Bigfix Inventory Open Source Licenses and Notices
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Ruby Best Practices.Pdf
Ruby Best Practices Ruby Best Practices Gregory Brown foreword by Yukihiro “Matz” Matsumoto Beijing • Cambridge • Farnham • Köln • Sebastopol • Taipei • Tokyo Ruby Best Practices by Gregory Brown Copyright © 2009 Gregory Brown. All rights reserved. Printed in the United States of America. Published by O’Reilly Media, Inc., 1005 Gravenstein Highway North, Sebastopol, CA 95472. O’Reilly books may be purchased for educational, business, or sales promotional use. Online editions are also available for most titles (http://my.safaribooksonline.com). For more information, contact our corporate/institutional sales department: 800-998-9938 or [email protected]. Editor: Mike Loukides Indexer: Ellen Troutman Zaig Production Editor: Sarah Schneider Cover Designer: Karen Montgomery Copyeditor: Nancy Kotary Interior Designer: David Futato Proofreader: Sada Preisch Illustrator: Robert Romano Printing History: June 2009: First Edition. O’Reilly and the O’Reilly logo are registered trademarks of O’Reilly Media, Inc. Ruby Best Practices, the image of a green crab, and related trade dress are trademarks of O’Reilly Media, Inc. Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. Where those designations appear in this book, and O’Reilly Media, Inc. was aware of a trademark claim, the designations have been printed in caps or initial caps. While every precaution has been taken in the preparation of this book, the publisher and author assume no responsibility for errors or omissions, or for damages resulting from the use of the information con- tained herein. In March 2010, this work will be released under the Creative Commons Attribution- Noncommercial-Share Alike 3.0 License. -

X-XSS- Protection
HTTP SECURITY HEADERS (Protection For Browsers) BIO • Emmanuel JK Gbordzor ISO 27001 LI, CISA, CCNA, CCNA-Security, ITILv3, … 11 years in IT – About 2 years In Security Information Security Manager @ PaySwitch Head, Network & Infrastructure @ PaySwitch Head of IT @ Financial Institution Bug bounty student by night – 1st Private Invite on Hackerone Introduction • In this presentation, I will introduce you to HyperText Transfer Protocol (HTTP) response security headers. • By specifying expected and allowable behaviors, we will see how security headers can prevent a number of attacks against websites. • I’ll explain some of the different HTTP response headers that a web server can include in a response, and what impact they can have on the security of the web browser. • How web developers can implement these security headers to make user experience more secure A Simple Look At Web Browsing Snippet At The Request And Response Headers Browser Security Headers help: ➢ to define whether a set of security precautions should be activated or Why deactivated on the web browser. ➢ to reinforce the security of your web Browser browser to fend off attacks and to mitigate vulnerabilities. Security ➢ in fighting client side (browser) attacks such as clickjacking, Headers? injections, Multipurpose Internet Mail Extensions (MIME) sniffing, Cross-Site Scripting (XSS), etc. Content / Context HTTP STRICT X-FRAME-OPTIONS EXPECT-CT TRANSPORT SECURITY (HSTS) CONTENT-SECURITY- X-XSS-PROTECTION X-CONTENT-TYPE- POLICY OPTIONS HTTP Strict Transport Security (HSTS) -

Software Package Licenses
DAVIX 1.0.0 Licenses Package Version Platform License Type Package Origin Operating System SLAX 6.0.4 Linux GPLv2 SLAX component DAVIX 0.x.x Linux GPLv2 - DAVIX Manual 0.x.x PDF GNU FDLv1.2 - Standard Packages Font Adobe 100 dpi 1.0.0 X Adobe license: redistribution possible. Slackware Font Misc Misc 1.0.0 X Public domain Slackware Firefox 2.0.0.16 C Mozilla Public License (MPL), chapter 3.6 and Slackware 3.7 Apache httpd 2.2.8 C Apache License 2.0 Slackware apr 1.2.8 C Apache License 2.0 Slackware apr-util 1.2.8 C Apache License 2.0 Slackware MySQL Client & Server 5.0.37 C GPLv2 Slackware Wireshark 1.0.2 C GPLv2, pidl util GPLv3 Built from source KRB5 N/A C Several licenses: redistribution permitted dropline GNOME: Copied single libraries libgcrypt 1.2.4 C GPLv2 or LGPLv2.1 Slackware: Copied single libraries gnutls 1.6.2 C GPLv2 or LGPLv2.1 Slackware: Copied single libraries libgpg-error 1.5 C GPLv2 or LGPLv2.1 Slackware: Copied single libraries Perl 5.8.8 C, Perl GPL or Artistic License SLAX component Python 2.5.1 C, PythonPython License (GPL compatible) Slackware Ruby 1.8.6 C, Ruby GPL or Ruby License Slackware tcpdump 3.9.7 C BSD License SLAX component libpcap 0.9.7 C BSD License SLAX component telnet 0.17 C BSD License Slackware socat 1.6.0.0 C GPLv2 Built from source netcat 1.10 C Free giveaway with no restrictions Slackware GNU Awk 3.1.5 C GPLv2 SLAX component GNU grep / egrep 2.5 C GPLv2 SLAX component geoip 1.4.4 C LGPL 2.1 Built from source Geo::IPfree 0.2 Perl This program is free software; you can Built from source redistribute it and/or modify it under the same terms as Perl itself. -

Open Source Software As Intangible Capital: Measuring the Cost and Impact of Free Digital Tools Preliminary Draft October 31, 20181 Carol A
Open Source Software as Intangible Capital: Measuring the Cost and Impact of Free Digital Tools Preliminary Draft October 31, 20181 Carol A. Robbins*(1), Gizem Korkmaz (2), José Bayoán Santiago Calderón (3), Daniel Chen (2), Claire Kelling (4) , Stephanie Shipp (2), Sallie Keller (2) Abstract Open source software is everywhere, both as specialized applications nurtured by devoted user communities, and as digital infrastructure underlying platforms used by millions daily, yet its value and impact are not currently measured (with small exceptions). We develop an approach to document the scope and impact of open source software created by all sectors of the economy: businesses, universities, government research institutions, nonprofits, and individuals. We use a bottom-up approach to measure subset of OSS projects and languages, collecting data on open source software languages R, Python, Julia, and JavaScript, as well as from the Federal Government’s code.gov website. Using lines of code and a standard model to estimate package developer time, we convert lines of code to resource cost. We estimate that the resource cost for developing R, Python, Julia, and JavaScript exceeds $3 billion dollars, based on 2017 costs. Applying this approach to open source software available on code.gov results in an estimated value of more than $1 billion, based on 2017 costs, as a lower bound for the resource cost of this software. We analyze the dependencies between software packages through network analysis and estimate re-use statistics. This reuse is one measure of relative impact. Key words: Open Source Software, Intangibles, Network Analysis National Center for Science and Engineering Statistics, National Science Foundation; 2) Social & Decision Analytics Division, Biocomplexity Institute & Initiative, University of Virginia; 3) Claremont Graduate University; 4) Pennsylvania State University 1 An earlier version of this paper was presented August 21, 2018 at the International Association for Research on Income and Wealth. -

Identifying Javascript Skimmers on High-Value Websites
Imperial College of Science, Technology and Medicine Department of Computing CO401 - Individual Project MEng Identifying JavaScript Skimmers on High-Value Websites Author: Supervisor: Thomas Bower Dr. Sergio Maffeis Second marker: Dr. Soteris Demetriou June 17, 2019 Identifying JavaScript Skimmers on High-Value Websites Thomas Bower Abstract JavaScript Skimmers are a new type of malware which operate by adding a small piece of code onto a legitimate website in order to exfiltrate private information such as credit card numbers to an attackers server, while also submitting the details to the legitimate site. They are impossible to detect just by looking at the web page since they operate entirely in the background of the normal page operation and display no obvious indicators to their presence. Skimmers entered the public eye in 2018 after a series of high-profile attacks on major retailers including British Airways, Newegg, and Ticketmaster, claiming the credit card details of hundreds of thousands of victims between them. To date, there has been little-to-no work towards preventing websites becoming infected with skimmers, and even less so for protecting consumers. In this document, we propose a novel and effective solution for protecting users from skimming attacks by blocking attempts to contact an attackers server with sensitive information, in the form of a Google Chrome web extension. Our extension takes a two-pronged approach, analysing both the dynamic behaviour of the script such as outgoing requests, as well as static analysis by way of a number of heuristic techniques on scripts loaded onto the page which may be indicative of a skimmer. -

An Empirical Study of the Use of Integrity Verification Mechanisms
An Empirical Study of the Use of Integrity Verification Mechanisms for Web Subresources Bertil Chapuis, Olamide Omolola, Mauro Cherubini, Mathias Humbert, Kévin Huguenin To cite this version: Bertil Chapuis, Olamide Omolola, Mauro Cherubini, Mathias Humbert, Kévin Huguenin. An Empiri- cal Study of the Use of Integrity Verification Mechanisms for Web Subresources. The Web Conference (WWW), Apr 2020, Taipei, Taiwan. pp.34-45, 10.1145/3366423.3380092. hal-02435688 HAL Id: hal-02435688 https://hal.archives-ouvertes.fr/hal-02435688 Submitted on 20 Jan 2020 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. An Empirical Study of the Use of Integrity Verification Mechanisms for Web Subresources Bertil Chapuis Olamide Omolola Mauro Cherubini UNIL – HEC Lausanne TU Graz UNIL – HEC Lausanne Switzerland Austria Switzerland [email protected] [email protected] [email protected] Mathias Humbert Kévin Huguenin armasuisse S+T UNIL – HEC Lausanne Switzerland Switzerland [email protected] [email protected] ABSTRACT 1 INTRODUCTION Web developers can (and do) include subresources such as scripts, The Web is a set of interlinked resources identied by their URLs. stylesheets and images in their webpages. -

Phonegap and Angularjs for Cross-Platform Development
www.allitebooks.com PhoneGap and AngularJS for Cross-platform Development Build exciting cross-platform applications using PhoneGap and AngularJS Yuxian, Eugene Liang BIRMINGHAM - MUMBAI www.allitebooks.com PhoneGap and AngularJS for Cross-platform Development Copyright © 2014 Packt Publishing All rights reserved. No part of this book may be reproduced, stored in a retrieval system, or transmitted in any form or by any means, without the prior written permission of the publisher, except in the case of brief quotations embedded in critical articles or reviews. Every effort has been made in the preparation of this book to ensure the accuracy of the information presented. However, the information contained in this book is sold without warranty, either express or implied. Neither the author, nor Packt Publishing, and its dealers and distributors will be held liable for any damages caused or alleged to be caused directly or indirectly by this book. Packt Publishing has endeavored to provide trademark information about all of the companies and products mentioned in this book by the appropriate use of capitals. However, Packt Publishing cannot guarantee the accuracy of this information. First published: October 2014 Production reference: 1241014 Published by Packt Publishing Ltd. Livery Place 35 Livery Street Birmingham B3 2PB, UK. ISBN 978-1-78398-892-1 www.packtpub.com Cover image by Aniket Sawant ([email protected]) [ FM-2 ] www.allitebooks.com Credits Author Project Coordinator Yuxian, Eugene Liang Kartik Vedam Reviewers Proofreaders Simon Basset Maria Gould Razi Mahmood Elinor Perry-Smith Commissioning Editor Indexers Kunal Parikh Monica Ajmera Mehta Tejal Soni Acquisition Editor Meeta Rajani Production Coordinators Kyle Albuquerque Content Development Editor Nilesh R. -

Inference and Regeneration of Programs That Store and Retrieve Data Martin Rinard and Jiasi Shen
Computer Science and Artificial Intelligence Laboratory Technical Report MIT-CSAIL-TR-2017-006 April 24, 2017 Inference and Regeneration of Programs that Store and Retrieve Data Martin Rinard and Jiasi Shen massachusetts institute of technology, cambridge, ma 02139 usa — www.csail.mit.edu Inference and Regeneration of Programs that Store and Retrieve Data Martin Rinard Jiasi Shen EECS & CSAIL EECS & CSAIL MIT MIT [email protected] [email protected] Abstract networked, distributed computing platforms. A common As modern computation platforms become increasingly com- scenario, for example, is for a program to compute over data plex, their programming interfaces are increasingly dicult stored across many machines in a cloud computing environ- to use. is complexity is especially inappropriate given the ment to generate results that are then distributed via the relatively simple core functionality that many of the compu- Internet for graphical presentation on remote devices. tations implement. We present a new approach for obtaining Modern soware environments rely heavily on soware soware that executes on modern computing platforms with packages that help developers deal with the resulting com- complex programming interfaces. Our approach starts with plexity. Examples include application server frameworks a simple seed program, wrien in the language of the devel- such as JBoss and IBM WebSphere, key/value storage sys- oper’s choice, that implements the desired core functionality. tems such as Redis, NoSQL databases such as HBase, dis- It then systematically generates inputs and observes the re- tributed memory caching systems such as memcached, and sulting outputs to learn the core functionality. It nally auto- cluster computing frameworks such as Spark and MapRe- matically regenerates new code that implements the learned duce. -
How to Download Older Version of Ruby Get Ruby on Rails in No Time
how to download older version of ruby Get Ruby on Rails in no time. We recommend Ruby 2.2 or newer for use with Rails. Rails requires Ruby 1.9.3 or newer. Source: Compile it yourself Windows installer: Ruby, popular extensions, editor OS X 10.5+: Included with developer tools (then do gem update rails ) We recommend managing your Ruby installation through rbenv. It’s an easy way to run multiple versions for different applications and update when a new release is made. Rails. With Ruby installed, you can install all of Rails and its dependencies through RubyGems on the command line: New versions of Rails can be installed the same way. Make your application. Create your application skeleton and start the server: You’re running Ruby on Rails! Follow the instructions on http://localhost:3000. Editors. TextMate on OS X has long been the favored Rails editor, but the classic editors are still going strong. See VIM for Rails and Emacs for Rails. For a full-on IDE, check out JetBrains RubyMine. “Rails”, “Ruby on Rails”, and the Rails logo are registered trademarks of David Heinemeier Hansson. All rights reserved. Download Ruby. Here you can get the latest Ruby distributions in your favorite flavor. The current stable version is 3.0.2. Please be sure to read Ruby’s License. Ways of Installing Ruby. We have several tools on each major platform to install Ruby: On Linux/UNIX, you can use the package management system of your distribution or third-party tools (rbenv and RVM). On macOS machines, you can use third-party tools (rbenv and RVM). -

Dell EMC Powerstore Open Source License and Copyright Information
Open Source License and Copyright Information Dell EMC PowerStore Open Source License and Copyright Information June 2021 Rev A04 Revisions Revisions Date Description May 2020 Initial release September 2020 Version updates for some licenses and addition of iwpmd component December 2020 Version updates for some licenses, and addition and deletion of other components January 2021 Version updates for some licenses June 2021 Version updates for some licenses, and addition and deletion of other components The information in this publication is provided “as is.” Dell Inc. makes no representations or warranties of any kind with respect to the information in this publication, and specifically disclaims implied warranties of merchantability or fitness for a particular purpose. Use, copying, and distribution of any software described in this publication requires an applicable software license. Copyright © 2020-2021 Dell Inc. or its subsidiaries. All Rights Reserved. Dell Technologies, Dell, EMC, Dell EMC and other trademarks are trademarks of Dell Inc. or its subsidiaries. Other trademarks may be trademarks of their respective owners. [6/1/2021] [Open Source License and Copyright Information] [Rev A04] 2 Dell EMC PowerStore: Open Source License and Copyright Information Table of contents Table of contents Revisions............................................................................................................................................................................. 2 Table of contents ............................................................................................................................................................... -

07. 1957-2007: 50 Years of Higher Order Programming Languages
JIOS, V OL . 33, N O. 1 (2009) SUBMITTED 10/08; A CCEPTED 02/09 UDC 004.432 Review Paper 1957-2007: 50 Years of Higher Order Programming Languages Alen Lovren ciˇ c´ [email protected] University of Zagreb Faculty of Organization and Informatics Mario Konecki [email protected] University of Zagreb Faculty of Organization and Informatics Tihomir Orehova ckiˇ [email protected] University of Zagreb Faculty of Organization and Informatics Abstract Fifty years ago one of the greatest breakthroughs in computer programming and in the history of computers happened – the appearance of FORTRAN, the first higher-order programming lan- guage. From that time until now hundreds of programming languages were invented, different programming paradigms were defined, all with the main goal to make computer programming easier and closer to as many people as possible. Many battles were fought among scientists as well as among developers around concepts of programming, programming languages and paradigms. It can be said that programming paradigms and programming languages were very often a trigger for many changes and improvements in computer science as well as in computer industry. Definitely, computer programming is one of the cornerstones of computer science. Today there are many tools that give a help in the process of programming, but there is still a programming tasks that can be solved only manually. Therefore, programming is still one of the most creative parts of interaction with computers. Programmers should chose programming language in accordance to task they have to solve, but very often, they chose it in accordance to their personal preferences, their beliefs and many other subjective reasons. -
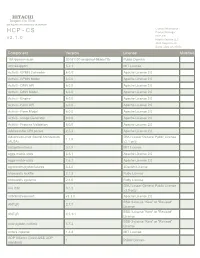
HCP - CS Product Manager HCP-CS V 2
HITACHI Inspire the Next 2535 Augustine Drive Santa Clara, CA 95054 USA Contact Information : HCP - CS Product Manager HCP-CS v 2 . 1 . 0 Hitachi Vantara LLC 2535 Augustine Dr. Santa Clara CA 95054 Component Version License Modified 18F/domain-scan 20181130-snapshot-988de72b Public Domain activesupport 5.2.1 MIT License Activiti - BPMN Converter 6.0.0 Apache License 2.0 Activiti - BPMN Model 6.0.0 Apache License 2.0 Activiti - DMN API 6.0.0 Apache License 2.0 Activiti - DMN Model 6.0.0 Apache License 2.0 Activiti - Engine 6.0.0 Apache License 2.0 Activiti - Form API 6.0.0 Apache License 2.0 Activiti - Form Model 6.0.0 Apache License 2.0 Activiti - Image Generator 6.0.0 Apache License 2.0 Activiti - Process Validation 6.0.0 Apache License 2.0 Addressable URI parser 2.5.2 Apache License 2.0 Advanced Linux Sound Architecture GNU Lesser General Public License 1.1.8 (ALSA) v2.1 only adzap/timeliness 0.3.8 MIT License aggs-matrix-stats 5.5.1 Apache License 2.0 aggs-matrix-stats 7.6.2 Apache License 2.0 agronholm/pythonfutures 3.3.0 3Delight License ahoward's lockfile 2.1.3 Ruby License ahoward's systemu 2.6.5 Ruby License GNU Lesser General Public License ai's r18n 3.1.2 v3.0 only airbnb/streamalert v3.3.0 Apache License 2.0 BSD 3-clause "New" or "Revised" ANTLR 2.7.7 License BSD 3-clause "New" or "Revised" ANTLR 4.5.1-1 License BSD 3-clause "New" or "Revised" antlr-python-runtime 4.7.2 License antw's iniparse 1.4.4 MIT License AOP Alliance (Java/J2EE AOP 1 Public Domain standard) HITACHI Inspire the Next 2535 Augustine Drive Santa Clara, CA