Poster: IDE Plugins for Secure Coding
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Said GUERRAB
Said GUERRAB CONTACT 404-5100 Boulevard Pie IX E-mail: [email protected] H1X 2B6 Website: www.sguerrab-developper.com Montreal (QC) Phone: 438-935-8707 SUMMARY 05 years of experience designing and developing websites. Bilingual French-English. Implementation of numerous IT projects within the school. Design and implementation of websites in PHP, MySQL, JSP, HTML5, CSS3, Sass, Less, Stylus, and JavaScript, Bootstrap, D3.js, MVC framworks (PHP Laravel), Photoshop... Web project management (specifications, deadlines, risks management...). Audio editing, video editing, and graphic design. SEO for websites Autonomous, organized, have a team spirit, available, highly motivated, adaptable to new situations, can work under pressure. TECHNICAL Operating Systems: Windows, Linux , Mac OS X SKILLS Programming Languages: Java, JSP, Ruby, Cobol, VB.NET, C++, PHP, HTML/CSS, JavaScript Markup Languages:JSON, YAML, XML CSS Preprocessors: Sass CSS, Stylus CSS, Less CSS Editors & IDEs: Eclipse, PHPStorm, NetBeans, RubyMine, Sublime Text… Version Control Systems: GIT, Github, Bitbucket, SVN Frameworks & libraries: Laravel, JQuery, Bootstrap, D3.js... CMS: Drupal, Joomla, WordPress Server management: Apache, Tomcat, Glassfish, CPanel, DNS Database: Oracle SQL, PL/SQL, SQL Server, MySQL, Access. Office Applications:Excel, Word, Powerpoint and LibreOffice suite Other software: Microsoft Project, Microsoft Visio, Oracle Forms, Oracle Reports Graphism: Photoshop, The Gimp, Illustrator, Inkscape et InDesign. Maintening:Software (installation and updating). PROFESSIONAL Identify the needs of clients. SKILLS Analyze specifications of the website. Establish a site plan with the design of each page. Choosing tools for the development of the site . Coordinate the collection and the organization of information to include on the site. Collaborate in the definition of the architecture of the site and the choice of navigation scenarios. -
Overall Features Performance Price
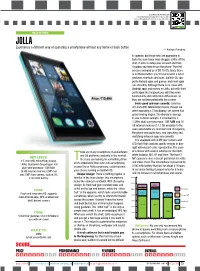
Scan this code for more info. To download a barcode app, SMS <f2k> to 56677 from a mobile phone with Internet access and camera. SMARTPHONE JOLLA Experience a different way of operating a smartphone without any home or back button — Ashok Pandey to operate, but those who are upgrading to taste the new flavor may struggle a little. At the start, it asks to setup your account and then, it guides you how to use the phone. The first screen reminded us of BB 10 OS. Since there is no Home button, you’ll have to learn a lot of gestures, shortcuts and cues. Sailfish OS sup- ports Android apps and games, and most apps run smoothly. Although there is no issue with Android apps and games on Jolla, but with third party apps like facebook you will find some functionality and notification differences, as Price: `15,490 they are not integrated with the system. Feels good and runs smooth: Jolla has 4.5-inch qHD (960x450p) display, though we were expecting a 720p display, yet screen has good viewing angles. The display is average to use in direct sunlight. It is backed by a 1.4GHz dual-core processor, 1GB RAM and 16 GB internal memory (13.7 GB available to the user) expandable via microSD card. Navigating the phone was quite easy, and launching and switching between apps was smooth. It is equipped with 8 MP rear camera with LED flash that captures quality images in day- light with decent color reproduction. The cam- here are many smartphone manufacturers era comes with several settings for the flash, and OS platforms available in the market. -

Avatud Lähtekoodiga Vahendite Kohandamine Microsoft Visual C++ Tarkvaralahenduste Kvaliteedi Analüüsiks Sonarqube Serveris
TALLINNA TEHNIKAÜLIKOOL Infotehnoloogia teaduskond Tarkvarateaduse instituut Anton Ašot Roolaid 980774IAPB AVATUD LÄHTEKOODIGA VAHENDITE KOHANDAMINE MICROSOFT VISUAL C++ TARKVARALAHENDUSTE KVALITEEDI ANALÜÜSIKS SONARQUBE SERVERIS Bakalaureusetöö Juhendaja: Juhan-Peep Ernits PhD Tallinn 2019 Autorideklaratsioon Kinnitan, et olen koostanud antud lõputöö iseseisvalt ning seda ei ole kellegi teise poolt varem kaitsmisele esitatud. Kõik töö koostamisel kasutatud teiste autorite tööd, olulised seisukohad, kirjandusallikatest ja mujalt pärinevad andmed on töös viidatud. Autor: Anton Ašot Roolaid 21.05.2019 2 Annotatsioon Käesolevas bakalaureusetöös uuritakse, kuidas on võimalik saavutada suure hulga C++ lähtekoodi kvaliteedi paranemist, kui ettevõttes kasutatakse arenduseks Microsoft Visual Studiot ning koodikaetuse ja staatilise analüüsi ülevaate saamiseks SonarQube serverit (Community Edition). Seejuures SonarSource'i poolt pakutava tasulise SonarCFamily for C/C++ analüsaatori (mille eelduseks on SonarQube serveri Developer Edition) asemel kasutatakse tasuta ja vaba alternatiivi: SonarQube C++ Community pluginat. Analüüsivahenditena eelistatakse avatud lähtekoodiga vabu tarkvaravahendeid. Valituks osutuvad koodi kaetuse analüüsi utiliit OpenCppCoverage ja staatilise analüüsi utiliit Cppcheck. Siiski selgub, et nende utiliitide töö korraldamiseks ja väljundi sobitamiseks SonarQube Scanneri vajadustega tuleb kirjutada paar skripti: üks PowerShellis ja teine Windowsi pakkfailina. Regulaarselt ajastatud analüüside käivitamist tagab QuickBuild, -
Fira Code: Monospaced Font with Programming Ligatures
Personal Open source Business Explore Pricing Blog Support This repository Sign in Sign up tonsky / FiraCode Watch 282 Star 9,014 Fork 255 Code Issues 74 Pull requests 1 Projects 0 Wiki Pulse Graphs Monospaced font with programming ligatures 145 commits 1 branch 15 releases 32 contributors OFL-1.1 master New pull request Find file Clone or download lf- committed with tonsky Add mintty to the ligatures-unsupported list (#284) Latest commit d7dbc2d 16 days ago distr Version 1.203 (added `__`, closes #120) a month ago showcases Version 1.203 (added `__`, closes #120) a month ago .gitignore - Removed `!!!` `???` `;;;` `&&&` `|||` `=~` (closes #167) `~~~` `%%%` 3 months ago FiraCode.glyphs Version 1.203 (added `__`, closes #120) a month ago LICENSE version 0.6 a year ago README.md Add mintty to the ligatures-unsupported list (#284) 16 days ago gen_calt.clj Removed `/**` `**/` and disabled ligatures for `/*/` `*/*` sequences … 2 months ago release.sh removed Retina weight from webfonts 3 months ago README.md Fira Code: monospaced font with programming ligatures Problem Programmers use a lot of symbols, often encoded with several characters. For the human brain, sequences like -> , <= or := are single logical tokens, even if they take two or three characters on the screen. Your eye spends a non-zero amount of energy to scan, parse and join multiple characters into a single logical one. Ideally, all programming languages should be designed with full-fledged Unicode symbols for operators, but that’s not the case yet. Solution Download v1.203 · How to install · News & updates Fira Code is an extension of the Fira Mono font containing a set of ligatures for common programming multi-character combinations. -

Using Findbugs in Anger
Making Static Analysis Part Of Your Build Process William Pugh Professor, Univ. of Maryland Visiting Scientist, Google Learn how to effectively use FindBugs on large software projects (100,000+ lines of code), and make effective use of the limited time you can schedule/afford for static analysis 2 Agenda FindBugs and static analysis Using FindBugs effectively Running FindBugs Scaling up FindBugs Historical Bug results 3 Static Analysis Analyzes your program without executing it Doesn’t depend on having good test cases • or even any test cases Doesn’t know what your software is supposed to do • Looks for violations of reasonable programming practices • Shouldn’t throw NPE • All statements should be reachable • Shouldn’t allow SQL injection Not a replacement for testing • Very good at finding problems on untested paths • But many defects can’t be found with static analysis 4 Common (Incorrect) Wisdom about Bugs and Static Analysis Programmers are smart Smart people don’t make dumb mistakes We have good techniques (e.g., unit testing, pair programming, code inspections) for finding bugs early I tried lint and it sucked: lots of warnings, few real issues So, bugs remaining in production code must be subtle, and finding them must require sophisticated static analysis techniques 5 Can You Find The Bug? if (listeners == null) listeners.remove(listener); JDK1.6.0, b105, sun.awt.x11.XMSelection • lines 243-244 6 Why Do Bugs Occur? Nobody is perfect Common types of errors: • Misunderstood language features, API methods • Typos (using wrong boolean -

Towards Our Development Environment
Euclid Consortium Towards our development environment 2012, Dec. 4th SDC meeting 1 Euclid External constraints Consortium ● CODEEN (Redmine and http://apceucliddev.in2p3.fr/jenkins/) ● Common tools – Python / C++ – Jira – Eclipse – Sonar – Subversion – Doxygen – Xunit – Goolge talk – Maven – Redmine – Nexus – Adobe Connect – Jenkins 2012, Dec. 4th SDC meeting 2 Euclid Language and architecture Consortium ● Language: Python (C, C++) ● Central svn repository (http://euclid.esac.esa.int/svn/EC/SGS/) ● IDE: Eclipse + PyDev ● Software architecture and packaging – Model the testbed, data trains and taker Gaia concepts – Separate the data handling and algorithmic programming – Data model, Framework, Algo (projects? Modules?) ● Study flexible solutions for – local development, testing and survey data analysis – integration into the IAL – distributing the software? 2012, Dec. 4th SDC meeting 3 Euclid Data model and data handling Consortium ● Data model: first version as XML schema on SVN – PyXB for automatic Python code generation ● Framework with data handling, loading data from – ASCII files : SciPy (loadtxt) – Database : SQLAlchemy ORM – FITS files : PyFits ● Panda : large table ● Pickle : object serialization 2012, Dec. 4th SDC meeting 4 Euclid Dependencies and building managementConsortium ● Nexus, Ivy and Ant used in Gaia ● Maven - Nexus is proposed, is it too Java oriented? – Difference between Ant and Maven? ● How can we used the Python “setup” files ● Hubert proposals – http://zero-install.sourceforge.net/ – http://www.cmake.org/ ● Solution for – local software development and usage – distribution 2012, Dec. 4th SDC meeting 5 Euclid Configuration, testing and doc Consortium ● Solution for handling configuration – model the Gaia XML based solution? (Java “properties” thread unsafe) – Python solution? Init? ● Testing set up and conventions – xUnit and PyUnit? ● Javadoc as an example (look up in Eclipse, automatic doc generation) – Doxygen 2012, Dec. -

Technologies We Use IT Project Management
SolDevelo Sp. z o.o. is a dynamic software development and information technology outsourcing company, focused on delivering high quality software and innovative solutions. Our approach is a unique mix of highly experienced development team, client-oriented service and passion for IT. This guarantees projects to be completed on time, with the superior quality and precisely the way client imagined it. IT Project Management Requirements Specification Architecture Implementation Detailed Design Testing Integration Validation Maintenance Technologies We Use Software development and Integration Ý Application Servers Languages Web Servers Glassfish, JBOSS, Geronimo Java/JEE, Python, C#/.NET Nginx, Apache HTTP Android, PHP, Objective-C, Swift, Ruby Frameworks Web Technologies Database Environments Hibernate, Datanucleus, J2EE, PHP, XML, JavaScript, Oracle, SQL, PL/SQL, MySQL, OSGi, Spring Integration, SOAP, WSDL, RichFaces, PostgreSQL, HSQLDB, CouchDB, Quartz, Spring Batch, jQuery, JSP, JSF, AJAX, (S)CSS, SQLite3, Hypersonic Android Designer, LESS, XHTML, ASP.NET, Robotium, JBoss Seam Node.js Mobile Technologies Servlet Containers Android, iOS Tomcat, Jetty Web Frameworks AngularJS, Django, Spring WebFlow, Bootstrap, Zend, Ə CMS ǡ Business Intelligence Symfony, Express, Ruby on Rails Drupal, Wordpress, Joomla! DHIS2, Tableau 01 Competence Map Tools we use IDE Wiki < Knowledge Sharing IntelliJ IDEA, Eclipse, Android Confluence, Assembla Wiki, Trac Studio, Xcode, PHPStorm Project Methodology Issue/Bug Tracking Agile/Scrum JIRA, Assembla, -

Rational Purifyplus for UNIX
Develop Fast, Reliable Code Rational PurifyPlus for UNIX Customers and end-users demand that your Automatically Pinpoint code works reliably and offers adequate execu- Hard-To-Find Bugs tion performance. But the reality of your deliv- Reliability problems, such as runtime errors and ery schedule often forces you to sacrifice relia- memory leaks in C/C++, can kill a software bility or performance – sometimes both. And company’s reputation. These errors are hard to without adequate time for testing, you may not find, hard to reproduce, and hardest of all, to even know these issues exist. So you reluctant- explain to customers who discover them. No ly deliver your code before it’s ready, knowing one intentionally relies on their customer as good and well that the integrity of your work their "final QA." But without adequate tools, this may be suspect. is the inevitable outcome. Even the best pro- Rational Software has a solution for ensuring grammers make mistakes in their coding. that your code is both fast and reliable. Rational PurifyPlus for UNIX automatically finds HIGHLIGHTS Rational® PurifyPlus for UNIX combines runtime these reliability errors in C/C++ code that can’t error detection, application performance profil- Automatically finds runtime be found in any other way. It finds the errors ing, and code coverage analysis into a single, errors in C/C++ code even before visible symptoms occur (such as a complete package. Together, these functions system crash or other spurious behavior). And help developers ensure the highest reliability Quickly isolates application it shows you exactly where the error originated, and performance of their software from the very performance bottlenecks regardless of how remote from the visible first release. -

The Kate Handbook
The Kate Handbook Anders Lund Seth Rothberg Dominik Haumann T.C. Hollingsworth The Kate Handbook 2 Contents 1 Introduction 10 2 The Fundamentals 11 2.1 Starting Kate . 11 2.1.1 From the Menu . 11 2.1.2 From the Command Line . 11 2.1.2.1 Command Line Options . 12 2.1.3 Drag and Drop . 13 2.2 Working with Kate . 13 2.2.1 Quick Start . 13 2.2.2 Shortcuts . 13 2.3 Working With the KateMDI . 14 2.3.1 Overview . 14 2.3.1.1 The Main Window . 14 2.3.2 The Editor area . 14 2.4 Using Sessions . 15 2.5 Getting Help . 15 2.5.1 With Kate . 15 2.5.2 With Your Text Files . 16 2.5.3 Articles on Kate . 16 3 Working with the Kate Editor 17 4 Working with Plugins 18 4.1 Kate Application Plugins . 18 4.2 External Tools . 19 4.2.1 Configuring External Tools . 19 4.2.2 Variable Expansion . 20 4.2.3 List of Default Tools . 22 4.3 Backtrace Browser Plugin . 25 4.3.1 Using the Backtrace Browser Plugin . 25 4.3.2 Configuration . 26 4.4 Build Plugin . 26 The Kate Handbook 4.4.1 Introduction . 26 4.4.2 Using the Build Plugin . 26 4.4.2.1 Target Settings tab . 27 4.4.2.2 Output tab . 28 4.4.3 Menu Structure . 28 4.4.4 Thanks and Acknowledgments . 28 4.5 Close Except/Like Plugin . 28 4.5.1 Introduction . 28 4.5.2 Using the Close Except/Like Plugin . -

Evaluating the Flexibility of the Java Sandbox
Evaluating the Flexibility of the Java Sandbox Zack Coker, Michael Maass, Tianyuan Ding, Claire Le Goues, and Joshua Sunshine Carnegie Mellon University {zfc,mmaass}@cs.cmu.edu, [email protected], {clegoues,sunshine}@cs.cmu.edu ABSTRACT should protect both the host application and machine from The ubiquitously-installed Java Runtime Environment (JRE) malicious behavior. In practice, these security mechanisms provides a complex, flexible set of mechanisms that support are problematically buggy such that Java malware is often the execution of untrusted code inside a secure sandbox. able to alter the sandbox's settings [4] to override security However, many recent exploits have successfully escaped the mechanisms. Such exploits take advantage of defects in either sandbox, allowing attackers to infect numerous Java hosts. the JRE itself or the application's sandbox configuration to We hypothesize that the Java security model affords devel- disable the security manager, the component of the sandbox opers more flexibility than they need or use in practice, and responsible for enforcing the security policy [5, 6, 7, 8]. thus its complexity compromises security without improving In this paper, we investigate this disconnect between theory practical functionality. We describe an empirical study of the and practice. We hypothesize that it results primarily from ways benign open-source Java applications use and interact unnecessary complexity and flexibility in the design and with the Java security manager. We found that developers engineering of Java's security mechanisms. For example, regularly misunderstand or misuse Java security mechanisms, applications are allowed to change the security manager at that benign programs do not use all of the vast flexibility runtime, whereas static-only configuration of the manager afforded by the Java security model, and that there are clear would be more secure. -

The Developer's Guide to Debugging
The Developer’s Guide to Debugging Thorsten Grotker¨ · Ulrich Holtmann Holger Keding · Markus Wloka The Developer’s Guide to Debugging 123 Thorsten Gr¨otker Ulrich Holtmann Holger Keding Markus Wloka Internet: http://www.debugging-guide.com Email: [email protected] ISBN: 978-1-4020-5539-3 e-ISBN: 978-1-4020-5540-9 Library of Congress Control Number: 2008929566 c 2008 Springer Science+Business Media B.V. No part of this work may be reproduced, stored in a retrieval system, or transmitted in any form or by any means, electronic, mechanical, photocopying, microfilming, recording or otherwise, without written permission from the Publisher, with the exception of any material supplied specifically for the purpose of being entered and executed on a computer system, for exclusive use by the purchaser of the work. Printed on acid-free paper 987654321 springer.com Foreword Of all activities in software development, debugging is probably the one that is hated most. It is guilt-ridden because a technical failure suggests personal fail- ure; because it points the finger at us showing us that we have been wrong. It is time-consuming because we have to rethink every single assumption, every single step from requirements to implementation. Its worst feature though may be that it is unpredictable: You never know how much time it will take you to fix a bug - and whether you’ll be able to fix it at all. Ask a developer for the worst moments in life, and many of them will be related to debugging. It may be 11pm, you’re still working on it, you are just stepping through the program, and that’s when your spouse calls you and asks you when you’ll finally, finally get home, and you try to end the call as soon as possible as you’re losing grip on the carefully memorized observations and deductions. -

Heapmon: a Low Overhead, Automatic, and Programmable Memory Bug Detector ∗
Appears in the Proceedings of the First IBM PAC2 Conference HeapMon: a Low Overhead, Automatic, and Programmable Memory Bug Detector ∗ Rithin Shetty, Mazen Kharbutli, Yan Solihin Milos Prvulovic Dept. of Electrical and Computer Engineering College of Computing North Carolina State University Georgia Institute of Technology frkshetty,mmkharbu,[email protected] [email protected] Abstract memory bug detection tool, improves debugging productiv- ity by a factor of ten, and saves $7,000 in development costs Detection of memory-related bugs is a very important aspect of the per programmer per year [10]. Memory bugs are not easy software development cycle, yet there are not many reliable and ef- to find via code inspection because a memory bug may in- ficient tools available for this purpose. Most of the tools and tech- volve several different code fragments which can even be in niques available have either a high performance overhead or require different files or modules. The compiler is also of little help a high degree of human intervention. This paper presents HeapMon, in finding heap-related memory bugs because it often fails to a novel hardware/software approach to detecting memory bugs, such fully disambiguate pointers [18]. As a result, detection and as reads from uninitialized or unallocated memory locations. This new identification of memory bugs must typically be done at run- approach does not require human intervention and has only minor stor- time [1, 2, 3, 4, 6, 7, 8, 9, 11, 13, 14, 18]. Unfortunately, the age and execution time overheads. effects of a memory bug may become apparent long after the HeapMon relies on a helper thread that runs on a separate processor bug has been triggered.