Iphone 5S Environmental Report
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Refer to the Next Page to Find Your Device Make and Model, and Which Device Tier Applies
T-Mobile® Deductible and Fee Schedule Basic Device Protection Summary of Program Fees Device Tier* 1 2 3 4 5 Monthly Charge per Device $6 $8 $11 $13 $14 Service Fees/Deductibles per Approved Claim by Incident Type** Hardware Service (mechanical breakdown) † $0 $0 $0 $0 $0 Accidental Damage $10 $49 $99 $149 $249 Loss/Theft $10 $49 $99 $149 $249 * If you switch your device to one that is classified in another tier, and as device depreciation adjustments are made, the monthly charge for your new tier will be reflected on your T-Mobile bill. ** Claim limits apply. Refer to coverage documents for details. When you receive a replacement device, you'll need to return your damaged/ malfunctioning device to avoid being charged an Unrecovered Equipment Fee (non-return fee) equal to the retail value of your claimed device (up to $150 for Tier 1; $350 for Tier 2; $600 for Tier 3; $800 for Tier 4; and $1,200 for Tier 5). † There is a $5 processing fee collected by T-Mobile when devices are exchanged through T-Mobile. Refer to the next page to find your device make and model, and which device tier applies. T-Mobile is a registered trademark of Deutsche Telekom AG. All marks associated with the devices listed herein are the property of their respective owners. CL03475B-1018 © 2018 Assurant, Inc. T-Mobile® Deductible and Fee Schedule Alcatel Tier BlackBerry Tier Huawei Tier 3T 8 9810, 9900 Comet 665 Q10 3 Sonic 4G 768 Z10 Summit 1 A30 Tap Aspire Priv 4 webConnect Evolve Fierce XL Fierce, Fierce 2, Fierce 4 1 Coolpad Tier myTouch 2 GO FLIP LINKZONE Catalyst -

Jay Chiat Award 2015
iPhone 5S ‘You Are More Powerful Than You Think’ The Jay Chiat Awards 2015 Summary The goal of ‘iPhone 5S : You’re More Powerful Than You Think’ campaign was to reframe the smartphone category conversation and communicate the iPhone difference to consumers in a way that went far deeper than tech-and-specs. In the 12 markets we advertised at that time (U.S., Canada, Australia, UK, France, Germany, Italy, Spain, Switzerland, China, Japan, Korea), iPhone was by far the most admired smartphone in market. However on the surface, to many smartphone shoppers, iPhone didn’t look that different from its less expensive competitors. But that didn’t mean they were better. In other words, none of these “facts” told the full story. However similar these features and specs might appear to consumers on paper, in reality they were often nowhere near iPhone’s level of performance. Our mission was clear: to use Apple’s cornerstone product to make consumers around the world feel the difference, and to eliminate all doubt around a very important question: Why iPhone? The answer ….. it actually laid in the behaviors of our core users. A Successful Launch “The new iPhone 5S is a delight. On September 20, 2013, Apple released it newest flagship smartphone, the iPhone 5S, Its hardware and software make it featuring a powerful new 64-bit processor, a significant upgrade to its camera, and a the best smartphone on the market.” revolutionary fingerprint recognition system called Touch ID. iPhone 5S and 5C sold over nine million units in the first three days, which sets a record for first weekend smartphone sales[1]. -

Hardware Recommendations Forward
Hardware Recommendations Forward This guide is an accumulation of hardware, which through our customers, EVS has had positive experiences with in the past. The intent of this guide is to help prospects and customers identify hardware that could be relevant and used in conjunction with mobe3™. EVS recommends the verification of current models as specs with the companies who sell these products. EVS does not sell, warranty or endorse any of these products. We defer to the manufacturers for support and warranty, if applicable, for any of the products listed herein. Summary For ease of your planning purposes, this document covers hardware recommendations to use with mobe3 Cloud, including iOS devices, scanners, mounts, printers and accessories. These devices are sold through 3rd party retailers and EVS receives no financial motivation from these resellers. 2 iOS Devices iOS devices must meet the following criteria to be compatible with mobe3 Cloud: § 64-bit chip architecture § Run on one of the current / -1 versions of iOS* *iOS version must be w/in one version of the current version available. For example, as of September 2019, iOS 13 is the latest version, so mobe3 will operate on iOS versions 12 and 13. iOS 12 is compatible with these devices iPhone iPad iPod • iPhone XR 12.9-inch iPad Pro (3rd gen) • iPod Touch (7th gen) • iPhone XS 12.9-inch iPad Pro (2nd gen) • iPod Touch (6th gen) • iPhone XS Max 12.9-inch iPad Pro (1st gen) • iPhone X iPad Pro (11-inch) • iPhone 8 iPad Pro (10.5-inch) • iPhone 8 Plus iPad Pro (9.7-inch) we don’t • iPhone 7 iPad Air (3rd gen) recommend • iPhone 7 Plus iPad Air 2 iPods due to • iPhone 6s iPad Air due to poor • iPhone 6s Plus iPad (6th gen) battery life & • iPhone 6 iPad (5th gen) • iPhone 6 Plus iPad mini (5th gen) usability • iPhone SE iPad mini 4 • iPhone 5s iPad mini 3 iPad mini 2 3 iOS Devices EVS recommends the most current -2 iOS devices to ensures our customers benefit long-term for the life of the device per the iOS support matrix. -

Größe, Gewicht Und Farbe Audiotechnologie Homepod
HomePod Space Grau Weiß Größe, Gewicht Abmessungen: und Farbe 172 mm hoch 142 mm breit Gewicht: 2,5 kg Farbe: Space Grau Weiß Audiotechnologie High-Excursion Tieftöner mit speziellem Verstärker Ring aus sieben horngeladenen Hochtönern, jeweils mit eigenem Verstärker Ring aus sechs Mikrofonen für Siri aus der Ferne Internes niederfrequentes Kalibrierungsmikrofon zur automatischen Basskorrektur Direktes und Umgebungs-Audio-Beamforming Transparente dynamische Verarbeitung auf Studioniveau Audioquellen Apple Music1 iTunes Musikeinkäufe iCloud Musikmediathek mit einem Apple Music oder iTunes Match Abonnement Beats 1 Live Radio Apple Podcasts Übertragung anderer Inhalte zum HomePod über AirPlay von iPhone, iPad, iPod touch, Apple TV und Mac Audioformate HE-AAC (V1), AAC (16 bis 320 kbit/s), Protected AAC (aus dem iTunes Store), MP3 (16 bis 320 kbit/s), MP3 VBR, Apple Lossless, AIFF, WAV und FLAC2 Touch Oberfläche + oder – tippen oder halten zur Lautstärkeregelung Berühren und halten für Siri Tippen zum Abspielen/Pausieren von Musik oder Siri Zweimal tippen zum Überspringen Dreimal tippen für vorherigen Titel Bedienungs hilfen Bedienungs hilfen helfen Menschen mit Behinderung, ihren HomePod optimal zu nutzen. Weitere Infos Funktionen: Touch Anpassungen Siri VoiceOver Home App und HomeKit Drahtlose 802.11ac WLAN mit MIMO Technologien Direkter Gastzugriff3 Bluetooth 5.0 System - iPhone 5s oder neuer, iPad Pro, iPad (5. Generation oder neuer), iPad Air oder neuer, iPad mini 2 voraussetzungen oder neuer und iPod touch (6. Generation) mit iOS 11.2.5 -
Iphone User Guide for Ios 7 Software Contents
iPhone User Guide For iOS 7 Software Contents 8 Chapter 1: iPhone at a Glance 8 iPhone overview 9 Accessories 10 Multi-Touch screen 10 Buttons 12 Status icons 14 Chapter 2: Getting Started 14 Install the SIM card 14 Set up and activate iPhone 15 Connect iPhone to your computer 15 Connect to Wi-Fi 16 Connect to the Internet 16 Set up mail and other accounts 16 Apple ID 17 Manage content on your iOS devices 17 iCloud 18 Sync with iTunes 19 Date and time 19 International settings 19 Your iPhone name 20 View this user guide on iPhone 21 Chapter 3: Basics 21 Use apps 23 Customize iPhone 25 Type text 27 Dictate 28 Voice Control 29 Search 29 Control Center 30 Alerts and Notification Center 31 Sounds and silence 31 Do Not Disturb 31 AirDrop, iCloud, and other ways to share 32 Transfer files 33 Personal Hotspot 33 AirPlay 34 AirPrint 34 Use an Apple headset 35 Bluetooth devices 35 Restrictions 2 36 Privacy 36 Security 38 Charge and monitor the battery 39 Travel with iPhone 40 Chapter 4: Siri 40 Make requests 41 Tell Siri about yourself 41 Make corrections 42 Siri settings 43 Chapter 5: Phone 43 Phone calls 46 Visual voicemail 47 Contacts 47 Call forwarding, call waiting, and caller ID 47 Ringtones and vibrations 47 International calls 48 Phone settings 49 Chapter 6: Mail 49 Write messages 50 Get a sneak peek 50 Finish a message later 50 See important messages 51 Attachments 52 Work with multiple messages 52 See and save addresses 53 Print messages 53 Mail settings 54 Chapter 7: Safari 54 Safari at a glance 54 Search 55 Browse 55 Bookmark 56 Share -

How to Unlock an Iphone for FREE with Unlocky Tool
How To Unlock an iPhone for FREE with Unlocky Tool Unlock any iPhone for free with Unlocky Tool in less than 3 minutes. With our iPhone unlocker you can generate free unlock codes for your Apple device without paying a dime. More on that, you will also get the step by step instructions to get rid of sim not supported on iPhone. iPhone unlocking is not as hard or expensive as you think. Not anymore. With our unlock code generator created by most experienced developers which worked for big companies like Apple, AT&T, and Samsung Mobile, you can generate a free iPhone unlock code within the next 3 minutes and the most important you don’t have to pay anything. NADA! CLICK HERE TO ACCESS THE GENERATOR Unlock iPhone Steps and Instructions The iPhone unlocking process is the easiest and sought unlocking solution which requires no technical knowledge, even a novice can perform the procedure. You have to complete some requested fields, such as submitting the IMEI and choosing the country and network provider. Then sit back and relax until Unlocky does his magic: calculating and generate your Apple unlock code. Let me explain you each step: Send the IMEI number Because our tool is working based on the cell phone’s IMEI, guess what? you have to send your International Mobile Equipment Identity (IMEI) number through the app. Please pay attention when writing the 15 digits number, as this number is necessary to perform the unlock. Are we done? Let’s move to the next step. Select Country and Network Once you complete the first step and your IMEI is connected with our database, you will be asked to select the country and network provider (carrier) which your phone is locked to. -
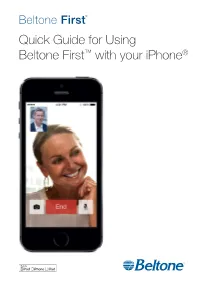
Quick Guide for Using Beltone First™ with Your Iphone® Quick Setup and Usage Guide for Made for Iphone (Mfi) Functionality
Beltone First™ Quick Guide for Using Beltone First™ with your iPhone® Quick setup and usage guide for Made for iPhone (MFi) functionality Hardware supported Beltone First™ supports MFi functionality with the following hardware from Apple. • iPhone® 5s • iPhone 5c • iPhone 5 • iPad® Air • iPad 4th generation • iPad mini with Retina display • iPad mini • iPod touch® 5th generation MFi hearing instruments require iOS 7.X or later versions. Pairing and connecting your Beltone First™ devices to your iPhone, iPad, or iPod touch Now you are ready to pair to your Beltone First hearing instruments. Pairing the hearing aids to a supported Apple device To start, make sure you have your Beltone First hearing instruments available with fresh batteries inserted. Do not close the battery doors at this point. 1. Turn on Bluetooth functionality on the Apple device if it is not already on. 2. Go to the Settings > General menu. Then select Accessibility in the General menu. 3. Power up Beltone First hearing instruments by closing the battery doors. 4. Select Hearing Aids in the Accessibility menu on the Apple device. 5. Once you enter the Hearing Aids screen, you will see the name of your hearing instruments appear along with the Beltone brand name and model number. 6. Tap on the center of the name of your hearing instruments on the screen. 2 7. Pairing requests will now appear asking if you would like to pair to your iPhone, iPad, or iPod touch. Press ”Pair” to begin the pairing process to your Beltone First hearing instruments. Note that for pairing to two hearing instruments, there will be two separate pairing requests. -

Magicpairing: Apple's Take on Securing Bluetooth Peripherals
MagicPairing: Apple’s Take on Securing Bluetooth Peripherals Dennis Heinze Jiska Classen Felix Rohrbach Secure Mobile Networking Lab Secure Mobile Networking Lab Cryptoplexity TU Darmstadt, Germany TU Darmstadt, Germany TU Darmstadt, Germany [email protected] [email protected] [email protected] ABSTRACT Most problems originated from the initial key negotiation and con- Device pairing in large Internet of Things (IoT) deployments is a nection setup. In Bluetooth, trust is established on first use by challenge for device manufacturers and users. Bluetooth offers a generating a permanent key. This permanent key protects device comparably smooth trust on first use pairing experience. Bluetooth, authenticity, message integrity, and message confidentiality [7, p. though, is well-known for security flaws in the pairing process. 269]. It is established individually between each pair of devices In this paper, we analyze how Apple improves the security of Blue- and only changes when a user manually deletes and reestablishes tooth pairing while still maintaining its usability and specification a pairing. In Classic Bluetooth, the permanent key is called Link compliance. The proprietary protocol that resides on top of Blue- Key (LK), while it is called Long Term Key (LTK) in Bluetooth Low tooth is called MagicPairing. It enables the user to pair a device Energy (BLE)—however, they can be converted into each other [7, once with Apple’s ecosystem and then seamlessly use it with all p. 280]. For the duration of each Bluetooth connection, a session their other Apple devices. key is derived from the permanent key. Thus, if a device is out of We analyze both, the security properties provided by this protocol, reach or switched off, this invalidates a session key. -
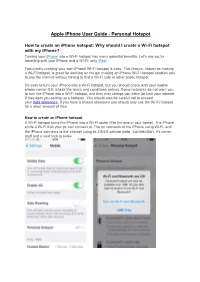
Apple Iphone User Guide - Personal Hotspot
Apple iPhone User Guide - Personal Hotspot How to create an iPhone hotspot: Why should I create a Wi-Fi hotspot with my iPhone? Turning your iPhone into a Wi-Fi hotspot has many potential benefits. Let's say you're travelling with your iPhone and a WI-Fi- only iPad. Fortunately creating your own iPhone Wi-Fi hotspot is easy. This feature, known as making a Wi-Fi hotspot, is great for working on the go: making an iPhone Wi-Fi hotspot enables you to use the internet without having to find a Wi-Fi cafe or other public hotspot. It's easy to turn your iPhone into a Wi-Fi hotspot, but you should check with your mobile phone carrier first (check the terms and conditions online). Some networks do not want you to turn the iPhone into a Wi-Fi hotspot, and they may charge you extra (or limit your internet if they spot you setting up a hotspot). You should also be careful not to exceed your data allowance. If you have a limited allowance you should only use the Wi-Fi hotspot for a short amount of time. How to create an iPhone hotspot A Wi-Fi hotspot turns the iPhone into a Wi-Fi router (like the one in your home). The iPhone emits a Wi-Fi that your pc can connect to. The pc connects to the iPhone using Wi-Fi, and the iPhone connects to the internet using its 3G/4G cellular data, connection. It's clever stuff and a neat trick to know. -
Iphone User Guide for Ios 8.1 Software Contents
iPhone User Guide For iOS 8.1 Software Contents 8 Chapter 1: iPhone at a Glance 8 iPhone overview 9 Accessories 10 Multi-Touch screen 10 Buttons 12 Status icons 13 SIM card 14 Chapter 2: Getting Started 14 Set up and activate iPhone 15 Connect iPhone to your computer 15 Connect to Wi-Fi 16 Connect to the Internet 16 Apple ID 16 Set up other mail, contacts, and calendar accounts 16 iCloud 18 Manage content on your iOS devices 18 Sync with iTunes 19 Date and time 19 International settings 20 Your iPhone name 20 View this user guide on iPhone 20 Tips for using iOS 8 21 Chapter 3: Basics 21 Use apps 24 Continuity 26 Customize iPhone 28 Type text 30 Dictate 31 Voice Control 32 Search 33 Control Center 33 34 Sounds and silence 34 Do Not Disturb 35 Sharing 37 iCloud Drive 38 38 Personal Hotspot 39 AirPlay 39 AirPrint 2 39 Use an Apple headset 40 Bluetooth devices 41 Restrictions 41 Privacy 42 Security 44 Charge and monitor the battery 45 Travel with iPhone 46 Chapter 4: Siri 46 Make requests 47 Tell Siri about yourself 47 Make corrections 47 Siri settings 48 Chapter 5: Phone 48 Phone calls 52 Visual voicemail 52 Contacts 53 Call forwarding, call waiting, and caller ID 53 Ringtones and vibrations 53 International calls 54 Phone settings 55 Chapter 6: Mail 55 Write messages 56 Get a sneak peek 56 Finish a message later 57 See important messages 57 Attachments 58 Work with multiple messages 58 See and save addresses 58 Print messages 59 Mail settings 60 Chapter 7: Safari 60 Safari at a glance 60 Search the web 61 Browse the web 62 Keep bookmarks -

Apple US Education Price List
US Education Institution – Hardware and Software Price List September 15, 2020 For More Information: Please refer to the online Apple Store for Education Institutions: www.apple.com/education/pricelists or call 1-800-800-2775. Pricing Price Part Number Description Date iMac MHK03LL/A iMac 21.5"/2.3GHz dual-core 7th-gen Intel Core i5/8GB/256GB SSD/Intel Iris Plus Graphics 640 w/Apple Magic Keyboard, Apple Magic Mouse 2 8/4/20 1,049.00 MHK23LL/A iMac 21.5" 4K/3.6GHz quad-core 8th-gen Intel Core i3/8GB/256GB SSD/Radeon Pro 555X w/Apple Magic Keyboard and Apple Magic Mouse 2 8/4/20 1,249.00 MHK33LL/A iMac 21.5" 4K/3.0GHz 6-core 8th-gen Intel Core i5/8GB/256GB SSD/Radeon Pro 560X w/Apple Magic Keyboard and Apple Magic Mouse 2 8/4/20 1,399.00 MXWT2LL/A iMac 27" 5K/3.1GHz 6-core 10th-gen Intel Core i5/8GB/256GB SSD/Radeon Pro 5300 w/Apple Magic Keyboard and Apple Magic Mouse 2 8/4/20 1,699.00 MXWU2LL/A iMac 27" 5K/3.3GHz 6-core 10th-gen Intel Core i5/8GB/512GB SSD/Radeon Pro 5300 w/Apple Magic Keyboard & Apple Magic Mouse 2 8/4/20 1,899.00 MXWV2LL/A iMac 27" 5K/3.8GHz 8-core 10th-gen Intel Core i7/8GB/512GB SSD/Radeon Pro 5500 XT w/Apple Magic Keyboard & Apple Magic Mouse 2 8/4/20 2,099.00 BR332LL/A BNDL iMac 21.5"/2.3GHz dual-core 7th-generation Core i5/8GB/256GB SSD/Intel IPG 640 with 3-year AppleCare+ for Schools 8/4/20 1,168.00 BR342LL/A BNDL iMac 21.5"/2.3GHz dual-core 7th-generation Core i5/8GB/256GB SSD/Intel IPG 640 with 4-year AppleCare+ for Schools 8/4/20 1,218.00 BR3G2LL/A BNDL iMac 21.5" 4K/3.6GHz quad-core 8th-gen Intel Core i3/8GB/256GB -

2.17.15 Hied K12 3PP Price List
Apple Inc. K-12 and Higher Education Institution US Only Third-Party Products: Software Licensing and Hardware Price List February 17, 2015 Table Of Contents Page • How to Order 1 • Revisions to the Price List 1-3 SECTION A: THIRD-PARTY HARDWARE 5-23 • Bags & Cases 5-7 • Cables 7-8 • Carts, Mounts & Stands 8-10 • Digital Cameras 10 • Headphones 10-11 15-16 • Input Devices 11-12 • iPad Accessories 12-13 • iPad Cases 13-15 • iPhone/iPod Accessories 15-16 • iPhone Cases 16-18 • iPod Cases 18 • Music Creation 18-19 • Networking 19 • Printers 19 • Printer Supplies Note: Printer supplies are no longer offered through Apple 19 • Projectors & Presentation 19 • Scanners 19 • Security & More 19-20 • Server Accessories 20-21 • Speakers & Audio 21-22 • Storage 22-23 • Video Cameras & Devices - Graphic Cards 23 SECTION B: THIRD-PARTY SOFTWARE LICENSING 23-30 • Creativity & Productivity Tools 23 • IT Infrastructure & Learning Services 23-30 SECTION C: FOR MORE INFORMATION 30 • Apple Store for Education 30 • Third-Party Websites 30 • Third-Party Sales Policies 30 • Third-Party Products and Ship-Complete Orders 30 HOW TO ORDER Many of the products on this price list are available to order online from the Apple Store for Education: www.apple.com/education/store or 800-800-2775 Purchase orders for all products may be submitted to: Apple Inc. Attn: Apple Education Sales Support 12545 Riata Vista Circle Mail Stop: 198-3ED Austin, TX 78727-6524 Phone: 1-800-800-2775 Fax: (800) 590-0063 IMPORTANT INFORMATION REGARDING ORDERING THIRD PARTY SOFTWARE LICENSING Contact Information: End-user (or, tech coordinator) contact information is required in order to fulfill orders for third party software licensing.