Brno University of Technology Vysoké Učení Technické V Brně
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Crypto Ransomware Analysis and Detection Using
CRYPTO RANSOMWARE ANALYSIS AND DETECTION USING PROCESS MONITOR by ASHWINI BALKRUSHNA KARDILE Presented to the Faculty of the Graduate School of The University of Texas at Arlington in Partial Fulfillment of the Requirements for the Degree of MASTER OF SCIENCE IN COMPUTER SCIENCE THE UNIVERSITY OF TEXAS AT ARLINGTON December 2017 Copyright © by Ashwini Balkrushna Kardile 2017 All Rights Reserved ii Acknowledgements I would like to thank Dr. Ming for his timely guidance and motivation. His insights for this research were valuable. I would also like to thank my committee members Dr. David Levine and Dr. David Kung for taking out time from their schedule and attending my dissertation. I am grateful to John Podolanko; it would not have been possible without his help and support. Thank you, John, for helping me and foster my confidence. I would like to thank my colleagues for supporting me directly or indirectly. Last but not the least; I would like to thank my parents, my family and my friends for encouraging me and supporting me throughout my research. November 16, 2017 iii Abstract CRYPTO RANSOMWARE ANALYSIS AND DETECTION USING PROCESS MONITOR Ashwini Balkrushna Kardile, MS The University of Texas at Arlington, 2017 Supervising Professor: Jiang Ming Ransomware is a faster growing threat that encrypts user’s files and locks the computer and holds the key required to decrypt the files for ransom. Over the past few years, the impact of ransomware has increased exponentially. There have been several reported high profile ransomware attacks, such as CryptoLocker, CryptoWall, WannaCry, Petya and Bad Rabbit which have collectively cost individuals and companies well over a billion dollars according to FBI. -

Thriving in a Crowded and Changing World: C++ 2006–2020
Thriving in a Crowded and Changing World: C++ 2006–2020 BJARNE STROUSTRUP, Morgan Stanley and Columbia University, USA Shepherd: Yannis Smaragdakis, University of Athens, Greece By 2006, C++ had been in widespread industrial use for 20 years. It contained parts that had survived unchanged since introduced into C in the early 1970s as well as features that were novel in the early 2000s. From 2006 to 2020, the C++ developer community grew from about 3 million to about 4.5 million. It was a period where new programming models emerged, hardware architectures evolved, new application domains gained massive importance, and quite a few well-financed and professionally marketed languages fought for dominance. How did C++ ś an older language without serious commercial backing ś manage to thrive in the face of all that? This paper focuses on the major changes to the ISO C++ standard for the 2011, 2014, 2017, and 2020 revisions. The standard library is about 3/4 of the C++20 standard, but this paper’s primary focus is on language features and the programming techniques they support. The paper contains long lists of features documenting the growth of C++. Significant technical points are discussed and illustrated with short code fragments. In addition, it presents some failed proposals and the discussions that led to their failure. It offers a perspective on the bewildering flow of facts and features across the years. The emphasis is on the ideas, people, and processes that shaped the language. Themes include efforts to preserve the essence of C++ through evolutionary changes, to simplify itsuse,to improve support for generic programming, to better support compile-time programming, to extend support for concurrency and parallel programming, and to maintain stable support for decades’ old code. -

Ideablade Devforce Installation Guide
DevForceDevForce Silverlight WinClient Installation Guide DevForce Silverlight Installation Guide Table of Contents Table of Contents Preface ................................................................................................................................ 1 Installation .......................................................................................................................... 2 Product Prerequisites ........................................................................................................................... 2 Pre-installation Checklist ...................................................................................................................... 2 Installing DevForce Silverlight .............................................................................................................. 4 Post-Installation Tasks ......................................................................................................................... 6 Updating Existing Applications....................................................................................... 7 Consult the Release Notes ................................................................................................................... 7 Upgrading DevForce Versions.............................................................................................................. 7 Upgrading DevForce Editions ............................................................................................................. 11 Troubleshooting -

Billquick-SQL Server 2012 Express Installation Guide
INSTALLATION GUIDE BillQuick-SQL Server 2012 Express Installation BillQuick-SQL Server 2012 Express Installation BillQuick | Power Up Your Business (866) 945-1595 | www.bqe.com | [email protected] INSTALLATION GUIDE BillQuick-SQL Server 2012 Express Installation CONTENTS SQL EXPRESS INSTALLATION 1 SYSTEM REQUIREMENTS 1 INSTALLING SQL 2012 EXPRESS 1 SQL EXPRESS CONFIGURATION 8 BILLQUICK DATABASE 11 BillQuick | Power Up Your Business (866) 945-1595 | www.bqe.com | [email protected] INSTALLATION GUIDE BillQuick-SQL Server 2012 Express Installation SQL EXPRESS INSTALLATION The Microsoft® SQL Server® 2012 Express software is the database engine you will use to store and report on data in BillQuick (Basic, Pro and Enterprise editions). It is available free from Microsoft and is a replacement for MSDE and SQL 2005. We do not recommend using SQL Server 2005 that might be installed with your Windows Server because other software programs that rely on that SQL Server instance can break if you attempt to install service pack updates on them. System Requirements You can check Microsoft Download Center to download Microsoft SQL Server 2012 R2 SP2. Click to know about the system requirements and installation instructions. Hardware/Software Requirements To know about the hardware and software requirements, go to Microsoft Developer Network . Installing SQL 2012 Express Please follow the steps below to install SQL Server 2012 Express edition. If you prefer, click here to watch a video on installing SQL Server Express. 1. Download the appropriate SQL Server 2012 Express setup to your desktop. Express Version System Microsoft® SQL Server® 2012 Express SP1 For 32-Bit machines, download the file: SQLEXPRWT_x86_ENU.exe For 64-Bit machines, download the file: SQLEXPRWT_x64_ENU.exe 2. -

SQL Server Express: Setting up for Unistream User Guide 3/17
Headquarters Unitronics (1989) (R"G). Unitronics Building, Airport City P.O.B. 300, Ben Gurion Airport, Israel 70100 Tel: + 972 (3) 977 8888 Fax: + 972 (3) 977 8877 SQL Server Express: Setting up for UniStream User Guide 3/17 Contents SQL Server Express: Setting up for UniStream ...................................................... 1 Overview ....................................................................................................... 1 Supported Controllers ...................................................................................... 1 First-time Installation & Configuration ................................................................. 2 Download ...................................................................................................... 2 Installing SQL Server ...................................................................................... 3 Setting up the Local Database .......................................................................... 5 Configuring SQL Server ................................................................................... 6 Activating the SQL Server Browser. ................................................................ 6 Enable TCP/IP, Assign Port ............................................................................ 7 Create a new Login ....................................................................................... 8 SQL Server Express—Existing Installation ........................................................... 10 Enable TCP/IP, Assign Port -

Vcpkg, Un Outil Pour Acquérir Et Compiler Plus Simplement Les Librairies Open Source C++ Sur Windows
043_044_204 24/01/17 21:59 Page43 microsoft 43 # 204 Vcpkg, un outil pour acquérir et compiler plus simplement les librairies open source C++ sur Windows. Eric Mittelette Acquérir une librairie open source, la compiler sur Windows et l’intégrer dans son Microsoft Corp. projet C++ reste une opération délicate, voire une galère. Pour une librairie donnée, il faut trouver les sources, les installer localement, compiler la librairie et enfin la mettre à disposition du projet dans lequel vous souhaitez l’utiliser. a phase de build est de loin la plus subtile et complexe, elle nécessi- source de la librairie. Nous voulions que cette collection de « port files » te souvent un peu d’adaptation (patch) si la librairie n’est pas encore soit open source et que la communauté des développeurs C++ puisse y Ldisponible pour la version de compilateur que vous utilisez, cette contribuer en ajoutant les librairies qu’ils maintiennent ou utilisent. adaptation nécessite encore l’usage d’incantations (sous forme de scripts, L’architecture générale en découle assez naturellement : pas de magie noire…), que seuls les grands « faiseurs » maîtrisent réelle- • Créer une liste de « port file » dans un repo Github ; ment. Nous savons par sondage et les appels au support technique de • Créer un outil en ligne de commande qui exploite cette liste et capable Microsoft que les librairies tierces restent pour plus de 30% des cas le blo- de lancer le processus de compilation au regard des instructions de queur a la migration vers les dernières versions du compilateur C++. Nous chaque « port file » ; savons également que 80% des projets C++ utilisent 2 ou 3 librairies • Installer le résultat de la compilation dans un répertoire local « « LibFolder » ; tierces en moyenne, et que la vaste majorité d’entre elles sont aujourd’hui • Permettre une intégration simple avec Visual studio, CMake ou tout des librairies open source. -

Syncstudio Requirements
Hardware and Software Requirements The SyncStudio Sync Management Console and the custom generate Sync Web Service run on Windows OS systems. We support Windows 7, 8.1, 10 and Windows Server 2012 or 2016. Win XP is not supported. For production environments, we recommend Windows Server. We support both virtual and physical machines. The machine needs to have IIS 7 or above installed, enabled and with the features/roles as per our quick start guide. .NET Framework 3.5 is the minimum but 4.6 or higher is recommended. The server database can be either MS SQL SERVER or MS SQL EXPRESS versions 2008, 2010, 2012, 2014, 2016. Version 2014 and above is recommended. If you don’t have MS SQL Server, you can download SQL Server Express from this link: MS SQL Server 2016 Express Edition In SQL add login NT AUTHORITY\NETWORK SERVICE and make it a db owner of the selected SQL database. Visual Studio – SyncStudio depends on portions of Visual Studio to perform automated code generation. If you’ve installed a full license of Visual Studio 2010 or above, then you are good to go. If you do not own a full license, then you can use the Free Visual Studio Express or Visual Studio Integration Shell 2010. Minimum Microsoft Visual Studio 2010 or 2012 SyncStudio does not require that you own a full license of Visual Studio. You do however need to have installed one of the following… - Microsoft Visual Studio Integration Shell 2010 - Microsoft Visual Studio Express for Web 2010 or 2012 - Microsoft Visual Studio 2010 or 2012 full license Windows Firewall - Turn off firewall or configure pass thru as needed. -

Xactimate 28 Network Installation Guide
Network Installation Guide © 2011-2013 by Xactware . All rights reserved. Xactware, Xactimate, Xactimate Online, XactNet, and/or other Xactware products referenced herein are either trademarks or registered trademarks of Xactware Solutions, Inc. Other product and company names mentioned herein may be the trademarks of their respective owners. (031213) www.xactware.com Xactimate version 28 Network Installation Guide INTRODUCTION Like all networked software applications, Xactimate must be installed on a workstation connected to a network that has been properly set up and mapped to a shared drive (this document uses the X drive as an example). Xactware recommends that a certified network technician set up and administer the network. It is recommended for a network installation of Xactimate to use the physical disc. For instructions about how to set up a network installation of Xactimate via the downloadable version, visit the eService Center at https:/ / eservice.xactware.com/apps/esc/ Xactimate v28.0 Network Installation Guide Page 1 Introduction SYSTEM REQUIREMENTS - XACTIMATE V28.0 NETWORK INSTALLATION Specifications Minimum Requirements Recommended Requirements Processor Single Core Processor 1.5GHz Dual Core Processors Operating System Windows 8 (32 bit, 64 bit) Windows 7 (32 bit, 64 bit) Windows Vista (32 bit, 64 bit Business, 64 bit Ultimate) Windows XP Service Pack 3 *Windows RT is not Supported Video Card Open GL 2.0 Compatible with 128 Open GL 2.0 Compatible with MB of VRAM and Latest Drivers 512 MB of VRAM and Latest Drivers -

Development Environment
BLUESPAWN BLUESPAWN Dev Team Apr 28, 2021 CONTENTS 1 Our Mission 3 2 What is BLUESPAWN 5 3 Get Involved & Contribute to the project7 4 Why we made BLUESPAWN9 4.1 Contact Us................................................9 4.2 Sponsoring................................................9 4.3 Licensing.................................................9 4.4 Project Authors.............................................. 10 4.5 Publications............................................... 11 4.6 Hunts................................................... 11 4.7 Scan Mode................................................ 11 4.8 Mitigations................................................ 11 4.9 Reactions................................................. 11 4.10 Logging and Output........................................... 11 4.11 Agent7 Integration............................................ 11 4.12 Getting Started.............................................. 11 4.13 Examples of BLUESPWAN in Action.................................. 13 4.14 Using Mitigations............................................ 14 4.15 Getting Involved............................................. 18 4.16 Setting up your Development Environment............................... 18 4.17 Software Architecture Info........................................ 19 4.18 Project Roadmap............................................. 21 i ii BLUESPAWN CONTENTS 1 BLUESPAWN 2 CONTENTS CHAPTER ONE OUR MISSION BLUESPAWN helps blue teams monitor systems in real-time against active attackers by detecting -

Введение В Silverlight 3
2 Здравствуйте, дорогой читатель! Мы очень рады продолжить добрую традицию и представить Вам первую книгу о технологии Microsoft Silverlight 3 на русском языке! Microsoft Silverlight позволяет разработчикам с помощью простых и мощных инструментов создавать интерактивные Интернет- приложения, которые становятся все популярнее среди широкого круга пользователей. Данная технология уже используется на многих известных ресурсах – как в мире, так и в России. Silverlight 3 – важный шаг в развитии технологии. Среди новых возможностей можно отметить 3D-трансформации, аппаратное ускорение, работа вне браузера и много другое. Уже более трети Интернет-устройств в мире имеют установленный Silverlight. Принимая во внимание текущую динамику, можно с уверенностью сказать, что данная технология будет и дальше распространяться среди пользователей во всем мире, и Россия здесь не исключение. Менее года назад мы выпустили электронную книгу «Введение в Microsoft Silverlight 2», за это время ее загрузило более 30000 читателей. Для перевода книги по Silverlight 3 мы вновь выбрали издание Лоуренса Морони, основываясь на положительных отзывах от Вас, российских разработчиков, и на международном опыте. Книга представляет комплексный обзор Silverlight 3, который будет интересен как тем, кто уже имеет опыт работы с прошлыми версиями данной технологии, так и для начинающих свой путь в мир Silverlight. В завершение хочу поблагодарить Вас за интерес к технологии Microsoft Silverlight и предлагаю окунуться в увлекательный мир интерактивности. Дмитрий Халин, Директор департамента стратегических технологий Майкрософт Россия 3 ОПУБЛИКОВАНО Microsoft Press A Division of Microsoft Corporation One Microsoft Way Redmond, Washington 98052-6399 Copyright © 2009 by Laurence Moroney Все права защищены. Ни одна часть данной книги не может быть воспроизведена в любой форме или любыми средствами без письменного разрешения издателя. -

Creating a Web Site with Expression Web
05_115091 ch01.qxp 3/2/07 9:23 PM Page 7 Chapter 1 Creating a Web Site with Expression Web In This Chapter ᮣ Starting Expression Web for the first time ᮣ Exploring the workspace ᮣ Creating and saving a new Web site ᮣ Using a template to create a new Web site ᮣ Opening, closing, and deleting Web sites ᮣ Adding existing files to a Web site ᮣ Closing Expression Web n this chapter, you get started with Expression Web: You get familiar with Ithe workspace and find out how to create and save Web sites. Before you hang your shingle as a Web publisher, though, you should understand what you’re really doing when you create and publish a Web site. No doubt you’ve already seen a Web site. Web sites are the places you visit as you make your way around the World Wide Web. In the same way as a book is made up of individual pages, a Web site is made up of individual files called Web pages. Web pages contain the text, pictures, and other content you see when you visit a Web site. As you constructCOPYRIGHTED a Web site, you create WebMATERIAL pages and then string the pages together by using hyperlinks. Hyperlinks are the highlighted words and pic- tures inside the page that visitors can click to jump to a different location, page, or Web site. Hyperlinks can also initiate a download or pop open an e-mail window. After your site is complete, you publish it. In other words, you make the site visible to the rest of the world on the World Wide Web (or, if you’re working on an internal company site, on the company’s intranet). -
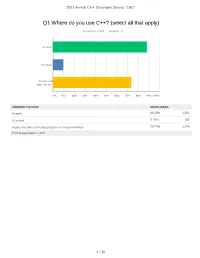
Q1 Where Do You Use C++? (Select All That Apply)
2021 Annual C++ Developer Survey "Lite" Q1 Where do you use C++? (select all that apply) Answered: 1,870 Skipped: 3 At work At school In personal time, for ho... 0% 10% 20% 30% 40% 50% 60% 70% 80% 90% 100% ANSWER CHOICES RESPONSES At work 88.29% 1,651 At school 9.79% 183 In personal time, for hobby projects or to try new things 73.74% 1,379 Total Respondents: 1,870 1 / 35 2021 Annual C++ Developer Survey "Lite" Q2 How many years of programming experience do you have in C++ specifically? Answered: 1,869 Skipped: 4 1-2 years 3-5 years 6-10 years 10-20 years >20 years 0% 10% 20% 30% 40% 50% 60% 70% 80% 90% 100% ANSWER CHOICES RESPONSES 1-2 years 7.60% 142 3-5 years 20.60% 385 6-10 years 20.71% 387 10-20 years 30.02% 561 >20 years 21.08% 394 TOTAL 1,869 2 / 35 2021 Annual C++ Developer Survey "Lite" Q3 How many years of programming experience do you have overall (all languages)? Answered: 1,865 Skipped: 8 1-2 years 3-5 years 6-10 years 10-20 years >20 years 0% 10% 20% 30% 40% 50% 60% 70% 80% 90% 100% ANSWER CHOICES RESPONSES 1-2 years 1.02% 19 3-5 years 12.17% 227 6-10 years 22.68% 423 10-20 years 29.71% 554 >20 years 34.42% 642 TOTAL 1,865 3 / 35 2021 Annual C++ Developer Survey "Lite" Q4 What types of projects do you work on? (select all that apply) Answered: 1,861 Skipped: 12 Gaming (e.g., console and..