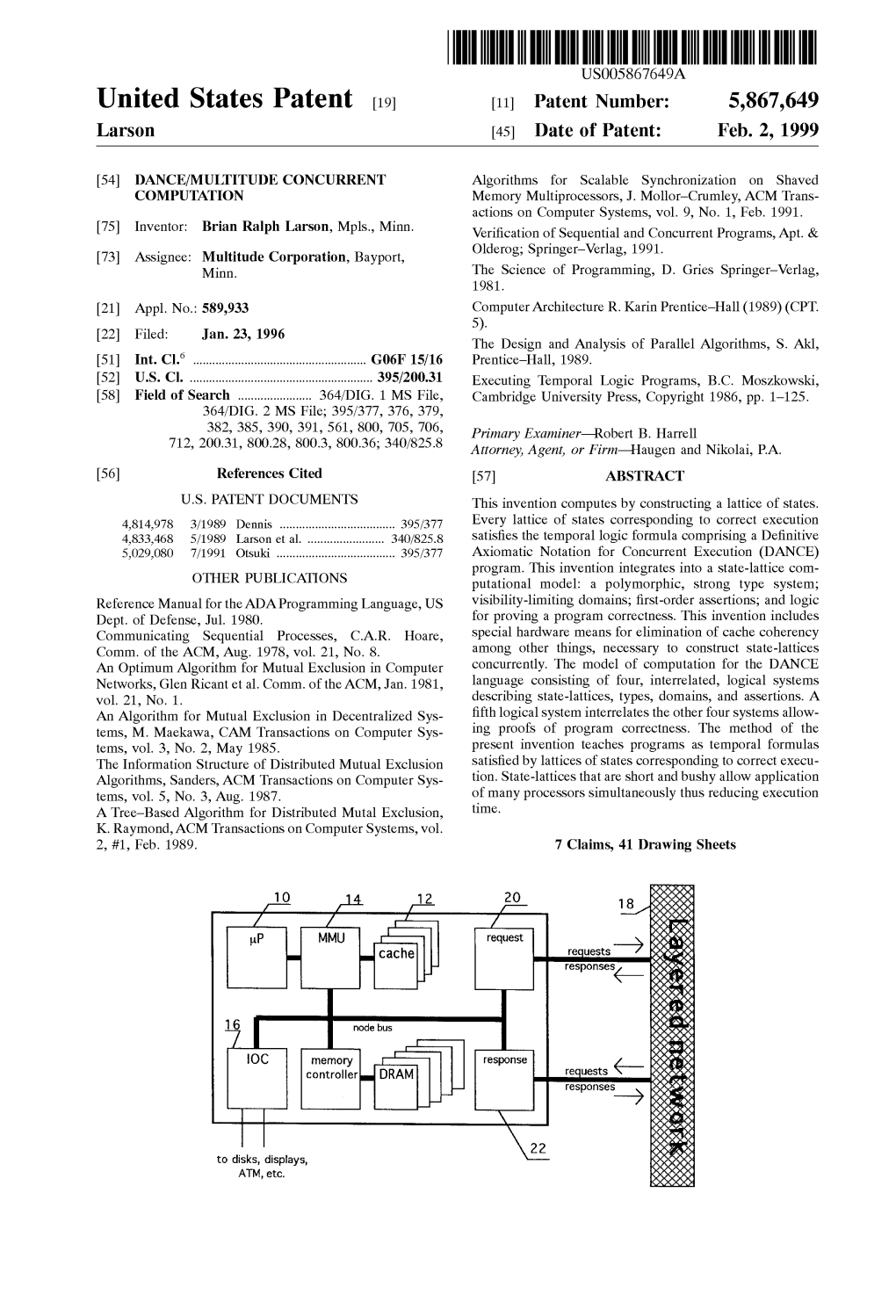
8 : : H Responses -> : : : S: to Disks, Displays, 8 : : ATM, Etc
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

1 Lecture 13: Quantifier Laws1 1. Laws of Quantifier Negation There
Ling 409 lecture notes, Lecture 13 Ling 409 lecture notes, Lecture 13 October 19, 2005 October 19, 2005 Lecture 13: Quantifier Laws1 true or there is at least one individual that makes φ(x) true (or both). Those are also equivalent statements. 1. Laws of Quantifier Negation Laws 2 and 3 suggest a fundamental connection between universal quantification and There are a number of equivalences based on the set-theoretic semantics of predicate logic. conjunction and existential quantification and disjunction: Take for instance a statement of the form (∃x)~ φ(x)2. It asserts that there is at least one individual d which makes ~φ(x) true. That means that d makes ϕ(x) false. That, in turn, (∀x) ψ(x) is true iff ψ(a) and ψ(b) and ψ(c) … (where a, b, c … are the names of the means that (∀x) φ(x) is false, which means that ~(∀x) φ(x) is true. The same reasoning individuals in the domain.) can be applied in the reverse direction and the result is the first quantifier law: ∃ ψ ψ ψ ψ ( x) (x) is true iff (a) or (b) or c) … (where a, b, c … are the names of the (1) Laws of Quantifier Negation individuals in the domain.) Law 1: ~(∀x) φ(x) ⇐⇒ (∃x)~ φ(x) From that point of view, Law 1 resembles a generalized DeMorgan’s Law: (Possible English correspondents: Not everyone passed the test and Someone did not pass (4) ~(ϕ(a) & ϕ(b) & ϕ(c) … ) ⇐⇒ ~ϕ(a) v ~ϕ(b) v ϕ(c) … the test.) (5) Law 4: (∀x) ψ(x) v (∀x)φ(x) ⇒ (∀x)( ψ(x) v φ(x)) ϕ ⇐ ϕ Because of the Law of Double Negation (~~ (x) ⇒ (x)), Law 1 could also be written (6) Law 5: (∃x)( ψ(x) & φ(x)) ⇒ (∃x) ψ(x) & (∃x)φ(x) as follows: These two laws are one-way entailments, NOT equivalences. -

Lexical Scoping As Universal Quantification
University of Pennsylvania ScholarlyCommons Technical Reports (CIS) Department of Computer & Information Science March 1989 Lexical Scoping as Universal Quantification Dale Miller University of Pennsylvania Follow this and additional works at: https://repository.upenn.edu/cis_reports Recommended Citation Dale Miller, "Lexical Scoping as Universal Quantification", . March 1989. University of Pennsylvania Department of Computer and Information Science Technical Report No. MS-CIS-89-23. This paper is posted at ScholarlyCommons. https://repository.upenn.edu/cis_reports/785 For more information, please contact [email protected]. Lexical Scoping as Universal Quantification Abstract A universally quantified goal can be interpreted intensionally, that is, the goal ∀x.G(x) succeeds if for some new constant c, the goal G(c) succeeds. The constant c is, in a sense, given a scope: it is introduced to solve this goal and is "discharged" after the goal succeeds or fails. This interpretation is similar to the interpretation of implicational goals: the goal D ⊃ G should succeed if when D is assumed, the goal G succeeds. The assumption D is discharged after G succeeds or fails. An interpreter for a logic programming language containing both universal quantifiers and implications in goals and the body of clauses is described. In its non-deterministic form, this interpreter is sound and complete for intuitionistic logic. Universal quantification can provide lexical scoping of individual, function, and predicate constants. Several examples are presented to show how such scoping can be used to provide a Prolog-like language with facilities for local definition of programs, local declarations in modules, abstract data types, and encapsulation of state. -

Sets, Propositional Logic, Predicates, and Quantifiers
COMP 182 Algorithmic Thinking Sets, Propositional Logic, Luay Nakhleh Computer Science Predicates, and Quantifiers Rice University !1 Reading Material ❖ Chapter 1, Sections 1, 4, 5 ❖ Chapter 2, Sections 1, 2 !2 ❖ Mathematics is about statements that are either true or false. ❖ Such statements are called propositions. ❖ We use logic to describe them, and proof techniques to prove whether they are true or false. !3 Propositions ❖ 5>7 ❖ The square root of 2 is irrational. ❖ A graph is bipartite if and only if it doesn’t have a cycle of odd length. ❖ For n>1, the sum of the numbers 1,2,3,…,n is n2. !4 Propositions? ❖ E=mc2 ❖ The sun rises from the East every day. ❖ All species on Earth evolved from a common ancestor. ❖ God does not exist. ❖ Everyone eventually dies. !5 ❖ And some of you might already be wondering: “If I wanted to study mathematics, I would have majored in Math. I came here to study computer science.” !6 ❖ Computer Science is mathematics, but we almost exclusively focus on aspects of mathematics that relate to computation (that can be implemented in software and/or hardware). !7 ❖Logic is the language of computer science and, mathematics is the computer scientist’s most essential toolbox. !8 Examples of “CS-relevant” Math ❖ Algorithm A correctly solves problem P. ❖ Algorithm A has a worst-case running time of O(n3). ❖ Problem P has no solution. ❖ Using comparison between two elements as the basic operation, we cannot sort a list of n elements in less than O(n log n) time. ❖ Problem A is NP-Complete. -

CHAPTER 1 the Main Subject of Mathematical Logic Is Mathematical
CHAPTER 1 Logic The main subject of Mathematical Logic is mathematical proof. In this chapter we deal with the basics of formalizing such proofs and analysing their structure. The system we pick for the representation of proofs is natu- ral deduction as in Gentzen (1935). Our reasons for this choice are twofold. First, as the name says this is a natural notion of formal proof, which means that the way proofs are represented corresponds very much to the way a careful mathematician writing out all details of an argument would go any- way. Second, formal proofs in natural deduction are closely related (via the Curry-Howard correspondence) to terms in typed lambda calculus. This provides us not only with a compact notation for logical derivations (which otherwise tend to become somewhat unmanageable tree-like structures), but also opens up a route to applying the computational techniques which un- derpin lambda calculus. An essential point for Mathematical Logic is to fix the formal language to be used. We take implication ! and the universal quantifier 8 as basic. Then the logic rules correspond precisely to lambda calculus. The additional connectives (i.e., the existential quantifier 9, disjunction _ and conjunction ^) will be added via axioms. Later we will see that these axioms are deter- mined by particular inductive definitions. In addition to the use of inductive definitions as a unifying concept, another reason for that change of empha- sis will be that it fits more readily with the more computational viewpoint adopted there. This chapter does not simply introduce basic proof theory, but in addi- tion there is an underlying theme: to bring out the constructive content of logic, particularly in regard to the relationship between minimal and classical logic. -

Precomplete Negation and Universal Quantification
PRECOMPLETE NEGATION AND UNIVERSAL QUANTIFICATION by Paul J. Vada Technical Report 86-9 April 1986 Precomplete Negation And Universal Quantification. Paul J. Voda Department of Computer Science, The University of British Columbia, Vancouver, B.C. V6T IW5, Canada. ABSTRACT This paper is concerned with negation in logic programs. We propose to extend negation as failure by a stronger form or negation called precomplete negation. In contrast to negation as failure, precomplete negation has a simple semantic charaterization given in terms of computational theories which deli berately abandon the law of the excluded middle (and thus classical negation) in order to attain computational efficiency. The computation with precomplete negation proceeds with the direct computation of negated formulas even in the presence of free variables. Negated formulas are computed in a mode which is dual to the standard positive mode of logic computations. With uegation as failure the formulas with free variables must be delayed until the latter obtain values. Consequently, in situations where delayed formulas are never sufficiently instantiated, precomplete negation can find solutions unattainable with negation as failure. As a consequence of delaying, negation as failure cannot compute unbounded universal quantifiers whereas precomplete negation can. Instead of concentrating on the model-theoretical side of precomplete negation this paper deals with questions of complete computations and efficient implementations. April 1986 Precomplete Negation And Universal Quanti.flcation. Paul J. Voda Department or Computer Science, The University or British Columbia, Vancouver, B.C. V6T 1W5, Canada. 1. Introduction. Logic programming languages ba.5ed on Prolog experience significant difficulties with negation. There are many Prolog implementations with unsound negation where the computation succeeds with wrong results. -

Not All There: the Interactions of Negation and Universal Quantifier Pu
Not all there: The interactions of negation and universal quantifier Puk'w in PayPaˇȷuT@m∗ Roger Yu-Hsiang Lo University of British Columbia Abstract: The current paper examines the ambiguity between negation and the univer- sal quantifier Puk'w in PayPaˇȷuT@m, a critically endangered Central Salish language. I ar- gue that the ambiguity in PayPaˇȷuT@m arises from the nonmaximal, exception-tolerating property of Salish all, instead of resorting to the scopal interaction between negation and the universal quantifier, as in English. Specifically, by assuming that negation in PayPaˇȷuT@m is always interpreted with the maximal force, the ambiguity can be under- stood as originating from exceptions to this canonical interpretation. Whether or not this ambiguity is only available in PayPaˇȷuT@m is still unclear, and further data elicitation and cross-Salish comparison are underway. Keywords: PayPaˇȷuT@m (Mainland Comox), semantics, ambiguities, negation, univer- sal quantifier 1 Introduction This paper presents a preliminary analysis of the semantic ambiguity involved in the combination of negation and the universal quantifier Puk'w in PayPaˇȷuT@m, a critically endangered Central Salish language. The ambiguity between a negative element and a universal quantifier is also found in English. For example, consider the English paradigm in (1) from Carden (1976), where (1a) has only one reading while (1b) is ambiguous. (1) a. Not all the boys will run. :(8x;boy(x);run(x)) b. [ All the boys ] won’t run. i. :(8x;boy(x);run(x)) ii. (8x;boy(x));:(run(x)) In the traditional account, with the readings in (1a) and (1b-i), negation takes higher scope than the quantified DP at LF. -

On Operator N and Wittgenstein's Logical Philosophy
JOURNAL FOR THE HISTORY OF ANALYTICAL PHILOSOPHY ON OPERATOR N AND WITTGENSTEIN’S LOGICAL VOLUME 5, NUMBER 4 PHILOSOPHY EDITOR IN CHIEF JAMES R. CONNELLY KEVIN C. KLEMENt, UnIVERSITY OF MASSACHUSETTS EDITORIAL BOARD In this paper, I provide a new reading of Wittgenstein’s N oper- ANNALISA COLIVA, UnIVERSITY OF MODENA AND UC IRVINE ator, and of its significance within his early logical philosophy. GaRY EBBS, INDIANA UnIVERSITY BLOOMINGTON I thereby aim to resolve a longstanding scholarly controversy GrEG FROSt-ARNOLD, HOBART AND WILLIAM SMITH COLLEGES concerning the expressive completeness of N. Within the debate HENRY JACKMAN, YORK UnIVERSITY between Fogelin and Geach in particular, an apparent dilemma SANDRA LaPOINte, MCMASTER UnIVERSITY emerged to the effect that we must either concede Fogelin’s claim CONSUELO PRETI, THE COLLEGE OF NEW JERSEY that N is expressively incomplete, or reject certain fundamental MARCUS ROSSBERG, UnIVERSITY OF CONNECTICUT tenets within Wittgenstein’s logical philosophy. Despite their ANTHONY SKELTON, WESTERN UnIVERSITY various points of disagreement, however, Fogelin and Geach MARK TEXTOR, KING’S COLLEGE LonDON nevertheless share several common and problematic assump- AUDREY YAP, UnIVERSITY OF VICTORIA tions regarding Wittgenstein’s logical philosophy, and it is these RICHARD ZACH, UnIVERSITY OF CALGARY mistaken assumptions which are the source of the dilemma. Once we recognize and correct these, and other, associated ex- REVIEW EDITORS pository errors, it will become clear how to reconcile the ex- JULIET FLOYD, BOSTON UnIVERSITY pressive completeness of Wittgenstein’s N operator, with sev- CHRIS PINCOCK, OHIO STATE UnIVERSITY eral commonly recognized features of, and fundamental theses ASSISTANT REVIEW EDITOR within, the Tractarian logical system. -

Existential Quantification
Quantification 1 From last time: Definition: Proposition A declarative sentence that is either true (T) or false (F), but not both. • Tucson summers never get above 100 degrees • If the doorbell rings, then my dog will bark. • You can take the flight if and only if you bought a ticket • But NOT x < 10 Why do we want use variables? • Propositional logic is not always expressive enough • Consider: “All students like summer vacation” • Should be able to conclude that “If Joe is a student, he likes summer vacation”. • Similarly, “If Rachel is a student, she likes summer vacation” and so on. • Propositional Logic does not support this! Predicates Definition: Predicate (a.k.a. Propositional Function) A statement that includes at least one variable and will evaluate to either true or false when the variables(s) are assigned value(s). • Example: S(x) : (−10 < x) ∧ (x < 10) E(a, b) : a eats b • These are not complete! Predicates Definition: Domain (a.ka. Universe) of Discourse The collection of values from which a variable’s value is drawn. • Example: S(x) : (−10 < x) ∧ (x < 10), x ∈ ℤ E(a, b) : a eats b, a ∈ People, b ∈ Vegetables • In This Class: Domains may NOT hide operators • OK: Vegetables • Not-OK: Raw Vegetables (Vegetable ∧ ¬Cooked) Predicates S(x) : (−10 < x) ∧ (x < 10), x ∈ ℤ E(a, b) : a eats b, a ∈ People, b ∈ Vegetables • Can evaluate predicates at specific values (making them propositions): • What is E(Joe, Asparagus)? • What is S(0)? Combining Predicates with Logical Operators • In E(a, b) : a eats b, a ∈ people, b ∈ vegetables, change the domain of b to “raw vegetables”. -

An Introduction to Formal Logic
forall x: Calgary An Introduction to Formal Logic By P. D. Magnus Tim Button with additions by J. Robert Loftis Robert Trueman remixed and revised by Aaron Thomas-Bolduc Richard Zach Fall 2021 This book is based on forallx: Cambridge, by Tim Button (University College Lon- don), used under a CC BY 4.0 license, which is based in turn on forallx, by P.D. Magnus (University at Albany, State University of New York), used under a CC BY 4.0 li- cense, and was remixed, revised, & expanded by Aaron Thomas-Bolduc & Richard Zach (University of Calgary). It includes additional material from forallx by P.D. Magnus and Metatheory by Tim Button, used under a CC BY 4.0 license, from forallx: Lorain County Remix, by Cathal Woods and J. Robert Loftis, and from A Modal Logic Primer by Robert Trueman, used with permission. This work is licensed under a Creative Commons Attribution 4.0 license. You are free to copy and redistribute the material in any medium or format, and remix, transform, and build upon the material for any purpose, even commercially, under the following terms: ⊲ You must give appropriate credit, provide a link to the license, and indicate if changes were made. You may do so in any reasonable manner, but not in any way that suggests the licensor endorses you or your use. ⊲ You may not apply legal terms or technological measures that legally restrict others from doing anything the license permits. The LATEX source for this book is available on GitHub and PDFs at forallx.openlogicproject.org. -

Universal Quantification in a Constraint-Based Planner
Universal Quantification in a Constraint-Based Planner Keith Golden and Jeremy Frank NASA Ames Research Center Mail Stop 269-1 Moffett Field, CA 94035 {kgolden,frank}@ptolemy.arc.nasa.gov Abstract Incomplete information: It is common for softbots to • have only incomplete information about their environ- We present a general approach to planning with a restricted class of universally quantified constraints. These constraints ment. For example, a softbot is unlikely to know about stem from expressive action descriptions, coupled with large all the files on the local file system, much less all the files or infinite universes and incomplete information. The ap- available over the Internet. proach essentially consists of checking that the quantified Large or infinite universes: The size of the universe is constraint is satisfied for all members of the universe. We • generally very large or infinite. For example, there are present a general algorithm for proving that quantified con- straints are satisfied when the domains of all of the variables hundreds of thousands of files accessible on a typical file are finite. We then describe a class of quantified constraints system and billions of web pages publicly available over for which we can efficiently prove satisfiability even when the Internet. The number of possible files, file path names, the domains are infinite. These form the basis of constraint etc., is effectively infinite. Given the presence of incom- reasoning systems that can be used by a variety of planners. plete information and the ability to create new files, it is necessary to reason about these infinite sets. 1 Introduction Constraints: As noted in (Chien et al. -

(Universal) Quantification: a Generalised Quantifier Theory Analysis of -Men∗
1 Covert (Universal) Quantification: A Generalised Quantifier Theory Analysis of -men∗ Sherry Yong Chen University of Oxford Introduction This paper explores the hypothesis of covert quantification – the idea that some nominals can be treated as having a (universal) quantifier covertly – by examining the interaction between the suffix -men and the particle dou within the Generalised Quantifier Theory framework (Barwise & Cooper, 1981; henceforth GQT). I begin by introducing the puzzle posed by -men in Mandarin Chinese (henceforth Chinese), a suffix that has been widely analysed as a collective marker but demonstrates various features of a plural marker. I argue that neither analysis is satisfactory given the interaction of -men and dou, the latter of which can be analysed as the lexical representation of the Matching Function (Rothstein, 1995; henceforth the M-Function). Crucially, the collective analysis of -men fails to explain why it can co-occur with dou, which requires access to individual atoms, while the plural analysis of -men fails to predict many of its distributions and interpretations. In light of these puzzles, I observe that when there is no overt universal quantifier in the sentence, nominals with -men turn out to be ambiguous between a strong and a weak reading, but they must receive a definite interpretation and have a “significant subpart” requirement, analogous to the semantic denotation of most of the X. This motivates the GQT treatment of - men which assumes covert quantification in its semantic representation. Moreover, the two readings of -men disambiguate in the presence of dou, with only the strong reading left, which further suggests the existence of a covert universal quantifier in -men, given that dou as the M-Function seeks a universal quantifier in the semantic composition (Pan, 2005; Zhang, 2007). -

Negation and Quantification. a New Look at the Square of Opposition
Negation and Quantification. A New Look at the Square of Opposition Dag Westerst˚ahl Stockholm University 1 Outline This paper is about how the fundamental logical notions of negation and quan- tification interact. The subject is as old as logic itself, and appears in various forms in all ancient traditions in logic, but perhaps most explicitly and system- atically in the Western tradition starting with Aristotle, which is the one I will refer to here. Many of the issues raised by Aristotle and his followers are still subject of lively debate among linguists and philosophers today. Negation is closely tied to opposition: a statement and its negation are in some sense opposed to each other. There are different kinds of opposition (and philosophers love displaying all kinds of opposing pairs), but Aristotle's main distinction is between contradictory and contrary opposition or negation. The contradictory negation of Socrates is wise is simply Socrates is not wise, which is true if and only if the positive statement is false. But there are several contrary negations: Socrates is non-wise/unwise/foolish/ . ; the hallmark of contrariety is that a statement and its contrary cannot both be true. The contrast between contrariety and contradictoriness becomes clearer, and simpler, when applied to quantified statements. Aristotle's syllogistics|the beginning of modern logic|is a systematic study of relations between the four quantifiers all, no, some, not all, and in particular of how they interact with negation. The contrary of all is no, whose contradictory negation is some. (Really it is the corresponding statements, all A are B, no A are B, etc.