Design and Testing of Mobile-Phone-Detectors
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Active Mobile Phone Detector Using Radio Frequency Signal
Available online at: http://www.ijmtst.com/vol6issue07.html International Journal for Modern Trends in Science and Technology ISSN: 2455-3778 :: Volume: 06, Issue No: 07, July 2020 Active Mobile Phone Detector using Radio Frequency Signal T.Agalya1| R.Mathumitha1 | P.Poongodi1 | D.Sangeetha1 | K.S.Gowthaman2 1UG Scholar, Department of EEE, Government College of Engineering, Sengipatti, Thanjavur-613402, Tamilnadu, India. 2Assistant Professor, Department of EEE, Government College of Engineering, Sengipatti, Thanjavur-613402, Tamilnadu, India. To Cite this Article T.Agalya, R.Mathumitha, P.Poongodi, D.Sangeetha and K.S.Gowthaman, “Active Mobile Phone Detector using Radio Frequency Signal”, International Journal for Modern Trends in Science and Technology, Vol. 06, Issue 07, July 2020, pp.:96-99; https://doi.org/10.46501/IJMTST060715 Article Info Received on 14-June-2020, Revised on 22-June-2020, Accepted on 29-June-2020, Published on 16-July-2020. ABSTRACT Mobile phone has made our communication easier. It is used for sending and receiving text messages, calls, E-mails, games, camera. Mobile phones are said to be in active mode, when they receive calls or make calls, sending and receiving text messages and when it is connected to internet. Some people uses mobile phone in unnecessary places where mobile phones are prohibited. Mobile phone detector is a device used to detect the active mobile phone in unauthorized places. It receives the radio frequency signals from mobile phones through antenna and indicates the use of cell phones by LED and buzzer. This device is useful for detecting the use of mobile phone in examination hall, during meeting and plane stations. -
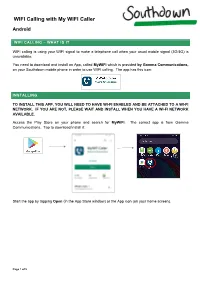
WIFI Calling with My WIFI Caller Android
WIFI Calling with My WIFI Caller Android WIFI CALLING – WHAT IS IT WIFI calling is using your WIFI signal to make a telephone call when your usual mobile signal (3G/4G) is unavailable. You need to download and install an App, called MyWiFi which is provided by Gamma Communications, on your Southdown mobile phone in order to use WIFI calling. The app has this icon: INSTALLING TO INSTALL THIS APP, YOU WILL NEED TO HAVE WI-FI ENABLED AND BE ATTACHED TO A WI-FI NETWORK. IF YOU ARE NOT, PLEASE WAIT AND INSTALL WHEN YOU HAVE A WI-FI NETWORK AVAILABLE. Access the Play Store on your phone and search for MyWiFi. The correct app is from Gamma Communications. Tap to download/install it: Start the app by tapping Open (in the App Store window) or the App icon (on your home screen). Page 1 of 5 WIFI Calling with My WIFI Caller Android The first time you use App you will need to Accept the Terms of Use: You will then be prompted to enter your mobile phone number. Enter it and tap Send Verification SMS You will receive the code in a text message. Enter the code and tap Continue Page 2 of 5 WIFI Calling with My WIFI Caller Android When asked, enter the code you have been sent via text. This code is valid for 15 minutes . There will be a series of message windows on screen: Please Allow all of these messages. These are necessary to allow the MyWiFi App to work like in the same way as the Phone App your phone, and are equivalent to the access that your Phone App has to your contacts, photos and audio etc. -
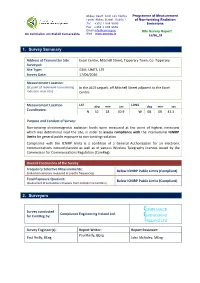
1. Survey Summary 2. Surveyors
Abbey Court Irish Life Centre Programme of Measurement Lower Abbey Street Dublin 1 of Non-Ionising Radiation Tel +353 1 804 9600 Emissions Fax +353 1 804 9680 Email [email protected] Site Survey Report An Coimisiún um Rialáil Cumarsáide Web www.comreg.ie 16/66_18 1. Survey Summary Address of Transmitter Site Excel Centre, Mitchell Street, Tipperary Town, Co. Tipperary Surveyed: Site Type: GSM, UMTS, LTE Survey Date: 17/06/2016 Measurement Location: (at point of maximum non-ionising In the ALDI carpark, off Mitchell Street adjacent to the Excel radiation near site) Centre Measurement Location LAT deg min sec LONG deg min sec Coordinates: N 52 28 30.9 W 08 09 41.3 Purpose and Conduct of Survey: Non-ionising electromagnetic radiation levels were measured at the point of highest emissions which was determined near the site, in order to assess compliance with the international ICNIRP Limits for general public exposure to non-ionising radiation. Compliance with the ICNIRP limits is a condition of a General Authorisation for an electronic communications network/service as well as of various Wireless Telegraphy licences issued by the Commission for Communications Regulation (ComReg). Overall Conclusions of the Survey Frequency Selective Measurements: Below ICNIRP Public Limits (Compliant) (Individual emissions measured at specific frequencies) Total Exposure Quotient: Below ICNIRP Public Limits (Compliant) (Assessment of cumulative emissions from multiple transmitters) 2. Surveyors Survey conducted Compliance Engineering Ireland Ltd. for ComReg by: Survey Engineer(s): Report Writer: Report Reviewer: Paul Reilly, BEng Paul Reilly, BEng John McAuley, MEng 3. Survey Location Details Transmitter Site Photo Survey Weather Sky: Partly Cloudy, Light rain Temperature: 16 ° C Relative Humidity: 43% Map of Transmitter Site and Measurement Location 4. -

Business Segments Ranging from Small- Proportionate Mobile Customers Across the World
Proportionate mobile customers across the globe. 341.1m (2009: 302.6m; 2008: 260.5m) BrandFinance global ranking 7th most valuable brand (2009: 8th; 2008: 11th) Customers and distribution Customers are at the core of everything we do. Through our products and services we endeavour to address all our customers’ communications needs. International customer base with diverse needs Enterprise Vodafone has a truly international customer base with 341.1 million Vodafone also caters to all business segments ranging from small- proportionate mobile customers across the world. We continually office-home-office (‘SoHo’) and small-medium enterprises (‘SMEs’) to seek to develop new and innovative propositions that deliver relevance corporates and multinational corporations (‘MNCs’). While our core and value to all our customers and build a long lasting relationship mobile voice and data business continues to grow, our enterprise meeting their expectations and needs. As customers move between customers are increasingly asking for combined fixed and mobile work and home environments and look for integrated solutions, solutions for their voice and data needs as well as integrated services we have a suite of propositions which often bundle together and productivity tools. voice, messaging, data and increasingly fixed line services to meet their needs. Brand We have continued to build brand value by delivering a superior, consistent and differentiated customer experience. During the 2010 financial year we evolved our brand positioning to “power to you” emphasising our role of empowering customers to be able to live their lives to the full. It is a further expression of the importance of the customer being central to everything we do and is reinforced in communications substantiating how products and services impact and empower our customers. -

User Guide to Duo Two-Factor Authentication Last Updated: 19 August 2021
User guide to Duo two-factor authentication Last updated: 19 August 2021 This manual aims to walk you through the most common tasks that involve Duo two-factor authentication. If you don’t find a section below that helps, please email [email protected] so that we can improve this document for future users. 1 -- About Duo two-factor authentication 3 1.1) Why has the University implemented two-factor authentication (2FA)? 3 1.2) When and how do I use Duo? 4 1.3) I connect and work on a desktop or laptop, do I install Duo on these devices? 5 2 -- Registering devices for Duo 6 2.1) How do I download the Duo Mobile app? 6 2.2) How do I log in to the Duo SelfService Console? 7 2.3) How do I register (enrol) a device to use the Duo Mobile app? 9 2.4) How do I register (enrol) my phone to use the SMS text message method? 11 2.5) How do I get a hard token? 13 2.6) How do I test my registered device? 14 2.7) Can I register more than one device (or phone number) with Duo? 15 3 -- Using Duo 16 3.1) How do I log in to services using the Duo Mobile app? 16 3.2) How do I log in to services using SMS text messages? 19 3.3) How do I log in to services using a hard token? 23 3.4) How do I log in to the Virtual Desktop Service? 26 3.5) Can I use Duo outside of the UK? 28 3.6) Is it possible to use Duo if I have no mobile phone signal or wifi? 29 3.7) What if I don't have my Duo registered device with me? 30 4 -- Changing your Duo device 31 4.1) I changed my mobile phone but kept the same phone number. -

Mobile Phone Network and Migration: Evidence from Myanmar
Konrad-Zuse-Strasse 1 · D-18057 Rostock · Germany · Tel +49 (0) 3 81 20 81 - 0 · Fax +49 (0) 3 81 20 81 - 202 · www.demogr.mpg.de MPIDR Working Paper WP 2020-016 l April 2020 https://doi.org/10.4054/MPIDR-WP-2020-016 Mobile Phone Network and Migration: Evidence from Myanmar Riccardo Ciacci l [email protected] Jorge García-Hombrados l [email protected] Ayesha Zainudeen l [email protected] This working paper has been approved for release by: Mikko Myrskylä ([email protected]), Head of the Laboratory of Population Health, the Laboratory of Fertility and Well-Being, and the Research Group Labor Demography. © Copyright is held by the authors. Working papers of the Max Planck Institute for Demographic Research receive only limited review. Views or opinions expressed in working papers are attributable to the authors and do not necessarily reflect those of the Institute. Mobile Phone Network and Migration: Evidence from Myanmar* Riccardo Ciacci † Jorge García-Hombrados‡ Ayesha Zainudeen§ May 4, 2020 Abstract This study explores the effect of the expansion of mobile phone signal on migration decisions in Myanmar. The empirical strategy proposed follows Manacorda and Tesei (2019) and Andersen et al.(2011), it uses variation in lightning frequency across space as an instrumental variable for the expansion of mobile phone signal. Our results suggest that longer exposure to mobile phone network decreases migration. Specifi- cally, an increase of 1 s.d. in the time exposed to mobile phone signal diminishes the probability of household members to migrate by 17%. We find empirical evidence suggesting that such findings are driven by the positive effects of access to mobile phone signal on labor market outcomes and on perceived well-being. -

Handbook on the Use of Mobile Phone Data for Official Statistics
Handbook on the Use of Mobile Phone Data for Official Statistics UN Global Working Group on Big Data for Official Statistics September 2019 1 Table of Contents Introduction ........................................................................................................................... 4 List of Definitions and Abbreviations .................................................................................... 5 1 Applications ................................................................................................................... 9 1.1 Mobile positioning data used in official statistics production ................................... 9 Travel statistics in Estonia .............................................................................................. 9 Inbound cross-border visitor arrival statistics in Indonesia .............................................. 9 1.2 Mobile positioning data used in research and pilots applicable for statistics ........... 10 Domain: Tourism and event statistics ........................................................................... 10 Domain: Population statistics ........................................................................................ 12 Domain: Migration statistics ......................................................................................... 14 Domain: Commuting statistics ...................................................................................... 15 Domain: Traffic flow statistics ..................................................................................... -

Design and Development of a Mobile Phone Signal Detector
International Journal of Engineering Research & Technology (IJERT) ISSN: 2278-0181 Vol. 3 Issue 7, July - 2014 Design and Development of a Mobile Phone Signal Detector Ajasa, A. A., Adenowo, A. A., Ogunlewe, A. O. and Shoewu, O. O. Department of Electronic and Computer Engineering Lagos State University, Epe Campus, Lagos, Nigeria. Abstract--This work involves the design and development of a respectively [8, 10]. digital signal detector which is capable of detecting incoming Mobile phone uses RF with a wavelength of 30cm at 872 to and outgoing signals from mobile phones. The presence of an 2170 MHz that is, the signal is high frequency with huge activated mobile phone can be detected by this handy, pocket- energy. When the mobile phone is active, it transmits the size mobile signal detector from a distance of one and a half signal in the form of sine wave which passes through the meters, which could be used in preventing the use of mobile space. The encoded audio/video signal contains phones in examination halls, confidential rooms etc. It is also suitable for detecting the use of mobile phone for spying and electromagnetic radiation which is picked up by the receiver unauthorized video transmission. The circuit can detect the in the base station. incoming and outing calls, text messages, and video transmission even if the mobile is kept in the silent mode. The 2.0 LITERATURE REVIEW moment the gadget detects Radio Frequency (RF) transmission signal from an activated mobile phone, it starts sounding a beep The existing technology currently available in the open alarm and the Light Emitting Diode (LED) blinks. -

Social and Human Considerations for a More Mobile World (2004)
INTERNATIONAL TELECOMMUNICATION UNION Document: SMIS/04 WORKSHOP ON SHAPING THE ITU/MIC 26 February 2004 FUTURE MOBILE INFORMATION SOCIETY Seoul, 4-5 March 2004 SOCIAL AND HUMAN CONSIDERATIONS FOR A MORE MOBILE WORLD BACKGROUND PAPER © ITU February 2004 This paper was prepared by Lara Srivastava <[email protected]>, Telecom Policy Analyst, International Telecommunication Union (ITU). The author wishes to acknowledge Maria Cristina Bueti and Alex Young for their assistance. The New Initiatives project on “Shaping the Future Mobile Information Society” is managed by Lara Srivastava <[email protected]> under the direction of Tim Kelly <[email protected]>. Country case studies (Japan, Korea, Morocco, Norway) on the future mobile information society, and a background paper on the future broadband convergence network, can be found at http://www.itu.int/futuremobile. The series editor is Joanna Goodrick <[email protected]>. The opinions expressed in this study are those of the author and do not necessarily reflect the views of the International Telecommunication Union or its membership. 2 Table of contents 1 Introduction ............................................................................................................................................... 4 1.1 Context .............................................................................................................................................. 4 1.2 A more mobile market...................................................................................................................... -

In the Modern World, We Can't Imagine Our Life Without Mobile Phone
In the modern world, we can’t imagine our life without mobile phone signals. Imagine, if your Smartphone has not a single bar? I know this is the disgusting situation for you but you don’t have any option except waiting for the cellular coverage. Here we come with the robust solution for weak cellular coverage in your Smartphone and Network Devices. The solution for the weak signal is known as the Signal Booster in India. We are sure that after installing the signal booster for the home you will never face the problem of call drop and slow internet. You can buy online Cell Phone Signal Booster for Home in India from us an affordable price. About: Cell Phone Signal Booster Mobile Phone Signals are the important part of your life because you can’t able to make calls and browse on the Internet without the Internet. Therefore getting good cellular coverage at any place is the important aspect for the users. Cell Phone Signal Booster in India is the network strength improving device which is working on the weak cell phone reception. You can’t imagine a single day without Smartphone and in the modern world; almost all devices are running on the principle of the Internet. Therefore the importance of the Internet is can’t avoid by us in our personal and professional life. This time you don’t have a need to face more call drops and you can simply get the good cellular coverage in your network devices such as Mobile phone, computer, laptop or Tablet. -

On the Physics of Gsm Jammer and Its Application in Lecture Theaters
Science Journal of Physics Published By Science Journal Publication ISSN: 2276-6367 doi:http://www.sjpub.org/sjp.html 10.7237/sjp/144 © Author(s) 2013. CC Attribution 3.0 License. ON THE PHYSICS OF GSM JAMMER AND ITS APPLICATION IN LECTURE THEATERS Uno, U .E, Okoye , P .F, and Charles, N. V Physics Department, Federal University of Technology Minna P.M.B 65,Niger State .Nigeria. Accepted 18th January, 2013 ABSTRACT The design and construction of a dual-band mobile-phone jammer was with the communication between cell phones and thoughtfully carried out to sense phone network signals and to towers to render the phones unusable. The jamming automatically activate it so as to de-activate the incoming or outgoing phone network signals. This jammer was designed to works at GSM becomes successful when the mobile phone is disabled 900mHz and GSM 1800mHz simultaneously and thus jams the four from making or receiving calls and other smart phone well-known network carriers in Nigeria (MTN, GLO, Etisalat and Zain.) activities ( sending or receiving text massages and as applied to lecture halls. It is evident from the results that the receiving internet services). Cell phones use one band to designed GSM jammer disabled mobile cell phone carriers. KEYWORDS: send signal to the base station (upward signal) and designed GSM jammer disabled mobile cell phone another band to receive signal from the base station (downward signal). Mobile phone can be disabled via INTRODUCTIONcarriers. interrupting any of these signals. Because the distance to the base station is larger than the distance to mobile phone that needs to be blocked, it needs less energy to block signal from base station to phone (Zanger 2002). -

ATTACHMENT 16 7T2712020 Amazon.Com: Cell Phone Signal Booster for Home and Office - Band 66 & Band 4 Mobile Cellular Repeater Boosts 4G Data and Volte Fo
ATTACHMENT 16 7t2712020 Amazon.com: Cell Phone Signal Booster for Home and Office - Band 66 & Band 4 Mobile Cellular Repeater Boosts 4G Data and Volte fo. lletlo RLrsrtL Rerrirn Art . subtotat: $5g.g9 - . Ar.t::urz?. & !..ittr l') a'ii't, I | 1,,,a tta,t.t\ Whole Foods Pa'.)try Buy Again Gift Cards Find a Browsing History - 1 fr:-;:*r'i.lar: f e$!4 €ift Cell Phones & Accessories Carrier Phones Untocked Phones Alexa Buitt-in Phones Accessories Cases Wearable I echnotoql l Proceed to ch€ckout l Cet[ Phones & Accessories ) Accessories ) Signat Boosters : l;,--l Ce[l Phone Signat B. Booster for Home l ETI : and Office - Band 55 a & Band 4 Mobite FREE c Order, Ce[[ular Repeater Detaitr Boosts 4G Data and : a=to FilI Volte for Multiple ln Sti I Users Up to 4,500Sq (Ge |;D ,eq:, ) @ Ft.(17oo/2100 Mhz) : l.ao F. Brand: Phonetone I 17 answered questions I t= t , Price: $189.89 i I @ & FREE Returns Save $10 with coupon. ls" Terms : Sotd b: Pay for 6 $31.65/month by Am, months, interest-free with your I Amazon Prime Rewards @ Visa Item d Card reveaI Avaitabte at a lower price from choos( other selters, potentia[[y without packal free Prime shipping. : @ . (Better VoLTE & Datal - Add al Enhances Volte and 4G data LJ2\ speed signals, enjoy faster t'1 uploads and downtoads to stream videos smoothly. Get Bnr rid of expensive monthly internet fees. Supports D( multiple users simu[taneousty. 2( . ICompatibte With Att Us Roll over image to zoom in Networksl - The booster supports All U.S.