I-Sources 08 Mars 2010 08
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

World Drug Report 2008 Report Entrusted UNODC with the Mandate to Publish “Com- Can Be Accessed Via
2008 WORLD DRUG REPORT Acknowledgements This Report was produced in the Policy Analysis and Research Branch under the supervision of Sandeep Chawla, by the Statistics and Survey Section (headed by Angela Me) and the Studies and Threat Analysis Section (headed by Thibault le Pichon). Core Team: Coen Bussink (maps), Philip Davis (data analysis), Laureta Kazanxhiu (maps), Suzanne Kunnen (graphic design and desktop publishing), and Kristina Kuttnig (graphic design and desktop publishing), Theodore Leggett (editorial assistance), Matthew Nice (ATS trends and statistical assistance), Thomas Pietschmann (estimates, trends, market and global analysis, Chapter 2), Catherine Pysden (interactive data), Martin Raithelhuber (coca, opium and cannabis production data and analysis), Wolfgang Rhomberg (database management), Ali Saadeddin (data entry and statistical assistance), Melissa Tullis (project management, global analysis, editorial assistance). The Report also benefited from the work and expertise of many other UNODC staff in Vienna and around the world. UNODC reiterates its appreciation and gratitude to States Members for the reports and information that provided the basis of this edition of the World Drug Report as well as to the International Narcotics Control Board (INCB) and the European Monitoring Centre on Drugs and Drug Addiction (EMCDDA). UNODC would like to thank the Government of Sweden for its continued financial support to the World Drug Report. The boundaries, names and designations used in all maps in this book do not imply official endorsement or acceptance by the United Nations. This publication has not been formally edited. United Nations Publication Sales No. E.08.XI.1 978-92-1-148229-4 CONTENTS Preface 1 Introduction 3 Explanatory notes 5 Executive Summary 7 1. -

Report of the International Narcotics Control Board for 2008
E/INCB/2008/1 preparations containing pseudoephedrine were reported 536. The unsafe practice of sharing needles among in Peru. In July 2008, the Argentine authorities drug abusers remains one of the main causes of HIV identified a case involving the diversion of ephedrine transmission in many countries in South-East Asia. The on a large scale and destroyed a methamphetamine Australian Agency for International Development laboratory in their country. The Board requests the launched the HIV/AIDS Asia Regional Program in Governments of all countries in South America to Chiang Mai, Thailand, in April 2008, to help stop the continue monitoring the licit trade in precursors of spread of HIV/AIDS in South-East Asia through amphetamine-type stimulants, including ephedrine and advocacy, knowledge-sharing and strategic pseudoephedrine traded as raw material or in the form partnerships. The Program, which is expected to last of pharmaceutical preparations, in order to prevent the eight years, involves Governments, regional agencies, diversion of those precursors from licit channels. civil society organizations and drug abuse prevention networks in controlling the spread of HIV transmission associated with drug abuse in Cambodia, China, the C. Asia Lao People’s Democratic Republic, Myanmar, the Philippines and Viet Nam. East and South-East Asia 537. National authorities of countries in East and 1. Major developments South-East Asia continued to report significant seizures of drugs smuggled through the postal system. Large 534. The Board noted the large-scale smuggling of amounts of benzodiazepines and cannabis were seized, illicit drugs into East and South-East Asia from outside but the most often seized drug was methamphetamine. -

Report of the International Narcotics Control Board for 2010
Report of the International Narcotics Control Board involving treatment for cocaine abuse accounted for 510. According to the 2009 AIDS Epidemic Update, 65 per cent of all cases involving treatment for published by the Joint United Nations Programme on substance abuse in 1998, and that figure decreased, in HIV/AIDS and WHO, an estimated 29 per cent of the relative terms, to 49 per cent in 2008. For the past more than 2 million Latin Americans who abuse drugs 10 years, cocaine has been the primary drug of abuse by injection are infected with HIV. HIV epidemics among persons treated for drug problems in the region. among such drug abusers in the region tend to be concentrated in the Southern Cone. It is estimated that 506. Demand for “crack” cocaine appears to be in Argentina alone, almost half of the persons who emerging in some countries in South America. In 2008, abuse drugs by injection are infected with HIV. seizures of “crack” cocaine were reported in Argentina, Brazil, Chile, Paraguay and Venezuela (Bolivarian Republic of). In the Bolivarian Republic of Venezuela, C. Asia lifetime prevalence of the abuse of “crack” cocaine among the population aged 15-70 is 11.9 per cent. In East and South-East Asia that country, about a quarter of the persons who received treatment for drug addiction were addicted to 1. Major developments “crack” cocaine. In 2010, the Government of Brazil launched its integrated plan to combat “crack” cocaine 511. In East and South-East Asia, progress in reducing and other drugs. opium production is under threat, owing to an upswing in opium poppy cultivation during the 2009 growing 507. -

Echogéo, 48 | 2019 Known Unknowns and Unknown Knowns: What We Know About the Cannabis and the Ha
EchoGéo 48 | 2019 Illegal cannabis cultivation in the world Known Unknowns and Unknown Knowns: What we know about the cannabis and the Hashish trade in Afghanistan James Bradford and David Mansfield Electronic version URL: https://journals.openedition.org/echogeo/17626 DOI: 10.4000/echogeo.17626 ISSN: 1963-1197 Publisher Pôle de recherche pour l'organisation et la diffusion de l'information géographique (CNRS UMR 8586) Electronic reference James Bradford and David Mansfield, “Known Unknowns and Unknown Knowns: What we know about the cannabis and the Hashish trade in Afghanistan”, EchoGéo [Online], 48 | 2019, Online since 13 July 2019, connection on 31 July 2021. URL: http://journals.openedition.org/echogeo/17626 ; DOI: https:// doi.org/10.4000/echogeo.17626 This text was automatically generated on 31 July 2021. EchoGéo est mis à disposition selon les termes de la licence Creative Commons Attribution - Pas d'Utilisation Commerciale - Pas de Modification 4.0 International (CC BY-NC-ND) Known Unknowns and Unknown Knowns: What we know about the cannabis and the Ha... 1 Known Unknowns and Unknown Knowns: What we know about the cannabis and the Hashish trade in Afghanistan James Bradford and David Mansfield Introduction 1 In recent decades, Afghanistan has become synonymous with opium. Whether it is the annually-increasing quantities harvested, or the much-publicized connections to insurgent groups like the Taliban, opium is center-stage in the contemporary narrative of Afghanistan. And yet, opium is but one of a broader mosaic of drugs that include heroin, alcohol and more recently methamphetamine, that comprise the illicit drug economy and Afghan drug culture. -
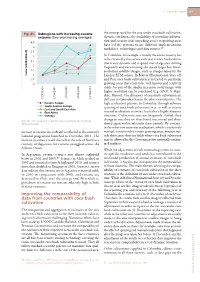
Improving the Comparability of Data from Countries with Coca Bush
C. Cocaine market 41 Fig. 31. Subregions with increasing cocaine the concept used for the area under coca bush cultivation, seizures (Two-year moving averages) climatic conditions, the availability of secondary informa- 4.5 tion and security risks impeding access to growing areas have led the systems to use different implementation 4 modalities, technologies and data sources.87 3.5 3 In Colombia, for example, virtually the entire country has to be covered by the survey each year as coca bush cultiva- 2.5 tion is very dynamic and is spread over a large area, shifting 2 frequently and necessitating the use of larger but lower- 1.5 resolution satellite images, such as images taken by the Index (2005/2006=1) 1 Landsat ETM sensor. In Bolivia (Plurinational State of) 0.5 and Peru coca bush cultivation is restricted to particular 0 growing areas that tend to be well known and relatively stable; because of the smaller area more costly images with higher resolution can be purchased (e.g. SPOT 5, Rapi- deye, Ikonos). The dynamics of coca bush cultivation are 2008/2009 2005/2006 2006/2007 2007/2008 2009/2010 20080/2009 different in Colombia than in the other two countries. The Eastern Europe high eradication pressure in Colombia, through airborne South-Eastern Europe spraying of coca bush cultivation sites, as well as intense East and South-East Asia East Africa manual eradication activities, has led to a highly dynamic Oceania situation. Cultivation sites are frequently shifted, they Source: Annual report questionnaire supplemented by other change in size, they are abandoned, reactivated and aban- official sources. -

The “Afghan Drugs” Problem – a Challenge to Iran and International Security
Vol. 1 — No. 2 — Summer 20102 The “Afghan Drugs” Problem – A Challenge to Iran and International Security Nasser Saghafi-Ameri rs i a ff A n g Nasser Saghafi-Ameri, is a retired career diplomat with 32 years of service, including at the i e Iranian diplomatic posts in Ottawa (1974-78), Stockholm (1980-84), and New Delhi (1992- r 96). He also participated in the Iranian delegations to the United Nations in Geneva and New o F York during the 1986-88 period. While based in Tehran, he worked at the Institute for Political and International Studies – IPIS - and served as the Head of Strategic Studies Group f o (1984-1992) and Director of the Central Asia and Caucasus Studies (1996-2000). His scholarly activities are focused on the Iranian foreign policy, international security, and EW I nuclear disarmament. His published works include five books in Persian and nearly 100 V E R articles in Persian and English. His latest book - "Iran and Look to the East Policy" - was N A published in Persian by the Center for Strategic Research - CSR – in 2008. I N A IR The “Afghan Drugs” Problem... Abstract This article looks in to the issue of the Afghan drugs problems from the international security perspective. The definition of international security has evolved since the end of the cold war. In the past, there were, and there are presently, some people who perceive that only military capabilities of their rivals can pose a threat to their security. That is, while the new definition of international security has expanded to include many issues that are not necessarily in the domain of military or armed forces. -

International Narcotics Control Strategy Report
United States Department of State Bureau for International Narcotics and Law Enforcement Affairs International Narcotics Control Strategy Report Volume I Drug and Chemical Control March 2015 INCSR 2015 Volume 1 Table of Contents Table of Contents Volume 1 Common Abbreviations ............................................................................................................................ iv International Agreements .......................................................................................................................... v Introduction ................................................................................................................................................. 1 Legislative Basis for the INCSR ................................................................................................................ 2 Major Illicit Drug Producing, Drug-Transit, Significant Source, Precursor Chemical, and Money Laundering Countries ................................................................................................................................ 5 Presidential Determination ........................................................................................................................ 7 Policy and Program Developments ......................................................................................................... 18 Overview ................................................................................................................................................. 19 Demand -

Afghanistan Cannabis Survey 2009, April 2010
Islamic Republic of Afghanistan Islamic Republic of Afghanistan Ministry of Counter Narcotics Ministry of Counter Narcotics Vienna International Centre, PO Box 500, 1400 Vienna, Austria Banayee Bus Station, Jalalabad Main Road Tel.: (+43-1) 26060-0, Fax: (+43-1) 26060-5866, www.unodc.org 9th District, Kabul, Afghanistan Tel.: (+93) 799891851, www.mcn.gov.af Afghanistan Survey of Commercial Cannabis Cultivation and Production 2012 2013 R BE M TE P E S 2012 Survey of Commercial Cannabis Cultivation and Production ABBREVIATIONS ANDS Afghanistan National Development Strategy AOPS Annual Opium Poppy Survey CNPA Counter Narcotics Police of Afghanistan ICMP Illicit Crop Monitoring Programme (UNODC) MCN Ministry of Counter-Narcotics NDCS National Drug Control Strategy UNODC United Nations Office on Drugs and Crime ACKNOWLEDGEMENTS The following organizations and individuals contributed to the implementation of the survey of commercial cannabis cultivation and production and to the preparation of this report: Ministry of Counter-Narcotics Mohammad Ibrahim Azhar (Deputy Minister), Haroon Rashid Sherzad (Deputy Minister), Mir Abdullah Sadat (Director Narcotics Survey Directorate), Saraj Ahmad (Deputy Director of Narcotics Survey Directorate), Hamida Hussaini (Administration Officer). Survey Coordinators: Eshaq Masumi (Central Region), Abdul Mateen (Eastern Region), Abdul Latif Ehsan (Western Region), Fida Mohammad (Northern Region), Mohammed Ishaq Anderabi (North-Eastern Region), Khalil Ahmad (Southern Region), Khiali Jan Mangal (Eradication Verification -
![Echogéo, 48 | 2019, “Illegal Cannabis Cultivation in the World” [Online], Online Since 13 July 2019, Connection on 31 July 2021](https://docslib.b-cdn.net/cover/9092/echog%C3%A9o-48-2019-illegal-cannabis-cultivation-in-the-world-online-online-since-13-july-2019-connection-on-31-july-2021-5239092.webp)
Echogéo, 48 | 2019, “Illegal Cannabis Cultivation in the World” [Online], Online Since 13 July 2019, Connection on 31 July 2021
EchoGéo 48 | 2019 Illegal cannabis cultivation in the world Electronic version URL: https://journals.openedition.org/echogeo/17489 DOI: 10.4000/echogeo.17489 ISSN: 1963-1197 Publisher Pôle de recherche pour l'organisation et la diffusion de l'information géographique (CNRS UMR 8586) Electronic reference EchoGéo, 48 | 2019, “Illegal cannabis cultivation in the world” [Online], Online since 13 July 2019, connection on 31 July 2021. URL: https://journals.openedition.org/echogeo/17489; DOI: https:// doi.org/10.4000/echogeo.17489 This text was automatically generated on 31 July 2021. EchoGéo est mis à disposition selon les termes de la licence Creative Commons Attribution - Pas d'Utilisation Commerciale - Pas de Modification 4.0 International (CC BY-NC-ND) 1 TABLE OF CONTENTS Editorial Marijuana et haschich, regards sur le cannabis Jean-Louis Chaléard Marijuana and hashish: perspectives on cannabis Editorial Jean-Louis Chaléard Sur le Champ Illegal cannabis cultivation in the world Illegal cannabis cultivation in the world, and as a subject in academic research Introduction Pierre-Arnaud Chouvy Cannabis cultivation in the world: heritages, trends and challenges Pierre-Arnaud Chouvy A brief agricultural history of cannabis in Africa, from prehistory to canna-colony Chris S. Duvall Turning Cannabis Into Cash: Agrarian Change and Lesotho’s Evolving Experience Julian Bloomer Living Dangerously: Confronting Insecurity, Navigating Risk, and Negotiating Livelihoods in the Hidden Economy of Congo’s Cannabis Trade Ann Laudati Known Unknowns and Unknown -

Analysing Phenological Characteristics Extracted from Landsat NDVI Time Series to Identify Suitable Image Acquisitiondatesforcannabismappinginafghanistan
PFG 2014 / 5, 0383–0392 Article Stuttgart, October 2014 Analysing Phenological Characteristics Extracted from Landsat NDVI Time Series to Identify Suitable Image AcquisitionDatesforCannabisMappinginAfghanistan MATTEO MATTIUZZI,COEN BUSSINK &THOMAS BAUER, Vienna, Austria Keywords: illicitcropmonitoring,cannabis,NDVI,phenology,seasonality,senescence Summary: Since2009,theUnitedNationsOffice Zusammenfassung: Analyse phänologischer Ei- on Drugs and Crime (UNODC) has carried out genschaften basierend auf Landsat NDVI Zeitrei- various annual surveys of cannabis cultivation in hen für die Bestimmung geeigneter Zeitpunkte für Afghanistan. The mapping of cannabis fields is die Aufnahme von Satellitenbildern für die Kartie- based on very high resolution satellite imagery. The rung von Cannabis in Afghanistan. Das Büro für image acquisition dates have a strong influence on Drogen- und Verbrechensbekämpfung der Verein- whether cannabis can be visually differentiated ten Nationen (UNODC) führt seit 2009 jährlich from other crops. Expert knowledge shows that the eine Auswertung der Anbaufläche von Cannabis in idealacquisitiondatesareattheendofthegrowing Afghanistan durch. Die Kartierung von Cannabis- period (senescence) of cannabis. For future surveys feldernerfolgtmitHilfevonsehrhochauflösenden amethodwasdevelopedtopredicttheoptimumob- Fernerkundungsdaten. Der Aufnahmezeitpunkt servationdatesindependentoftemporaldifferenc- der Daten ist sehr bedeutend dafür, ob Cannabis es of the phenology. The study includes an analysis von anderen Feldfrüchten visuell -

Cannabis Use and Its Health Consequences in Afghanistan: Implication for Intervention and Prevention
Georgia State University ScholarWorks @ Georgia State University Public Health Theses School of Public Health 8-13-2013 Cannabis Use and Its Health Consequences in Afghanistan: Implication for Intervention and Prevention Mohammad Ajmal Yasin School of Public Health Follow this and additional works at: https://scholarworks.gsu.edu/iph_theses Recommended Citation Yasin, Mohammad Ajmal, "Cannabis Use and Its Health Consequences in Afghanistan: Implication for Intervention and Prevention." Thesis, Georgia State University, 2013. https://scholarworks.gsu.edu/iph_theses/291 This Thesis is brought to you for free and open access by the School of Public Health at ScholarWorks @ Georgia State University. It has been accepted for inclusion in Public Health Theses by an authorized administrator of ScholarWorks @ Georgia State University. For more information, please contact [email protected]. Cannabis Use and Its Health Consequences in Afghanistan: Implication for Intervention and Prevention by Doctor Mohammad Ajmal Yasin M.D., Kandahar University A Capstone Submitted to the Graduate Faculty of Georgia State University in Partial Fulfillment of the Requirements for the Degree MASTER OF PUBLIC HEALTH ATLANTA, GEORGIA 30303 i Table of content Page Acknowledgements ........................................................................................................................ iii Dedication ...................................................................................................................................... iv Approval Page -

International Narcotics Control Strategy Report
United States Department of State Bureau for International Narcotics and Law Enforcement Affairs International Narcotics Control Strategy Report Volume I Drug and Chemical Control March 2013 INCSR 2013 Volume 1 Table of Contents Table of Contents Common Abbreviations ............................................................................................................................ iv International Agreements ......................................................................................................................... vi Introduction ................................................................................................................... 1 Legislative Basis for the INCSR ................................................................................................................ 2 Presidential Determination ........................................................................................................................ 5 Major Illicit Drug Producing, Drug-Transit, Significant Source, Precursor Chemical, and Money Laundering Countries .............................................................................................................................. 13 Policy and Program Developments ........................................................................... 15 Overview ................................................................................................................................................. 16 Demand Reduction ................................................................................................................................