Social and Human Considerations for a More Mobile World (2004)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Active Mobile Phone Detector Using Radio Frequency Signal
Available online at: http://www.ijmtst.com/vol6issue07.html International Journal for Modern Trends in Science and Technology ISSN: 2455-3778 :: Volume: 06, Issue No: 07, July 2020 Active Mobile Phone Detector using Radio Frequency Signal T.Agalya1| R.Mathumitha1 | P.Poongodi1 | D.Sangeetha1 | K.S.Gowthaman2 1UG Scholar, Department of EEE, Government College of Engineering, Sengipatti, Thanjavur-613402, Tamilnadu, India. 2Assistant Professor, Department of EEE, Government College of Engineering, Sengipatti, Thanjavur-613402, Tamilnadu, India. To Cite this Article T.Agalya, R.Mathumitha, P.Poongodi, D.Sangeetha and K.S.Gowthaman, “Active Mobile Phone Detector using Radio Frequency Signal”, International Journal for Modern Trends in Science and Technology, Vol. 06, Issue 07, July 2020, pp.:96-99; https://doi.org/10.46501/IJMTST060715 Article Info Received on 14-June-2020, Revised on 22-June-2020, Accepted on 29-June-2020, Published on 16-July-2020. ABSTRACT Mobile phone has made our communication easier. It is used for sending and receiving text messages, calls, E-mails, games, camera. Mobile phones are said to be in active mode, when they receive calls or make calls, sending and receiving text messages and when it is connected to internet. Some people uses mobile phone in unnecessary places where mobile phones are prohibited. Mobile phone detector is a device used to detect the active mobile phone in unauthorized places. It receives the radio frequency signals from mobile phones through antenna and indicates the use of cell phones by LED and buzzer. This device is useful for detecting the use of mobile phone in examination hall, during meeting and plane stations. -
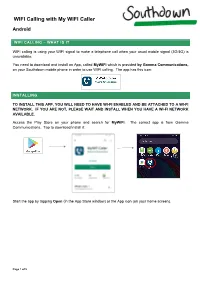
WIFI Calling with My WIFI Caller Android
WIFI Calling with My WIFI Caller Android WIFI CALLING – WHAT IS IT WIFI calling is using your WIFI signal to make a telephone call when your usual mobile signal (3G/4G) is unavailable. You need to download and install an App, called MyWiFi which is provided by Gamma Communications, on your Southdown mobile phone in order to use WIFI calling. The app has this icon: INSTALLING TO INSTALL THIS APP, YOU WILL NEED TO HAVE WI-FI ENABLED AND BE ATTACHED TO A WI-FI NETWORK. IF YOU ARE NOT, PLEASE WAIT AND INSTALL WHEN YOU HAVE A WI-FI NETWORK AVAILABLE. Access the Play Store on your phone and search for MyWiFi. The correct app is from Gamma Communications. Tap to download/install it: Start the app by tapping Open (in the App Store window) or the App icon (on your home screen). Page 1 of 5 WIFI Calling with My WIFI Caller Android The first time you use App you will need to Accept the Terms of Use: You will then be prompted to enter your mobile phone number. Enter it and tap Send Verification SMS You will receive the code in a text message. Enter the code and tap Continue Page 2 of 5 WIFI Calling with My WIFI Caller Android When asked, enter the code you have been sent via text. This code is valid for 15 minutes . There will be a series of message windows on screen: Please Allow all of these messages. These are necessary to allow the MyWiFi App to work like in the same way as the Phone App your phone, and are equivalent to the access that your Phone App has to your contacts, photos and audio etc. -
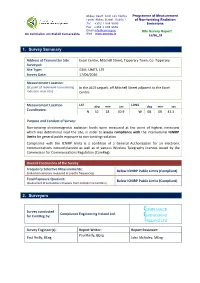
1. Survey Summary 2. Surveyors
Abbey Court Irish Life Centre Programme of Measurement Lower Abbey Street Dublin 1 of Non-Ionising Radiation Tel +353 1 804 9600 Emissions Fax +353 1 804 9680 Email [email protected] Site Survey Report An Coimisiún um Rialáil Cumarsáide Web www.comreg.ie 16/66_18 1. Survey Summary Address of Transmitter Site Excel Centre, Mitchell Street, Tipperary Town, Co. Tipperary Surveyed: Site Type: GSM, UMTS, LTE Survey Date: 17/06/2016 Measurement Location: (at point of maximum non-ionising In the ALDI carpark, off Mitchell Street adjacent to the Excel radiation near site) Centre Measurement Location LAT deg min sec LONG deg min sec Coordinates: N 52 28 30.9 W 08 09 41.3 Purpose and Conduct of Survey: Non-ionising electromagnetic radiation levels were measured at the point of highest emissions which was determined near the site, in order to assess compliance with the international ICNIRP Limits for general public exposure to non-ionising radiation. Compliance with the ICNIRP limits is a condition of a General Authorisation for an electronic communications network/service as well as of various Wireless Telegraphy licences issued by the Commission for Communications Regulation (ComReg). Overall Conclusions of the Survey Frequency Selective Measurements: Below ICNIRP Public Limits (Compliant) (Individual emissions measured at specific frequencies) Total Exposure Quotient: Below ICNIRP Public Limits (Compliant) (Assessment of cumulative emissions from multiple transmitters) 2. Surveyors Survey conducted Compliance Engineering Ireland Ltd. for ComReg by: Survey Engineer(s): Report Writer: Report Reviewer: Paul Reilly, BEng Paul Reilly, BEng John McAuley, MEng 3. Survey Location Details Transmitter Site Photo Survey Weather Sky: Partly Cloudy, Light rain Temperature: 16 ° C Relative Humidity: 43% Map of Transmitter Site and Measurement Location 4. -

Business Segments Ranging from Small- Proportionate Mobile Customers Across the World
Proportionate mobile customers across the globe. 341.1m (2009: 302.6m; 2008: 260.5m) BrandFinance global ranking 7th most valuable brand (2009: 8th; 2008: 11th) Customers and distribution Customers are at the core of everything we do. Through our products and services we endeavour to address all our customers’ communications needs. International customer base with diverse needs Enterprise Vodafone has a truly international customer base with 341.1 million Vodafone also caters to all business segments ranging from small- proportionate mobile customers across the world. We continually office-home-office (‘SoHo’) and small-medium enterprises (‘SMEs’) to seek to develop new and innovative propositions that deliver relevance corporates and multinational corporations (‘MNCs’). While our core and value to all our customers and build a long lasting relationship mobile voice and data business continues to grow, our enterprise meeting their expectations and needs. As customers move between customers are increasingly asking for combined fixed and mobile work and home environments and look for integrated solutions, solutions for their voice and data needs as well as integrated services we have a suite of propositions which often bundle together and productivity tools. voice, messaging, data and increasingly fixed line services to meet their needs. Brand We have continued to build brand value by delivering a superior, consistent and differentiated customer experience. During the 2010 financial year we evolved our brand positioning to “power to you” emphasising our role of empowering customers to be able to live their lives to the full. It is a further expression of the importance of the customer being central to everything we do and is reinforced in communications substantiating how products and services impact and empower our customers. -

User Guide to Duo Two-Factor Authentication Last Updated: 19 August 2021
User guide to Duo two-factor authentication Last updated: 19 August 2021 This manual aims to walk you through the most common tasks that involve Duo two-factor authentication. If you don’t find a section below that helps, please email [email protected] so that we can improve this document for future users. 1 -- About Duo two-factor authentication 3 1.1) Why has the University implemented two-factor authentication (2FA)? 3 1.2) When and how do I use Duo? 4 1.3) I connect and work on a desktop or laptop, do I install Duo on these devices? 5 2 -- Registering devices for Duo 6 2.1) How do I download the Duo Mobile app? 6 2.2) How do I log in to the Duo SelfService Console? 7 2.3) How do I register (enrol) a device to use the Duo Mobile app? 9 2.4) How do I register (enrol) my phone to use the SMS text message method? 11 2.5) How do I get a hard token? 13 2.6) How do I test my registered device? 14 2.7) Can I register more than one device (or phone number) with Duo? 15 3 -- Using Duo 16 3.1) How do I log in to services using the Duo Mobile app? 16 3.2) How do I log in to services using SMS text messages? 19 3.3) How do I log in to services using a hard token? 23 3.4) How do I log in to the Virtual Desktop Service? 26 3.5) Can I use Duo outside of the UK? 28 3.6) Is it possible to use Duo if I have no mobile phone signal or wifi? 29 3.7) What if I don't have my Duo registered device with me? 30 4 -- Changing your Duo device 31 4.1) I changed my mobile phone but kept the same phone number. -

Dating, Digital Media, and Diaspora: Contextualising the Cultural Uses of Tinder and Tantan Among Australian Chinese Diasporas
DATING, DIGITAL MEDIA, AND DIASPORA: CONTEXTUALISING THE CULTURAL USES OF TINDER AND TANTAN AMONG AUSTRALIAN CHINESE DIASPORAS Xu Chen BA, MA Submitted in fulfillment of the requirements for the degree of Doctor of Philosophy School of Communication Creative Industries Faculty Queensland University of Technology 2020 Keywords Chinese diasporas Dating apps Digital cultures Ethnicity Sexual cultures Social media Dating, digital media, and diaspora: Contextualising the cultural uses of Tinder and Tantan among Australian Chinese diasporas i Abstract Bringing together perspectives from digital dating, sexual cultures, and diaspora studies, this project investigates how Australia-based Chinese users engage with Tinder and Tantan, two dating applications (apps) that have emerged from different cultural contexts – one Western, and one non-Western. Tantan is a popular dating app in mainland China. It was designed to mimic Tinder which, like other Western social media platforms, is blocked in mainland China. Although the study of dating apps has become a burgeoning research field over the past decade, little work has been done – and then only recently – on diasporic uses of dating apps. Research focusing on digital diaspora has shown that social media are essential to the maintenance and negotiation of diasporic identity among Australian Chinese diasporas. Within this digital-diasporic research, however, little attention has been paid to the role of dating apps, despite the popularity of both Chinese and Western dating apps among Chinese diasporic communities. To address this lack of attention, this research places a much-needed focus on the role of dating apps within digital diaspora studies. At the same time, it expands the emerging critical focus on diaspora within dating app studies. -

Snapchat Launches Own Multi-Player Gaming Platform 4 April 2019
Snapchat launches own multi-player gaming platform 4 April 2019 long holiday weekend, something that makes us feel like we're sitting with friends, controllers in hand," he said. "Unfortunately, these games are hard to find on mobile (...) it's hard to get everybody to install the same game, and it's hard to chat." The six games will be directly accessible from Snapchat's popular messaging feature Chat, offering users the possibility to play while at the same time exchanging messages. "Bitmoji Party," developed by Snapchat parent Snap and inspired by Nintendo's "Wii Party," for example features players, brought to life with 3D Bitmojis, as they compete across four fast-paced Snapchat—the popular messaging app—is lauching its mini-games. own multiplayer gaming platform "You can launch Bitmoji Party right from the chat bar, allowing you and your friends to instantly play together, no install required," Wu said. Messaging app Snapchat, which is widely popular among younger users but has struggled to turn a "Alphabear Hustle" is described as a fast-paced profit since its creation in 2011, on Thursday word game in which players work together to spell unveiled new features including an integrated words, collect cute bears and build their own gaming platform, an expansion of its original series personal bear village. and new parnerships with developers. "Zombie Rescue Squad" deals with a zombie "Friendship is more than just the things you chat apocalypse that calls on players to "rescue about," said Will Wu, the director of product at survivors from the hungry hordes and gather as Snapchat as he unveiled Snap Games at a Partner many supplies as you can. -

A Comparison of Mobile Application Adoption Between Chinese and Us College Students
WHY DO WE CHOOSE THIS APP? A COMPARISON OF MOBILE APPLICATION ADOPTION BETWEEN CHINESE AND US COLLEGE STUDENTS Chenjie Zhang A Dissertation Submitted to the Graduate College of Bowling Green State University in partial fulfillment of the requirements for the degree of DOCTOR OF PHILOSOPHY August 2018 Committee: Louisa Ha, Advisor Patrick D. Pauken Graduate Faculty Representative Lisa Hanasono Kate Magsamen-Conrad © 2018 Chenjie Zhang All Rights Reserved iii ABSTRACT Louisa Ha, Advisor The present cross-cultural study applies the regulatory focus theory developed by Higgins and modifies the cultural dimensions proposed by Hofstede to explore and compare the relationships between cultural values and the focused strategic means college consumers use in China and the US. In total, 377 Chinese and 403 US college students participated in a survey to reveal the relations between variables of app download and their cultural values. In addition, for a deeper and insightful understanding of the app download behavior, the method of semi-structured interview was used to raise participants’ and the researcher’s consciousness of and critical reflections upon app download processes and experiences. The research results are five-fold: First, Chinese college students share similar scores of four cultural dimensions with the US college students, and there is no difference in indulgence between the two countries. Second, country is a more powerful variable than cultural dimensions in model testing in terms of differentiating consumers’ regulatory focus. US consumers are more likely to be promotion focused and Chinese consumers are likely to be prevention focused. Third, promotion focused consumers are likely to seek both hedonic and utilitarian gratifications, and to heuristically process information. -

Design and Testing of Mobile-Phone-Detectors
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by International Institute for Science, Technology and Education (IISTE): E-Journals Innovative Systems Design and Engineering www.iiste.org ISSN 2222-1727 (Paper) ISSN 2222-2871 (Online) Vol.7, No.9, 2016 Design and Testing of Mobile-Phone-Detectors Edwin Ataro* Diana Starovoytova Madara Simiuy Sitati School of Engineering, Moi University P. O. Box 3900, Eldoret, Kenya Abstract Students use mobile-phones to store lecture-materials, e-books, tutorials, videos, communicate with their classmates and browse the internet for exceedingly-different-intentions. These projected-advantages, however, would have potential-undesirable-effects if mobile-phones are utilized in restricted-premises, such as exam-venues. Noncompliant- students (to general University exam-regulations) do use mobile-phones to cheat in exams. The rapid-explosion of cell-phones at the beginning of the 21st Century eventually raised problems, such as their potential-use to invade privacy or contribute to widespread academic-cheating. In this paper, two systems, that will be used, independently, to detect mobile-phones in the exam-venues, were proposed: a mobile-detector with a range of 1.0m, using resistor-capacitor-circuit, which can detect both the incoming and outgoing-calls, as well as video-transmission and text messages, even if a mobile-phone is kept at the silent mode; and a Reed-switch- circuit-scanner, which, responds to an applied-magnetic-field and, can be used to detect mobile-phones that are switched-off or put on flight-mode, and thus, it can be used to scan students (without physical-inspection) on their entering examination-rooms. -

Dating Expectations in Social Media
Aalto University School of Science Master’s Programme in Information Networks Annukka Jänkälä Dating expectations in social media: From profile pictures to a date and beyond Master’s Thesis Helsinki, January 18, 2017 Supervisor: Professor Tapio Takala, Aalto University Advisor: Asko Lehmuskallio Ph.D. (Social Sciences), University of Tampere ii Aalto University School of Science ABSTRACT OF Master’s Programme in Information Networks MASTER’S THESIS Author: Annukka Jänkälä Title: Dating expectations in social media: From profiles pictures to a date and beyond Pages: vii + 127 Date: January 18, 2017 Major: Information Networks Supervisor: Professor Tapio Takala Advisor: Asko Lehmuskallio, Ph.D. (Social Sciences) Computer-mediated communication (CMC) has widely been seen as inferior to face-to- face (FtF) communication because of for example the lack of immediate feedback and nonverbal cues. However, the social information processing theory sees CMC as equal to FtF communication because people want to build social relationships also in CMC. The hyperpersonal theory goes even further by stating that the reduced cues in CMC foster more affection and emotion compared with FtF communication. This thesis aimed to explore this field further from the view of singles seeking a romantic life partner online. The study was conducted by interviewing 13 current and former Tinder users with semi- structured interviews. Some of them also provided their Tinder profiles and/or conversation histories for further analysis. The subjects were young adults with no children, living in the Helsinki metropolitan area of Finland, and most of them had or were pursuing a university degree. They were seeking a life partner rather than one-night stands. -

Mobile Phone Network and Migration: Evidence from Myanmar
Konrad-Zuse-Strasse 1 · D-18057 Rostock · Germany · Tel +49 (0) 3 81 20 81 - 0 · Fax +49 (0) 3 81 20 81 - 202 · www.demogr.mpg.de MPIDR Working Paper WP 2020-016 l April 2020 https://doi.org/10.4054/MPIDR-WP-2020-016 Mobile Phone Network and Migration: Evidence from Myanmar Riccardo Ciacci l [email protected] Jorge García-Hombrados l [email protected] Ayesha Zainudeen l [email protected] This working paper has been approved for release by: Mikko Myrskylä ([email protected]), Head of the Laboratory of Population Health, the Laboratory of Fertility and Well-Being, and the Research Group Labor Demography. © Copyright is held by the authors. Working papers of the Max Planck Institute for Demographic Research receive only limited review. Views or opinions expressed in working papers are attributable to the authors and do not necessarily reflect those of the Institute. Mobile Phone Network and Migration: Evidence from Myanmar* Riccardo Ciacci † Jorge García-Hombrados‡ Ayesha Zainudeen§ May 4, 2020 Abstract This study explores the effect of the expansion of mobile phone signal on migration decisions in Myanmar. The empirical strategy proposed follows Manacorda and Tesei (2019) and Andersen et al.(2011), it uses variation in lightning frequency across space as an instrumental variable for the expansion of mobile phone signal. Our results suggest that longer exposure to mobile phone network decreases migration. Specifi- cally, an increase of 1 s.d. in the time exposed to mobile phone signal diminishes the probability of household members to migrate by 17%. We find empirical evidence suggesting that such findings are driven by the positive effects of access to mobile phone signal on labor market outcomes and on perceived well-being. -

Data Cultures of Mobile Dating and Hook-Up Apps
Original Research Article Big Data & Society July–December 2017: 1–11 ! The Author(s) 2017 Data cultures of mobile dating and DOI: 10.1177/2053951717720950 hook-up apps: Emerging issues for journals.sagepub.com/home/bds critical social science research Kath Albury1, Jean Burgess2, Ben Light3, Kane Race4 and Rowan Wilken5 Abstract The ethical and social implications of data mining, algorithmic curation and automation in the context of social media have been of heightened concern for a range of researchers with interests in digital media in recent years, with particular concerns about privacy arising in the context of mobile and locative media. Despite their wide adoption and economic importance, mobile dating apps have received little scholarly attention from this perspective – but they are intense sites of data generation, algorithmic processing, and cross-platform data-sharing; bound up with competing cultures of pro- duction, exploitation and use. In this paper, we describe the ways various forms of data are incorporated into, and emerge from, hook-up apps’ business logics, socio-technical arrangements, and cultures of use to produce multiple and intersecting data cultures. We propose a multi-layered research agenda for critical and empirical inquiry into this field, and suggest appropriate conceptual and methodological frameworks for exploring the social and political challenges of data cultures. Keywords Online dating, apps, mobile media, geo-location, sexuality, data culture Introduction studied mainly with regard to specific aspects and par- ticular demographics, especially gay men (Blackwell The practice of everyday life is entangled with digital et al., 2015; Brubaker et al., 2016; Gudelunas, 2012; media, especially mobile media (Goggin, 2006), and this Light, 2016a; Light et al., 2008; Mowlabocus, 2010; extends to sex and intimate relationships (Light, 2014).