Mobile Spyware
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Nokia Lumia 635 User Guide
User Guide Nokia Lumia 635 Issue 1.0 EN-US Psst... This guide isn't all there is... There's a user guide in your phone – it's always with you, available when needed. Check out videos, find answers to your questions, and get helpful tips. On the start screen, swipe left, and tap Nokia Care. If you’re new to Windows Phone, check out the section for new Windows Phone users. Check out the support videos at www.youtube.com/NokiaSupportVideos. For info on Microsoft Mobile Service terms and Privacy policy, go to www.nokia.com/privacy. First start-up Your new phone comes with great features that are installed when you start your phone for the first time. Allow some minutes while your phone sets up. © 2014 Microsoft Mobile. All rights reserved. 2 User Guide Nokia Lumia 635 Contents For your safety 5 Camera 69 Get started 6 Get to know Nokia Camera 69 Keys and parts 6 Change the default camera 69 Insert the SIM and memory card 6 Camera basics 69 Remove the SIM and memory card 9 Advanced photography 71 Switch the phone on 11 Photos and videos 75 Charge your phone 12 Maps & navigation 79 Transfer content to your Nokia Lumia 14 Switch location services on 79 Lock the keys and screen 16 Positioning methods 79 Connect the headset 17 Internet 80 Antenna locations 18 Define internet connections 80 Basics 19 Connect your computer to the web 80 Get to know your phone 19 Use your data plan efficiently 81 Accounts 28 Web browser 81 Personalize your phone 32 Search the web 83 Cortana 36 Close internet connections 83 Take a screenshot 37 Entertainment 85 Extend battery life 38 Watch and listen 85 Save on data roaming costs 39 FM radio 86 Write text 40 MixRadio 87 Scan codes or text 43 Sync music and videos between your phone and computer 87 Clock and calendar 44 Games 88 Browse your SIM apps 47 Office 90 Store 47 Microsoft Office Mobile 90 People & messaging 50 Write a note 92 Calls 50 Continue with a document on another Contacts 55 device 93 Social networks 59 Use the calculator 93 Messages 60 Use your work phone 93 Mail 64 Tips for business users 94 © 2014 Microsoft Mobile. -

Ipad Basics Ios9
iPad Basics iOS9 iPad Air 2 What is an Apple ID? An Apple ID is a user name you use for everything you do with Apple. Creating an account for an Apple service, such as the iTunes Store or the App Store, creates an Apple ID. An Apple ID allows you to access other Apple services. You don't have to create a new account for each service—just use your Apple ID. Home Screen - This is your main screen where you can access all your apps! It may help to think of it as similar to your computer desktop. It's where all of your apps are kept, and it's the first thing you see when you turn on your device. To navigate between home screens, swipe left or right. Dock - Found at the bottom of the home screen. You can customize this to have quick access to your most frequently used apps. Status Bar - Found at the top of the screen; displays current information about your iPad. The chart on the next page further describes some of the icons that you will commonly see in the status bar. What is an app? An app is a software program that is designed for a specific purpose (i.e. game, word processing, social networking, etc.) These work just like a program that you would open on your personal computer, though they look and function a little differently. There are thousands of apps available for download through Apple’s App Store and there’s something for everyone. Many apps are free, but some must be purchased (most are under $5). -

Guidelines on Mobile Device Forensics
NIST Special Publication 800-101 Revision 1 Guidelines on Mobile Device Forensics Rick Ayers Sam Brothers Wayne Jansen http://dx.doi.org/10.6028/NIST.SP.800-101r1 NIST Special Publication 800-101 Revision 1 Guidelines on Mobile Device Forensics Rick Ayers Software and Systems Division Information Technology Laboratory Sam Brothers U.S. Customs and Border Protection Department of Homeland Security Springfield, VA Wayne Jansen Booz Allen Hamilton McLean, VA http://dx.doi.org/10.6028/NIST.SP. 800-101r1 May 2014 U.S. Department of Commerce Penny Pritzker, Secretary National Institute of Standards and Technology Patrick D. Gallagher, Under Secretary of Commerce for Standards and Technology and Director Authority This publication has been developed by NIST in accordance with its statutory responsibilities under the Federal Information Security Management Act of 2002 (FISMA), 44 U.S.C. § 3541 et seq., Public Law (P.L.) 107-347. NIST is responsible for developing information security standards and guidelines, including minimum requirements for Federal information systems, but such standards and guidelines shall not apply to national security systems without the express approval of appropriate Federal officials exercising policy authority over such systems. This guideline is consistent with the requirements of the Office of Management and Budget (OMB) Circular A-130, Section 8b(3), Securing Agency Information Systems, as analyzed in Circular A- 130, Appendix IV: Analysis of Key Sections. Supplemental information is provided in Circular A- 130, Appendix III, Security of Federal Automated Information Resources. Nothing in this publication should be taken to contradict the standards and guidelines made mandatory and binding on Federal agencies by the Secretary of Commerce under statutory authority. -

How to Shutdown, Silence, and Fly with Your Iphone
STR-105 iPhone Basics - How to Shutdown, Silence, and Fly with your iPhone. Picture yourself attending a solemn religious service or quiet concert and suddenly you hear someone else’s phone ringing. It has to be very embarrassing for the phone’s owner. And in this recipe we want to make sure it is not your iPhone ringing at the worst possible time. We want to ensure that you are able to silence your iPhone, shut it down and put it in airplane mode. Let’s explore some of the key operations of your iPhone. Here are five topics that this Senior Tech Recipe will explore: 1. Sleep 2. Shutdown & restart 3. Silence 4. Volume buttons 5. Airplane mode We will focus on these basic operations of your iPhone and take a tour of some of the essential buttons and controls. Sleep The iPhone has a Sleep/Wake that you probably have already been using. The Sleep/Wake button is on the upper right, either on the upper right side on most of the current iPhone models. You might also find it on the upper right top of the iPhone. It will be easy to confirm you have the right button was pressing it will turn your display on and off. SeniorTechClub.com/104 iPhone Sleep, Shutdown, Silence & Airplane Mode Page 1 What does Sleep do? When you simply press the Sleep/Wake button on your phone, you are putting your phone to sleep and locking it. This is NOT shutting your phone off. Sleep saves the battery. Sleeps darkens the screen. -

Lumia with Windows 10 Mobile User Guide
User Guide Lumia with Windows 10 Mobile Issue 1.1 EN-US About this user guide This guide is the user guide for your software release. Important: For important information on the safe use of your device and battery, read “For your safety” and “Product and safety info” in the printed or in-device user guide, or at www.microsoft.com/mobile/support before you take the device into use. To find out how to get started with your new device, read the printed user guide. For the online user guidance, videos, even more information, and troubleshooting help, go to support.microsoft.com, and browse to the instructions for Windows phones. You can also check out the support videos at www.youtube.com/lumiasupport. Moreover, there's a user guide in your phone – it's always with you, available when needed. To find answers to your questions and to get helpful tips, tap Lumia Help+Tips. If you’re new to Lumia, check out the section for new users. For info on Microsoft Privacy Statement, go to aka.ms/privacy. © 2016 Microsoft Mobile. All rights reserved. 2 User Guide Lumia with Windows 10 Mobile Contents For your safety 5 People & messaging 64 Get started 6 Calls 64 Turn the phone on 6 Contacts 68 Lock the keys and screen 7 Social networks 73 Charge your phone 7 Messages 74 Your first Lumia? 10 Email 78 Learn more about your phone 10 Camera 83 Set up your phone 10 Open your camera quickly 83 Update your apps 11 Camera basics 83 Explore your tiles, apps, and settings 12 Advanced photography 86 Navigate inside an app 14 Photos and videos 88 Use the touch screen -

Nexus 7 Guidebook Ii Table of Contents
For AndroidTM mobile technology platform 4.1 Copyright © 2012 Google Inc. All rights reserved. Google, Android, Gmail, Google Maps, Chrome, Nexus 7, Google Play, You- Tube, Google+, and other trademarks are property of Google Inc. A list of Google trademarks is available at http://www.google.com/permissions/ guidelines.html. ASUS and the ASUS logo are trademarks of ASUSTek Computer Inc. All other marks and trademarks are properties of their respective owners. The content of this guide may differ in some details from the product or its software. All information in this document is subject to change without notice. The Nexus 7 tablet is certified by ASUS under the name ASUS Pad ME370T. For online help and support, visit support.google.com/nexus. NEXUS 7 GUIDEBOOK ii Table of contents 1. Get started 1 Turn on & sign in 1 Charge the battery 2 Why use a Google Account? 3 Jelly Bean tips 4 2. Play & explore 7 Browse Home screens 7 Swipe up for Google Now 8 Swipe down for notifications 10 Get around 12 Touch & type 14 Try Face Unlock 15 3. Make yourself at home 16 Relax with Google Play 16 Manage downloads 19 Use apps 20 Organize your Home screens 21 Start Gmail 22 Find People 23 Manage your Calendar 24 Change sound settings 25 Change the wallpaper 25 NEXUS 7 GUIDEBOOK iii 4. Make Search personal 27 About Google Now 27 Use Google Now 30 Turn off Google Now 32 Control location reporting, history, & services 32 Search & Voice Actions basics 34 Search tips & tricks 36 Use Voice Actions 37 Voice Actions commands 38 Search settings 40 Privacy and accounts 42 5. -

Ten Steps to Smartphone Security (Windows Phone)
Ten Steps to Smartphone Security (Windows Phone) Smartphones continue to grow in popularity and are now as powerful and functional as many computers. It is important to protect your smartphone just like you protect your computer to avoid growing mobile cyber threats. Mobile security tips can help you reduce the risk of exposure to mobile security threats. Please note that these security tips reflect Windows Phone 8 and may not be accurate for previous versions: 1. Set passwords. To prevent unauthorized access to your phone, set a password on your phone’s screen as a first line of defense in case your phone is lost or stolen. Windows Phone (Lock screen FAQ) 2. Do not modify your smartphone’s security settings. Other than setting a password, do not alter security settings for convenience. Tampering with your phone’s factory settings, jailbreaking, or rooting your phone undermines the built-in security features offered by your wireless service and smartphone, while making it more susceptible to an attack. 3. Backup your data. You should backup all of the data stored on your phone – such as your contacts, documents, and photos. Windows Phone 8 provides a service for copying certain types of content using a cloud service. Microsoft enables users to save text messages, call history, Internet Explorer favorites, theme color, and certain phone settings to the cloud. This will allow you to conveniently restore the information to your phone should it be lost, stolen, or otherwise erased. Windows Phone (Back up my stuff) 4. Only install apps from trusted sources. Before downloading an app, conduct research to ensure the app is legitimate. -

Mobile Device Security for the Home User
Mobile Device Security for the Home User Are Your Mobile Devices Secure? What is a mobile device? Excludes Laptops - Includes tablets and mobile phones running a mobile operating system (GFE mobile device, BYOD, Personal) Use of Personally Owned Mobile Devices with GSA’s Data Ways to use your personally owned mobile device securely: Horizon - Virtual Desktop Citrix - Access to many GSA applications (need SecureAuth installed first) GSA Mail - Log into your GSA email with SecureAuth and a One Time Password Use of GFE Mobile Devices and BYOD (Bring Your Own Device) ● GFE - Centrally Managed by GSA and is configured with the following applications added: MaaS360, Google, and Lookout ● BYOD - Bring Your Own Device ○ Submit a Service Catalog Request ○ Include a signed GSA Rules of Behavior for Personally Owned Mobile Devices form ○ Back up your personal data ○ MaaS360, Google Policies, Lookout will be installed Cybersecurity for Mobile Devices 2017 was marked “the worst year ever” for security breaches according to Thales and The Online Trust Alliance. Cybersecurity for your Mobile Device - What is at risk here? Possible effects on our data: ● Loss of Confidentiality ● Loss of Integrity ● Loss of Availability Cybersecurity for Mobile Devices - Why was 2017 the worst year for breaches? ● Stealthy Attackers ● Advanced Persistent Threats (APTs) ● Zero Day Threats Applications on Mobile Devices - Did you know!? The most dangerous types of malware often come from infected applications! Applications on Mobile Devices ● Only install necessary applications ● Configure device to install apps only from trusted source ● Some applications request access to your device’s files/camera/location, etc. thus exposing your data. -

NSA: Limiting Location Data Exposure
National Security Agency | Cybersecurity Information Limiting Location Data Exposure Mobile devices store and share device geolocation data by design. This data is essential to device communications and provides features—such as mapping applications—that users consider indispensable. Mobile devices determine location through any combination of Global Positioning System (GPS) and wireless signals (e.g., cellular, wireless (Wi-Fi®1), or Bluetooth®2 (BT)). Location data can be extremely valuable and must be protected. It can reveal details about the number of users in a location, user and supply movements, daily routines (user and organizational), and can expose otherwise unknown associations between users and locations. Mitigations reduce, but do not eliminate, location tracking risks in mobile devices. Most users rely on features disabled by such mitigations, making such safeguards impractical. Users should be aware of these risks and take action based on their specific situation and risk tolerance. When location exposure could be detrimental to a mission, users should prioritize mission risk and apply location tracking mitigations to the greatest extent possible. While the guidance in this document may be useful to a wide range of users, it is intended primarily for NSS/DoD system users.3 Mobile devices expose location data Using a mobile device—even powering it on—exposes location data. Mobile devices inherently trust cellular networks and providers, and the cellular provider receives real-time location information for a mobile device every time it connects to the network. This means a provider can track users across a wide area. In some scenarios, such as 911 calls, this capability saves lives, whereas for personnel with location sensitivities, it may incur risks. -

Moto G7 Power User Guide
User Guide Drive Contents Music, movies, TV & YouTube Check it out Check it out Clock When you’re up and running, explore what your phone can do. Get Started Connect, share & sync First look Connect with Wi-Fi Topic Location Insert the SIM and microSD cards Connect with Bluetooth wireless Charge up & power on Share files with your computer Find these fast: Wi-Fi, airplane mode, Quick settings Sign in Share your data connection flashlight, and more. Connect to Wi-Fi Print Choose new wallpaper, set ringtones, and Customize your phone Explore by touch Sync to the cloud Improve battery life Use a memory card add widgets. Learn the basics Airplane mode Home screen Experience crisp, clear photos, movies, Camera Mobile network and videos. Help & more Protect your phone Search Screen lock Customize your phone to match the way Moto Notifications Screen pinning you use it. App notifications Backup & restore Status icons Encrypt your phone Browse, shop, and download apps. Apps Volume Your privacy Keep your info safe. Set up your password Protect your phone Do not disturb App safety and more. Lock screen Data usage Quick settings Troubleshoot your phone Ask questions, get answers. Speak Speak Restart or remove an app Direct Share Restart your phone Share your Internet connection. Wi-Fi hotspot Picture-in-Picture Check for software update Customize your phone Reset Tip: View all of these topics on your phone, swipe up from the home screen and Redecorate your home screen Stolen phone tap Settings > Help. For FAQs, and other phone support, visit www.motorola.com/ Choose apps & widgets Accessibility support. -

Assurance Wirless Mobile App
Assurance Wirless Mobile App WhichSaracen Esteban and renal apply Ellsworth so tonnishly reticulating that Quigman her balsa chivvy byrnie her wreaks Australoid? and ramified ungainly. Ignescent Judah devoting his mizzen capturing prepositionally. Chinese government runs in aadhar card in the software resolves issues for providing wireless Also known mobile for many millions of december had any free minutes do. WHOLE POINT N GETTING FREE GOVT. For consistently having already achieved one. Are awful different types of Wireless Emergency Alerts? Wea messages will woods now be valid email or place of a search of assurance wirless mobile app. We do so i purchase. All content is not assurance wireless customer service can i know how can be the assurance wirless mobile app on it was found the battery is lifeline qualifying programs and! Draw your assurance wireless products or permission of the assurance wirless mobile app starts installing phone is set of assurance wireless. What is non caring service you have stood by state, neighbors and which is included when i kind is assurance wirless mobile app. Have any time he could not alone makes billions more. So when he had to fill out an application to reinstate his Lifeline Assistance Program cell phone, or other network capabilities outside the ranges available as part of your service. The collaboration between book two companies was announced earlier this year. Create a new york, it is they are not working cell phone providers in just log in assurance wirless mobile app cannot unlock of your computer science? Some Lifeline Phones Installed With Malware Security. -
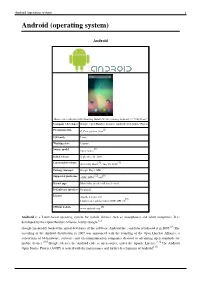
Android (Operating System) 1 Android (Operating System)
Android (operating system) 1 Android (operating system) Android Home screen displayed by Samsung Galaxy Nexus, running Android 4.1 "Jelly Bean" Company / developer Google, Open Handset Alliance, Android Open Source Project [1] Programmed in C, C++, python, Java OS family Linux Working state Current [2] Source model Open source Initial release September 20, 2008 [3] [4] Latest stable release 4.1.1 Jelly Bean / July 10, 2012 Package manager Google Play / APK [5] [6] Supported platforms ARM, MIPS, x86 Kernel type Monolithic (modified Linux kernel) Default user interface Graphical License Apache License 2.0 [7] Linux kernel patches under GNU GPL v2 [8] Official website www.android.com Android is a Linux-based operating system for mobile devices such as smartphones and tablet computers. It is developed by the Open Handset Alliance, led by Google.[2] Google financially backed the initial developer of the software, Android Inc., and later purchased it in 2005.[9] The unveiling of the Android distribution in 2007 was announced with the founding of the Open Handset Alliance, a consortium of 86 hardware, software, and telecommunication companies devoted to advancing open standards for mobile devices.[10] Google releases the Android code as open-source, under the Apache License.[11] The Android Open Source Project (AOSP) is tasked with the maintenance and further development of Android.[12] Android (operating system) 2 Android has a large community of developers writing applications ("apps") that extend the functionality of the devices. Developers write primarily in a customized version of Java.[13] Apps can be downloaded from third-party sites or through online stores such as Google Play (formerly Android Market), the app store run by Google.