Microsoft 365 Security Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Introduction to Microsoft Publisher
Introduction to Microsoft Publisher Class Description This is an introduction to Microsoft Publisher, with a focus on choosing a template and modifying it to meet your needs. Class Length One and one‐half (1½) hours Introduction Microsoft Publisher is an entry‐level desktop publishing program (the big two used by professional graphic artists are Adobe’s InDesign and Quark’s QuarkXPress) targeted towards small businesses and organizations lacking a professional page designer. It can produce brochures, newsletters, menus, postcards, and more and prepare these documents for self‐printing or sending to a commercial printer. Although much of what Microsoft Publisher does can be done in Microsoft Word, it has more emphasis on page layout and page design whereas Microsoft Word has more emphasis on text composition and proofing. Knowledge of Microsoft Word is a great benefit to learning Microsoft Publisher. Objectives Learn how to create a new document from a template Become familiar with the various ribbons Learn how to change Color Schemes and Font Schemes Learn how to format text Learn how to change a picture Learn how to use Master Pages Learn how to create a publication from a blank page Understand how to insert various types of objects into a publication This manual is a handout for you to keep. Please feel free to use it for taking notes. 1 * Creating Your First Publisher Document By default, Microsoft Publisher opens to the New template gallery. If you are connected to the Internet, Microsoft Publisher will, by default, open to the New template gallery with the ‘Featured’ templates dis‐ played. -

Information on Microsoft Office 365 for Students
Information on Microsoft Office 365 for Students We inform you that according to the decision of the Management of Károli Gáspár University of the Reformed Church the Microsoft Office 365 has become available for our students from 3 April 2020. As part of this, the students get a university e-mail address, 1 TB OneDrive storage and opportunity to download the Office programme package to five computers and five mobile devices free of charge. The main components of Office 365 University e-mail address As part of the service our students get a university e-mail address composed of their educational ID number and @cloud.kre.hu. First and further login is possible on the webpage http://portal.office.com 1 TB OneDrive Storage Access to OneDrive of 1 TB is also available for the students thus they can organise their notes and other study materials in one place, in transparent way. These materials can be easily accessed and shared with each other anywhere, anytime from the cloud. The OneDrive is available on http://portal.office.com. Office Programme package The latest version of the Office programme package can be downloaded free or used online from http://portal.office.com. The students can legally install it on their computers and mobile devices, so they can practice and do their tasks using the latest programs of the university. Available 365 services: Exchange (enables intelligent, well-organised correspondence and efficient calendar use) Microsoft OneDrive (you can save your files and photos to OneDrive, you can create, view, edit and -

Microsoft Office Professional 2010 Step by Step, Includes a Selection of Instructional Content for Each Program in the Office Professional 2010 Software Suite
PUBLISHED BY Microsoft Press A Division of Microsoft Corporation One Microsoft Way Redmond, Washington 98052-6399 Copyright © 2011 by Online Training Solutions, Inc. and Curtis Frye All rights reserved. No part of the contents of this book may be reproduced or transmitted in any form or by any means without the written permission of the publisher. Library of Congress Control Number: 2010932312 ISBN: 978-0-7356-2696-6 Printed and bound in the United States of America. 5 6 7 8 9 10 11 12 13 QG 7 6 5 4 3 2 Microsoft Press books are available through booksellers and distributors worldwide. For further infor mation about international editions, contact your local Microsoft Corporation office or contact Microsoft Press International directly at fax (425) 936-7329. Visit our Web site at www.microsoft.com/mspress. Send comments to mspinput@ microsoft.com. Microsoft and the trademarks listed at www.microsoft.com/about/legal/en/us/IntellectualProperty/Trademarks/ EN-US.aspx are trademarks of the Microsoft group of companies. All other marks are property of their respective owners. The example companies, organizations, products, domain names, e-mail addresses, logos, people, places, and events depicted herein are fictitious. No association with any real company, organization, product, domain name, e-mail address, logo, person, place, or event is intended or should be inferred. This book expresses the author’s views and opinions. The information contained in this book is provided without any express, statutory, or implied warranties. Neither the authors, Microsoft Corporation, nor its resellers, or distributors will be held liable for any damages caused or alleged to be caused either directly or indirectly by this book. -

Pdfdocs 4 – Advanced User Guide
pdfDocs 4 – Advanced User Guide pdfDocs 4.2 U1 with OCRDesktop August 2015 Sydney - London - Pittsburgh - Portland - Manila www.docscorp.com - [email protected] Table of Contents TABLE OF CONTENTS ............................................................................................................................................................. 3 INTRODUCTION ..................................................................................................................................................................... 7 WHAT ARE THE KEY FEATURES IN PDFDOCS 4 ...................................................................................................................... 8 SINGLE DOCUMENT MODE ............................................................................................................................................................... 8 ORGANIZER PROJECTS ..................................................................................................................................................................... 8 BINDER PROJECTS ........................................................................................................................................................................... 8 REDACTION .................................................................................................................................................................................... 8 DMS INTEGRATION ........................................................................................................................................................................ -

About Your USING Book
About Your USING Book USING is more than just a book: it’s the fastest, easiest way to gain the technology skills you’re looking for! Don’t just read about it: see it, hear it, with step-by-step video tutorials and valuable audio sidebars delivered through the Free Web Edition that comes with every USING book. For the price of the book you get online access anywhere with a web connection—no books to carry, updated content, and the benefi t of video and audio learning. About the USING Web Edition The Web Edition of every USING book is powered by Safari allowing you to access the video tutorials and valuable audio sidebars. Plus, you can search the contents of the book, highlight text and attach a note to that text, print your notes and highlights in a custom summary, and cut and paste directly from Safari Books Online. How Do You Get Access to the Free Web Edition? Simply visit quepublishing.com/using for information about how to register your USING book or eBook. quepublishing.com Brien Posey 800 East 96th Street, Indianapolis, Indiana 46240 USA Using Microsoft® Publisher 2010 Associate Publisher Greg Wiegand Copyright © 2011 by Pearson Education, Inc. Senior Acquisitions Editor All rights reserved. No part of this book shall be reproduced, stored in a retrieval system, or transmitted by any means, electronic, mechanical, photocopying, recording, or otherwise, Loretta Yates without written permission from the publisher. No patent liability is assumed with respect to Development Editor the use of the information contained herein. Although every precaution has been taken in Mark Cierzniak the preparation of this book, the publisher and author assume no responsibility for errors or omissions. -

Getting Started with Microsoft Publisher 2007 a University of Michigan Library Instructional Technology Workshop
Getting Started with Microsoft Publisher 2007 A University of Michigan Library Instructional Technology Workshop Overview .................................................................................................................... 2 Getting Started ........................................................................................................... 3 Working with Text ....................................................................................................... 4 Linking Text Boxes ................................................................................................................................... 4 Using Text Styles in Publisher ................................................................................................................. 5 Formatting Exercise: Adding a Drop Cap ............................................................................................. 5 Working with Graphics .............................................................................................. 6 Replacing the Sample Image .................................................................................................................... 6 Inserting a New Image .............................................................................................................................. 6 Editing Images ........................................................................................................................................... 7 Creating Shapes ......................................................................................................................................... -
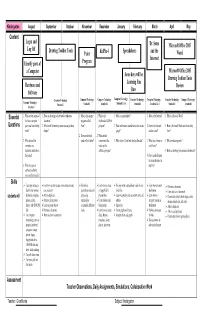
Content Essential Questions Skills Assessment Teacher Observations
Kindergarten August September October November December January February March April May Content Logon and Dr. Seuss Microsoft Office 2003 Log Off Drawing Toolbar Tools KidPix 4 Spreadsheets and the Paint Word Program Internet Identify parts of a Computer Microsoft Office 2003 Some days will be Drawing Toolbar Tools Learning Fun Hardware and Review Days Software Computer/Technology Computer/Technology Computer/Technology Computer/Technology Computer/Technology Computer/Technology Computer/Technology Computer/Technology Computer/Technology Standard 1 Standard 1 Standard 2 Standard 2 & 3 Standard 1 Standard 2 & 3 Standard 2 Standard 2 Standard 1 Essential 1. What are the names of 1. How can drawing tools be used to enhance a 1. What is this snappy 1. What is the 1. What is a spreadsheet? 1. What is the Internet? 1. What is Microsoft Word? the basic computer document? program called multimedia KidPix4 Questions parts and how do they 2. What are all formatting instructions to get these Paint? program? 2. What information should be used to create a 2. How is the Internet 2. How is Microsoft Word used is our daily work? shapes? graph? used as a tool? lives? 2. How are the tools 2. What are the 2. What parts of the used on the toolbar? components that 3. What style of chart best displays the data? 3. What does it mean to 3. What are drawing tools? computer are make up this surf the net? hardware and how are software program? 4. How can drawing tools enhance documents? they used? 4. How can the Internet be an unsafe place to 3. -

Microsoft Publisher
DESIGN BASICS: MICROSOFT PUBLISHER What is Microsoft Publisher? Microsoft Publisher is a desktop-publishing application that you can use to design a wide variety of documents in all sorts of sizes — everything from business cards, newsletters and brochures to cards, fliers and posters. Do I Have Microsoft Publisher? Publisher is included with Microsoft 365 Personal (one user) or Home (five users), which is the subscription version of Microsoft Office. You can subscribe to Microsoft 365 for either a monthly or annual fee. Other applications that come with Microsoft 365 are Word, Excel, PowerPoint, OneNote, Outlook and Access. Publisher is not included with Office Home & Student, but it is included with Office Professional (both of these are software packages you purchase for a one-time price). You can also purchase Publisher separately. In this class, you will create two projects and in the process, learn basic Publisher skills as well as some basic design principles. Course Topics: Publisher vs. Word Review of the Publisher Interface (Ribbon, Thumbnail Pane, Scratch Area) Creating a New Publication (Page Sizes) Four Design Principles Working with Text and Text Boxes Adding Pages Adding Pictures Using Templates Printing Publisher vs. Word Publisher is a page layout program used to create documents like fliers, brochures and posters. Word is a word processor that is better suited for documents like letters, resumes and reports. Although you can design layouts in Word, Publisher is more flexible and allows you to design more freely. In Publisher, you start out with an empty page; in Word, you start out with a text cursor. -

Computer Applications in Business 2
Computer Applications in Business 2 COURSE OUTLINE 1. Course Title: Computer Applications in Business 2 2. CBEDS Title: Computer Operations/Computer Science 3. CBEDS Number: 4601 4. Job Titles: Brokerage Clerk Order Clerk Cashier Production, Planning & Expediting Computer Operator Clerk Court Reporter Receptionist Information and Records Clerk Reservation and Transportation Library Assistant Ticket Agent Office Assistant Shipping and Receiving Clerk Office Clerks Bank Teller Administrative Support Worker 5. Course Description: Students will be able to enhance the skills developed in (ROP) Computer Applications 1-2 and acquire new skills as well. Each student will be able to select units of instruction that are suited to his/her ability and career goals. In addition, students may work on special projects, as approved by instructor, which include work for other classes, i.e. yearbook, newspaper, term papers, and other assignments. This course is designed for students seeking to further develop their computer/business skills. Students will be expected to produce work and conduct themselves in a businesslike manner, work with a minimum of supervision, and complete units of work as selected and assigned. Students will work towards Microsoft Office Specialist Certification at both the CORE and EXPERT level of expertise. Microsoft Office Specialist tests will be made available. Student Outcomes and Objectives: Students will: 1. Identify the application software in Microsoft Offices Suite. 2. Prepare complex Business Documents using MS Word. 3. Prepare and edit complex documents that include indexes, bookmarks, hypertext and other special formatting features. 4. Perform a mail merge utilizing database software. 5. Prepare and edit complex multi-page reports. -

Microsoft Office 2013 User Guide
Microsoft Office 2013 User Guide Revised April 2019 Microsoft Office 2013 Office 2013 and Skype for Business Office 2013 Your new computer, laptop, or virtual desktop includes Microsoft Office 2013. To assist with the transition from Office 2010 to Office 2013, documentation has been made available on the Statewide Learning Management System (SLMS). To access the material, go to https://nyslearn.ny.gov/, login to the site, and search for “Make+the+Switch.” What is Office 365? Microsoft Office 365 is a subscription-based office software and services suite hosted online in the cloud which offers access to various services and software built around the Microsoft Office platform. What is the cloud? The “cloud" can be described as a metaphor for the Internet. Applications and services hosted in the cloud are all accessible via the Internet and the data stored is held in a remote location. As such, cloud-based applications and services can be accessed from anywhere in the world using a multitude of devices such as desktop computers, laptops, tablets, and other mobile devices. What can Office 365 do for you? It will make your job easier. Office 365 diminishes digital overload by providing “one-stop” shopping. It brings all your collaboration resources into a single screen on desktop and mobile devices, so you can focus on your work, efficiently and effectively. Office 365 is intuitive and easy to learn. Revised April 2019 Page 2 of 63 Microsoft Office 2013 Office 2013 and Skype for Business Traditional Capabilities with New Collaborative Functionality Office 365 includes the traditional Microsoft Office Suite of Word, Excel, PowerPoint, and Outlook – but now provides collaborative capabilities. -

Skillchoice Desktop Catalog
OFFICE OF THE CHANCELLOR DesktopDesktop Available Now! SkillSoft offers the most comprehensive and compelling Systemwide e-learning content for desktop computer skills training. Professional SkillChoice Desktop provides learners with comprehensive Development coverage of relevant desktop technologies and skills, [email protected] including more than 400 interactive courses and over 450 Access this content at online books from the OfficeEssentials™ Collection by https://ds.calstate. Books24x7®. Content focuses on Microsoft Office (Mac and edu/?svc=skillsoft PC), Microsoft Windows, Apple OS X, e-mail, internet skills and browsers (including Internet Explorer and Apple Safari), computing fundamentals, and various Adobe products. The courses in this catalog are available at no charge to all CSU faculty and staff. The table of contents is fully searchable. Click the topic heading of interest to reach the course listing in the catalog. Find out more about the course, such as a full description, target audience, expected course duration, course number, and lesson objectives by clicking on the course name. 2 SkillChoice Desktop Catalog Microsoft Office 2013: Power User Excel 6 Course List Microsoft Office 2013: SharePoint for Power Users 6 DESKTOP COMPUTER SKILLS 5 Microsoft Office 2010 7 Adobe 5 Microsoft Office 2010: New Features 7 Microsoft Office 2010 New Features for Users Adobe Flash CS5 5 Migrating from Office 2003 7 Adobe Photoshop CS5 5 Microsoft Office 2010: Beginning Word 7 Adobe Dreamweaver CS5 5 Microsoft SharePoint 2010: New Features -

Computer Training Options Click Here
Your Total Training Resource Microsoft® Publisher® Microsoft Publisher is a powerful software with a user-friendly interface, that allows one to create and personalize professional-looking brochures, flyers, greeting cards, advisements, newsletters, certificates, business cards, booklets, and many more using a vast collection of templates. See how much more quickly you can create the most complex publications using the hundreds of available templates to cut development time down to a fraction. Swap pictures with a simple drag and drop, or add pictures directly from your online albums. Publisher offers a large selection of "building blocks" that can be dragged into your documents, helping you to create page elements such as calendars, newsletter sidebars, and borders. Publisher integrates online sharing and mail merge features, which are handy when you need to send publications to a list of customers. Make your publications look more professional with powerful visual impact to help sell your message. The modules for Publisher are as follows: Module 1 – Desktop Publishing Deluxe To Schedule / Need Additional Information To schedule sessions, receive more information or for questions/clarifications contact us at: Email: Ken Keller at [email protected] or Dean Carroll at [email protected] or Phone: (630) 495-0505 or (800) 869-7497. To see a complete list of our current computer training options click here. 101 W. 22nd Street, Suite 100 630-495-0505 Lombard, IL 60148 630-495-1321 Fax www.c-kg.com Your Total Training Resource Module 1 – Desktop Publishing Deluxe Formalities and Customization: • Identifying the different components to the program • Understanding the undo, redo and repeat keys to save screen and window.