor (ARM v5TE)Memory16 Mi B: 13.. 8 MiB User - 1 Dynamic Heap MiB)Display160×160 pixels 4096 colors (12 bits) CSTN displayInputGraffiti 2 input zone - TouchscreenivityInfrared, USBPower900 mAh rechargeable built-in lithium polymer batteryMass4.8 oz. / 136.1 grams (portable stylus) zier 31 is a zira portable from palmOne. The product was first released in April 2004 as a replacement for the zira 21. It runs the Palm OS 5.2.8 and has a 160×160 color display, an SDIO slot and a standard 3.5mm stereo headphone jack. Improved PIM apps (calendar, contacts, tasks, and memos) are available. Rom includes the RealOne Player, giving the device some digital audio player capabilities. They can be expanded using third party software such as TCPMP. The zier 31 has a 5-way navigator pad, but still only 2 quickbuttons, as opposed to the standard 4 on the mid-range of 71/72. It has been replaced by No22, which lacks an SD/MMC/SDIO extension and a headphone jack. 200 MHz specifications Intel Xscale PXA255 Processor (ARM v5TE) 200 MHz Memory 16 MiB RAM (13.8 MiB actual storage and 1 MiB heaps) Battery rechargeable lithium polymer 900mAh battery operating system Palm v OS5.8 Size 4.6 inch / 11.2 cm × 8 3.0 inch/7.4 cm per × 0.7 inches/1.6 cm thick inch Weight 4.8 ounces/136.1 grams (portable stylus) Display 160×160 pixels 4096 colors (12 bits) CSTN Display Display 1GB max SD, S and MMC through support slot extension card. -

3M Company (MMM)
COMPANY PROFILES 2008 The Research Group of Godsey & Gibb Associates compiled the following information in Godsey & Gibb Associates’ 2008 Company Profiles from Reuters’ Company Profiles. These reports are intended solely for the clients of Godsey & Gibb Associates and its affiliates. This material is for informational purposes only and is not intended to be a recommendation for the purchase or sale of any individual security. GODSEY & GIBB COMPANY PROFILES 2008 TABLE OF CONTENTS AFLAC Inc. (AFL)………………………………………………………………………………………. 1 AGL Resources Inc. (ATG)…………………………………………………………………………… 3 American Electric Power Co. Inc. (AEP)….………………………………………………………… 5 AT&T, Inc (T)…………………………………………………………………………………………… 7 Barrick Gold Corp. (ABX)……………………….……………………………………………………. 9 BB&T Corp. (BBT)………………………………………………………………..…………………… 10 BP, plc (BP)…………………………………………………………………………………….………. 12 Cisco Systems, Inc. (CSCO)……………………………………………………………….………… 13 Cognizant Technology Solutions (CTSH)……………………………………………………….….. 15 CVS Caremark Corp. (CVS)………………………………………………………………………….. 16 Dominion Resources, Inc. (D)………………………………………………….…………………….. 17 Emerson Electric Co. (EMR)………………………………………………………………………….. 19 Express Scripts, Inc. (ESRX)…………………………………………………………………..……… 23 ExxonMobil Corp. (XOM)………………………………………………………………….…………… 24 General Electric Company (GE)………………………………………………………………..……. 26 Gilead Sciences, Inc. (GILD)…………………………………………………………………………. 27 W.W. Grainger, Inc. (GWW)………………………………………………………………………….. 30 Hewlett-Packard Co. (HPQ)………………………………………………………………………….. 32 Integrys Energy Group, -

ANNUAL REPORT PURSUANT to SECTION 13 OR 15 (D) of THE
UNITED STATES SECURITIES AND EXCHANGE COMMISSION Washington, D.C. 20549 FORM 10-K (Mark One) ፤ ANNUAL REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the fiscal year ended: October 31, 2008 Or អ TRANSITION REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the transition period from to Commission file number 1-4423 HEWLETT-PACKARD COMPANY (Exact name of registrant as specified in its charter) Delaware 94-1081436 (State or other jurisdiction of (I.R.S. employer incorporation or organization) identification no.) 3000 Hanover Street, Palo Alto, California 94304 (Address of principal executive offices) (Zip code) Registrant’s telephone number, including area code: (650) 857-1501 Securities registered pursuant to Section 12(b) of the Act: Title of each class Name of each exchange on which registered Common stock, par value $0.01 per share New York Stock Exchange Securities registered pursuant to Section 12(g) of the Act: None Indicate by check mark if the registrant is a well-known seasoned issuer as defined in Rule 405 of the Securities Act. Yes No អ Indicate by check mark if the registrant is not required to file reports pursuant to Section 13 or Section 15(d) of the Act. Yes No ፤ Indicate by check mark whether the registrant (1) has filed all reports required to be filed by Section 13 or 15(d) of the Securities Exchange Act of 1934 (the ‘‘Exchange Act’’) during the preceding 12 months (or for such shorter period that the registrant was required to file such reports), and (2) has been subject to such filing requirements for the past 90 days. -

1 Star Trac Pro Partner – Training Partner Operations Manual Table of Contents I. Introduction II. Selecting Workout Partner
Star Trac Pro Partner – Training Partner Operations Manual Table of Contents I. Introduction II. Selecting Workout Partner a. Creating a Custom Workout III. Creating a Pro or Elite Treadmill Custom Workout a. Naming Your Workout b. Entering Weight/Time c. Designing Your Incline Profile d. Designing Your Speed Profile IV. Creating a Pro Bike Custom Workout a. Naming Your Workout b. Entering Weight/Time c. Designing Your Resistance Profile V. Accessing a Custom Workout VI. Beaming a Custom Workout a. Beaming to a Pro or Elite Treadmill b. Beaming to a Pro Bike c. Beaming to a PDA Device VII. Editing a Custom Workout VIII. Deleting a Custom Workout IX. Reviewing a Completed Workout X. Collecting an Existing Workout from a Pro or Elite Treadmill or Pro Bike XI. Appendix A: List of PDAs Compatible with Pro Partner 1 I. Introduction Thank you for choosing Star Trac for your fitness needs. Are you ready to take your clients’ workout to a new level? The Star Trac Pro Partner software program will make your Palm-powered PDA (Personal Digital Assistant) an integral part of your personal training experience when using a Star Trac Pro or Elite Treadmill or Pro Bike. Personalized workouts and tracking client workout data are now all in the palm of your hand! In this manual you will learn how to use the Training Partner application to design custom workouts and track workout information for your clients for a more personal approach. It’s simple! Just follow the steps in this user manual and you’re one step closer to making your personal training more efficient. -
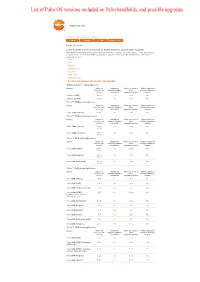
List of Palm OS Versions Included on Palm Handhelds, and Possible Upgrades
List of Palm OS versions included on Palm handhelds, and possible upgrades www.palm.com < Home < Support < Knowledge Library Article ID: 10714 List of Palm OS versions included on Palm handhelds, and possible upgrades Palm OS® is the operating system that drives Palm devices. In some cases, it may be possible to update your device with ROM upgrades or patches. Find your device below to see what's available for you: Centro Treo LifeDrive Tungsten, T|X Zire, Z22 Palm (older) Handspring Visor Questions & Answers about Palm OS upgrades Palm Centro™ smartphone Device Palm OS Handheld Palm OS version Palm Desktop & version (out- Upgrade/Update after HotSync Manager of-box) available? upgrade/update update Centro (AT&T) 5.4.9 No N/A No Centro (Sprint) 5.4.9 No N/A No Treo™ 755p smartphone Device Palm OS Handheld Palm OS version Palm Desktop & version (out- Upgrade/Update after HotSync Manager of-box) available? upgrade/update update Treo 755p (Sprint) 5.4.9 No N/A No Treo™ 700p smartphones Device Palm OS Handheld Palm OS version Palm Desktop & version (out- Upgrade/Update after HotSync Manager of-box) available? upgrade/update update Treo 700p (Sprint) Garnet Yes N/A No 5.4.9 Treo 700p (Verizon) Garnet No N/A No 5.4.9 Treo™ 680 smartphones Device Palm OS Handheld Palm OS version Palm Desktop & version (out- Upgrade/Update after HotSync Manager of-box) available? upgrade/update update Treo 680 (AT&T) Garnet Yes 5.4.9 No 5.4.9 Treo 680 (Rogers) Garnet No N/A No 5.4.9 Treo 680 (Unlocked) Garnet No N/A No 5.4.9 Treo™ 650 smartphones Device Palm OS -

Choose the Lockbox Key That's Right for You!
GE Supra Security Choose the lockbox key that’s right for you! Supra offers alternatives to the DisplayKEY so that you can customize your lockbox key to match your workstyle! Now you can use a smart phone or PDA to open your iBoxes. Do you want to use a smart phone as your lockbox key? With a smart phone, you carry one device that does it all ― cell phone, organizer, and lockbox key. Your key is renewed automatically in the middle of the night through a wireless connection without the use of a cradle. MLS and showing information can also be downloaded. These are the smart phones you can choose from and the wireless carriers that support them. Information and key renewals are delivered wirelessly. • Treo 650 ― Cingular, Sprint, Verizon, SunCom Wireless • Treo 600 ― Cingular, Sprint, T-Mobile, Verizon, Cellular One of Amarillo • Samsung i500 ― Sprint • Kyocera 7135 (must contain firmware version MZ1.0.44 / SZ1.0.29 or newer)― Verizon, Alltel Treo 650 • Treo 300 ― Sprint • Treo 270 ― Cingular, T-Mobile • Tungsten W ― Cingular If you do not already have one of the above smart phones, contact your wireless carrier to obtain one. A voice and data service plan is also required for wireless updates when using a smart phone as your lockbox key. eSYNC Connection Options for Your Smart Phone There are two ways to eSYNC your smart phone: wirelessly, or through your computer. Your smart phone comes with a factory-shipped cradle or cable. Save wireless minutes by downloading update codes and/or MLS information using the cradle or cable connected to your computer through the Internet. -

Zire 31 User Guide
User Guide User Guide Cover Copyright and Trademark © 2004-2006 palmOne, Inc. All rights reserved. palmOne, the palmOne logo, Zire, the Zire logo, “Z” (Stylized) and stylizations and design marks associated with all the preceding, and trade dress associated with palmOne, Inc.’s products, are among the trademarks or registered trademarks owned by or licensed to palmOne, Inc. or its subsidiaries. Palm OS, the Palm logo, Graffiti, HotSync, Palm, Palm Reader, the HotSync logo and the Palm and PalmSource trade dress are trademarks owned by or licensed to PalmSource, Inc. palmOne, Inc. uses the MPEG Layer-3 audio decoding technology trademarks under express license from Thomson Licensing S.A. All other brand and product names are or may be trademarks of, and are used to identify products or services of, their respective owners. This product includes technology owned by Microsoft Corporation and cannot be used or distributed without a license from Microsoft Licensing, GP. Disclaimer and Limitation of Liability palmOne, Inc. assumes no responsibility for any damage or loss resulting from the use of this guide. palmOne, Inc. assumes no responsibility for any loss or claims by third parties which may arise through the use of this software. palmOne, Inc. assumes no responsibility for any damage or loss caused by deletion of data as a result of malfunction, dead battery, or repairs. Be sure to make backup copies of all important data on other media to protect against data loss. [ ! ] IMPORTANT Please read the End User Software License Agreement with this product before using the accompanying software program(s). Using any part of the software indicates that you accept the terms of the End User Software License Agreement. -

Noviiremote Deluxe for Palm OS ®, Ver 3.5 User's Guide
__________________________________________________________ For Palm OS Devices NoviiRemote turns your handheld computer into a Universal Learning Remote Control! You can control all of your home entertainment equipment with one easy-to-use program. Table of Contents Introduction ...............................................................................................................................2 1. Getting Started......................................................................................................................2 2. Install NoviiRemote Deluxe...................................................................................................3 3. Setup Form ...........................................................................................................................4 4. Remote Screen Form............................................................................................................5 5. Add New Device Wizard .......................................................................................................7 6. Learning IR Codes................................................................................................................8 7. Hot Buttons Form................................................................................................................10 8. Hard Buttons Form .............................................................................................................12 9. Preferences for Multiple Rooms..........................................................................................14 -
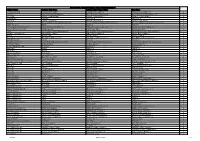
Software Use Analyses Software Catalog 22
IBM TEM SUA Software Catalog - Newly Added Applications Catalog Publisher Name Software Title Name Software Title Version Name App Name Version ACD Systems Ltd. ACDSee Photo Editor ACDSee Photo Editor 4 ACDSee Photo Editor 4.0 2 Acer Inc. Acer eRecovery Management Acer eRecovery Management 2 Acer eRecovery Management 2.0 2 acs39 Ltd. Science Toolbox Demo Science Toolbox Demo 1 Science Toolbox Demo 1 2 activePDF Inc. PrimoPDF PrimoPDF 4 PrimoPDF 4 2 Activision Ultimate Spiderman Ultimate Spiderman 1 Ultimate Spiderman 1 2 Actuate Actuate e.Report Designer Professional Actuate e.Report Designer Professional 7 Actuate e.Report Designer Professional 7 2 ADINA R & D Inc. ADINA ADINA 8 ADINA 8 2 Adobe Systems Incorporated Adobe Photoshop Lightroom Adobe Photoshop Lightroom 1 Adobe Photoshop Lightroom 1 2 Advanced Geosciences Inc. EarthImager 2D EarthImager 2D 2 EarthImager 2D 2 2 Ageia AGEIA PhysX Boxes Demonstration AGEIA PhysX Boxes Demonstration 2 AGEIA PhysX Boxes Demonstration 2 2 Agilent Technologies Inc. Agilent Data Capture Agilent Data Capture 2 Agilent Data Capture 2 2 AICPCU AICPCU Exam AICPCU Exam 4 AICPCU Exam 4 2 Aide CAD Systems Incorporated Aide PDF to DXF Converter Aide PDF to DXF Converter 6 Aide PDF to DXF Converter 6 2 Alden Group Ltd. Xassist Xassist 1 Xassist 1 2 ALeadSoft.com Inc. Search Engine Builder Professional Search Engine Builder Professional 2 Search Engine Builder Professional 2.0 2 Alentum Software WebLog Expert WebLog Expert 3 WebLog Expert 3 2 AlfaSoft Research Labs AlfaClock AlfaClock 1 AlfaClock 1 2 ALGOR Inc. ALGOR ALGOR 14 ALGOR 14 2 ALGOR Inc. -

Palmfahrschule
PalmFahrSchule Anhang A - Geräteliste verschiedener Hersteller Palm (Handhelds) OS Version Speicher Kompatibel Palm Pilot 1000 Palm OS 1.0 128 Kb nein Palm Pilot 5000 Palm OS 1.0 512 Kb nein Palm Pilot Personal Palm OS 1.0 512 Kb nein Palm Pilot Professional Palm OS 2.0 2 Mb nein Palm III Palm OS 3.0 2 Mb nein Palm IIIc Palm OS 3.5 8 Mb Palm IIIe Palm OS 3.3 2 Mb nein Palm IIIx Palm OS 3.1 4 Mb nein Palm IIIxe Palm OS 3.5 8 Mb Palm V Palm OS 3.0.1 / 3.1 2 Mb nein Palm Vx Palm OS 3.5 8 Mb Palm VII Palm OS 3.2 2 Mb nein Palm VIIx Palm OS 3.3 / 3.5 / 3.5.3 8 Mb nein Palm m100 Palm OS 3.5 2 Mb Palm m105 Palm OS 3.5.1 8 Mb Palm m125 Palm OS 4.0 8 Mb Palm m130 Palm OS 4.0/4.1 8 Mb Palm m500 Palm OS 4.0 8 Mb Palm m505 Palm OS 4.0 / 4.1 8 Mb Palm m515 Palm OS 4.1 16 Mb Palm i705 Palm OS 4.1 8 Mb Zire Palm OS 4.1 2 Mb Zire 119 ? Zire m150 Palm OS 4.1 2 Mb Zire 21 Palm OS 5.2.8 8 Mb Zire 31 Palm OS 5.2.8 16 Mb Zire 71 Palm OS 5.2.1 16 Mb (14 Mb nutzbare Kapazität) Zire 72 Palm OS 5.2.8 32 Mb (24 Mb nutzbare Kapazität) Palm Z22 Palm OS Garnet 5.4.9 32 Mb (20 Mb nutzbare Kapazität) Palm T|X Handheld (tx) Palm OS 5.4.9 128 Mb Flash-RAM, ca.