Geospatial Analysis of Terrorist Activities
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Beirut Divided: the Potential of Urban Design in Reuniting a Culturally Divided City
The Bartlett Development Planning Unit DPU WORKING PAPER NO. 153 Beirut Divided: The potential of urban design in reuniting a culturally divided city Benjamin J Leclair-Paquet DPU Working Papers are downloadable at: www.bartlett.ucl.ac.uk/dpu/latest/ publications/dpu-papers If a hard copy is required, please contact the De- velopment Planning Unit (DPU) at the address at the bottom of the page. Institutions, organisations and booksellers should supply a Purchase Order when ordering Working Papers. Where multiple copies are or- dered, and the cost of postage and package is significant, the DPU may make a charge to cov- er costs. DPU Working Papers provide an outlet for researchers and professionals working in the fields of development, environment, urban and regional development, and planning. They report on work in progress, with the aim to dissemi- nate ideas and initiate discussion. Comments and correspondence are welcomed by authors and should be sent to them, c/o The Editor, DPU Working Papers. Copyright of a DPU Working Paper lies with the author and there are no restrictions on it being published elsewhere in any version or form. DPU Working Papers are refereed by DPU academic staff and/or DPU Associates before selection for publication. Texts should be submitted to the DPU Working Papers' Editors, Dr Camillo Boano and Dr Barbara Lipietz. Graphics and layout: Giorgio Talocci, Camila Cociña and Luz Navarro The Bartlett Development Planning Unit | The Bartlett | University College London 34 Tavistock Square - London - WC1H 9EZ Tel: +44 (0)20 7679 1111 - Fax: +44 (0)20 7679 1112 - www.bartlett.ucl.ac.uk/dpu DPU WORKING PAPER NO. -

The Eco-Terrorist Wave (1970-2016)
THE ECO-TERRORIST WAVE (1970-2016) By João Raphael da Silva Submitted to Central European University Department of International Relations In partial fulfilment of the requirements for the degree of Master of Arts in International Relations Supervisor: Professor Matthijs Bogaards Word Count: Budapest, Hungary 2017 CEU eTD Collection 1 ABSTRACT The present research aims to shed light on the geographical and temporal spread of the ecological typology of terrorism – hereinafter referred as “Eco-Terrorism” – through the lens of the David C. Rapoport’s Wave and Tom Parker and Nick Sitter’s Strain Theories. This typology that has posed high levels of threats to the United States and the European Union member States remains uncovered by these two theoretical frameworks. My arguments are that, first, like many other typologies previously covered by the above-mentioned theories, Eco-Terrorism spread. Second, “Wave”, “Strain” or “Wavy Strain” should be able to explain the pattern followed by Eco-Terrorism. Making use of the “Contagion Effect” as an analytical tool, the present research found that, like in other typologies, as an indirect way of contagion, literary production has played a crucial role in the spread of Eco-Terrorism, with a slight difference on who was writing them. Eventually, they became leaders or members of an organization, but in most of the cases were philosophers and fiction authors. In addition, it was found that the system of organization of the ALF and the ELF contributes to the spread. As a direct way of contagion, aside from training like in other typologies, the spread occurs when members of a certain organization disaffiliate from an organization and found a new one, and sometimes when two organizations act in cooperation. -

2. (U//FOUO) Health: Detainee Is in Good Health
SECRET // 20330311 DEPARTMENT OF DEFENSE STATES COMMAND HEADQUARTERS , JOINT TASK FORCE GUANTANAMO U.S. NAVAL STATION , GUANTANAMO BAY , CUBA APOAE09360 JTF- GTMO- CDR 11 March 2008 MEMORANDUMFORCommander, UnitedStates SouthernCommand, 3511NW Avenue, Miami, FL 33172 SUBJECT : Recommendation for Continued Detention Under Control (CD) for Guantanamo Detainee, ISN -000048DP (S ) JTF - GTMO Detainee Assessment 1. (S) PersonalInformation: JDIMS/ NDRC ReferenceName: Abdullah K al-Hamairi Current/ True Name andAliases: Abdullah al-Hamiri, Abdallah Khalaf Atiq al-Hamayri, Abu Khalid, Abu Khalid al-Emirati Abdallah al-Emirati Place of Birth: Al- Ayn , United Arab Emirates (AE, UAE) Date ofBirth: 25 October 1979 Citizenship: United Arab Emirates InternmentSerial Number (ISN) : - 000048DP 2. (U// FOUO) Health: Detainee is in good health . 3. ( U ) JTF- GTMO Assessment : a. (S) Recommendation : JTF -GTMO recommends this detainee for Continued Detention Under DoD Control (CD) . JTF -GTMO previously recommended detainee for Continued Detention Under DoD Control (CD) on 20 March 2007 . b . (S ) Executive Summary: Detainee was a fighter in Usama BinLaden's (UBL) 55th Arab Brigade supporting the Taliban. Under the guise of pursuing an education, detainee traveled to Portland, Oregon ( OR ), in 1997. Detainee spent almost three years in the Portland area attending the al- Sabr Mosque that was reported to have provided fundraising, recruitment, and indoctrination services for al-Qaida. Many of the detainee's associates during his stay in the US consisted -

Scare Tactics: Ashcroft's Phony 'War on Terrorism'
Click here for Full Issue of EIR Volume 31, Number 12, March 26, 2004 EIRNational Scare Tactics: Ashcroft’s Phony ‘War on Terrorism’ by Edward Spannaus Once described as America’s “de facto Minister of Fear,” Convictions Without Trials Attorney General John Ashcroft fit that description in a state- The fraud of Ashcroft’s “war on terrorism” was dramati- ment issued on March 4, immediately after the conviction cally demonstrated in December, when a research institute of three defendants in the “Virginia Jihad” case. Ashcroft associated with Syracuse University, the Transactional Re- declared: “Today, Americans get a glimpse of what is hiding cords Access Clearinghouse (TRAC), published a study in the shadows. Terrorists recruit, train, and finance jihad which blew a major hole in Ashcroft’s scare campaign about in America.” “Islamic terrorists” and “sleeper cells” inside the United The truth is that Ashcroft’s “war on terrorism” gives no States. The study showed that there had been a sharp increase such glimpse; it is a gigantic dud. The blunderbus tools given in the number of convictions in serious terrorism cases in the by Congress to the Justice Department have enabled Ashcroft two years following the 9/11 attacks, from 96 for the two and Co. to use the threat of draconian prison sentences to years prior to September 2001, to 341 for the two years after. force defendants to plead guilty to offenses that they may or What was most surprising about the Syracuse study was what may have not committed. As a result, the Justice Department it showed about sentences. -

Terr. Awareness Project 9/03
FALL 2003 VOL. 2, NO.2 Terrorism Awareness Project A Periodic Newsletter Updating the Chicago Connection to International Terrorism The Jewish Community Relations Council of the Jewish United Fund of Metropolitan Chicago BIF’s Bosnian Director Found Guilty Since September 11, 2001, the U.S. government In July 2003, a Sarajevo court found that BIF’s Bosnia has stepped up its aggressive investigation of director – Munib Zahiragic –guilty of disclosing state secrets American individuals and organizations it asserts to Enaam Arnaout and BIF’s US offices. Zahiragic, who was sentenced to two years, was also accused of being an are connected to international terrorism. informant for an alleged Al Qaeda member connected to the 1998 bombing of the U.S. embassies in Tanzania and Kenya. During this time three Chicago-based fundraising organizations – the Holy Land Foundation, GRF Co-Founder Deported Benevolence International Foundation, and the Rabih Haddad, co-founder and Global Relief Foundation – have had their assets chairman of the Bridgeview – based frozen for allegedly supporting terrorism. They Global Relief Foundation (GRF), was joined a fourth local group, the Quranic Literacy deported July 14 to Lebanon. Institute, whose assets were frozen in 1998. Haddad had applied for political Together, these four groups (two tied to Hamas asylum in the U.S., citing fears of a and two to Al Qaeda) have the distinction of backlash abroad after being publicly being the only U.S. organizations so charged. accused of terrorist connections. Hadad was initially denied asylum in www.windchimewalker.com Nov. 2002 and ordered deported. Rabih Haddad The U.S. -

Craig-Cvd506-Manual.Pdf
.BJOUFOBODFBOE$BSF $BSJOHGPSUIF6OJU *ODMJOBUJPO ti5IFBQQBSBUVTTIBMMOPUCFFYQPTFEUPESJQQJOHPS t%POPUJOTUBMMUIFVOJUJOBOJODMJOFEQPTJUJPO*UJTEFTJHOFE TQMBTIJOHwBOEUIBUOPPCKFDUTGJMMFEXJUIMJRVJETIBMM UPCFPQFSBUFEJOBIPSJ[POUBMQPTJUJPOPOMZ CFQMBDFEPOUIFVOJU t*GBOZUIJOHGBMMTJOUPUIFDBCJOFU VOQMVHUIFVOJUBOEIBWF "WPJE*OUFSGFSFODF JUDIFDLFECZRVBMJGJFEQFSTPOOFMCFGPSFPQFSBUJOHJUBOZ t8IFOZPVQMBDFUIJTVOJUOFBS57 SBEJPPS7$3 UIFQJDUVSF GVSUIFS NBZCFDPNFQPPSBOEUIFTPVOENBZCFEJTUPSUFE*OUIJT DBTF NPWFUIFVOJUBXBZGSPNUIF57 SBEJPPS7$3 $MFBOJOHUIF6OJU t5PQSFWFOUGJSFPSTIPDLIB[BSE EJTDPOOFDUZPVSVOJUGSPN %JTDPOOFDU1PXFS UIF"$QPXFSTPVSDFXIFODMFBOJOH t*GZPVBSFOPUHPJOHUPVTFUIFVOJUGPSBMPOHUJNF CF t5IFGJOJTIPOZPVSVOJUNBZCFDMFBOFEXJUIBEVTUDMPUI TVSFUPEJTDPOOFDUUIFVOJUGSPNUIFXBMMPVUMFU5P BOEDBSFEGPSBTPUIFSGVSOJUVSF EJTDPOOFDUUIF"$QPXFSDPSE NBJOMFBET HSBTQUIFQMVH 6TFDBVUJPOXIFODMFBOJOHBOEXJQJOHUIFQMBTUJDQBSUT JUTFMG OFWFSQVMMUIFDPSE t.JMETPBQBOEBEBNQDMPUINBZCFVTFEPOUIFGSPOUQBOFM *.1035"/54"'&5:*/4536$5*0/4 8BSOJOH5PSFEVDFUIFSJTLPGGJSFPSFMFDUSJDTIPDL EPOPU #FGPSFVTJOHUIFVOJU CFTVSFUPSFBEBMMPQFSBUJOH FYQPTFUIJTBQQMJBODFUPSBJOPSNPJTUVSF JOTUSVDUJPOTDBSFGVMMZ1MFBTFOPUFUIBUUIFTFBSFHFOFSBM %BOHFSPVTIJHIWPMUBHFTBSFQSFTFOUJOTJEFUIF QSFDBVUJPOTBOENBZOPUQFSUBJOUPZPVSVOJU'PSFYBNQMF FODMPTVSF%POPUPQFOUIFDBCJOFU SFGFSTFSWJDJOH UIJTVOJUNBZOPUIBWFUIFDBQBCJMJUZUPCFDPOOFDUFEUPBO UPRVBMJGJFEQFSTPOOFMPOMZ PVUEPPSBOUFOOB 3FBEUIFTFJOTUSVDUJPOT "MMUIFTBGFUZBOEPQFSBUJOHJOTUSVDUJPOTTIPVMECFSFBE CFGPSFUIFQSPEVDUJTPQFSBUFE ,FFQUIFTFJOTUSVDUJPOT 5IFTBGFUZBOEPQFSBUJOHJOTUSVDUJPOTTIPVMECFSFUBJOFE GPSGVUVSFSFGFSFODF -

Greenpeace, Earth First! and the Earth Liberation Front: the Rp Ogression of the Radical Environmental Movement in America" (2008)
University of Rhode Island DigitalCommons@URI Senior Honors Projects Honors Program at the University of Rhode Island 2008 Greenpeace, Earth First! and The aE rth Liberation Front: The rP ogression of the Radical Environmental Movement in America Christopher J. Covill University of Rhode Island, [email protected] Follow this and additional works at: http://digitalcommons.uri.edu/srhonorsprog Part of the Environmental Sciences Commons Recommended Citation Covill, Christopher J., "Greenpeace, Earth First! and The Earth Liberation Front: The rP ogression of the Radical Environmental Movement in America" (2008). Senior Honors Projects. Paper 93. http://digitalcommons.uri.edu/srhonorsprog/93http://digitalcommons.uri.edu/srhonorsprog/93 This Article is brought to you for free and open access by the Honors Program at the University of Rhode Island at DigitalCommons@URI. It has been accepted for inclusion in Senior Honors Projects by an authorized administrator of DigitalCommons@URI. For more information, please contact [email protected]. Greenpeace, Earth First! and The Earth Liberation Front: The Progression of the Radical Environmental Movement in America Christopher John Covill Faculty Sponsor: Professor Timothy Hennessey, Political Science Causes of worldwide environmental destruction created a form of activism, Ecotage with an incredible success rate. Ecotage uses direct action, or monkey wrenching, to prevent environmental destruction. Mainstream conservation efforts were viewed by many environmentalists as having failed from compromise inspiring the birth of radicalized groups. This eventually transformed conservationists into radicals. Green Peace inspired radical environmentalism by civil disobedience, media campaigns and direct action tactics, but remained mainstream. Earth First’s! philosophy is based on a no compromise approach. -

Environmental Law Section Newsletter
LAW SECTION Susan Richardson, Editor Kilpatrick Stockton LLP Spring 2002 Protecting Against Environmental Terrorism by Robert D. Schmitter Senior Scientist and Head of Environmental Management and Technology Branch In This Issue: Georgia Tech Research Institute1 Protecting Against Introduction Environmental Protection of the environment is a major concern of both the public and private sectors, but it is now seen in a new light since the September 11 attacks exposed the vulnerabil- Terrorism . pg. 1 ity of certain segments of the country’s infrastructure to terrorist acts. Most environ- mental protection efforts have been directed at operations with the potential to cause From the Chair’s environmental damage as a result of accidental spills or releases of toxic materials. Desk . pg. 2 Attention has now turned to addressing issues of environmental terrorism, which can include the intentional release of hazardous materials via terrorist activities at facilities The Enviromental or operations, with a resultant tremendous adverse impact on the environment and the Litigator’s Procedual public. Primer on the Office of State Administra- What is Environmental Terrorism? tive Hearings . .pg. 3 The FBI defines terrorism as “the unlawful use of force or violence against persons or property to intimidate or coerce a government, the civilian population, or any segment An Overview of the thereof, in furtherance of political or social objectives.”2 Terrorism takes on many Small Business forms, including assassinations, homicide/suicide bombings, chemical or biological Liability Relief and attacks, and concerns about attacks on the environment and the associated impact on the public. Environmental terrorism has been defined as “the unlawful use of force Brownfields Revital- against in situ environmental resources as to deprive populations of their benefits and/ ization Act . -
4.1 Unit Circle Cosine & Sine (Slides 4-To-1).Pdf
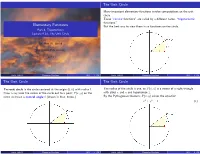
The Unit Circle Many important elementary functions involve computations on the unit circle. These \circular functions" are called by a different name, \trigonometric functions." Elementary Functions But the best way to view them is as functions on the circle. Part 4, Trigonometry Lecture 4.1a, The Unit Circle Dr. Ken W. Smith Sam Houston State University 2013 Smith (SHSU) Elementary Functions 2013 1 / 54 Smith (SHSU) Elementary Functions 2013 2 / 54 The Unit Circle The Unit Circle The unit circle is the circle centered at the origin (0; 0) with radius 1. The radius of the circle is one, so P (x; y) is a vertex of a right triangle Draw a ray from the center of the circle out to a point P (x; y) on the with sides x and y and hypotenuse 1. circle to create a central angle θ (drawn in blue, below.) By the Pythagorean theorem, P (x; y) solves the equation x2 + y2 = 1 (1) Smith (SHSU) Elementary Functions 2013 3 / 54 Smith (SHSU) Elementary Functions 2013 4 / 54 Central Angles and Arcs Central Angles and Arcs An arc of the circle corresponds to a central angle created by drawing line segments from the endpoints of the arc to the center. The Babylonians (4000 years ago!) divided the circle into 360 pieces, called degrees. This choice is a very human one; it does not have a natural mathematical reason. (It is not \intrinsic" to the circle.) The most natural way to measure arcs on a circle is by the intrinsic unit of measurement which comes with the circle, that is, the length of the radius. -

Download Thepdf
Volume 59, Issue 5 Page 1395 Stanford Law Review KEEPING CONTROL OF TERRORISTS WITHOUT LOSING CONTROL OF CONSTITUTIONALISM Clive Walker © 2007 by the Board of Trustees of the Leland Stanford Junior University, from the Stanford Law Review at 59 STAN. L. REV. 1395 (2007). For information visit http://lawreview.stanford.edu. KEEPING CONTROL OF TERRORISTS WITHOUT LOSING CONTROL OF CONSTITUTIONALISM Clive Walker* INTRODUCTION: THE DYNAMICS OF COUNTER-TERRORISM POLICIES AND LAWS................................................................................................ 1395 I. CONTROL ORDERS ..................................................................................... 1403 A. Background to the Enactment of Control Orders............................... 1403 B. The Replacement System..................................................................... 1408 1. Control orders—outline................................................................ 1408 2. Control orders—contents and issuance........................................ 1411 3. Non-derogating control orders..................................................... 1416 4. Derogating control orders............................................................ 1424 5. Criminal prosecution.................................................................... 1429 6. Ancillary issues............................................................................. 1433 7. Review by Parliament and the Executive...................................... 1443 C. Judicial Review.................................................................................. -

(U//FOUO) Terrorist Training and Recruitment of CONUS Subjects: Lackawanna, Portland, and Northern Virginia
UNCLASSIFIED//FOR OFFICIAL USE ONLY (U//FOUO) Terrorist Training and Recruitment of CONUS Subjects: Lackawanna, Portland, and Northern Virginia 30 October 2006 UNCLASSIFIED Prepared by FBI Counterterrorism Division UNCLASSIFIED//FOR OFFICIAL USE ONLY UNCLASSIFIED//FOR OFFICIAL USE ONLY (U//FOUO) Terrorist Training and Recruitment of CONUS Subjects: Lackawanna, Portland, and Northern Virginia (U//FOUO) Scope Note (U//FOUO) This assessment addresses the Terrorism (TERR) topic of the NIPF and the following FBI International Terrorism intelligence requirements: IT I.B.2-4; IT II.B.1. (U//FOUO) This assessment addresses the central role of terrorist training in three significant post-9/11 continental United States (CONUS) terrorism investigations: Lackawanna, Portland, and Northern Virginia. This assessment does not address other individuals who may have sought training independently, nor does it address groups of individuals who sought training in regions outside of South or Central Asia. (U//FOUO) This assessment is not a comprehensive account of terrorist training by CONUS subjects. It compares and contrasts these cases in order to illustrate the various ways CONUS subjects could be drawn into extremist circles and seek terrorist training in the United States and abroad. The information contained in this assessment is primarily derived from FBI case files and open source information and is current as of 25 October 2006. (U) This assessment was prepared by the FBI’s Threat Analysis Unit. Comments and queries may be addressed to the acting unit chief at 202-324-2292. UNCLASSIFIED//FOR OFFICIAL USE ONLY 2 UNCLASSIFIED//FOR OFFICIAL USE ONLY (U//FOUO) Key Judgments • (U//FOUO) Assessment of groups involved in the Lackawanna, Northern Virginia, and Portland cases suggests there is no single profile of groups that become involved in terrorist training. -

Assessing Security Threats to Canada's Energy Infrastructure
Assessing Security Threats to Canada’s Energy Infrastructure: The Enbridge Northern Gateway Pipeline By Jenny Benoit B.A., University of Guelph, 2011 Research Project Submitted In Partial Fulfillment of the Requirements for the Degree of Master of Arts in the School of Criminology Faculty of Arts and Social Science Jenny Benoit 2014 SIMON FRASER UNIVERSITY Summer 2014 Approval Name: Jenny Benoit Degree: Master of Arts (Criminology) Title of Thesis: Assessing Security Threats to Canada’s Energy Infrastructure: The Enbridge Northern Gateway Pipeline Examining Committee: Chair: William Glackman Associate Professor J. Bryan Kinney Senior Supervisor Associate Professor Garth Davies Supervisor Associate Professor Andrea Curman External Examiner Research Analyst, Police Services Division, Road Safety Unit BC Government, Ministry of Justice Date Defended/Approved: July 29, 2014 ii Partial Copyright Licence iii Abstract Safe and secure critical infrastructure is essential for the functioning of Canada's society. A robust system of infrastructure allows Canada to be a leader on the world stage but also presents potential security risks. Using open source data, this paper identifies why energy infrastructure is the ideal target for malicious attack and includes a focus on the proposed Enbridge Northern Gateway pipeline. Using the Harmonized Threat and Risk Assessment Methodology, to perform a risk based analysis; the likelihood of an attack on the Northern Gateway was assessed. A risk rating of low to medium was found, with a variety of vulnerabilities and possible threat actors identified. Keywords: Energy infrastructure, risk assessment, Northern Gateway pipeline iv Dedication To R.A. – Thank you. v Acknowledgements I would like to thank Dr.