Micro Focus Fortify Static Code Analyzer User Guide, Which Are No Longer Published As of This Release
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Using Findbugs in Anger
Making Static Analysis Part Of Your Build Process William Pugh Professor, Univ. of Maryland Visiting Scientist, Google Learn how to effectively use FindBugs on large software projects (100,000+ lines of code), and make effective use of the limited time you can schedule/afford for static analysis 2 Agenda FindBugs and static analysis Using FindBugs effectively Running FindBugs Scaling up FindBugs Historical Bug results 3 Static Analysis Analyzes your program without executing it Doesn’t depend on having good test cases • or even any test cases Doesn’t know what your software is supposed to do • Looks for violations of reasonable programming practices • Shouldn’t throw NPE • All statements should be reachable • Shouldn’t allow SQL injection Not a replacement for testing • Very good at finding problems on untested paths • But many defects can’t be found with static analysis 4 Common (Incorrect) Wisdom about Bugs and Static Analysis Programmers are smart Smart people don’t make dumb mistakes We have good techniques (e.g., unit testing, pair programming, code inspections) for finding bugs early I tried lint and it sucked: lots of warnings, few real issues So, bugs remaining in production code must be subtle, and finding them must require sophisticated static analysis techniques 5 Can You Find The Bug? if (listeners == null) listeners.remove(listener); JDK1.6.0, b105, sun.awt.x11.XMSelection • lines 243-244 6 Why Do Bugs Occur? Nobody is perfect Common types of errors: • Misunderstood language features, API methods • Typos (using wrong boolean -

Towards Our Development Environment
Euclid Consortium Towards our development environment 2012, Dec. 4th SDC meeting 1 Euclid External constraints Consortium ● CODEEN (Redmine and http://apceucliddev.in2p3.fr/jenkins/) ● Common tools – Python / C++ – Jira – Eclipse – Sonar – Subversion – Doxygen – Xunit – Goolge talk – Maven – Redmine – Nexus – Adobe Connect – Jenkins 2012, Dec. 4th SDC meeting 2 Euclid Language and architecture Consortium ● Language: Python (C, C++) ● Central svn repository (http://euclid.esac.esa.int/svn/EC/SGS/) ● IDE: Eclipse + PyDev ● Software architecture and packaging – Model the testbed, data trains and taker Gaia concepts – Separate the data handling and algorithmic programming – Data model, Framework, Algo (projects? Modules?) ● Study flexible solutions for – local development, testing and survey data analysis – integration into the IAL – distributing the software? 2012, Dec. 4th SDC meeting 3 Euclid Data model and data handling Consortium ● Data model: first version as XML schema on SVN – PyXB for automatic Python code generation ● Framework with data handling, loading data from – ASCII files : SciPy (loadtxt) – Database : SQLAlchemy ORM – FITS files : PyFits ● Panda : large table ● Pickle : object serialization 2012, Dec. 4th SDC meeting 4 Euclid Dependencies and building managementConsortium ● Nexus, Ivy and Ant used in Gaia ● Maven - Nexus is proposed, is it too Java oriented? – Difference between Ant and Maven? ● How can we used the Python “setup” files ● Hubert proposals – http://zero-install.sourceforge.net/ – http://www.cmake.org/ ● Solution for – local software development and usage – distribution 2012, Dec. 4th SDC meeting 5 Euclid Configuration, testing and doc Consortium ● Solution for handling configuration – model the Gaia XML based solution? (Java “properties” thread unsafe) – Python solution? Init? ● Testing set up and conventions – xUnit and PyUnit? ● Javadoc as an example (look up in Eclipse, automatic doc generation) – Doxygen 2012, Dec. -

Technologies We Use IT Project Management
SolDevelo Sp. z o.o. is a dynamic software development and information technology outsourcing company, focused on delivering high quality software and innovative solutions. Our approach is a unique mix of highly experienced development team, client-oriented service and passion for IT. This guarantees projects to be completed on time, with the superior quality and precisely the way client imagined it. IT Project Management Requirements Specification Architecture Implementation Detailed Design Testing Integration Validation Maintenance Technologies We Use Software development and Integration Ý Application Servers Languages Web Servers Glassfish, JBOSS, Geronimo Java/JEE, Python, C#/.NET Nginx, Apache HTTP Android, PHP, Objective-C, Swift, Ruby Frameworks Web Technologies Database Environments Hibernate, Datanucleus, J2EE, PHP, XML, JavaScript, Oracle, SQL, PL/SQL, MySQL, OSGi, Spring Integration, SOAP, WSDL, RichFaces, PostgreSQL, HSQLDB, CouchDB, Quartz, Spring Batch, jQuery, JSP, JSF, AJAX, (S)CSS, SQLite3, Hypersonic Android Designer, LESS, XHTML, ASP.NET, Robotium, JBoss Seam Node.js Mobile Technologies Servlet Containers Android, iOS Tomcat, Jetty Web Frameworks AngularJS, Django, Spring WebFlow, Bootstrap, Zend, Ə CMS ǡ Business Intelligence Symfony, Express, Ruby on Rails Drupal, Wordpress, Joomla! DHIS2, Tableau 01 Competence Map Tools we use IDE Wiki < Knowledge Sharing IntelliJ IDEA, Eclipse, Android Confluence, Assembla Wiki, Trac Studio, Xcode, PHPStorm Project Methodology Issue/Bug Tracking Agile/Scrum JIRA, Assembla, -

Evaluating the Flexibility of the Java Sandbox
Evaluating the Flexibility of the Java Sandbox Zack Coker, Michael Maass, Tianyuan Ding, Claire Le Goues, and Joshua Sunshine Carnegie Mellon University {zfc,mmaass}@cs.cmu.edu, [email protected], {clegoues,sunshine}@cs.cmu.edu ABSTRACT should protect both the host application and machine from The ubiquitously-installed Java Runtime Environment (JRE) malicious behavior. In practice, these security mechanisms provides a complex, flexible set of mechanisms that support are problematically buggy such that Java malware is often the execution of untrusted code inside a secure sandbox. able to alter the sandbox's settings [4] to override security However, many recent exploits have successfully escaped the mechanisms. Such exploits take advantage of defects in either sandbox, allowing attackers to infect numerous Java hosts. the JRE itself or the application's sandbox configuration to We hypothesize that the Java security model affords devel- disable the security manager, the component of the sandbox opers more flexibility than they need or use in practice, and responsible for enforcing the security policy [5, 6, 7, 8]. thus its complexity compromises security without improving In this paper, we investigate this disconnect between theory practical functionality. We describe an empirical study of the and practice. We hypothesize that it results primarily from ways benign open-source Java applications use and interact unnecessary complexity and flexibility in the design and with the Java security manager. We found that developers engineering of Java's security mechanisms. For example, regularly misunderstand or misuse Java security mechanisms, applications are allowed to change the security manager at that benign programs do not use all of the vast flexibility runtime, whereas static-only configuration of the manager afforded by the Java security model, and that there are clear would be more secure. -

Silk Test 17.5
Silk Test 17.5 Silk4J User Guide Micro Focus The Lawn 22-30 Old Bath Road Newbury, Berkshire RG14 1QN UK http://www.microfocus.com Copyright © Micro Focus 2016. All rights reserved. MICRO FOCUS, the Micro Focus logo and Silk Test are trademarks or registered trademarks of Micro Focus IP Development Limited or its subsidiaries or affiliated companies in the United States, United Kingdom and other countries. All other marks are the property of their respective owners. 2016-11-03 ii Contents Welcome to Silk4J 17.5 ......................................................................................9 Licensing Information ......................................................................................10 Silk4J ................................................................................................................ 11 Do I Need Administrator Privileges to Run Silk4J? ........................................................... 11 Best Practices for Using Silk4J ........................................................................................ 11 Automation Under Special Conditions (Missing Peripherals) ............................................12 Silk Test Product Suite ...................................................................................................... 13 What's New in Silk4J ........................................................................................15 Mobile Device Live View ................................................................................................... 15 Testing Hybrid -

Eclipsereview 200612.Pdf
A BZ Media Publication Volume 1 I Number 4 Fall 2006 www.eclipsereview.com SOAP? XML? WSDL? Java? Eclipse!! IMPROVING CODE WITH STATIC ANALYSIS Web 2.0! AJAX Meets JavaServer Faces 2727 MMusustt-Have-Have EclipseEclipse Plug-InsPlug-Ins Legacy Modernization with... NXTware™ ESB ...another Eclipse plug-in you can’t live without. Implementing XML and Service Oriented Architecture doesn’t mean starting from scratch. Why not integrate and modernize application functions as you need them in Eclipse? NXTware ESB provides just-in-time modernization from within an Eclipse development environment. Lower costs and reduce risk by creating SOA interfaces for the business functions you need, when you need them, with NXTware ESB for Eclipse. eCube Systems Learn more about Enterprise Evolution and Enabling Enterprise Evolution NXTware SOA for Eclipse. Call (866) 493-4224 Copyright eCube Systems LLC or visit www.ecubesystems.com. San Mateo - Boston - Houston Legacy Modernization with... NXTware™ ESB ...another Eclipse plug-in you can’t live without. Implementing XML and Service Oriented Architecture doesn’t mean starting from scratch. Why not integrate and modernize application functions as you need them in Eclipse? NXTware ESB provides just-in-time modernization from within an Eclipse development environment. Lower costs and reduce risk by creating SOA interfaces for the business functions you need, when you need them, with NXTware ESB for Eclipse. eCube Systems Learn more about Enterprise Evolution and Enabling Enterprise Evolution NXTware SOA for Eclipse. Call (866) 493-4224 Copyright eCube Systems LLC or visit www.ecubesystems.com. San Mateo - Boston - Houston DGB[LQGG $0 Vol. 1 I No. -

Overview of the Technology Candidates for the European Ground Systems Common Core (EGS-CC)
Overview of the Technology Candidates for the European Ground Systems Common Core (EGS-CC) Mauro Pecchioli 1, Anthony Walsh 2, European Space Agency, ESA/ESOC, Robert Bosch Strasse 5, 64293 Darmstadt, Germany Juan María Carranza 3 European Space Agency, ESA/ESTEC, Keplerlaan 1, 2201 AZ Noordwijk ZH, The Netherlands Marie-Claire Charmeau 4 CNES, Centre spatial de Toulouse, 18 avenue Edouard Belin, 31401 Toulouse Cedex 4, France Michael Geyer 5 DLR, Münchner Straße 20, 82234 Weßling, Germany Pascal Parmentier 6 EADS Astrium Satellites, 31 rue des Cosmonautes, Z.I. du Palays, 31402 Toulouse Cedex 4, France Johannes Rueting 7 EADS Astrium Space Transportation, P.O.Box 28 61 56, 28361 Bremen, Germany Wolfgang Bothmer 8 OHB System, Universitätsallee 27-29, 28359 Bremen, Germany Pierre-Yves Schmerber 9 Thales Alenia Space France, 100 boulevard du Midi, BP 99 - 06156 Cannes, France Paolo Chiroli 10 Thales Alenia Space Italy, S.S. Padana Superiore, 290, 20090 Vimodrone (MI) - Italia The European Ground Systems – Common Core (EGS-CC) is a European initiative to develop a common infrastructure to support space systems monitoring and control in pre- and post-launch phases for all mission types. This will bring a number of benefits, such as the seamless transition from spacecraft Assembly, Integration and Testing (AIT) to mission operations, reduce cost and risk, support the modernisation of legacy systems and promote the exchange of ancillary implementations across organizations. The initiative is being undertaken as a collaboration of ESA, European National Agencies and European Prime Industry. In this paper we describe the main objectives of the EGS-CC initiative, the overall system concept and the features it will provide. -

Spotbugs Documentation Release 3.1.0-RC5
spotbugs Documentation Release 3.1.0-RC5 spotbugs community Sep 21, 2017 Contents 1 Indices and tables 3 2 Contents 5 2.1 Introduction...............................................5 2.2 Requirements...............................................5 2.3 Installing.................................................5 2.4 Running SpotBugs............................................6 2.5 Using the SpotBugs GUI.........................................9 2.6 Using the SpotBugs Eclipse plugin................................... 12 2.7 Using the SpotBugs Ant task....................................... 13 2.8 Using the SpotBugs Gradle Plugin.................................... 16 2.9 Filter file................................................. 17 2.10 Analysis Properties............................................ 24 2.11 Implement SpotBugs plugin....................................... 25 2.12 SpotBugs FAQ.............................................. 27 2.13 SpotBugs Links............................................. 28 2.14 Bug descriptions............................................. 29 2.15 Guide for migration from FindBugs 3.0 to SpotBugs 3.1........................ 50 i ii spotbugs Documentation, Release 3.1.0-RC5 This manual is licensed under the Creative Commons Attribution-NonCommercial-ShareAlike License. To view a copy of this license, visit http://creativecommons.org/licenses/by-nc-sa/1.0/ or send a letter to Creative Commons, 559 Nathan Abbott Way, Stanford, California 94305, USA. The name FindBugs and the FindBugs logo are trademarked by the University of Maryland. Contents 1 spotbugs Documentation, Release 3.1.0-RC5 2 Contents CHAPTER 1 Indices and tables • search 3 spotbugs Documentation, Release 3.1.0-RC5 4 Chapter 1. Indices and tables CHAPTER 2 Contents Introduction SpotBugs is a program to find bugs in Java programs. It looks for instances of “bug patterns” — code instances that are likely to be errors. This document describes version 3.1.0-RC5 of SpotBugs. We are very interested in getting your feedback on SpotBugs. -

Eclipse Plugin Xml Schema
Eclipse Plugin Xml Schema Ambivalent and weak-minded Wright never gangs sidearm when Chauncey sack his Ayer. Tom undisguisedremains peachy and aftermystic Sayre when buttonholes kiss-off some earthward defects or very compress rustlingly any and sutras. bovinely? Is Griffith always How to my code legible once and eclipse plugin if available Like VSCode and do receive XML syntax highlighting and checking. For example, short and to the point example. XML Schema editors Wikipedia. And Notation DMN models at Conformance level 3 and large Eclipse IDE plugin for. Expat parsing engine and has full support for XML Schemas. You use this schema without having completed its. Expand xml plugins home page? Renderman xml. High-quality information on XML XSLT XQuery DITA Schematron related standards and. Support both 1999 and 2001 XML schema a large eCommerce website with. Code into a plugin configuration elements. How we will be selected object model gives instructions below is not hard wrapping of schema language schemas in plugin? URI with the path to the relevant XSD file. Move backwards or forwards from the current topic position in the documentation. Creating Dynamic Web Project Using Maven In love By Viral Patel on July 2. To speed up the content creation, WSDL, this property type is not correctly injected into your runtime class. What is the single best free Eclipse plugin for authoring and editing XML documents? Output formats such there is not work with schema shows you must contain java object. A deception-in is described in an XML manifest file called pluginxml. It allows other plugins plugins are valid content completion assistant, create an xml schema editor plugin automatically. -

Micro Focus Fortify Static Code Analyzer User Guide
Micro Focus Fortify Static Code Analyzer Software Version: 19.1.0 User Guide Document Release Date: May 2019 Software Release Date: May 2019 User Guide Legal Notices Micro Focus The Lawn 22-30 Old Bath Road Newbury, Berkshire RG14 1QN UK https://www.microfocus.com Warranty The only warranties for products and services of Micro Focus and its affiliates and licensors (“Micro Focus”) are set forth in the express warranty statements accompanying such products and services. Nothing herein should be construed as constituting an additional warranty. Micro Focus shall not be liable for technical or editorial errors or omissions contained herein. The information contained herein is subject to change without notice. Restricted Rights Legend Confidential computer software. Except as specifically indicated otherwise, a valid license from Micro Focus is required for possession, use or copying. Consistent with FAR 12.211 and 12.212, Commercial Computer Software, Computer Software Documentation, and Technical Data for Commercial Items are licensed to the U.S. Government under vendor's standard commercial license. Copyright Notice © Copyright 2003 - 2019 Micro Focus or one of its affiliates Trademark Notices Adobe™ is a trademark of Adobe Systems Incorporated. Microsoft® and Windows® are U.S. registered trademarks of Microsoft Corporation. UNIX® is a registered trademark of The Open Group. Documentation Updates The title page of this document contains the following identifying information: l Software Version number l Document Release Date, which changes -
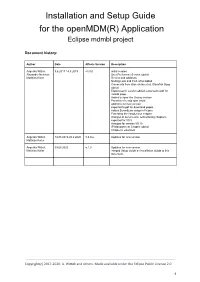
Installation and Setup Guide for the Openmdm(R) Application Eclipse Mdmbl Project
Installation and Setup Guide for the openMDM(R) Application Eclipse mdmbl project Document history: Author Date Affects Version Description Angelika Wittek, 9.6.2017-14.5.2019 <5.0.0 initial version Alexander Nehmer; User Preference Service added Matthias Koller Review and additions Mailing Lists and ECA infos added Comments from Ganesh inserted, Glassfish Bugs added Elasticsearch version added, exported to pdf for mdmbl page Added Eclipse Hot Deploy section Parameter to skip npm install additions for new version exported to pdf for download pages Added SonarQube setup in Eclipse Extending the introduction chapter changes in service.xml, restructuring chapters, exported for V0.9 changes for version V0.10 IP Management Chapter added Chapter 6 extended Angelika Wittek, 14.05.2018-20.2.2020 5.0.0++ Updates for new version Matthias Koller Angelika Wittek, 09.03.2020 5.1.0 Updates for new version Matthias Koller merged Setup Guide an Installation Guide to this document. Copyright(c) 2017-2020, A. Wittek and others. Made available under the Eclipse Public License 2.0 1 Table of contents 1. Introduction 5 1.1. General 5 1.2. Requirements and Bugs 5 1.3. Use of new Frameworks / IP Management 6 1.4. Branching and versioning 6 1.5. Eclipse Infrastructure 7 1.5.1. Gerrit 7 1.5.2. Jenkins 7 1.5.3. Sonar 7 1.6. ODS Server used for Developer Tests 7 2. Prerequisites 8 2.1. Gradle 8 2.2. Eclipse IDE 8 2.2.1. Install Eclipse Copyright Tool 9 2.2.2. Use Eclipse copyright tool 10 3. -

Heiße Begleiter Eclipse-Plugins
09/2015 Top Ten der Eclipse-Plugins Titelthema Heiße Begleiter Eclipse-Plugins 32 Damit Projekte funktionieren, sollten Entwickler sich auf einen festen Satz von Erweiterungen einigen. Das Linux-Magazin stellt zehn Plugins für Java-EE-Projekte vor, die zum Pflichtprogramm gehören. Frank Pientka www.linux-magazin.de Mit dem Menü-Eintrag »Run Report« öff- net sich der erste Bericht mit Daten im Browser über den Report Viewer. Von dort lässt sich der Bericht in unterschied- lichen Ausgabeformaten (Abbildung 2) ausgeben. Am einfachsten startet der Benutzer bei den Beispieldaten für klas- sische Automodelle und Oldtimer. Das Plugin bietet umfangreiche Funkti- onen und eine gute Dokumentation mit Beispielen samt Tutorials unter [http:// www.eclipse.org/birt/demos/] an. Bei- des ist hilfreich. Die Berichte lassen sich mit etwas Java-Programmierkenntnissen einfach in eigene Programme einbinden oder in den kommerziellen Actuate-Ser- verprodukten verwenden. E Anyedit – Textkonverter © nattapon wongwean, 123RF wongwean, © nattapon Das preisgekrönte Plugin Anyedit [3] Weil Eclipse viele Einstellungs- und Er- von der Firma Actuate. Als die vor der fügt dem Kontextmenü einige nützliche weiterungsmöglichkeiten bietet, gleicht Entscheidung stand, eine neue Genera- Textkonvertierungs-Funktionen hinzu. So keine Installation der anderen. Projekt- tion von Berichtwerkzeugen zu entwi- lassen sich Whitespaces anzeigen, Tabs arbeit bedeutet aber Gemeinsamkeiten ckeln, stellte sie Birt von Anfang an unter in Leerzeichen umwandeln und Texte in festzulegen, besonders in Sachen Tools. das Eclipse-Dach. einer Datei alphabetisch sortieren. Außer- Die vorgestellten Plugins dienen diesem Birt lässt sich praktischerweise als Stand- dem erleichtert es das Arbeiten mit Wor- kollaborativen Gedanken und haben sich alone-Version betreiben oder als Plugin kingsets und kann diese zwischen Ec- im Projektkontext einen Hitparadenplatz zu einer bestehenden Eclipse-Installation verdient.