Client Side Penetration Testing
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Scala Infochannel Player Setup Guide
SETUP GUIDE P/N: D40E04-01 Copyright © 1993-2002 Scala, Inc. All rights reserved. No part of this publication, nor any parts of this package, may be copied or distributed, transmitted, transcribed, recorded, photocopied, stored in a retrieval system, or translated into any human or computer language, in any form or by any means, electronic, mechanical, magnetic, manual, or otherwise, or disclosed to third parties without the prior written permission of Scala Incorporated. TRADEMARKS Scala, the exclamation point logo, and InfoChannel are registered trademarks of Scala, Inc. All other trademarks or registered trademarks are the sole property of their respective companies. The following are trademarks or registered trademarks of the companies listed, in the United States and other countries: Microsoft, MS-DOS, Windows, Windows 95, Windows 98, Windows NT, Windows 2000, Windows XP, DirectX, DirectDraw, DirectSound, ActiveX, ActiveMovie, Internet Explorer, Outlook Express: Microsoft Corporation IBM, IBM-PC: International Business Machines Corporation Intel, Pentium, Indeo: Intel Corporation Adobe, the Adobe logo, Adobe Type Manager, Acrobat, ATM, PostScript: Adobe Systems Incorporated TrueType, QuickTime, Macintosh: Apple Computer, Incorporated Agfa: Agfa-Gevaert AG, Agfa Division, Bayer Corporation “Segoe” is a trademark of Agfa Monotype Corporation. “Flash” and “Folio” are trademarks of Bauer Types S.A. Some parts are derived from the RSA Data Security, Inc. MD5 Message-Digest Algorithm. JPEG file handling is based in part on the work of the Independent JPEG Group. Lexsaurus Speller Technology Copyright © 1992, 1997 by Lexsaurus Software Inc. All rights reserved. TIFF-LZW and/or GIF-LZW: Licensed under Unisys Corporation US Patent No. 4,558,302; End-User use restricted to use on only a single personal computer or workstation which is not used as a server. -

Case Study: Internet Explorer 1994..1997
Case Study: Internet Explorer 1994..1997 Ben Slivka General Manager Windows UI [email protected] Internet Explorer Chronology 8/94 IE effort begins 12/94 License Spyglass Mosaic source code 7/95 IE 1.0 ships as Windows 95 feature 11/95 IE 2.0 ships 3/96 MS Professional Developer’s Conference AOL deal, Java license announced 8/96 IE 3.0 ships, wins all but PC Mag review 9/97 IE 4.0 ships, wins all the reviews IE Feature Chronology IE 1.0 (7/14/95) IE 2.0 (11/17/95) HTML 2.0 HTML Tables, other NS enhancements HTML <font face=> Cell background colors & images Progressive Rendering HTTP cookies (arthurbi) Windows Integration SSL Start.Run HTML (MS enhancements) Internet Shortcuts <marquee> Password Caching background sounds Auto Connect, in-line AVIs Disconnect Active VRML 1.0 Navigator parity MS innovation Feature Chronology - continued IE 3.0 (8/12/96) IE 3.0 - continued... IE 4.0 (9/12/97) Java Accessibility Dynamic HTML (W3C) HTML Frames PICS (W3C) Data Binding Floating frames HTML CSS (W3C) 2D positioning Componentized HTML <object> (W3C) Java JDK 1.1 ActiveX Scripting ActiveX Controls Explorer Bars JavaScript Code Download Active Setup VBScript Code Signing Active Channels MSHTML, SHDOCVW IEAK (corporations) CDF (XML) WININET, URLMON Internet Setup Wizard Security Zones DocObj hosting Referral Server Windows Integration Single Explorer ActiveDesktop™ Navigator parity MS innovation Quick Launch, … Wins for IE • Quality • CoolBar, Explorer Bars • Componetization • Great Mail/News Client • ActiveX Controls – Outlook Express – vs. Nav plug-ins -

How to Use Rules in Outlook and Outlook Express to Forward Email
How to use rules in Outlook and Outlook Express to forward email. In Outlook Express (6) 1. Click on the Tools menu and select Options. 2. In options select the Send tab. 3. Make sure the settings for Mail Sending Format has the Plain Text radio button selected. 4. Then click the Plain Text Settings button. 5. Leave the Message format on “MIME”. 6. Uncheck the box at the bottom that says “Indent the original text with…”. 7. Click OK. 8. Now click on the Signatures tab. 9. Make sure if you have a signature(s) listed that the box labeled “Don’t add signatures to Replies and Forwards” is checked. Then click OK. 10. Click on the Tools menu and select Message Rules, and then select Mail. 11. Click on the Mail Rules tab. 12. Click the New Button. 13. In the area labeled 1. Select the Conditions for your rule: Select the box next to Where the Subject line contains specific words (in this example we will use the subject but you could use account or email address if desired). 14. Then in the area labeled 2. Select the Actions for your rule: Select the box next to Forward it to people. 15. In the area labeled 3. Rule Description… click on the blue link that says “contains specific words” then type your member code in the box and click on the Add Button and then click OK. 16. Then in the same area click on the blue link that says “people”, then type in the email address of where you want the email to automatically forward to and then click OK. -

Planning for Internet Explorer and the IEAK
02_Inst.fm Page 15 Monday, October 16, 2000 9:40 AM TWO 2Chapter 2 Planning for Internet Explorer and the IEAK LChapter Syllabus In this chapter, we will look at material covered in the Planning section of Microsoft’s Implementing MCSE 2.1 Addressing Technical Needs, Rules, and Policies and Supporting Microsoft Internet Explorer 5 by using the Internet Explorer Administration Kit exam MCSE 2.2 Planning for Custom (70-080). After reading this chapter, you should be Installations and Settings able to: MCSE 2.3 Providing Multiple • Identify and evaluate the technical needs of business Language Support units, such as Internet Service Providers (ISPs), con- tent providers, and corporate administrators. MCSE 2.4 Providing Multiple Platform Support • Design solutions based on organizational rules and policies for ISPs, content providers, and corporate MCSE 2.5 Developing Security Strategies administrators. • Evaluate which components to include in a custom- MCSE 2.6 Configuring for Offline ized Internet Explorer installation package for a given Viewing deployment scenario. MCSE 2.7 Replacing Other Browsers • Develop appropriate security strategies for using Internet Explorer at various sites, including public MCSE 2.8 Developing CMAK kiosks, general business sites, single-task-based sites, Strategies and intranet-only sites. 15 02_Inst.fm Page 16 Monday, October 16, 2000 9:40 AM 16 Chapter 2 • Planning for Internet Explorer and the IEAK • Configure offline viewing for various types of users, including gen- eral business users, single-task users, and mobile users. • Develop strategies for replacing other Internet browsers, such as Netscape Navigator and previous versions of Internet Explorer. • Decide which custom settings to configure for Microsoft Outlook Express for a given scenario. -

Getting Started with Outlook Express for Windows 2000/XP Author Marcie Matsuo Revised by Darren Kato
WIN9X015 November 2005 Getting Started With Outlook Express For Windows 2000/XP Author Marcie Matsuo Revised by Darren Kato Introduction.................................................................................................................................1 What is Outlook Express ............................................................................................................1 Requirements ..............................................................................................................................2 Where do I get Outlook Express.................................................................................................2 Issues...........................................................................................................................................2 POP and IMAP ...........................................................................................................................2 Installing Outlook Express..........................................................................................................3 Configuring Outlook Express .....................................................................................................3 Using Outlook Express ...............................................................................................................9 Importing Messages From Other Mail Programs .....................................................................12 Using the Address Book ...........................................................................................................14 -
How to Backup&Restore Outlook Express Emails,Addressbook,Mail
How to Backup&Restore Outlook Express emails,Addressbook,mail acco... http://www.windowsreference.com/outlook-express/how-to-backup-resto... Windows Reference Windows 7 2008 2003 Vista XP 2000 Ms Office Tutorials Fixes Tips Home About Privacy Policy Top Posts Sitemap Search Manage Active Directory Streamline Active Directory Management. Free 30-day Trial www.systemtools.com Dell Tape Storage Find Powerful Storage Solutions. Shop the Dell™ Official Site Today! www.Dell.com/IN/Storage Hard Disk Recovery Tool Data recovery for Windows. Disk recovery and file undeletion. www.file-recovery.easis.com By vistafix | Comments (0) | Trackbacks (0) | Email This Post If you're new here, you may want to subscribe to Windows Reference RSS feed Thanks for visiting! Outlook Express backup and restore is not as simple as it is in Ms Outlook. The following procedure will help you with a step by step procedure on backup and restore of Ms Outlook Express. This should work on Outlook Express 5 & 6 and as you are aware there is no Outlook Express 7. The procedure involves 1. Backing up emails 2. Backing up (export) Address Book 3. Backing up (export) Mail Accounts Backup EMails Backup the outlook Express mails to a seperate folder by doing the following: 1. Open Outlook Express, click Tools and then Options. 2. Click the Maintenance tab then Store Folder. 1 of 6 3/20/2011 08:31 How to Backup&Restore Outlook Express emails,Addressbook,mail acco... http://www.windowsreference.com/outlook-express/how-to-backup-resto... 3. Copy the storage location path. 4. Click Cancel, Cancel to close the dialog box. -

Outlook Security
E-mail Security in the Wake of Recent Malicious Code Incidents By: Trent Pitsenbarger and Paul Bartock of the Systems and Network Attack Center (SNAC) [email protected] Acknowledgments: The authors would like to acknowledge Neal Ziring and Dave Albanese, NSA and Sean Finnegan, Microsoft for their contributions. Dated: Jan 29, 2002 Version 2.6 UNCLASSIFIED Warnings Do not attempt to implement any of the settings in this guide without first testing in a non-operational environment. This document is only a guide containing recommended security settings. It is not meant to replace well-structured policy or sound judgment. Furthermore this guide does not address site-specific configuration issues. Care must be taken when implementing this guide to address local operational and policy concerns. SOFTWARE IS PROVIDED "AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE EXPRESSLY DISCLAIMED. IN NO EVENT SHALL THE CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE. Please keep track of the latest security patches and advisories at the Microsoft security bulletin page at http://www.microsoft.com/technet/security/current.asp. This document contains possible recommended settings for the system Registry. -

Introduction to Outlook Express 6 with IMAP
Introduction to Outlook Express 6 with IMAP Version 3 – May 2006 Massachusetts Institute of Technology Getting Started This Quick Start class assumes that: 1. Outlook Express is configured for use at MIT. If you need help with configuration please see Outlook Express for Windows: Setting up for Use at MIT (http://itinfo.mit.edu/article?id=7876). 2. If you are migrating from another email program such as Eudora it is assumed that process has already taken place. For information about migrating see Email Migration at MIT (http://web.mit.edu/ist/topics/email/migration.html). 3. You are familiar with the features of at least one email program. The Outlook Express Window The first time you open Outlook Express your window may look like the window below. This is the Outlook Express screen which appears by default. Click the check box in the lower left to go directly to your inbox the next time you open Outlook Express. This picture shows a typical Outlook Express Window after using it for a while. Local Folders Message List Folder List IMAP Folders Preview Pane Contacts List Outlook Express Quick Start Guide v3 Page 2 http://web.mit.edu/ist/topics/email/migration.htm [email protected] The Basics: Read and Send Email Reading Email Messages After Outlook Express downloads your messages, or after you click the Send/Recv button on the toolbar, you can read messages either in a message window or in the preview pane. 1. Click the Inbox icon on the Folders list under poXX.mit.edu (XX is your po box number, e.g., po14.mit.edu) to show the mail in your inbox. -

Download Chapter
Chapter 2 Chapter 2: Protection at the Client Level.......................................................................................19 Virus Entry Points..........................................................................................................................19 Securing the Desktop—Client Protection 101...............................................................................20 Choosing Antivirus Client Software..................................................................................20 Common Vendors of Antivirus Client Software ...................................................21 General Recommendations ................................................................................................22 Netscape Mail ........................................................................................................22 Qualcomm Eudora .................................................................................................22 Outlook Security Update................................................................................................................23 Understanding the Outlook Security Update .....................................................................23 Demoting Attachments to Level-2.....................................................................................29 Installing the Office Update for Outlook 2000..................................................................30 Desktop Configuration Best Practices ...........................................................................................31 -

Set up an Outlook Express E-Mail Account
Set Up an Outlook Express E-Mail Account The Internet Connection Wizard makes short work of setting up your online mailbox by walking you through each step for every e-mail account you set up. 1. Before you get going, make sure you know your email address along with your password. (You may have to contact CRMU if you are unsure.) 2. Start Outlook Express, and on the Tools menu, click Accounts. If the Internet Connection Wizard starts up automatically, skip ahead to step 4. 3. Click Add, and then click Mail to open the Internet Connection Wizard. Mail option from the Add button 4. On the Your Name page of the wizard, type your name as you want it to appear to everyone who gets e-mail from you, and then click Next. Most people use their full name, but you can use any name—even a nickname—that people will recognize. 5. On the Internet Explorer Address page, type your e-mail address, and then click Next. 6. On the E-mail Server Names page, fill in the incoming mail server with pop3.crmu.net and the outgoing mail server with smtp.crmu.net then click Next. pop3.crmu.net smtp.crmu.net 7. On the Internet Mail Logon page, your account name should appear in the box but you will need to type in your password. Remember that your password is case sensitive. Username will appear here Put in your password here 8. Click Next, and then click Finish. . -
Windows Outlook Express Email Instructions Outlook Express 5.02
Windows Outlook Express Email Instructions Outlook Express 5.02 and higher -Setup for Windows Need to print this article? Click Here for the Adobe Acrobat version (requires Adobe Acrobat Reader). This document will guide you through the configuration of Outlook Express for the HANSAE email system. You will need to have MS Outlook Express v5.02 or higher installed, and a working Internet connection. IMPORTANT: First of all, Check your DNS server address (especially Vietnam user) Click Here for further Information Once you have Outlook Express open: 1. Click Tools 2. Click Accounts 3. You should see this window: 4. Click Add 5. Click Mail 6. Enter your name, as you would like it to appear in Display name field of messages that you send. 7. Click Next 8. Enter your email address 9. Click Next Most mail programs are capable of using two different protocols for checking e-mail: the Post Office Protocol (POP3) and the Internet Mail Access Protocol (IMAP). See Choosing IMAP or POP3 at the end of this document to decide which is right for you. (We highly recommend POP3 J). 10. Select POP3 for the server. 11. Enter your email server information: The incoming mail server is mail.hansae.com (Korea user) mailvn.hansae.com (Vietnam user) The outgoing mail server is mail.hansae.com (Korea user) mailvn.hansae.com (Vietnam user) 12. Click Next 13. Enter your user ID and password in the Account name and Password fields. Check Remember password if you do not want to enter you password every time you use you outlook express. -
Microsoft Windows XP Endoworks® 7
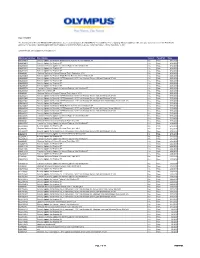
Date: 9/12/2013 The following list of Microsoft Windows XP updates have been tested and approved for EndoWorks 7 compatibility. Prior to applying Windows Updates, make sure your system is current with EndoWorks patches. For questions regarding applying Microsoft Updates or EndoWorks Patches, please contact Olympus Technical Assistance Center. EndoWorks does not support Internet Explorer 7. Windows Updates Description Tested Pass/Fail Date KB2834903 Security Update for Windows Media Format Runtime 9.5 for Windows XP Yes Pass 9/12/2013 KB2864063 Security Update for Windows XP Yes Pass 9/12/2013 KB2870699 Cumulative Security Update for Internet Explorer 6 for Windows XP Yes Pass 9/12/2013 KB2876217 Security Update for Windows XP Yes Pass 9/12/2013 KB2876315 Security Update for Windows XP Yes Pass 9/12/2013 KB890830 Windows Malicious Software Removal Tool - September 2013 Yes Pass 9/12/2013 KB2834903 Security Update for Windows Media Format Runtime 9.5 for Windows XP Yes Pass 8/25/2013 KB2844285 Security Update for Microsoft .NET Framework 2.0 SP2 on Windows Server 2003 and Windows XP x86 Yes Pass 8/25/2013 KB2849470 Security Update for Windows XP Yes Pass 8/25/2013 KB2850869 Security Update for Windows XP Yes Pass 8/25/2013 KB2859537 Security Update for Windows XP Yes Pass 8/25/2013 KB2862772 Cumulative Security Update for Internet Explorer 6 for Windows XP Yes Pass 8/25/2013 KB2863058 Update for windows XP Yes Pass 8/25/2013 KB890830 Windows Malicious Software Removal Tool - August 2013 Yes Pass 8/25/2013 KB2832411 Security Update for Microsoft