(IQ): Asia- Pacific Network Firewall Vendors, 2014 Table of Contents
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Annual Report 2011
Table of Contents 004 (I)Important Notes 005 (II)Company Profile 007 (III)Financial and Operating Highlights 010 (IV)Changes in Equity and Shareholders 017 (V)Directors, Supervisors and Senior Management 026 (VI)Corporate Governance 034 (VII)Shareholders’Meeting 035 (VIII)Reports of the Board of Directors 061 (IX)Reports of the Board of Supervisors 063 (X)Important issues 075 (XI)Financial Report 203 (XII)Documents Available For Inspection Neusoft Corporation Annual Report 2011 The year 2011 saw the 20th anniversary of Neusoft, a milestone year for us. Focusing on business model innovation, global strategy and operational excellence, we have mapped out future development strategies to build up necessary power and capacities for a sustainable growth. In the aspect of business model innovation, we have been devoted to building a company driven by innovation and service through leveraging our competitiveness and com- petence. In the aspect of global strategy, we have combined all business lines in and outside China, making all products and services available in both local and international markets. In the aspect of operational excellence, we have made some reforms covering organization, technology, culture, leadership and human resources to ensure that Neusoft operates at in- creasingly high efficiency levels. However, the past years were merely a start for our future adventure at Neusoft. We need more entrepreneurial employees to stand out and continue our growth with passion and wisdom. In the coming years, Neusoft will strive to maintain -
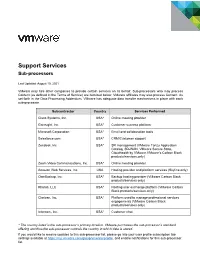
Support Services Sub-Processors
Support Services Sub-processors Last Updated: August 10, 2021 VMware may hire other companies to provide certain services on its behalf. Sub-processors who may process Content (as defined in the Terms of Service) are itemized below. VMware affiliates may also process Content. As set forth in the Data Processing Addendum, VMware has adequate data transfer mechanisms in place with each sub-processor. Subcontractor Country Services Performed Cisco Systems, Inc. USA* Online meeting provider Gainsight, Inc. USA* Customer success platform Microsoft Corporation USA* Email and collaboration tools Salesforce.com USA* CRM/Customer support Zendesk, Inc USA* SR management (VMware Tanzu Application Catalog, SD-WAN, VMware Secure State, Cloudhealth by VMware,VMware’s Carbon Black products/services, only) Zoom Video Communications, Inc. USA* Online meeting provider Amazon Web Services, Inc. USA Hosting provider and platform services (Skyline only) OwnBackup, Inc. USA* Backup hosting provider (VMware Carbon Black products/services only) Khoros, LLC USA* Hosting user exchange platform (VMware Carbon Black products/services only) Clarizen, Inc. USA* Platform used to manage professional services engagements (VMware Carbon Black products/services only) Intercom, Inc. USA* Customer chat * The country listed is the sub-processor’s primary location. VMware purchases the sub-processor’s standard offering and thus the sub-processor controls the country in which data is stored. If you would like to receive updates to this sub-processor list, please go into your user profile subscription tab settings available at https://my.vmware.com/group/vmware/profile, and enable notifications for this sub-processor list. Sub-processors who provide contract staff The following sub-processors provide contract staff that work in close coordination with VMware staff to help provide the support services to VMware customers and in the course of doing so may be exposed to Your Content/Support Request Content (including personal data contained therein). -
China Computer Software Industry Report, 2014-2017
China Computer Software Industry Report, 2014-2017 Apr. 2014 STUDY GOAL AND OBJECTIVES METHODOLOGY This report provides the industry executives with strategically significant Both primary and secondary research methodologies were used competitor information, analysis, insight and projection on the in preparing this study. Initially, a comprehensive and exhaustive competitive pattern and key companies in the industry, crucial to the search of the literature on this industry was conducted. These development and implementation of effective business, marketing and sources included related books and journals, trade literature, R&D programs. marketing literature, other product/promotional literature, annual reports, security analyst reports, and other publications. REPORT OBJECTIVES Subsequently, telephone interviews or email correspondence To establish a comprehensive, factual, annually updated and cost- was conducted with marketing executives etc. Other sources effective information base on market size, competition patterns, included related magazines, academics, and consulting market segments, goals and strategies of the leading players in the companies. market, reviews and forecasts. To assist potential market entrants in evaluating prospective INFORMATION SOURCES acquisition and joint venture candidates. The primary information sources include Company Reports, To complement the organizations’ internal competitor information and National Bureau of Statistics of China etc. gathering efforts with strategic analysis, data interpretation -
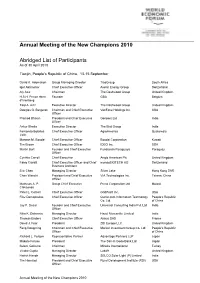
Annual Meeting of the New Champions 2010 Abridged List Of
Annual Meeting of the New Champions 2010 Abridged List of Participants As of 30 April 2010 Tianjin, People's Republic of China, 13-15 September David K. Adomakoh Group Managing Director TisoGroup South Africa Igor Akhmerov Chief Executive Officer Avelar Energy Group Switzerland Aly Aziz Chairman The Dashwood Group United Kingdom H.S.H. Prince Henri Founder GBA Belgium d'Arenberg Taqi A. Aziz Executive Director The Dashwood Group United Kingdom Douglas G. Bergeron Chairman and Chief Executive VeriFone Holdings Inc. USA Officer Pramod Bhasin President and Chief Executive Genpact Ltd India Officer Ankur Bhatia Executive Director The Bird Group India Fernando Bolaños Chief Executive Officer AgroAmerica Guatemala Valle Marwan M. Boodai Chief Executive Officer Boodai Corporation Kuwait Tim Brown Chief Executive Officer IDEO Inc. USA Martin Burt Founder and Chief Executive Fundación Paraguaya Paraguay Officer Cynthia Carroll Chief Executive Anglo American Plc United Kingdom Fabio Cavalli Chief Executive Officer and Chief mondoBIOTECH AG Switzerland Business Architect Eric Chen Managing Director Silver Lake Hong Kong SAR Chen Wenchi President and Chief Executive VIA Technologies Inc. Taiwan, China Officer Mathews A. P. Group Chief Executive Press Corporation Ltd Malawi Chikaonda Peter L. Corsell Chief Executive Officer GridPoint Inc. USA Fritz Demopoulos Chief Executive Officer Qunar.com Information Technology People's Republic Co. Ltd. of China Jay P. Desai Founder and Chief Executive Universal Consulting India Pvt. Ltd India Officer Nitin K. Didwania Managing Director Hazel Mercantile Limited India Thomas Enders Chief Executive Officer Airbus SAS France David J. Fear President ZBI Europe LLC United Kingdom Feng Dongming Chairman and Chief Executive Markor Investment Group Co. -

Annual Report 2013
Important Notes 4 (Ⅰ) Definitions and Significant Risk Warning 5 (Ⅱ) Company Profile 6 (Ⅲ) Accounting Data and Financial Indicators 9 (IV) Report of the Board of Directors 12 (V) Important Issues 43 (VI) Changes in Equity and Shareholders 53 (VII) Directors, supervisors and Senior management 59 (VIII) Corporate Governance 69 (IX) Internal Control 74 (X) Financial Report 75 (XI) Documents Available for Inspection 203 Neusoft Annual Report 2013 Dr. Liu Jiren Chairman Neusoft Corporation The world is changing faster than ever before. An increasing number of new policies, transformative technologies and new trend are constantly catalyzing innovative business models, emerging markets and new demands in recent years. With that big picture in mind, Neusoft has always been focusing on innovation and globalization. We encourage in- novation at all levels of our operations to drive transformation for better. Specifically, we have built a robust growth model driven by knowledge assets. These efforts have helped us not only overcome many challenges and ward off potential risks, but also build our new competitive advantages. Today, new technologies such as mobile Internet, cloud computing, big data and social media are overthrowing tra- ditional business models with new IT products/services and business patterns springing up. This stimulated new mar- ket demands and gradually broke industry barriers, and what followed by are increasingly growing cross-industry competition and cooperation. Over the past twenty-plus years, Neusoft has achieved a great-leap-forward growth through incremental innovation and transformation. In the future, we will integrate innovation into a daily routine, reengineering and strengthening our business capabilities through collaboration. -

NEUSOFT XIKANG HOLDINGS INC. 東軟熙康控股有限公司 (Incorporated in the Cayman Islands with Limited Liability)
The Stock Exchange of Hong Kong Limited and the Securities and Futures Commission take no responsibility for the contents of this Application Proof, make no representation as to its accuracy or completeness and expressly disclaim any liability whatsoever for any loss howsoever arising from or in reliance upon the whole or any part of the contents of this Application Proof. Application Proof of NEUSOFT XIKANG HOLDINGS INC. 東軟熙康控股有限公司 (Incorporated in the Cayman Islands with limited liability) WARNING The publication of this Application Proof is required by The Stock Exchange of Hong Kong Limited (the “Stock Exchange”) and the Securities and Futures Commission (the “Commission”) solely for the purpose of providing information to the public in Hong Kong. This Application Proof is in draft form. The information contained in it is incomplete and is subject to change which can be material. By viewing this document, you acknowledge, accept and agree with NEUSOFT XIKANG HOLDINGS INC. (the “Company”), its joint sponsors, advisors or members of the underwriting syndicate that: (a) this document is only for the purpose of providing information about the Company to the public in Hong Kong and not for any other purposes. No investment decision should be based on the information contained in this document; (b) the publication of this document or any supplemental, revised or replacement pages on the Stock Exchange’s website does not give rise to any obligation of the Company, its joint sponsors, advisors or members of the underwriting syndicate to proceed -
The Trend of Cloud Computing in China Chunmei Chi, Feng Gao School of Computer Engineering, Qingdaotechnological University, Qingdao, China E-Mail: [email protected]
1230 JOURNAL OF SOFTWARE, VOL. 6, NO. 7, JULY 2011 The Trend of Cloud Computing in China Chunmei Chi, Feng Gao School of Computer Engineering, QingdaoTechnological University, Qingdao, China E-mail: [email protected] Abstract—With the rapid development of internet, cloud growth of internet users. ( see fig 1). computing rapidly becomes the next round of growth wave in IT industry. In this paper, we introduce some recent trends in the cloud computing in China. We analyze the 10 thousand policy, the related companies, the advantages of this sector, the services and also some technological problems existed in this area. Index Terms—cloud computing, trends, IaaS, service I. WHAT IS CLOUD COMPUTING Cloud computing is a super internet based computing model in which tens of thousands of computers and servers are connected into a computer cloud. Therefore, the users can get access to the data centers through their Internet users Ratio of netizens computers, laptops, cell phones, etc. Cloud computing Fig 1 allows you to experience more than 10 trillion times per Cloud computing makes breakthrough with the rapid second computing capacity; the computers in the clouds growth of things internet. It tops Gartner’s list of 10 will significantly change the current computer model. strategic technologies in 2010 and will become the Cloud computing comes into focus only when you think mainstream technology in the coming two to five years. about what IT always needs: a way to increase capacity Things internet breaks the boundaries of interpersonal or add capabilities on the fly without investing in new communication and has been recognized as the general infrastructure, training new personnel, or licensing new direction of the industrial development. -

Tohoku Economics Research Group
Discussion Paper No.293 The Formation of the Software and Information Services Industry in Dalian, China Yan Zhang and Nozomu Kawabata April 2013 TOHOKU ECONOMICS RESEARCH GROUP GRADUATE SCHOOL OF ECONOMICS AND MANAGEMENT TOHOKU UNIVERSITY 27-1 KAWAUCHI, AOBA-KU, SENDAI, 980-8576 JAPAN 2 The Formation of the Software and Information Services Industry in Dalian, China Yan Zhang (Fujitsu Research Institute) Nozomu Kawabata (Tohoku University) 1. Introduction (1) The Purpose of This Study The purpose of this paper is to elucidate the factors leading to the formation of the software and information services industry in the city of Dalian, China. Studies on information services industries around the world acknowledge India as a center for offshore development and service outsourcing. In contrast, China’s information services industry has a higher ratio of software product development targeting domestic markets (Gregory et al., 2009, Chapter 4). Dalian, however, has prospered as a hub for development and services aimed at Japanese market. While the sales volume and value of exports for the software and information services industry in Dalian were over 200 million yuan and several million dollars, respectively, in 1998, the figures exceeded 40.27 billion yuan and 1.4 billion dollars, respectively, in 2009. The export ratio is 23.8% based on the conversion to the U.S. dollar using each year’s foreign exchange rate. This is significantly higher than the 13.2% export ratio of the entire Chinese software and information services industry (Figure 1). In addition, 90.9% of Dalian’s exports are directed to Japan (Dalian Economic and Information Technology Committee et al., 2009), a percentage considerably greater than that for all of China, which is approximately 60% (Department of Software and Services Industry, Ministry of Industry and Information Technology of the People’s Republic of China, et al., 2010). -

Table of Contents
Table of Contents Greetings from Founder, General Chair and Program Chair ........ 1 Vision, Mission, & Actions of UV Program @ MIT ITRC ............... 4 Open invitation letter ...................................................................... 5 Program at a glance ...................................................................... 7 Program with paper titles ............................................................... 8 Logistics ....................................................................................... 11 Paper abstracts ............................................................................ 12 Committees .................................................................................. 28 Organizers, collaborators, sponsors & media.............................. 30 Information from Sponsors & Media ............................................ 31 Conference information in Chinese ............................................. 34 Greetings from Founder, General Chair and Program Chair From Founder, Dr. Ichiro Masaki: Welcome to the First Universal Village Conference. I am the founder of the conference. My name is Ichiro Masaki. I am the Director of the Intelligent Transportation Research Center at MIT (Massachusetts Institute of Technology). Universal Village (UV) is a desired future society which provides their residents with sustainable happiness. In order to develop UV, we take a top-down or, in other words, system-oriented approach instead of a bottom-up or element-oriented approach. In the development process, -

Connecting Sichuan
Connecting Sichuan A landmark partnership to revitalize communities by transforming healthcare, education, and the workforce Rebuilding Better, Together The people of Sichuan suffered great losses when a Social Impact at a Glance massive earthquake devastated their province in May 2008. In addition to significant loss of life, the earthquake Indicator Description Metric as of June 2011 destroyed many schools and hospitals located in rural, Community Counties within Sichuan 8 out of 10 of the hardest hard to reach areas. Cisco, the Cisco Foundation, and our investment benefiting from the program hit counties employees immediately responded by donating more Economic Program social investment US$50 million than US$2.6 million (about RMB 16.8 million) in grants and investment relief funds. But a longer-term response was needed to Building capacity Commercial, NGO, and 40 partners* restore and revitalize the region. Cisco and the Chinese through partners government partners contributing to the program government saw an opportunity for renewal in the midst of the Sichuan destruction—an opportunity to rebuild better, 21st century ICT Number of network-enabled 193 infrastructure healthcare and education together. institutions That vision for a better future resulted in the creation of 21st century skills Investment in professional +9,900 healthcare and development development and ICT skills education professionals a unique public-private partnership, a three-year Cisco trained corporate social responsibility program called Connecting Sichuan. * Excludes healthcare organizations and educational institutions Connecting Sichuan was designed to systematically transform healthcare, education, and the workforce About Sichuan in the province through the use of information and Long known as China’s Province of Abundance, communications technology (ICT). -

The 2009 Global Outsourcing Outsourcing 100™ Service Providers and and the World’S Best Advisors Outsourcing Advisors
The International 2009 Association of Outsourcing ™ Professionals™ (IAOP™) is pleased to announce the companies selected The World’s BEST as The 2009 Global Outsourcing Outsourcing 100™ Service Providers and and the World’s Best Advisors Outsourcing Advisors. 2009 World’s Best Outsourcing Advisors The global, standard-setting organization and advocate for the outsourcing profession. To learn more visit: www.outsourcingprofessional.org 2009 ™ The 2009 Global Outsourcing 100 Plus Report Abstract Please visit www.outsourcingprofessional.org to purchase a complete version of The 2009 Global Outsourcing 100 Plus Report. © 2009 International Association of Outsourcing Professionals™ (IAOP™) All Rights Reserved 2600 South Road, Suite 44-240 Poughkeepsie, NY 12601 +1.845.452.0600 www.outsourcingprofessional.org International Association of Outsourcing Professionals, IAOP, The Global Outsourcing 100 and Certified Outsourcing Professionals are all registered trademarks Table of Contents The Global Outsourcing 100 Industry Analysis ..................................................................................................Section A Introduction ..............................................................................................................................................................................A1-A2 Leaders Overview ..........................................................................................................................................................................A3 Rising Stars Overview ...................................................................................................................................................................A4 -

2017 Selection Order Date
RSNA 2017 Space Selection Appointment Schedule as of November 9, 2017 COMPANY NAME DAY TIME 20/20 Imaging - A Konica Minolta Company Wednesday, November 30, 2016 9:00 AM 3D Systems Monday, November 28, 2016 9:50 AM 4th World Congress of Thoracic Imaging Wednesday, November 30, 2016 11:15 AM AADCO Medical, Inc Monday, November 28, 2016 11:05 AM AbyzR Co Ltd Wednesday, November 30, 2016 12:05 PM Accusoft Monday, November 28, 2016 3:30 PM Active Ideas Wednesday, November 30, 2016 3:15 PM ACUMYN Inc Wednesday, November 30, 2016 11:15 AM Adako USA Wednesday, November 30, 2016 3:15 PM ADANI Systems Inc Tuesday, November 29, 2016 1:40 PM Adaptix Ltd Wednesday, November 30, 2016 12:00 PM Advanced Accelerator Applications Wednesday, November 30, 2016 11:20 AM Advanced Data Systems Tuesday, November 29, 2016 11:10 AM Advanced Mobility By Kentucky Trailer Tuesday, November 29, 2016 11:40 AM Aegys LLC Wednesday, November 30, 2016 2:25 PM Aerosino Wednesday, November 30, 2016 11:20 AM AFC Industries, Inc Monday, November 28, 2016 3:35 PM Affiliated Professional Services Inc Tuesday, November 29, 2016 1:40 PM Agfa HealthCare Monday, November 28, 2016 9:00 AM AGITO Medical Tuesday, November 29, 2016 3:00 PM All Pro Solutions, Inc. Wednesday, November 30, 2016 3:20 PM Allengers Medical Systems Ltd Wednesday, November 30, 2016 10:25 AM Allied Powers LLC Wednesday, November 30, 2016 1:35 PM Alltech Medical Systems America Inc Tuesday, November 29, 2016 3:15 PM Alpha Tau Medical LTD.