Mobile Device Manager
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

2014 BT Compatibility List 20141030
Item Brand Name Model 1 Acer Acer beTouch E210 2 Acer acer E400 3 Acer acer P400 4 Acer DX650 5 Acer E200 6 Acer Liquid E 7 Acer Liquid Mini (E310) 8 Acer M900 9 Acer S110 10 Acer Smart handheld 11 Acer Smart handheld 12 Acer Smart handheld E100 13 Acer Smart handheld E101 14 Adec & Partner AG AG vegas 15 Alcatel Alcatel OneTouch Fierce 2 16 Alcatel MISS SIXTY MSX10 17 Alcatel OT-800/ OT-800A 18 Alcatel OT-802/ OT-802A 19 Alcatel OT-806/ OT-806A/ OT-806D/ OT-807/ OT-807A/ OT-807D 20 Alcatel OT-808/ OT-808A 21 Alcatel OT-880/ OT-880A 22 Alcatel OT-980/ OT-980A 23 Altek Altek A14 24 Amazon Amazon Fire Phone 25 Amgoo Telecom Co LTD AM83 26 Apple Apple iPhone 4S 27 Apple Apple iPhone 5 28 Apple Apple iPhone 6 29 Apple Apple iPhone 6 Plus 30 Apple iPhone 2G 31 Apple iPhone 3G 32 Apple iPhone 3Gs 33 Apple iPhone 4 34 Apple iPhone 5C 35 Apple iPHone 5S 36 Aramasmobile.com ZX021 37 Ascom Sweden AB 3749 38 Asustek 1000846 39 Asustek A10 40 Asustek G60 41 Asustek Galaxy3_L and Galaxy3_S 42 Asustek Garmin-ASUS M10E 43 Asustek P320 44 Asustek P565c 45 BlackBerry BlackBerry Passport 46 BlackBerry BlackBerry Q10 47 Broadcom Corporation BTL-A 48 Casio Hitachi C721 49 Cellnet 7 Inc. DG-805 Cellon Communications 50 C2052, Technology(Shenzhen) Co., Ltd. Cellon Communications 51 C2053, Technology(Shenzhen) Co., Ltd. Cellon Communications 52 C3031 Technology(Shenzhen) Co., Ltd. Cellon Communications 53 C5030, Technology(Shenzhen) Co., Ltd. -

Reporting Period: July 1, 2013 – June 30, 2014
Device Manufacturers Information by Handset Reporting Period: July 1, 2013 – June 30, 2014 Starting Ending Operating Frequency M- M-Rating M-Rating T-Rating T-Rating Handset Maker Model Name (s) FCC ID (s) Date Date Air Interface Technology(ies) Bands Rating Cert Date ANSI Version T-Rating Cert Date ANSI Remarks (1) M3 rating for the 1900 MHz GSM band uses the Section 20.19(e)(1)(iii) power reduction option, 47 C.F.R. Sec. 20.19(e)(1)(iii), and requires activation of Hearing Aid Mode in iOS 5 or later. (2) iPhone 4 (A1332) supports additional frequency bands BCG-E2380A, BCG- GSM, WCDMA, GSM, WCDMA, 850, 850, 1900, 1900, that do not operate in U.S. territories and that were not Apple iPhone 4 (A1332) E2380B 07/ 13 09/ 13 Wi-Fi 2.4 M3 10/04/11 2007 T3 10/04/11 2007 certified under U.S. HAC rules. BCG-E2422A, BCG- Apple iPhone 4 (A1349) E2422B 07/ 13 09/ 13 CDMA, CDMA, Wi-Fi 800, 1900, 2.4 M4 01/20/11 2007 T4 01/20/11 2007 N/A (1) iPhone 4S is compatible with Made for iPhone hearing aids. (2) CDMA available only if iPhone 4S is sold and activated for use on a CDMA network. (3) iPhone 4S supports additional frequency bands that do CDMA, GSM, WCDMA, GSM, 800, 850, 850, 1900, not operate in U.S. territories and that were not certified Apple iPhone 4S (A1387) BCG-E2430A 07/ 13 06/ 14 CDMA, WCDMA, Wi-Fi 1900, 1900, 2.4 N/A N/A N/A N/A N/A N/A under U.S. -

Case 5:18-Cv-06739-VKD Document 27 Filed 07/02/18 Page 1 of 11
Case 5:18-cv-06739-VKD Document 27 Filed 07/02/18 Page 1 of 11 IN THE UNITED STATES DISTRICT COURT FOR THE NORTHERN DISTRICT OF TEXAS DALLAS DIVISION § UNILOC USA, INC. and § UNILOC LUXEMBOURG, S.A., § Civil Action No. 3:18-cv-00560-DCG § Plaintiffs, § § v. § PATENT CASE § LG ELECTRONICS U.S.A., INC., § LG ELECTRONICS MOBILECOMM § U.S.A. INC. and § LG ELECTRONICS, INC., § § Defendant. § JURY TRIAL DEMANDED § FIRST AMENDED COMPLAINT FOR PATENT INFRINGEMENT Plaintiffs, Uniloc USA, Inc. (“Uniloc USA”) and Uniloc Luxembourg, S.A. (“Uniloc Luxembourg”) (together, “Uniloc”), for their First Amended Complaint against defendant, LG Electronics U.S.A. (“LGE”), Inc., LG Electronics Mobilecomm U.S.A., Inc., and LG Electronics, Inc., (“LG Korea”) (together “LG”), allege as follows:1 THE PARTIES 1. Uniloc USA is a Texas corporation having a principal place of business at Legacy Town Center I, Suite 380, 7160 Dallas Parkway, Plano Texas 75024. Uniloc USA also maintains a place of business at 102 N. College, Suite 603, Tyler, Texas 75702. 1 An amended complaint supersedes the original complaint and renders it of no legal effect, King v. Dogan, 31 F.3d 344. 346 (5th Cir. 1994), rendering a motion to dismiss the original complaint moot. See, e.g., Mangum v. United Parcel Services, No. 3:09-cv-0385, 2009 WL 2700217 (N.D. Tex. Aug. 26, 2009). 2988606.v1 Case 5:18-cv-06739-VKD Document 27 Filed 07/02/18 Page 2 of 11 2. Uniloc Luxembourg is a Luxembourg public limited liability company having a principal place of business at 15, Rue Edward Steichen, 4th Floor, L-2540, Luxembourg (R.C.S. -
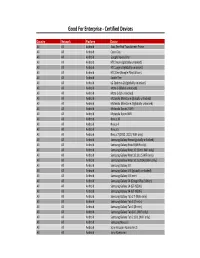
MMS Copy of Supported Devices
Good For Enterprise ‐ Certified Devices Country Network Platform Device All All Android Asus Eee Pad Transformer Prime All All Android Cisco Cius All All Android Google Nexus One All All Android HTC Desire (globally unlocked) All All Android HTC Legend (globally unlocked) All All Android HTC One (Google Play Edition) All All Android Kindle Fire All All Android LG Optimus 2X (globally unlocked) All All Android Moto G (Global unlocked) All All Android Moto G (US unlocked) All All Android Motorola Milestone (globally unlocked) All All Android Motorola Milestone 2 (globally unlocked) All All Android Motorola Xoom 2 WiFi All All Android Motorola Xoom WiFi All All Android Nexus 10 All All Android Nexus 4 All All Android Nexus 5 All All Android Nexus 7 (2012, 2013, WiFi only) All All Android Samsung Galaxy Nexus (globally unlocked) All All Android Samsung Galaxy Note 8 (WiFi only) All All Android Samsung Galaxy Note 10.1 (Intl. WiFi only) All All Android Samsung Galaxy Note 10.1 (U.S WiFi only) All All Android Samsung Galaxy Note 10.1 (2014) (WiFi only) All All Android Samsung Galaxy S II All All Android Samsung Galaxy S III (globally unlocked) All All Android Samsung Galaxy S III mini All All Android Samsung Galaxy S4 (Google Play Edition) All All Android Samsung Galaxy S4 (GT‐I9500) All All Android Samsung Galaxy S4 (GT‐I9505) All All Android Samsung Galaxy Tab 2 7 (WiFi only) All All Android Samsung Galaxy Tab 3 (7‐inch) All All Android Samsung Galaxy Tab 3 (8‐inch) All All Android Samsung Galaxy Tab 10.1 (WiFi only) All All Android Samsung -

Presentación De Powerpoint
Modelos compatibles de Imóvil No. Marca Modelo Teléfono Versión del sistema operativo 1 360 1501_M02 1501_M02 Android 5.1 2 100+ 100B 100B Android 4.1.2 3 Acer Iconia Tab A500 Android 4.0.3 4 ALPS (Golden Master) MR6012H1C2W1 MR6012H1C2W1 Android 4.2.2 5 ALPS (Golden Master) PMID705GTV PMID705GTV Android 4.2.2 6 Amazon Fire HD 6 Fire HD 6 Fire OS 4.5.2 / Android 4.4.3 7 Amazon Fire Phone 32GB Fire Phone 32GB Fire OS 3.6.8 / Android 4.2.2 8 Amoi A862W A862W Android 4.1.2 9 amzn KFFOWI KFFOWI Android 5.1.1 10 Apple iPad 2 (2nd generation) MC979ZP iOS 7.1 11 Apple iPad 4 MD513ZP/A iOS 7.1 12 Apple iPad 4 MD513ZP/A iOS 8.0 13 Apple iPad Air MD785ZP/A iOS 7.1 14 Apple iPad Air 2 MGLW2J/A iOS 8.1 15 Apple iPad Mini MD531ZP iOS 7.1 16 Apple iPad Mini 2 FE276ZP/A iOS 8.1 17 Apple iPad Mini 3 MGNV2J/A iOS 8.1 18 Apple iPhone 3Gs MC132ZP iOS 6.1.3 19 Apple iPhone 4 MC676LL iOS 7.1.2 20 Apple iPhone 4 MC603ZP iOS 7.1.2 21 Apple iPhone 4 MC604ZP iOS 5.1.1 22 Apple iPhone 4s MD245ZP iOS 8.1 23 Apple iPhone 4s MD245ZP iOS 8.4.1 24 Apple iPhone 4s MD245ZP iOS 6.1.2 25 Apple iPhone 5 MD297ZP iOS 6.0 26 Apple iPhone 5 MD298ZP/A iOS 8.1 27 Apple iPhone 5 MD298ZP/A iOS 7.1.1 28 Apple iPhone 5c MF321ZP/A iOS 7.1.2 29 Apple iPhone 5c MF321ZP/A iOS 8.1 30 Apple iPhone 5s MF353ZP/A iOS 8.0 31 Apple iPhone 5s MF353ZP/A iOS 8.4.1 32 Apple iPhone 5s MF352ZP/A iOS 7.1.1 33 Apple iPhone 6 MG492ZP/A iOS 8.1 34 Apple iPhone 6 MG492ZP/A iOS 9.1 35 Apple iPhone 6 Plus MGA92ZP/A iOS 9.0 36 Apple iPhone 6 Plus MGAK2ZP/A iOS 8.0.2 37 Apple iPhone 6 Plus MGAK2ZP/A iOS 8.1 -

Udynamo Compatibility List
uDynamo Compatibility List Reader Manuf. Device Name Alt. Model Info Model Info OS OS Version Carrier Date Added Date Tested Type iDynamo 5 Apple iPad Air 2 Lightning N/A iOS N/A N/A Tablet iDynamo 5 Apple iPad Air* Lightning N/A iOS N/A N/A Tablet iDynamo 5 Apple iPad with Retina Display* Lightning N/A iOS N/A N/A Tablet iDynamo 5 Apple iPad mini 3 Lightning N/A iOS N/A N/A Tablet iDynamo 5 Apple iPad mini 2 Lightning N/A iOS N/A N/A Tablet iDynamo 5 Apple iPad mini* Lightning N/A iOS N/A N/A Tablet iDynamo 5 Apple iPhone 5c* Lightning N/A iOS N/A N/A Phone iDynamo 5 Apple iPhone 5s* Lightning N/A iOS N/A N/A Phone iDynamo 5 Apple iPhone 5* Lightning N/A iOS N/A N/A Phone iDynamo 5 Apple iPod touch (5th* generation) Lightning N/A iOS N/A N/A iPod iDynamo 5 Apple iPhone 6* Lightning N/A iOS N/A N/A Phone iDynamo 5 Apple iPhone 6 Plus* Lightning N/A iOS N/A N/A Phone iDynamo Apple iPad (3rd generation) 30 PIN N/A iOS N/A N/A Tablet iDynamo Apple iPad 2 30 PIN N/A iOS N/A N/A Tablet iDynamo Apple iPad 30 PIN N/A iOS N/A N/A Tablet iDynamo Apple iPhone 4s 30 PIN N/A iOS N/A N/A Phone iDynamo Apple iPhone 4 30 PIN N/A iOS N/A N/A Phone iDynamo Apple iPhone 3GS 30 PIN N/A iOS N/A N/A Phone iDynamo Apple iPod touch (3rd and 4th generation) 30 PIN N/A iOS N/A N/A iPod uDynamo Acer liquid MT liquid MT Android 2.3.6 101.18 1/24/14 1/24/14 uDynamo Alcatel Alcatel OneTouch Fierce 7024W Android 4.2.2 101.18 3/6/14 3/6/14 uDynamo ALCATEL Megane ALCATEL ONE TOUCH 5020T Android 4.1.2 101.18 8/10/15 8/10/15 uDynamo ALCATEL ALCATEL ONE TOUCH IDOL X ALCATEL -

Android (Legacy) Platform
Android (Legacy) Platform VMware Workspace ONE UEM Android (Legacy) Platform You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ VMware, Inc. 3401 Hillview Ave. Palo Alto, CA 94304 www.vmware.com © Copyright 2021 VMware, Inc. All rights reserved. Copyright and trademark information. VMware, Inc. 2 Contents 1 Workspace ONE UEM Integration with Android(Legacy) 6 Supported Devices and OS Versions for Android (Legacy) Deployment 7 Requirements for Configuring Devices with Android (Legacy) Deployment 8 Android (Legacy) Device Administrator Migration 8 Create Smart Group to Migrate from Android (Legacy) to Android Work Profile 11 Prerequisites for Migrating to Android Enterprise to Work Profile Android (Legacy) Migration 12 Migrating to Work Profile From Android (Legacy) Using Migration Tool 14 Migrate to Android Enterprise Using Zero Touch Enrollment 15 Migration Details Page 15 Frequently Asked Questions for Android (Legacy) Migration 16 2 Android (Legacy) Enrollment 18 Requirements for Android (Legacy) Enrollment 20 Enrollment Restrictions for Android 20 Enrolling an Android Device with the Workspace ONE Intelligent Hub 21 Workspace ONE Intelligent Hub Sideloading for Android (Legacy) Deployment 22 Hub-Based Sideload Enrollment 22 Sideload Workspace ONE Intelligent Hub Using a USB Port 23 Sideload Workspace ONE Intelligent Hub Using a Hosted Download Site 23 3 Profiles for Android (Legacy) 25 Device Passcode Profile (Android (Legacy)) 27 Enforce Device Passcode (Android (Legacy)) 28 -

Known Issues with Android Devices Using Native Activesync
The following table is an index of the known issues associated with Android devices on which an account has been created using the ActiveSync protocol native to the device. Click on a link to view the knowledge base article for the issue described. Known Issues with Android Devices Using Native ActiveSync Important! Knowledge base articles list the devices on which the issue has been observed, however, the issue may not be limited to the device(s) noted. Select a Device Manufacturer Amazon Motorola ASUS Pantech Dell Samsung Fujitsu Sharp HTC Sony Ericsson Huawei Verizon Kyocera ZTE LG Android devices tested but NOT supported Amazon Kindle Fire HD Drafts do not synchronize unless “Synchronize All Mail” is enabled Temporary error message displays on device when policy changes are made Recurring events created on the device have no end date Cannot add reply text when responding to a meeting invitation Signal Level does not display in User Statistics Password change prompt can be bypassed When password restrictions are loosened, they are not loosened on the device If Inactivity Timeout is the only security setting changed, it does not update on the server Home Address ”City” field is replaced by the Other Address “City field Email priority not supported Device does not wipe unless a Pin or password is set ASUS Nexus 7 Devices may allow numeric PIN or password Drafts do not synchronize unless “Synchronize All Mail” is enabled Password change prompt can be bypassed When password restrictions are loosened, they are not loosened -

LG Cell Phone Software - LG Cell Phones Blog
LG Cell Phone Software - LG Cell Phones Blog http://www.lg-phones.org/category/lg-cell-phone-software LG Cell Phones Blog Phones,games,software all in here HOME New LG Phones LG Tools & Firmware Game List SEARCH: Categories LG Android Phones (1266) LG Windows Phone 7 (53) LG Pad (17) LG Cell Phone News (1040) LG Cell Phone Previews (380) LG Cell Phone Reviews (165) LG Cell Phone Software (858) LG Phone Problem and Solution (787) LG Cell Phone Specifications (70) LG Cell Phone Pictures (152) LG Cell Phone Accessories (96) LG Cell Phone Games (58) LG Randomness (86) LG-Ally info (55) LG-Arena info (68) LG-Bliss info (7) LG-Chocolate info (31) LG-Chocolate Touch info (32) LG-Cookie info (79) LG-Cookie Fresh info (7) LG-Dare info (115) LG-enV touch info (78) LG-enV2 info (10) LG-enV3 info (18) LG-Eve/Etna/Intouch Max info (20) LG-Esteem info (33) LG-eXpo info (39) LG-Fathom info (13) LG-Glimmer info (5) LG-Incite info (43) LG-Layla info (1) LG-Lucid-4G info (24) LG-Marquee info (25) LG-Motion-4G info (16) 1 of 9 3/12/2013 11:22 AM LG Cell Phone Software - LG Cell Phones Blog http://www.lg-phones.org/category/lg-cell-phone-software LG-Neon2 info (5) LG-Nexus-4 info (51) LG-Nitro-HD info (26) LG-Optimus info (760) LG-Pop info (37) LG-Prada-2 info (3) LG-Prada-3.0 info (16) LG-Prime info (7) LG-Quantum info (9) LG-Renoir info (59) LG-Revolution info (38) LG-Secret info (17) LG-Sentio info (1) LG-Shine info (35) LG-Spectrum info (36) LG-Spectrum-2 (13) LG-Spirit-4G info (11) LG-Thrill-4G info (37) LG-T-Mobile-G2X info (33) LG-Tritan info (11) LG-Versa info (50) LG-Viewty info (55) LG-Viewty Smart info (22) LG-Vortex info (3) LG-Voyager info (63) LG-Vu info (93) LG-Vu-Plus info (9) LG-Xenon info (31) 2 of 9 3/12/2013 11:22 AM LG Cell Phone Software - LG Cell Phones Blog http://www.lg-phones.org/category/lg-cell-phone-software Related Results Cell Phones for Business Compare Business Phone Plans & Solutions @ Business.com. -

Smart Fusion Списък Съвместимост На Устройствата
Smart Fusion Списък Съвместимост на Устройствата Acer Alcatel Acer Cloud Mobile Alcatel Idol 4 Acer E320 Liquid Express Alcatel One Touch 922 Acer Liquid Glow Alcatel One Touch 996 Acer Liquid S2 Alcatel Onetouch Idol 2 Alcatel Onetouch Idol 2 Mini S Adlink Alcatel Onetouch Idol 2S Alcatel Onetouch Pop Fit Adlink IMX-3000 Apple Asus Apple iPhone 11 and iPhone 11 Pro Asus MeMO Pad 8 (ME581CL) Apple iPhone 12, iPhone 12 mini, iPhone 12 Asus Padfone 2 Pro, iPhone 12 Pro Max Asus Padfone Infinity Apple iPhone 6 and iPhone 6 Plus Asus Vivo Tab Apple iPhone 6s and iPhone 6s Plus Asus Vivo Tab RT Apple iPhone 7 and iPhone 7 Plus Asus VivoTab Smart Apple iPhone 8 and iPhone 8 Plus Asus ZenFone 2 Apple iPhone SE Asus Zenfone 4 Apple iPhone X Asus Zenfone 5 Apple iPhone XR Asus Zenfone 6 Apple iPhone Xs and iPhone Xs Max Apple Watch: BlackBerry HTC BlackBerry Bold 9790 HTC Desire 500 BlackBerry Bold 9900/9930 HTC Desire 510 BlackBerry Classic HTC Desire 610 BlackBerry Curve 9350/9360/9370 HTC Desire 620 BlackBerry Curve 9380 HTC Desire 816 BlackBerry Dtek50 HTC Desire C BlackBerry Dtek60 HTC Desire Eye BlackBerry KEY2 HTC Droid DNA/HTC J Butterfly BlackBerry KEYone HTC Droid Incredible 4G LTE BlackBerry Motion HTC Evo 4G LTE BlackBerry Passport HTC First BlackBerry PlayBook HTC Incredible BlackBerry Priv HTC Mini BlackBerry Q10 HTC One BlackBerry Q5 HTC One M8 BlackBerry Z10 HTC One M9 BlackBerry Z30 HTC One Max Blackview BV9800 HTC One SV Blackview BV9800 Pro HTC One VX Blu Life Pure XL HTC One X/XL HTC Ruby/Amaze 4G BBK Vivo Xplay HTC U Play -

View Complaint
Case 3:18-cv-00560-N Document 27 Filed 07/02/18 Page 1 of 11 PageID 110 IN THE UNITED STATES DISTRICT COURT FOR THE NORTHERN DISTRICT OF TEXAS DALLAS DIVISION § UNILOC USA, INC. and § UNILOC LUXEMBOURG, S.A., § Civil Action No. 3:18-cv-00560-DCG § Plaintiffs, § § v. § PATENT CASE § LG ELECTRONICS U.S.A., INC., § LG ELECTRONICS MOBILECOMM § U.S.A. INC. and § LG ELECTRONICS, INC., § § Defendant. § JURY TRIAL DEMANDED § FIRST AMENDED COMPLAINT FOR PATENT INFRINGEMENT Plaintiffs, Uniloc USA, Inc. (“Uniloc USA”) and Uniloc Luxembourg, S.A. (“Uniloc Luxembourg”) (together, “Uniloc”), for their First Amended Complaint against defendant, LG Electronics U.S.A. (“LGE”), Inc., LG Electronics Mobilecomm U.S.A., Inc., and LG Electronics, Inc., (“LG Korea”) (together “LG”), allege as follows:1 THE PARTIES 1. Uniloc USA is a Texas corporation having a principal place of business at Legacy Town Center I, Suite 380, 7160 Dallas Parkway, Plano Texas 75024. Uniloc USA also maintains a place of business at 102 N. College, Suite 603, Tyler, Texas 75702. 1 An amended complaint supersedes the original complaint and renders it of no legal effect, King v. Dogan, 31 F.3d 344. 346 (5th Cir. 1994), rendering a motion to dismiss the original complaint moot. See, e.g., Mangum v. United Parcel Services, No. 3:09-cv-0385, 2009 WL 2700217 (N.D. Tex. Aug. 26, 2009). 2988606.v1 Case 3:18-cv-00560-N Document 27 Filed 07/02/18 Page 2 of 11 PageID 111 2. Uniloc Luxembourg is a Luxembourg public limited liability company having a principal place of business at 15, Rue Edward Steichen, 4th Floor, L-2540, Luxembourg (R.C.S. -

In the United States District Court for the Northern District of Texas Dallas Division
IN THE UNITED STATES DISTRICT COURT FOR THE NORTHERN DISTRICT OF TEXAS DALLAS DIVISION § UNILOC USA, INC. and § UNILOC LUXEMBOURG, S.A., § Civil Action No. § Plaintiffs, § § v. § PATENT CASE § LG ELECTRONICS U.S.A., INC., § LG ELECTRONICS MOBILECOMM § U.S.A. INC. AND § LG ELECTRONICS, INC., § § Defendant. § JURY TRIAL DEMANDED § COMPLAINT FOR PATENT INFRINGEMENT Plaintiffs, Uniloc USA, Inc. (“Uniloc USA”) and Uniloc Luxembourg, S.A. (“Uniloc Luxembourg”) (together, “Uniloc”), for their complaint against defendants LG Electronics U.S.A., Inc. (“LGE USA”), LG Electronics Mobilecomm U.S.A., Inc. (“LGE Mobilecomm”), and LG Electronics, Inc., (“LG Korea”) (collectively, “LG”), allege as follows: THE PARTIES 1. Uniloc USA is a Texas corporation having a principal place of business at Legacy Town Center I, Suite 380, 7160 Dallas Parkway, Plano Texas 75024. Uniloc USA also maintains a place of business at 102 N. College, Suite 603, Tyler, Texas 75702. 2. Uniloc Luxembourg is a Luxembourg public limited liability company having a principal place of business at 15, Rue Edward Steichen, 4th Floor, L-2540, Luxembourg (R.C.S. Luxembourg B159161). 3. LGE USA is a Delaware corporation having a regular and established place of business at 2151-2155 Eagle Parkway, Fort Worth, Texas 76177. LGE USA offers its products and/or services, including those accused herein of infringement, to customers and potential customers located in Texas and in the judicial Northern District of Texas. LGE USA may be served with process through its registered agent for service in Texas: United States Corporation Company, 211 E. 7th Street, Suite 620, Austin, Texas 78701.