Integrating LDAP with Payara® Server
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

MICHAEL STRÖDER Phone +49 721 8304316 [email protected]
Klauprechtstr. 11 D-76137 Karlsruhe, Germany MICHAEL STRÖDER Phone +49 721 8304316 [email protected] http://www.stroeder.com/ OBJECTIVE A contractor position as a consultant for planning and implementing identity and access management (IAM), security infrastructures (PKI, directory services) and related applications. CAPABILITIES • Planning / designing architectures and implementing mechanisms for secure usage of IT services (PKI, SSL, S/MIME, VPN, LDAP, Identity & Access Management (IAM), Single Sign-On, Firewalls) • Designing, implementing and automatically installing/configuring (DevOps) secure software (e.g. web applications), object-oriented software design and programming (e.g. Python) • System integration and user management in large and complex environments • Training and workshops EXPERIENCE Diverse Projekte (05/2019..12/2020) • Concepts, development, pilots, deployment, integration • Development: Python, migration to Python 3 • Software: OpenLDAP/Æ-DIR, keycloak, integration MS AD • Configuration management: ansible, puppet • Operating systems: Debian Linux, CentOS/RHEL, SLE • Hardening Linux: AppArmor, systemd IT-company Data Science (10/2019..09/2020) • Improved and updated internal IAM based on Æ-DIR (OpenLDAP) • Configuration management with ansible • 3rd-level support for operations As a trainer (05/2019..02/2020) • Python for system administrators • LDAP/OpenLDAP/IAM Versicherung (03/2019) • Implemented secure and highly available configuration of OpenLDAP servers used for customer user accounts • Implemented puppet -

Installation of Portal Applications
TIBCO Foresight® Transaction Insight® Installation of Portal Applications Software Release 5.2 September 2017 Two-Second Advantage® Important Information SOME TIBCO SOFTWARE EMBEDS OR BUNDLES OTHER TIBCO SOFTWARE. USE OF SUCHEM BEDDED OR BUNDLED TIBCO SOFTWARE IS SOLELY TO ENABLE THE FUNCTIONALITY (OR PROVIDE LIMITED ADD-ON FUNCTIONALITY) OF THE LICENSED TIBCO SOFTWARE. THE EMBEDDED OR BUNDLED SOFTWARE IS NOT LICENSED TO BE USED OR ACCESSED BY ANY OTHER TIBCO SOFTWARE OR FOR ANY OTHER PURPOSE. USE OF TIBCO SOFTWARE AND THIS DOCUMENT IS SUBJECT TO THE TERMS AND CONDITIONS OF A LICENSE AGREEMENT FOUND IN EITHER A SEPARATELY EXECUTED SOFTWARE LICENSE AGREEMENT, OR, IF THERE IS NO SUCH SEPARATE AGREEMENT, THE CLICKWRAP END USER LICENSE AGREEMENT WHICH IS DISPLAYED DURING DOWNLOAD OR INSTALLATION OF THE SOFTWARE (AND WHICH IS DUPLICATED IN THE LICENSE FILE) OR IF THERE IS NO SUCH SOFTWARE LICENSE AGREEMENT OR CLICKWRAP END USER LICENSE AGREEMENT, THE LICENSE(S) LOCATED IN THE “LICENSE” FILE(S) OF THE SOFTWARE. USE OF THIS DOCUMENT IS SUBJECT TO THOSE TERMS AND CONDITIONS, AND YOUR USE HEREOF SHALL CONSTITUTE ACCEPTANCE OF AND AN AGREEMENT TO BE BOUND BY THE SAME. This document contains confidential information that is subject to U.S. and international copyright laws and treaties. No part of this document may be reproduced in any form without the written authorization of TIBCO Software Inc. TIBCO, Two-Second Advantage, TIBCO BusinessConnect Insight, TIBCO Foresight Archive and Retrieval System, TIBCO Foresight BI Bridge – BAM, TIBCO Foresight EDISIM, TIBCO Foresight Instream, TIBCO Foresight Operational Monitor, TIBCO Foresight Studio, TIBCO Foresight Test Asset Management Suite, and TIBCO Foresight Transaction Insight are either registered trademarks or trademarks of TIBCO Software Inc. -

Hosting Requirements Smarter Balanced Assessment Consortium – Test Delivery System
Hosting Requirements Smarter Balanced Assessment Consortium – Test Delivery System American Institutes for Research Revision History Revision Description Author/Modifier Date Initial Release David Lopez de Quintana October 14, 2013 Updated to latest Amazon Web Service instance types and David Lopez de Quintana March 30, 2014 costs Updated concurrent student numbers, RDS IOP Jeff Treuting (Fairway) May 18, 2016 recommendation and AWS instance types Updated for TDS 3.1.0 Release Jeff Johnson (Fairway) July 10, 2017 Hosting Requirements Smarter Balanced Assessment Consortium Test Delivery System Contents Purpose ......................................................................................................................................................... 4 System Overview .......................................................................................................................................... 4 Component Software ................................................................................................................................... 6 Development/Operation Software Packages 6 Software Packages by Component 7 Deployment Assumptions .......................................................................................................................... 10 Deployment Configurations ....................................................................................................................... 10 Test Delivery Unit 11 Elastic Load Balancer 13 Web Server Instance Type 13 AWS ElastiCache – Redis Cluster -

Opendj Installation Guide Version 2.6
OpenDJ Installation Guide Version 2.6 Mark Craig ForgeRock AS 201 Mission St., Suite 2900 San Francisco, CA 94105, USA +1 415-599-1100 (US) www.forgerock.com Copyright © 2011-2016 ForgeRock AS. Abstract This guide shows you how to install OpenDJ directory services. The OpenDJ project offers open source LDAP directory services in Java. This work is licensed under the Creative Commons Attribution-NonCommercial-NoDerivs 3.0 Unported License. To view a copy of this license, visit http://creativecommons.org/licenses/by-nc-nd/3.0/ or send a letter to Creative Commons, 444 Castro Street, Suite 900, Mountain View, California, 94041, USA. ForgeRock™ is the trademark of ForgeRock Inc. or its subsidiaries in the U.S. and in other countries. Trademarks are the property of their respective owners. UNLESS OTHERWISE MUTUALLY AGREED BY THE PARTIES IN WRITING, LICENSOR OFFERS THE WORK AS-IS AND MAKES NO REPRESENTATIONS OR WARRANTIES OF ANY KIND CONCERNING THE WORK, EXPRESS, IMPLIED, STATUTORY OR OTHERWISE, INCLUDING, WITHOUT LIMITATION, WARRANTIES OF TITLE, MERCHANTIBILITY, FITNESS FOR A PARTICULAR PURPOSE, NONINFRINGEMENT, OR THE ABSENCE OF LATENT OR OTHER DEFECTS, ACCURACY, OR THE PRESENCE OF ABSENCE OF ERRORS, WHETHER OR NOT DISCOVERABLE. SOME JURISDICTIONS DO NOT ALLOW THE EXCLUSION OF IMPLIED WARRANTIES, SO SUCH EXCLUSION MAY NOT APPLY TO YOU. EXCEPT TO THE EXTENT REQUIRED BY APPLICABLE LAW, IN NO EVENT WILL LICENSOR BE LIABLE TO YOU ON ANY LEGAL THEORY FOR ANY SPECIAL, INCIDENTAL, CONSEQUENTIAL, PUNITIVE OR EXEMPLARY DAMAGES ARISING OUT OF THIS LICENSE OR THE USE OF THE WORK, EVEN IF LICENSOR HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. -

The Dzone Guide to Volume Ii
THE D ZONE GUIDE TO MODERN JAVA VOLUME II BROUGHT TO YOU IN PARTNERSHIP WITH DZONE.COM/GUIDES DZONE’S 2016 GUIDE TO MODERN JAVA Dear Reader, TABLE OF CONTENTS 3 EXECUTIVE SUMMARY Why isn’t Java dead after more than two decades? A few guesses: Java is (still) uniquely portable, readable to 4 KEY RESEARCH FINDINGS fresh eyes, constantly improving its automatic memory management, provides good full-stack support for high- 10 THE JAVA 8 API DESIGN PRINCIPLES load web services, and enjoys a diverse and enthusiastic BY PER MINBORG community, mature toolchain, and vigorous dependency 13 PROJECT JIGSAW IS COMING ecosystem. BY NICOLAI PARLOG Java is growing with us, and we’re growing with Java. Java 18 REACTIVE MICROSERVICES: DRIVING APPLICATION 8 just expanded our programming paradigm horizons (add MODERNIZATION EFFORTS Church and Curry to Kay and Gosling) and we’re still learning BY MARKUS EISELE how to mix functional and object-oriented code. Early next 21 CHECKLIST: 7 HABITS OF SUPER PRODUCTIVE JAVA DEVELOPERS year Java 9 will add a wealth of bigger-picture upgrades. 22 THE ELEMENTS OF MODERN JAVA STYLE But Java remains vibrant for many more reasons than the BY MICHAEL TOFINETTI robustness of the language and the comprehensiveness of the platform. JVM languages keep multiplying (Kotlin went 28 12 FACTORS AND BEYOND IN JAVA GA this year!), Android keeps increasing market share, and BY PIETER HUMPHREY AND MARK HECKLER demand for Java developers (measuring by both new job 31 DIVING DEEPER INTO JAVA DEVELOPMENT posting frequency and average salary) remains high. The key to the modernization of Java is not a laundry-list of JSRs, but 34 INFOGRAPHIC: JAVA'S IMPACT ON THE MODERN WORLD rather the energy of the Java developer community at large. -

Rakuten Card Smoothly Transition to Cloud-Native Architecture With
Case Study RakutenCase Study Card Smoothly Transition to Cloud-Native Architecture with Payara Server About Rakuten Card Established as its own credit card Enterprise brand in 2005, Rakuten Card Co. Ltd. is a Japanese credit card company formerly known as Rakuten Credit Inc. It has been recognised for In late 2017, Rakuten Card needed a reliable application server for its customer fac- achieving the number one credit card ing web applications. It found its best solution in Payara Server Enterprise: migrating shopping gross transaction value in Japan and hit the milestone of 20 in October 2017 for regular updates, improved support and services helping them in million credit card members in June achieving 99.9999% middleware availability. Two years later, Rakuten Card moved 2020. to a cloud-native architecture. It found Payara’s low maintenance technology and cloud-orientated features ensured a smooth transition with a stable version and flawless successful deployment. Industry: • Financial Challenges: The Initial Move to Payara Server • Banking Service Rakuten Card faced difficulties with its previous application server’s critical pending CVE bugs, memory leaks and sporadic errors without proper explanation in a stack Location: Tokyo, Japan trace. The expensive commercial support was too slow, and patches released intro- duced worsened security holes. Rakuten Card were looking for a support team who Software & Services: were well versed in Java based frameworks and could communicate in technical ter- • Payara Server Enterprise minology while resolving issues. • Java EE/Jakarta EE Moving to Payara Server Enterprise solved these issues, by providing monthly releases, bug fixes and patches, security improvements, and support directly from engineers within the Jakarta EE (Java EE) community. -
Hitachi Cloud Accelerator Platform Product Manager HCAP V 1
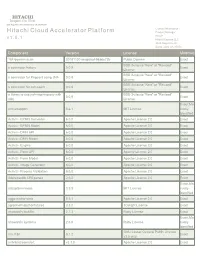
HITACHI Inspire the Next 2535 Augustine Drive Santa Clara, CA 95054 USA Contact Information : Hitachi Cloud Accelerator Platform Product Manager HCAP v 1 . 5 . 1 Hitachi Vantara LLC 2535 Augustine Dr. Santa Clara CA 95054 Component Version License Modified 18F/domain-scan 20181130-snapshot-988de72b Public Domain Exact BSD 3-clause "New" or "Revised" a connector factory 0.0.9 Exact License BSD 3-clause "New" or "Revised" a connector for Pageant using JNA 0.0.9 Exact License BSD 3-clause "New" or "Revised" a connector for ssh-agent 0.0.9 Exact License a library to use jsch-agent-proxy with BSD 3-clause "New" or "Revised" 0.0.9 Exact sshj License Exact,Ma activesupport 5.2.1 MIT License nually Identified Activiti - BPMN Converter 6.0.0 Apache License 2.0 Exact Activiti - BPMN Model 6.0.0 Apache License 2.0 Exact Activiti - DMN API 6.0.0 Apache License 2.0 Exact Activiti - DMN Model 6.0.0 Apache License 2.0 Exact Activiti - Engine 6.0.0 Apache License 2.0 Exact Activiti - Form API 6.0.0 Apache License 2.0 Exact Activiti - Form Model 6.0.0 Apache License 2.0 Exact Activiti - Image Generator 6.0.0 Apache License 2.0 Exact Activiti - Process Validation 6.0.0 Apache License 2.0 Exact Addressable URI parser 2.5.2 Apache License 2.0 Exact Exact,Ma adzap/timeliness 0.3.8 MIT License nually Identified aggs-matrix-stats 5.5.1 Apache License 2.0 Exact agronholm/pythonfutures 3.3.0 3Delight License Exact ahoward's lockfile 2.1.3 Ruby License Exact Exact,Ma ahoward's systemu 2.6.5 Ruby License nually Identified GNU Lesser General Public License ai's -

Download Java Ee Jdk Without Glassfish
Download java ee jdk without glassfish Is there any way I can install the Java EE SDK without the GlassFish Java because a bundle download package of Netbeans + the JDK exists. What you're asking is "can I get all the EE components" as a single download without GlassFish, NetBeans, etc. Well its helpful to know what. I assume you want the Java EE 6 API jar so you can write EJB applications Without Maven, you can download the jar from the repository. If your JDK installation is tied to the GlassFish application server, you (). Hi all is it possible to download Java EE SDK without GlassFish/GlassFish setup? Please I need a JDK I mean the latest one. The programs in my textbook are no more compiling guess it's kind of old. Please help. “Java Platform, Enterprise Edition 6 SDK Update 4 (with JDK 7u11)” or. java ee jdk without glassfish Download Link ?keyword=java-ee-jdk-without- glassfish&charset=utf-8 =========> java ee jdk without. GlassFish is the Open Source Java EE Reference Implementation; as such, we welcome external contributions. Make sure to read our Pull Request acceptance. Java EE 8 Tutorial Component. NetBeans IDE. Apache You can download JDK software from To Install NetBeans IDE without GlassFish Server. When you. Want all of our free Java training videos? Visit our Learning Library, which features all of our training courses. JDK 8 is required to use JavaFX 8 features in NetBeans IDE This download option also includes GlassFish Server Open Source Edition , from the Java EE download, launch the installer and select the Apache. -

JAVA EE Application Development in Practice Chapter 1: a Big Overview
JAVA EE Application Development in Practice Chapter 1: A Big Overview Sang Shin & Karim Djaafar Copyright JPassion Ó and Jasmine Conseil Ó 2018 AGENDA • What is Java EE • JEE Architecture • Enterprise Application Development • Java EE, a little story • The Java EE APIs • What’s new in Java EE 8 • Quick recap Copyright JPassion Ó and Jasmine Conseil Ó 2018 2 What is Java EE ? Fundamentals Concepts and Architecture Overview Copyright JPassion Ó and Jasmine Conseil Ó 2018 3 Introduction to Java EE • The Java Platform, Enterprise Edition (Java EE) is a collection of API specifications designed to work together when developing server-side, enterprise Java applications • Extension of Java SE • Simplify enterprise application development • Java EE is a standard : there are multiple implementations of the Java EE specifications Copyright JPassion Ó and Jasmine Conseil Ó 2018 4 Java EE is a Standard • Java EE go to a standardization process of the JCP, Java Community Process, an organization responsible for the development of Java technology • JCP members include Oracle (the current steward of the Java platform), and the Java community at large • The Java Community Process (JCP) allows interested parties to assist in developing standard technical specification for Java technology • Each Java EE API specification is developed as part of a Java Specification Request (JSR) • Each JSR is assigned a unique number. JavaServer Faces (JSF) 2.3 is developed as JSR 372, for instance Copyright JPassion Ó and Jasmine Conseil Ó 2018 5 Apache TomEE Java EE Implementation -

Distributed Data Framework Architecture
Distributed Data Framework Architecture Version 2.26.17. Copyright (c) Codice Foundation Table of Contents License. 1 1. Catalog Framework API . 2 2. Catalog API Design . 4 2.1. Ensuring Compatibility . 4 2.2. Catalog Framework Sequence Diagrams . 4 2.2.1. Error Handling. 5 2.2.2. Query . 5 2.2.3. Product Caching. 6 2.2.4. Product Download Status . 7 2.2.5. Catalog API . 7 2.2.5.1. Catalog API Search Interfaces. 7 2.2.5.2. Catalog Search Result Objects. 7 2.2.5.3. Search Programmatic Flow . 8 2.2.5.4. Sort Policies. 8 2.2.5.5. Product Retrieval . 9 2.2.5.6. Notifications and Activities . 10 2.3. Included Catalog Frameworks, Associated Components, and Configurations. 10 2.3.1. Standard Catalog Framework . 10 2.3.1.1. Installing the Standard Catalog Framework. 11 2.3.1.2. Configuring the Standard Catalog Framework . 11 2.3.1.3. Known Issues with Standard Catalog Framework . 12 2.3.2. Catalog Framework Camel Component . 12 2.3.2.1. Sending Messages to Catalog Framework Endpoint . 12 3. Transformers. 13 3.1. Available Input Transformers . 15 3.2. Available Metacard Transformers . 16 3.3. Available Query Response Transformers . 16 3.4. Transformers Details . 17 3.4.1. Atom Query Response Transformer . 17 3.4.1.1. Installing the Atom Query Response Transformer . 17 3.4.1.2. Configuring the Atom Query Response Transformer . 17 3.4.1.3. Using the Atom Query Response Transformer. 17 3.4.2. CSW Query Response Transformer . 21 3.4.2.1. -

Advanced Authentication 6.3 Administration Guide
Advanced Authentication 6.3 Administration Guide December 2019 Legal Notice For information about legal notices, trademarks, disclaimers, warranties, export and other use restrictions, U.S. Government rights, patent policy, and FIPS compliance, see http://www.microfocus.com/about/legal/. © Copyright 2021 Micro Focus or one of its affiliates. 2 Contents About this Book 15 1 Introduction to Advanced Authentication 17 1.1 How Is Advanced Authentication Better Than Other Solutions. .17 1.2 Key Features. .17 1.3 Advanced Authentication Server Components . .18 1.3.1 Administration Portal . .19 1.3.2 Self-Service Portal. .19 1.3.3 Helpdesk Portal. .20 1.3.4 Reporting Portal . .20 1.4 Architecture . .20 1.4.1 Basic Architecture. .20 1.4.2 Enterprise Level Architecture . .21 1.4.3 Enterprise Architecture With A Load Balancer. .23 1.5 Terminologies. .24 1.5.1 Authentication Method . .24 1.5.2 Authentication Chain . .24 1.5.3 Authentication Event . .24 1.5.4 Endpoint . .24 Part I Configuring Advanced Authentication 25 2 Logging In to the Advanced Authentication Administration Portal27 3 End to End Configuration with Examples 29 3.1 Implementing Multi-Factor Authentication to VPN . .29 3.1.1 Prerequisites . .30 3.1.2 Considerations Before Configuration . 30 3.1.3 Add a Repository. .31 3.1.4 Configure Methods. .32 3.1.5 Create a Chain. .32 3.1.6 Configure Public External URLs Policy. .32 3.1.7 Assign Chain to RADIUS Server Event . 33 3.1.8 Configure the OpenVPN Server . .33 3.1.9 End User Tasks . .34 3.2 Securing Windows Workstation with Multi-Factor Authentication. -

Pliego Prescripciones Técnicas
MINISTERIO SUBSECRETARÍA DE HACIENDA Y FUNCIÓN PÚBLICA COMISIONADO PARA EL MERCADO DE TABACOS PLIEGO DE PRESCRIPCIONES TÉCNICAS PARA LA CONTRATACIÓN DE SERVICIOS DE ASISTENCIA TÉCNICA PARA LA ADMINISTRACIÓN Y MANTENIMIENTO DE SISTEMAS INFORMÁTICOS EN EL ÁMBITO DEL COMISIONADO PARA EL MERCADO DE TABACOS Pº HABANA 140 28036 MADRID TEL.: 91 745 72 00 Página 1 de 23 FAX: 91 745 72 12 [email protected] CODIGO DIR 3: E00120903 MINISTERIO SUBSECRETARÍA DE HACIENDA Y FUNCIÓN PÚBLICA COMISIONADO PARA EL MERCADO DE TABACOS 201700000053 I. REQUERIMIENTOS TÉCNICOS ................................................................................................... 3 I.1 .- SEDE DEL COMISIONADO ................................................................................................ 3 I.2 .- ÁMBITO DE APLICACIÓN Y ALCANCE ............................................................................. 3 I.3 .- ESPECIFICACIONES TÉCNICAS DEL CONTRATO .......................................................... 3 II. PRESTACIONES OBLIGATORIAS DEL SERVICIO .................................................................. 10 II.1 .- SERVICIO DE EXPLOTACIÓN ......................................................................................... 10 II.2 .- SERVICIO DE ADMINISTRACIÓN, MANTENIMIENTO Y ACTUALIZACIÓN DE SISTEMAS ...................................................................................................................................... 11 II.3 .- SERVICIOS CON DISPONIBILIDAD 24X7 ......................................................................