Vista Kernel Systems Management Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

PL/SQL Multi-Diagrammatic Source Code Visualization
SQLFlow: PL/SQL Multi-Diagrammatic Source Code Visualization Samir Tartir Ayman Issa Department of Computer Science University of the West of England (UWE), University of Georgia Coldharbour Lane, Frenchay, Bristol BS16 1QY Athens, Georgia 30602 United Kingdom USA Email: [email protected] Email: [email protected] ABSTRACT: A major problem in software introducing new problems to other code that was perfectly maintenance is the lack of a well-documented source code working before. Therefore, educating programmers about in software applications. This has led to serious the behaviors of the target code before start modifying it difficulties in software maintenance and evolution. In is not an easy task. Source code visualization is one of the particular, for those developers who are faced with the heavily used techniques in the literature to overcome this task of fixing or modifying a piece of code they never lack of documentation problem, and its consequent even knew existed before. Database triggers and knowledge-sharing problem [7, 9]. procedures are parts of almost every application, are typical examples of badly documented software Therefore, this research aims at investigating the current components being the hidden back end of software database source code visualization tools and identifying applications. Source code visualization is one of the the main open issues for research. Consequently, the heavily used techniques in the literature so as to mostly used PL/SQL database programming language has familiarize software developers with new source code, been selected for a flowcharting reverse engineering and compensate for the knowledge-sharing problem. prototype tool called "SQLFlow". SQLFlow has been Therefore, a new PL/SQL flowcharting reverse designed, implemented, and tested to parse the target engineering tool, SQLFlow, has been designed and PL/SQL code stored in database procedures, analyze its developed. -

A Prolog-Based Proof Tool for Type Theory Taλ and Implicational Intuitionistic-Logic
A Prolog-based Proof Tool for Type Theory TAλ and Implicational Intuitionistic-Logic L. Yohanes Stefanus University of Indonesia Depok 16424, Indonesia [email protected] and Ario Santoso∗ Technische Universit¨atDresden Dresden 01187, Germany [email protected] Abstract Studies on type theory have brought numerous important contributions to computer science. In this paper we present a GUI-based proof tool that provides assistance in constructing deductions in type theory and validating implicational intuitionistic-logic for- mulas. As such, this proof tool is a testbed for learning type theory and implicational intuitionistic-logic. This proof tool focuses on an important variant of type theory named TAλ, especially on its two core algorithms: the principal-type algorithm and the type inhabitant search algorithm. The former algorithm finds a most general type assignable to a given λ-term, while the latter finds inhabitants (closed λ-terms in β-normal form) to which a given type can be assigned. By the Curry{Howard correspondence, the latter algorithm provides provability for implicational formulas in intuitionistic logic. We elab- orate on how to implement those two algorithms declaratively in Prolog and the overall GUI-based program architecture. In our implementation, we make some modification to improve the performance of the principal-type algorithm. We have also built a web-based version of the proof tool called λ-Guru. 1 Introduction In 1902, Russell revealed the inconsistency in naive set theory. This inconsistency challenged the foundation of mathematics at that time. To solve that problem, type theory was introduced [1, 5]. As time goes on, type theory becomes widely used, it becomes a logician's standard tool, especially in proof theory. -

PC Literacy II
Computer classes at The Library East Brunswick Public Library PC Literacy II Common Window Elements Most windows have common features, so once you become familiar with one program, you can use that knowledge in another program. Double-click the Internet Explorer icon on the desktop to start the program. Locate the following items on the computer screen. • Title bar: The top bar of a window displaying the title of the program and the document. • Menu bar: The bar containing names of menus, located below the title bar. You can use the menus on the menu bar to access many of the tools available in a program by clicking on a word in the menu bar. • Minimize button: The left button in the upper-right corner of a window used to minimize a program window. A minimized program remains open, but is visible only as a button on the taskbar. • Resize button: The middle button in the upper-right corner of a window used to resize a program window. If a program window is full-screen size it fills the entire screen and the Restore Down button is displayed. You can use the Restore Down button to reduce the size of a program window. If a program window is less than full-screen size, the Maximize button is displayed. You can use the Maximize button to enlarge a program window to full-screen size. • Close button: The right button in the upper-right corner of a window used to quit a program or close a document window – the X • Scroll bars: A vertical bar on the side of a window and a horizontal bar at the bottom of the window are used to move around in a document. -

Powerview Command Reference
PowerView Command Reference TRACE32 Online Help TRACE32 Directory TRACE32 Index TRACE32 Documents ...................................................................................................................... PowerView User Interface ............................................................................................................ PowerView Command Reference .............................................................................................1 History ...................................................................................................................................... 12 ABORT ...................................................................................................................................... 13 ABORT Abort driver program 13 AREA ........................................................................................................................................ 14 AREA Message windows 14 AREA.CLEAR Clear area 15 AREA.CLOSE Close output file 15 AREA.Create Create or modify message area 16 AREA.Delete Delete message area 17 AREA.List Display a detailed list off all message areas 18 AREA.OPEN Open output file 20 AREA.PIPE Redirect area to stdout 21 AREA.RESet Reset areas 21 AREA.SAVE Save AREA window contents to file 21 AREA.Select Select area 22 AREA.STDERR Redirect area to stderr 23 AREA.STDOUT Redirect area to stdout 23 AREA.view Display message area in AREA window 24 AutoSTOre .............................................................................................................................. -

LIGO Data Analysis Software Specification Issues
LASER INTERFEROMETER GRAVITATIONAL WAVE OBSERVATORY - LIGO - CALIFORNIA INSTITUTE OF TECHNOLOGY MASSACHUSETTS INSTITUTE OF TECHNOLOGY Document Type LIGO-T970100-A - E LIGO Data Analysis Software Specification Issues James Kent Blackburn Distribution of this draft: LIGO Project This is an internal working document of the LIGO Project. California Institute of Technology Massachusetts Institute of Technology LIGO Project - MS 51-33 LIGO Project - MS 20B-145 Pasadena CA 91125 Cambridge, MA 01239 Phone (818) 395-2129 Phone (617) 253-4824 Fax (818) 304-9834 Fax (617) 253-7014 E-mail: [email protected] E-mail: [email protected] WWW: http://www.ligo.caltech.edu/ Table of Contents Index file /home/kent/Documents/framemaker/DASS.fm - printed July 22, 1997 LIGO-T970100-A-E 1.0 Introduction The subject material discussed in this document is intended to support the design and eventual implementation of the LIGO data analysis system. The document focuses on raising awareness of the issues that go into the design of a software specification. As LIGO construction approaches completion and the interferometers become operational, the data analysis system must also approach completion and become operational. Through the integration of the detector and the data analysis system, LIGO evolves from being an operational instrument to being an operational grav- itational wave detector. All aspects of software design which are critical to the specifications for the LIGO data analysis are introduced with the preface that they will be utilized in requirements for the LIGO data analysis system which drive the milestones necessary to achieve this goal. Much of the LIGO data analysis system will intersect with the LIGO diagnostics system, espe- cially in the areas of software specifications. -

Download Servers Alive V4.1 Documentation
Administrator’s Guide Servers Alive 4.1 Woodstone® bvba i Contents Chapter 1 Quick Start Guide 1 Installation ....................................................................................................................................................2 Getting Started in the Main Window ............................................................................................................6 Technical Support .......................................................................................................................................11 What’s New? ...............................................................................................................................................12 Chapter 2 File Menu 17 Setup Dialog Box (Main Window) .............................................................................................................18 Alerts ...............................................................................................................................................19 Logging............................................................................................................................................53 Output..............................................................................................................................................72 General ............................................................................................................................................91 Built-in Servers..............................................................................................................................102 -

Using Windows XP and File Management
C&NS Summer ’07 Faculty Computer Training Introduction to the Mac Table of Contents Introduction to the Mac....................................................................................................... 1 Mac vs. PC.......................................................................................................................... 2 Introduction to Apple OS X (Tiger).................................................................................... 2 The OS X Interface ......................................................................................................... 3 Tools for accessing items on your computer .................................................................. 3 Menus.............................................................................................................................. 7 Using Windows............................................................................................................... 8 The Dock....................................................................................................................... 10 Using Mac OS X............................................................................................................... 11 Hard Drive Organization............................................................................................... 11 Folder and File Creation, Managing, and Organization ............................................... 12 Opening and Working with Applications .................................................................... -

Eztasktitanium Documentation USER MANUAL
® ezTaskTitanium Documentation USER MANUAL © 2016 ezTask.com, Inc. Table of Contents 2 1. ezTaskTitanium - The Basics 5 1.1 Login to your website ......................................................................................................... 5 1.2 Page Management .............................................................................................................. 6 1.2.1 Sorting Pages ................................................................................................................. 7 1.2.2 Add & Rename a Page .................................................................................................. 8 1.2.3 Copy a Page ................................................................................................................... 9 1.2.4 Set Meta Tags for a Page ............................................................................................ 10 1.3 Page Editing ....................................................................................................................... 11 1.3.1 Drag & Drop ................................................................................................................ 12 2. Layouts 13 2.1 1 Column ............................................................................................................................ 14 2.2 2 Column ............................................................................................................................ 15 2.3 3 Column ........................................................................................................................... -

IDE-JASMIN an Interactive Graphical Approach for Parallel Programming in Scientific Computing
IDE-JASMIN An Interactive Graphical Approach for Parallel Programming in Scientific Computing Liao Li, Zhang Aiqing, Yang Zhang, Wang Wei and Jing Cuiping Institute of Applied Physics and Computational Mathematics, No. 2, East Fenghao Road, Beijing, China Keywords: Parallel Programming, Integrator Component, Integrated Development Environment, Structured Flow Chart. Abstract: A major challenge in scientific computing lays in the rapid design and implementation of parallel applications for complex simulations. In this paper, we develop an interactive graphical system to address this challenge. Our system is based on JASMIN infrastructure and outstands three key features. First, to facilitate the organization of parallel data communication and computation, we encapsulate JASMIN integrator component models as user-configurable components. Second, to support the top-down design of the application, we develop a structured-flow-chart based visual programming approach. Third, to finally generate application code, we develop a powerful code generation engine, which can generate major part of the application code using information in flow charts and component configurations. We also utilize the FORTRAN 90 standard to assist users write numerical kernels. These approaches are integrated and implemented in IDE-JASMIN to ease parallel programming for domain experts. Real applications demonstrate that our approaches for developing complex numerical applications are both practical and efficient. 1 INTRODUCTION data access and manipulation, respectively. Using JASMIN, users need implement several subclasses “J Adaptive Structured Meshes applications of strategy classes in C++ language though they Infrastructure” (JASMIN) is an infrastructure for mainly focus on writing numerical subroutine in structured mesh and SAMR applications for FORTRAN. numerical simulations of complex systems on The limited popularization of JASMIN is parallel computers (Mo et al., 2010). -
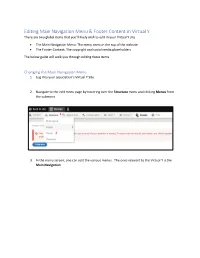
Editing Menu Items in Virtual Y
Editing Main Navigation Menu & Footer Content in Virtual Y There are two global items that you’ll likely wish to edit in your Virtual Y site • The Main Navigation Menu: The menu seen on the top of the website • The Footer Content: The copyright and social media placeholders The below guide will walk you through editing these items. Changing the Main Navigation Menu 1. Log into your association’s Virtual Y Site 2. Navigate to the edit menu page by hovering over the Structure menu and clicking Menus from the submenu 3. In the menu screen, one can edit the various menus. The ones relevant to the Virtual Y is the Main Navigation 4. To edit the menu, click Edit menu button. This will bring you to the screen where you may do the following: a. Edit the name of the menu by clicking Edit and changing the Menu link title on the subsequent screen. b. Removing a menu item by selecting Delete from the Operations drop down list c. Disable the menu (without removing it) by unchecking the Enabled checkbox and clicking Save d. Reorder the menus by dragging the menu items via the plus symbol to the desired location order. Change the Footer Menu Content 1. Navigate to the footer content section of the site by hovering on the Structure Menu and clicking the Block Layout Sub Menu item. Then click the Custom Block Library Tab at the top of the page. 2. On the Custom Block Page, you may edit the contents of each of the footer locations by clicking Edit in the Operations Column. -

Breakfast Menu Builder Version 2.0 USER GUIDE
Breakfast Menu Builder Version 2.0 USER GUIDE Overview 2 Navigating Breakfast Menu Builder 2.0 2 Creating a Menu 3 Building a Menu (Month) 4 Building a Menu (Day) 5 Editing a Menu 6 Finalizing and Printing Reports 7 Uploading a Logo 8 2019 NutriStudents K-12 1 © Our Breakfast Menu Builder helps you quickly and easily build your breakfast menus in a fraction of the time needed to manual plan them. We created this tool to help you simplify your breakfast program while improving student participation. **Tip: Print out the Breakfast Market Basket from the Training & Resources tab before you start. To access the Breakfast Menu Builder from the Client Home page, hover your mouse over the breakfast tab in the navigation menu, then click “Breakfast Menu Builder.” The Breakfast Menu Builder will open. The navigation menu has three options: Provides a full list of all the menus you’ve created. Allows you to upload a logo/picture to appear on your printable calendars and Food Production Reports (FPR). Returns you to the Client Home page. 2019 NutriStudents K-12 2 © To create a menu, click “New Menu” on the right side of the page. This opens a window prompting you to create a new menu. Pick the age group for which you would like to plan your menu. The tool uses your selection to determine the USDA grain requirements. If you serve multiple age groups, you may need to plan multiple menus. **Tip: The age groups listed ensure maximum nutritional flexibility and cost savings commonly caused by over-serving. -

Sewart User Manual
SEWCAT USER MANUAL V4.0.6 APRIL 14, 2017 S & S COMPUTING Oak Ridge, TN 37830 SewCat Contents 1. Introduction ................................................................................................................................ 3 1.1 Getting Started ...................................................................................................................... 3 1.2 Frequently Asked Questions (FAQ) ...................................................................................... 5 1.3 Contact Us ............................................................................................................................. 5 1.4 Purchase SewCat.................................................................................................................. 5 1.5 Videos ................................................................................................................................... 6 2. Menus ........................................................................................................................................ 6 2.1 File menu commands ............................................................................................................ 6 2.2 Edit menu command ............................................................................................................. 7 2.3 View menu commands .......................................................................................................... 7 2.4 Tools menu commands ........................................................................................................