CERN Articles on Computer Security Written by the CERN Computer Security Team (
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

IJIMAI20163 6.Pdf
INTERNATIONAL JOURNAL OF INTERACTIVE MULTIMEDIA AND ARTIFICIAL INTELLIGENCE ISSN: 1989-1660–VOL. III, NUMBER 6 IMAI RESEARCH GROUP COUNCIL Executive Director - Dr. Jesús Soto Carrión, Pontifical University of Salamanca, Spain Research Director - Dr. Rubén González Crespo, Universidad Internacional de La Rioja - UNIR, Spain Financial Director - Dr. Oscar Sanjuán Martínez, ElasticBox, USA Office of Publications Director - Lic. Ainhoa Puente, Universidad Internacional de La Rioja - UNIR, Spain Director, Latin-America regional board - Dr. Carlos Enrique Montenegro Marín, Francisco José de Caldas District University, Colombia EDITORIAL TEAM Editor-in-Chief Dr. Rubén González Crespo, Universidad Internacional de La Rioja – UNIR, Spain Associate Editors Dr. Jordán Pascual Espada, ElasticBox, USA Dr. Juan Pavón Mestras, Complutense University of Madrid, Spain Dr. Alvaro Rocha, University of Coimbra, Portugal Dr. Jörg Thomaschewski, Hochschule Emden/Leer, Emden, Germany Dr. Carlos Enrique Montenegro Marín, Francisco José de Caldas District University, Colombia Dr. Vijay Bhaskar Semwal, Indian Institute of Technology, Allahabad, India Editorial Board Members Dr. Rory McGreal, Athabasca University, Canada Dr. Abelardo Pardo, University of Sidney, Australia Dr. Hernán Sasastegui Chigne, UPAO, Perú Dr. Lei Shu, Osaka University, Japan Dr. León Welicki, Microsoft, USA Dr. Enrique Herrera, University of Granada, Spain Dr. Francisco Chiclana, De Montfort University, United Kingdom Dr. Luis Joyanes Aguilar, Pontifical University of Salamanca, Spain Dr. Ioannis Konstantinos Argyros, Cameron University, USA Dr. Juan Manuel Cueva Lovelle, University of Oviedo, Spain Dr. Pekka Siirtola, University of Oulu, Finland Dr. Francisco Mochón Morcillo, National Distance Education University, Spain Dr. Manuel Pérez Cota, University of Vigo, Spain Dr. Walter Colombo, Hochschule Emden/Leer, Emden, Germany Dr. Javier Bajo Pérez, Polytechnic University of Madrid, Spain Dr. -
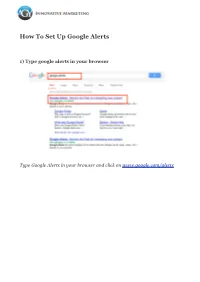
How to Set up Google Alerts
How To Set Up Google Alerts 1) Type google alerts in your browser Type Google Alerts in your browser and click on www.google.com/alerts 2) Set up your alerts In Search Query put in the topics you want google to source out for you. It might be of interest to have your name, your company domain, competitors domains, keywords you'd like to source information about or whatever you'd like to research. Enter the email address you want the alerts to go to. 3) Verify your alert Login into your email address that the alert is going to and verify it by clicking on the link. 4) Set up folders/labels so alerts skip your inbox (we will use Gmail for this example) 1) Tick the alerts that have come to your inbox. 2) Click on More, in the drop down menu choose 'Filter messages like these' 5) Create filter 1) Just click on 'create filter with this search' 6) Applying label/folder for alert to skip inbox. (Gmail calls folders labels, you can set them up under 'settings', 'labels'. 1) Tick skip the inbox (helps keep your inbox free) 2) Tick apply label 3) Choose what label (Here we have called it Alerts) 4) Tick to apply other alerts if found any 5) Create filter This is one easy way for information you are interested in to come to you. By setting up Alert Folders or Labels as Gmail calls them, they won't clog up your inbox, keeping it clear and leaving you to your choosing when you want to check your alerts for any useful information. -

Alcatel-Lucent Security Advisory Sa0xx
Alcatel-Lucent Security Advisory No. SA0053 Ed. 04 Information about Poodle vulnerability Summary POODLE stands for Padding Oracle On Downgraded Legacy Encryption. The POODLE has been reported in October 14th 2014 allowing a man-in-the-middle attacker to decrypt ciphertext via a padding oracle side-channel attack. The severity is not considered as the same for Heartbleed and/or bash shellshock vulnerabilities. The official risk is currently rated Medium. The classification levels are: Very High, High, Medium, and Low. The SSLv3 protocol is only impacted while TLSv1.0 and TLSv1.2 are not. This vulnerability is identified CVE- 2014-3566. Alcatel-Lucent Enterprise voice products using protocol SSLv3 are concerned by this security alert. Openssl versions concerned by the vulnerability: OpenSSL 1.0.1 through 1.0.1i (inclusive) OpenSSL 1.0.0 through 1.0.0n (inclusive) OpenSSL 0.9.8 through 0.9.8zb (inclusive) The Alcatel-Lucent Enterprise Security Team is currently investigating implications of this security flaw and working on a corrective measure, for OpenTouch 2.1.1 planned in Q4 2015, to prevent using SSLv3 that must be considered as vulnerable. This note is for informational purpose about the padding-oracle attack identified as “POODLE”. References CVE-2014-3566 http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-3566 Advisory severity CVSS Base score : 4.3 (MEDIUM) - AV:N/AC:M/Au:N/C:P/I:N/A:N https://www.openssl.org/news/secadv_20141015.txt https://www.openssl.org/~bodo/ssl-poodle.pdf Description of the vulnerabilities Information about Poodle vulnerability (CVE-2014-3566). -

Internet Security Threat Report VOLUME 21, APRIL 2016 TABLE of CONTENTS 2016 Internet Security Threat Report 2
Internet Security Threat Report VOLUME 21, APRIL 2016 TABLE OF CONTENTS 2016 Internet Security Threat Report 2 CONTENTS 4 Introduction 21 Tech Support Scams Go Nuclear, 39 Infographic: A New Zero-Day Vulnerability Spreading Ransomware Discovered Every Week in 2015 5 Executive Summary 22 Malvertising 39 Infographic: A New Zero-Day Vulnerability Discovered Every Week in 2015 8 BIG NUMBERS 23 Cybersecurity Challenges For Website Owners 40 Spear Phishing 10 MOBILE DEVICES & THE 23 Put Your Money Where Your Mouse Is 43 Active Attack Groups in 2015 INTERNET OF THINGS 23 Websites Are Still Vulnerable to Attacks 44 Infographic: Attackers Target Both Large and Small Businesses 10 Smartphones Leading to Malware and Data Breaches and Mobile Devices 23 Moving to Stronger Authentication 45 Profiting from High-Level Corporate Attacks and the Butterfly Effect 10 One Phone Per Person 24 Accelerating to Always-On Encryption 45 Cybersecurity, Cybersabotage, and Coping 11 Cross-Over Threats 24 Reinforced Reassurance with Black Swan Events 11 Android Attacks Become More Stealthy 25 Websites Need to Become Harder to 46 Cybersabotage and 12 How Malicious Video Messages Could Attack the Threat of “Hybrid Warfare” Lead to Stagefright and Stagefright 2.0 25 SSL/TLS and The 46 Small Business and the Dirty Linen Attack Industry’s Response 13 Android Users under Fire with Phishing 47 Industrial Control Systems and Ransomware 25 The Evolution of Encryption Vulnerable to Attacks 13 Apple iOS Users Now More at Risk than 25 Strength in Numbers 47 Obscurity is No Defense -

Combat Top Security Vulnerabilities: HPE Tippingpoint Intrusion
Business white paper Combat top security vulnerabilities HPE TippingPoint intrusion prevention system Business white paper Page 2 The year 2014 marked a new pinnacle for hackers. Vulnerabilities were uncovered in some of the most widely deployed software in the world—some of it in systems actually intended to make you more secure. HPE TippingPoint next-generation intrusion prevention system (IPS) and next-generation firewall (NGFW) customers rely on us to keep their networks safe. And when it comes to cyber threats, every second matters. So how did HPE TippingPoint do? This brief highlights the top security vulnerabilities of 2014—the ones that sent corporate security executives scrambling to protect their businesses. And it describes how HPE TippingPoint responded to keep our customers safe. Heartbleed—HPE TippingPoint intrusion prevention system stops blood flow early Any vulnerability is concerning, but when a vulnerability is discovered in software designed to assure security, it leaves businesses exposed and vulnerable. That was the case with the Heartbleed vulnerability disclosed by the OpenSSL project on April 7, 2014. They found the vulnerability in versions of OpenSSL—the open-source cryptographic library widely used to encrypt Internet traffic. Heartbleed grew from a coding error that allowed remote attackers to read information from process memory by sending heartbeat packets that trigger a buffer over-read. As a demonstration of the vulnerability, the OpenSSL Project created a sample exploit that successfully stole private cryptography keys, user names and passwords, instant messages, emails, and business-critical documents and communications. We responded within hours to protect TippingPoint customers. On April 8, we released a custom filter package to defend against the vulnerability. -

IBM X-Force Threat Intelligence Quarterly, 1Q 2015
IBM Security Systems March 2015 IBM X-Force Threat Intelligence Quarterly, 1Q 2015 Explore the latest security trends—from “designer vulns” to mutations in malware— based on 2014 year-end data and ongoing research 2 IBM X-Force Threat Intelligence Quarterly 1Q 2015 Contents Executive overview 2 Executive overview When we look back in history to review and understand the past year, you can be assured it will be remembered as a year of 4 Roundup of security incidents in 2014 significant change. 11 Citadel, the financial malware that continues to adapt In early January 2014, companies large and small scrambled to Are mobile application developers for Android putting their 14 better understand and analyze a major retail breach that left users at risk? them asking whether or not their own security measures would 17 Shaking the foundation: Vulnerability disclosures in 2014 survive the next storm. Before spring was barely in motion, we had our first taste of the “designer vuln”—a critical 21 About X-Force vulnerability that not only proved lethal for targeted attacks, 22 Contributors but also had a cleverly branded logo, website and call-name (or handle) that would forever identify the disclosure. 22 For more information 23 Footnotes These designer vulns appeared within long-held foundational frameworks used by the majority of websites, and they continued throughout 2014, garnering catchy name after catchy name—Heartbleed, Shellshock, POODLE, and into 2015, Ghost and FREAK. This in and of itself raises the question of what it takes for a vulnerability to merit a marketing push, PR and logo design, while the other thousands discovered throughout the year do not. -

TLS Attacks & DNS Security
IAIK TLS Attacks & DNS Security Information Security 2019 Johannes Feichtner [email protected] IAIK Outline TCP / IP Model ● Browser Issues Application SSLStrip Transport MITM Attack revisited Network Link layer ● PKI Attacks (Ethernet, WLAN, LTE…) Weaknesses HTTP TLS / SSL FLAME FTP DNS Telnet SSH ● Implementation Attacks ... ● Protocol Attacks ● DNS Security IAIK Review: TLS Services All applications running TLS are provided with three essential services Authentication HTTPS FTPS Verify identity of client and server SMTPS ... Data Integrity Detect message tampering and forgery, TLS e.g. malicious Man-in-the-middle TCP IP Encryption Ensure privacy of exchanged communication Note: Technically, not all services are required to be used Can raise risk for security issues! IAIK Review: TLS Handshake RFC 5246 = Establish parameters for cryptographically secure data channel Full handshake Client Server scenario! Optional: ClientHello 1 Only with ServerHello Client TLS! Certificate 2 ServerKeyExchange Certificate CertificateRequest ClientKeyExchange ServerHelloDone CertificateVerify 3 ChangeCipherSpec Finished ChangeCipherSpec 4 Finished Application Data Application Data IAIK Review: Certificates Source: http://goo.gl/4qYsPz ● Certificate Authority (CA) = Third party, trusted by both the subject (owner) of the certificate and the party (site) relying upon the certificate ● Browsers ship with set of > 130 trust stores (root CAs) IAIK Browser Issues Overview Focus: Relationship between TLS and HTTP Problem? ● Attacker wants to access encrypted data ● Browsers also have to deal with legacy websites Enforcing max. security level would „break“ connectivity to many sites Attack Vectors ● SSLStrip ● MITM Attack …and somehow related: Cookie Stealing due to absent „Secure“ flag… IAIK Review: ARP Poisoning How? Attacker a) Join WLAN, ● Sniff data start ARP Poisoning ● Manipulate data b) Create own AP ● Attack HTTPS connections E.g. -

3. Internet – Participating in the Knowledge Society
3. Internet – Participating in the knowledge society “Knowledge is power. Information is liberating. Education is the premise of progress, in every society, in every family.” Kofi Annan, former Secretary General of the United Nations, January 1997-December 2006 CHECKLIST FACT SHEET 10 – SEARCHING FOR INFORMATION Do you read the disclaimer when you are consulting a website? How can you be sure the information you find is factual and objective? Do you consult several websites to check your facts? CHECKLIST FACT SHEET 11 – FINDING QUALITY INFORMATION ON THE WEB Before downloading files, do you check that your anti-virus software is active? If you get your news from the Internet, do you seek multiple perspectives on the same story? Clean out your cookies from time to time to avoid being “profiled” by search engines. CHECKLIST FACT SHEET 12 – DISTANCE LEARNING AND MOOCs Choose a method of distance learning that is appropriate for you: determine what type of learning (synchronous, asynchronous, open schedule, hybrid distance learning) will best help you reach your goals. Before selecting a distance learning course, research the reviews – both from students and teachers. Take adequate precautions to ensure that your computer equipment and software is secure from hackers, viruses and other threats. CHECKLIST FACT SHEET 13 – SHOPPING ONLINE Do not make online purchases on unsecure Internet connections. Understand and agree to the key information provided about the product or service. Disable in-app purchases on your smartphone or tablet. Do not believe all user recommendations you see, creating “user” recommendations can also be a money-making business. Fact sheet 11 Finding quality information on the Web he original idea behind the creation of the Internet1 was to develop an electronic library for the Teasy access and distribution of information2. -

Efficient Monitoring Algorithm for Fast News Alerts
1 Efficient Monitoring Algorithm for Fast News Alerts Ka Cheung Sia, Junghoo Cho, and Hyun-Kyu Cho Abstract— Recently, there has been a dramatic increase in and its appearance at the aggregator? Note that the aggregation the use of XML data to deliver information over the Web. can be done either at a desktop (e.g., RSS feed readers) or at Personal weblogs, news Web sites, and discussion forums are a central server (e.g., Personalized Yahoo/Google homepage). now publishing RSS feeds for their subscribers to retrieve new postings. As the popularity of personal weblogs and the RSS While some of our developed techniques can be applied to the feeds grow rapidly, RSS aggregation services and blog search desktop-based aggregation, in this paper we primarily focus on engines have appeared, which try to provide a central access the server-based aggregation scenario. This problem is similar point for simpler access and discovery of new content from a to the index refresh problem for Web-search engines [7], [9], large number of diverse RSS sources. In this paper, we study how [11], [13], [15], [30], [31], [40], but two important properties the RSS aggregation services should monitor the data sources to retrieve new content quickly using minimal resources and to of the information in the RSS domain make this problem provide its subscribers with fast news alerts. We believe that unique and interesting: the change characteristics of RSS sources and the general user • The information in the RSS domain is often time sensi- access behavior pose distinct requirements that make this task significantly different from the traditional index refresh problem tive. -

The Software Vulnerability Ecosystem: Software Development in the Context of Adversarial Behavior
University of Pennsylvania ScholarlyCommons Publicly Accessible Penn Dissertations 2016 The Software Vulnerability Ecosystem: Software Development In The Context Of Adversarial Behavior Saender Aren Clark University of Pennsylvania, [email protected] Follow this and additional works at: https://repository.upenn.edu/edissertations Part of the Databases and Information Systems Commons, and the Engineering Commons Recommended Citation Clark, Saender Aren, "The Software Vulnerability Ecosystem: Software Development In The Context Of Adversarial Behavior" (2016). Publicly Accessible Penn Dissertations. 2233. https://repository.upenn.edu/edissertations/2233 This paper is posted at ScholarlyCommons. https://repository.upenn.edu/edissertations/2233 For more information, please contact [email protected]. The Software Vulnerability Ecosystem: Software Development In The Context Of Adversarial Behavior Abstract Software vulnerabilities are the root cause of many computer system security fail- ures. This dissertation addresses software vulnerabilities in the context of a software lifecycle, with a particular focus on three stages: (1) improving software quality dur- ing development; (2) pre- release bug discovery and repair; and (3) revising software as vulnerabilities are found. The question I pose regarding software quality during development is whether long-standing software engineering principles and practices such as code reuse help or hurt with respect to vulnerabilities. Using a novel data-driven analysis of large databases of vulnerabilities, I show the surprising result that software quality and software security are distinct. Most notably, the analysis uncovered a counterintu- itive phenomenon, namely that newly introduced software enjoys a period with no vulnerability discoveries, and further that this “Honeymoon Effect” (a term I coined) is well-explained by the unfamiliarity of the code to malicious actors. -

Exploit Kits, Which Seemed Nearly Dormant Last Year Following the Demise of Illicit Cryptocurrency Mining, the Hot New Thing in 2018, Appear to Be Making a Comeback
2020 TRUSTWAVE GLOBAL SECURITY REPORT Table of Contents Introduction ........................ 3 Threat Intelligence .................22 Email Threats ......................... 23 Executive Summary ................. 4 Extortion Scams ....................... 25 Data Compromises ..................... 4 Archive Mutant Tricks .................. 28 Email Threats .......................... 6 Multi-Stage Phishing Using Web Attacks ........................... 8 Trusted Cloud Providers ................ 29 Exploits ............................... 8 Office 365 Account Phishing ............30 Malware ............................... 9 Emotet: The Threat is in the Mail ......... 33 Database and Network Security ......... 10 Web Attacks .......................... 36 Database Compromise ...............11 Humans: The Lowest Hanging Fruit ....... 38 Compromise Demographics ..............11 Exploits .............................. 39 Compromises Per Environment ...........14 Finding Insights Through Trustwave Fusion ......................44 Environments Compromised by Industry ............................15 Malware ..............................46 Compromises by Region .................17 More and More Magecart ...............50 Compromise Duration ...................18 The State of Security ............... 51 Methods of Compromise .................19 Data Security ......................... 52 Sources of Detection ...................20 Network Security ...................... 56 Contributors ....................... 59 2 Introduction Welcome to the 2020 Trustwave -

Olson's Standard Poodles
Sun-Golden Kennels STANDARD POODLE PUPPY PURCHASE AGREEMENT LIMITED REGISTRATION BREEDER/Seller: Mike or Sharon Long 7812 N. Longview Ct. Edgerton, WI. 53534 608-884-4000 [email protected] www.sungoldenkennels.com Definitions used herein include: "BUYER" shall herein be define as: ___________________________ BREEDER" or “SELLER” Shall herein be defined as: Mike or Sharon Long "PUPPY" shall herein be defined as “A PUPPY”, registered with the American Kennel Club (AKC) with the registered name of: SHARMIK’S________________________________ AKC Litter registration # PRXXXXXX Sire: AKC #PRXXXXXX Reg Name ____________________________________ Dam: AKC# PRXXXXXX Reg Name ___________________________________ The Sun-Golden Standard Poodle described above is sold for the sum of $1000.00 Payment to be made in full with cash or visa/mc. A pet puppy is defined here to be a Standard Poodle puppy which is in good health at the time of sale, and embodies the characteristics of the Standard Poodle breed. This puppy is purebred and the litter has been (registered) with the American Kennel Club. The Parents of this Puppy have had OFA x-rays to establish that they are free of Hip Dysplasia, Elbow disease, Heart disease and Eye disease The puppy is registered with a limited registration, which will prohibit breeding and registering offspring. The BUYER agrees this PUPPY is to be spayed/neutered at the appropriate age of (9-12 months) allowing for some sexual maturity of the pup which is necessary for their development. Veterinarian confirmation of this procedure must be supplied to the BREEDER by the time the pup is 1year of age or the contract is null and void.