Lakeview School District 1:1 Chromebook Initiative Student Guide Introduction Chromebooks Are Simple and Easy to Use
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Mul-T-Lock 2016 Product Catalog Mul-T-Lock High Security & Access Control Solutions
Mul-T-Lock 2016 Product Catalog Mul-T-Lock High Security & Access Control Solutions Effective January 1, 2016 TABLE OF CONTENTS Introduction 1 Grade 1 Hercular® Deadbolts 65 How to Order 4 Hercular® Anti-Ligature & Latch Locks 66 Multiple Platforms – A Security Level for Every Need 6 Grade 2 Cronus® Deadbolts 67 MT5®+ Platform Introduction 7 Locksets & Hardware 68 Interactive®+ Platform Introduction 8 Rim Locks 69 Integrator® Platform Introduction 9 Mortise Locks 70 Access Control, Keyless Entry & Smart Solutions 10 Lever & Knob Locks 71 WatchLock™ 11 Utility, Furniture & Retail Locks 73 Traka® Key & Asset Management Solutions 14 Padlocks 76 ENTR™ Smart Lock Solution 16 ArmaD Locks 79 Yale® Key Safes & Boxes 18 Mul-T-Lock Junior 82 CLIQ® E-Cylinders & Smart Key Solutions 20 Mul-T-Lock Parts 84 SMARTair® Access Control Solutions 26 Cylinder Parts - Pins 86 SMARTair® E-Motion Electronic Cabinet & Locker Locks 32 Cylinder Parts 100 Yale® Shine™ Glass Digital Door Locks 36 Hercular® Deadbolt Parts 138 Code-It™ Electronic Pushbutton Levers 38 Anti-Ligature Deadbolt & Gate Latch Lock Parts 142 GotU®+ Digital Door Viewers 40 Top Guard® Parts 143 Mul-T-Lock Keys, Keying Options & Services 42 Utility & Furniture Lock Parts 144 Keys & Cards 43 Padlock Parts 160 Services 47 Key Cutting Machine Parts 170 Machinery, Pinkits & Tools 48 Standard Ordering Form 174 Locksmith Tools 49 Master Keying Information 175 Cylinders 51 Key & Cylinder Maintenance 178 Mortise Cylinders 52 Warranty 180 Mogul Cylinders 52 Conditions of Sale 182 Rim Cylinders 53 Available Finishes 187 Large Format Interchangeable Cores 53 Knob, Lever and Deadbolt Replacement Cylinders 54 Foreign Cylinders 62 Deadbolts & Deadlatches 64 Established in 1973, Mul-T-Lock is a worldwide leader in the developing, manufacturing, and marketing of high security products for Institutional, Commercial, Industrial, and Residential customers. -

Regulatory Guide 5.12, Revision 1
U.S. NUCLEAR REGULATORY COMMISSION October 2016 OFFICE OF NUCLEAR REGULATORY RESEARCH Revision 1 Technical Lead A. Tardiff REGULATORY GUIDE REGULATORY GUIDE 5.12 (Draft was issued as DG-5027, dated January 2015) GENERAL USE OF LOCKS IN THE PROTECTION AND CONTROL OF: FACILITIES, RADIOACTIVE MATERIALS, CLASSIFIED INFORMATION, CLASSIFIED MATTER, AND SAFEGUARDS INFORMATION A. INTRODUCTION Purpose This regulatory guide (RG) describes methods and procedures that the staff of the U.S. Nuclear Regulatory Commission (NRC) considers acceptable for the selection, use, and control of locking devices. Locks can be used in the protection of: areas, facilities, certain radioactive materials, and specific types of information (e.g., classified matter, National Security Information (NSI), Restricted Data (RD), Formerly Restricted Data (FRD), Safeguards Information (SGI)). Applicable Regulations • U.S. Code of Federal Regulations, “Domestic Licensing of Production and Utilization Facilities,” Part 50, Chapter I, Title 10, “Energy” (10 CFR Part 50), (Ref. 1). Specifically Section 10 CFR 50.34 "Contents of applications" requires under (c)(1) that "[e]ach applicant for an operating license for a production or utilization facility that will be subject to §§ 73.50 and 73.60 of this chapter must include a physical security plan" and under (c)(2) "[e]ach applicant for an operating license for a utilization facility that will be subject to the requirements of § 73.55 of this chapter must include a physical security plan…" • 10 CFR Part 50, Appendix R, “Fire Protection Program for Nuclear Power Facilities Operating Prior to January 1, 1979,” requires under III.N.4, that the fire brigade leader shall have ready access to keys for any locked fire doors. -

Master Lock Safety Series Catalogue
MASTER LOCK SAFETY SAFETY PADLOCKS LOCKOUT HASPS ELECTRICAL LOCKOUT VALVE LOCKOUT CABLE LOCKOUT & LOCK BOXES PADLOCK STATIONS & KITS TAGS 1 SAFETY LOCKOUT WHAT IS LOCKOUT? Lockout/tagout is an important safety procedure that involves shutting off the power to industrial machines or equipment during maintenance or repair. This procedure protects employees from risks caused by power sources. Used properly in conjunction with a well-planned lockout process, the safety padlock helps ensure that employees will not inadvertently activate a piece of equipment while someone else is working on it. 1 employee - 1 padlock - 1 key, this means all employees carry a unique key and no one else’s key can open another colleague’s safety padlock. SAFETY PADLOCK ORDERING PROCEDURES MASTER LOCK SAFETY LOCK MASTER Is your customer a Registered or Non Registered End User on the Master Lock Oracle Key Charting System? NO YES NON REGISTERED END USER REGISTERED END USER Recommended for small - medium end users. Recommended for large end users or end users with a concern about key code duplications. Orders will be supplied with randomly picked padlocks from the 108,000 key codes available. Orders will be registered with the Master Lock Oracle Note: Duplications may occur in subsequent orders. Key Charting System and will be assigned key codes to avoid the DANGER of key duplications. Stock: Ex Mayo Hardware warehouse. Ordering Process: No Special Ordering Requirements. Stock: Ex manufacturer 4-6 week lead time. Ordering Process: Special Ordering Requirements (Refer to below instructions). REGISTERED END USER SPECIAL ORDERING REQUIREMENT How do I register my End User? Simply arrange for your end user to complete the “MASTER LOCK KEY CHARTING REGISTRATION FORM” and forward with your official purchase order to Mayo Hardware Pty Ltd. -

Mul-T-Lock 2017 Price Catalog Mul-T-Lock High Security & Access Control Solutions
Mul-T-Lock 2017 Price Catalog Mul-T-Lock High Security & Access Control Solutions Effective January 1, 2017 TABLE OF CONTENTS Introduction 1 Large Format Interchangeable Cores 54 How to Order 4 Knob, Lever and Deadbolt Replacement Cylinders 55 Multiple Platforms – A Security Level for Every Need 6 Foreign Cylinders 65 MT5®+ Platform Introduction 7 Deadbolts & Deadlatches 68 Interactive®+ Platform Introduction 8 Grade 1 Hercular® Deadbolts 69 ClassicPro™ Platform Introduction 9 Hercular® Anti-Ligature & Latch Locks 72 Access Control, Keyless Entry & Smart Solutions 10 Grade 2 Cronus® Deadbolts 74 CLIQ® E-Cylinders & Smart Key Solutions 11 Locksets & Hardware 75 SMARTair® Access Control Solutions 17 Rim Locks 76 SMARTair® E-Motion Electronic Cabinet & Locker Locks 23 Mortise Locks 77 DONNA™ Multifamily and Hospitality 25 Lever & Knob Locks 78 Code-It™ Electronic Pushbutton Levers 27 Utility, Furniture & Retail Locks 80 KonnectLock™ (Formerly WatchLock™) 29 Padlocks 86 Traka® Key & Asset Management Solutions 32 ArmaD Locks 92 ENTR™ Smart Lock Solution 34 Mul-T-Lock Junior 95 GotU®+ Digital Door Viewers 37 Mul-T-Lock Parts 97 Yale® Real Living™ Residential Digital Locks 39 Cylinder Parts - Pins 100 Mul-T-Lock Keys, Keying Options & Services 41 Cylinder Parts 114 MT5®+ Keys & Cards 42 Hercular® Deadbolt Parts 152 Interactive®+ Keys & Cards 43 Anti-Ligature Deadbolt & Gate Latch Lock Parts 156 Old Interactive Keys 43 Top Guard® Parts 157 ClassicPro™ Keys & Cards 44 Utility & Furniture Lock Parts 158 Classic / Integrator® Keys & Cards 44 Padlock Parts 174 Services 46 Key Cutting Machine Parts 186 Machinery, Pinkits & Tools 47 Standard Ordering Form 190 Locksmith Tools 48 Master Keying Information 191 Cylinders 50 Key & Cylinder Maintenance 194 Mortise Cylinders 51 Warranty 196 Mogul Cylinders 51 Conditions of Sale 198 Rim Cylinders 53 Available Finishes 203 Established in 1973, Mul-T-Lock is a worldwide leader in the developing, manufacturing, and marketing of high security products for Institutional, Commercial, Industrial, and Residential customers. -

COMPUTER Class – I Chapter-6 Part 1 COMPUTER KEYBOARD
COMPUTER Class – I Chapter-6 Part 1 COMPUTER KEYBOARD A pencil or a pen is needed to write in a notebook, but we cannot use a pencil or pen for writing on a computer. You have to use the keyboard to write/enter the information and instruction into a computer. It looks like a typewriter’s keyboard. It has many small button on it. These buttons are called keys. Whatever we type on the keyboard appears on the monitor at the cursor position. Cursor is a small blinking line on the monitor. There are usually 104 keys on the keyboard. There are different types of keys to perform different tasks. The different types of keys are as follows: ❖ Alphabet Keys ❖ Number Keys ❖ Function Keys ❖ Special Keys ALPHABET KEYS These keys are used for typing letters and words. The letters A to Z are written on these keys. The alphabet keys resemble the keys of a typewriter. Due to its first row of alphabet (Q,W,E,R,T,Y), it is called a QWERTY keyboard/keypad. NUMBER KEYS These are keys with numbers written on them. These keys are used to type numbers. One set of number keys are placed above the alphabet keys and another set is on the right side of the keyboard.(0-9) Numeric keypad can be used only when the NUM LOCK is ON. EXERCISES 1. Fill in the blanks: a. Small buttons on the keyboard are called -------------. b. There are usually------------keys on the keyboard. c. Keyboard is used to enter ------------- and -------------- into the computer. -

REALFORCE Software User's Manual
REALFORCE Software User's Manual Wrining!An electrical product may cause a fire, injury, or death if the safety precautions are not observed. Thank you for purchasing our product. This user manual describes the important precautions to prevent an accident and the methods of handling this product. Please read this manual carefully and use this product safely. This manual should be kept in a handy place for reference. 2018 Topre Corporation August 2018(First edition) 1 Contents ●Introduction 3 1. Installing procedure 3 2. Starting REALFORCE software 6 3. Adjusting the Actuation Point (for Models with the APC Function Only) 7 4. Adjust RGB-LED (For the REALFORCE RGB Series Only) 11 5. Selecting the key to be locked 19 6. Adjusting settings 20 7. Updating firmware 27 8. Saving of Settings for Keyboard and Saving and Reading of Setting Profile Data 34 9. Selecting a keyboard when two or more keyboards are connected 38 10. Exiting software 41 11. If you have a problem 42 2 ●Introduction This User’s Manual explains how to use REALFORCE with its exclusive software to adjust the settings for REALFORCE. 1. Installing procedure First, install the installer from the following URL: www.realforce.co.jp/support/ Cautiion! The software should be downloaded and used at your own risk. Topre will assume no responsibility for any problem or damage that has taken place as a result of downloading or using the software. Double-click and execute the installer. “Select language” will be displayed. Select “Japanese” or “English” and click “Next” in the lower right corner. -

GLASS LOCKS CABINET LOCKS SHEET METAL CAM LOCKS PUSH LOCKS CAM LOCKS 624 623 623 621 622 614 614 615 615 616 616 617 618 618 619 Page Page 619~622 619~622
LOCKS GLASS LOCKS CABINET LOCKS SHEET METAL CAM LOCKS PUSH LOCKS CAM LOCKS 612 HOW TO ORDER INDEX - LOCKS For all lock orders, please specify one of the following keying options at the time of order: • Keyed Alike: All locks will have the same key number, and can be unlocked with the same key. Good option for low-security environments, or when multiple displays need to be easily accessed. • Keyed Differently: Each lock will have a different key number, and cannot be unlocked with the same key. Option for higher security environments, lockers, etc, when access must be restricted. • Keyed Differently with Master Keying: Each lock will have a different key number; a master key can be used to access all locks. For higher security environments with restricted access, where a supervisor or custodian requires complete access. (Not available for all models, available by special order only. A master key surcharge may apply.) GLASS LOCKS Picture Item No. Key Changes Master Key Option Page XL-GC01 24 - 614 XL-GC02 24 - 614 XL-GC03 24 - 615 2100GLK 12 - 615 1300GL 1 Million 2520 changes per master key 616 2200GL 12 Master key option available 616 NO990 40,000 - 617 1310GL 1 Million 2520 changes per master key 618 1310GLW 1 Million 2520 changes per master key 618 MD-N1 7800 750 changes per master key 619~622 MD-MK1, K1 - - 619~622 1330GL-MK 7800 750 changes per master key 619 MILLION CABINET LOCKS Picture Item No. Key Changes Master Key Option Page 1830-MK 7800 750 changes per master key 621 6830-30MK 7800 750 changes per master key 622 7810 1 Million 2520 changes per master key 623 6810-SP - - 623 8810-24 3 Million 3000 changes per master key 624 www.sugatsune.com 1-800-562-5267 (U.S.A. -
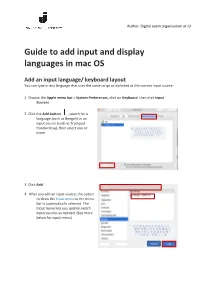
Guide to Add Input and Display Languages in Mac OS
Author: Digital exam organisation at JU Guide to add input and display languages in mac OS Add an input language/ keyboard layout You can type in any language that uses the same script or alphabet as the current input source. 1 Choose the Apple menu bar > System Preferences, click on Keyboard, then click Input Sources 2 Click the Add button , search for a language (such as Bengali) or an input source (such as Trackpad Handwriting), then select one or more 3 Click Add Choose among languages or choose an input source 4 After you add an input source, the option to show the Input menu in the menu bar is automatically selected. The Input menu lets you quickly switch input sources as needed. (See more below for input menu) Cancel Add Author: Digital exam organisation at JU Switch between input sources Input menu To switch between input sources, do any of the following: ▪ Use the Input menu: Click the Input menu in the menu bar, then choose an input source. If an input source is dimmed, the current app doesn’t support it ▪ Use the Caps Lock key: Press the Caps Lock key to switch between a non-Latin input source (such as Chinese or Korean) and a Latin input source (such as French or English). To use this method, you must select the “Use Caps Lock to switch to and from” option in the Input Sources pane. Choose Apple menu > System Preferences, click Keyboard, then click Input Sources ▪ Use keyboard shortcuts: Press Option-Control-Space bar to select the next input source in the Input menu, or Control-Space bar to select the previous input source When you add input sources, those languages are automatically added to the list of preferred languages in Language & Region preferences; you can set your Mac to use one of those languages. -

Title Keyboard : All Special Keys : Enter, Del, Shift, Backspace ,Tab … Contributors Dhanya.P Std II Reviewers Submission Approval Date Date Ref No
Title Keyboard : All special keys : Enter, Del, Shift, Backspace ,Tab ¼ Contributors Dhanya.P Std II Reviewers Submission Approval Date Date Ref No: This topic describes the special keys on the keyboard of a computer Brief Description and their functionalities . Goal To familiarize the special keys on the keyboard of a computer. Pre-requisites Familiarity with computer. Learning Concepts that special keys on a keyboard has special functionalities. Outcome One Period Duration http://www.ckls.org/~crippel/computerlab/tutorials/keyboard/ References http://computer.howstuffworks.com/ Page Nos: 2,3,4,5,6 Detailed Description Page No: 7 Lesson Plan Page No: 7 Worksheet Page No: 8 Evaluation Page No: 8 Other Notes Detailed Description A computer keyboard is a peripheral , partially modeled after the typewriter keyboard. Keyboards are designed for the input of text and characters. Special Keys Function Keys Cursor Control Keys Esc Key Control Key Shift Key Enter Key Tab Key Insert Key Delete Key ScrollLock Key NumLock Key CapsLock Key Pasue/Break Key PrtScr Key Function Keys F1 through F12 are the function keys. They have special purposes. The following are mainly the purpose of the function keys. But it may vary according to the software currently running. # F1 - Help # F2 - Renames selected file # F3 - Opens the file search box # F4 - Opens the address bar in Windows Explorer # F5 - Refreshes the screen in Windows Explorer # F6 - Navigates between different sections of a Windows Explorer window # F8 - Opens the start-up menu when booting Windows # F11 - Opens full screen mode in Explorer Function Keys F1 through F12 are the function keys. -

Emulator User's Reference
Personal Communications for Windows, Ver sion 5.8 Emulator User’s Reference SC31-8960-00 Personal Communications for Windows, Ver sion 5.8 Emulator User’s Reference SC31-8960-00 Note Before using this information and the product it supports, read the information in “Notices,” on page 217. First Edition (September 2004) This edition applies to Version 5.8 of Personal Communications (program number: 5639–I70) and to all subsequent releases and modifications until otherwise indicated in new editions. © Copyright International Business Machines Corporation 1989, 2004. All rights reserved. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Figures . vii Using PDT Files . .24 Double-Byte Character Support. .25 Tables . .ix Printing to Disk . .26 Workstation Profile Parameter for Code Page . .27 About This Book. .xi Chapter 5. Key Functions and Who Should Read This Book. .xi How to Use This Book . .xi Keyboard Setup . .29 Command Syntax Symbols . .xi Default Key Function Assignments . .29 Where to Find More Information . xii Setting the 3270 Keyboard Layout Default . .29 InfoCenter. xii Default Key Functions for a 3270 Layout . .29 Online Help . xii Setting the 5250 Keyboard Layout Default . .32 Personal Communications Library. xii Default Key Functions for a 5250 Layout . .32 Related Publications . xiii Default Key Functions for the Combined Package 34 Contacting IBM. xiii Setting the VT Keyboard Layout Default . .34 Support Options . xiv Default Key Functions for the VT Emulator Layout . .35 Keyboard Setup (3270 and 5250) . .36 Part 1. General Information . .1 Keyboard File . .36 Win32 Cut, Copy, and Paste Hotkeys . -

Goldtouch Go2 Travel Keyboard User Manual
Maintaining Your Keyboard Like all electronic equipment you need to avoid getting it wet, dropping it, or using un- due force to depress the keys or operate the latch handle. Go!2 Travel Keyboard Do not subject the keyboard to extremes in temperature. Your keyboard will operate best 2 in temperatures of - 5° C to 50° C (23°F to 122°F). Keep the surface of your keyboard clean GTP-0044 GOLDTOUCH Go! MOBILE USB KEYBOARD by wiping with a soft cloth that is dampened with a mild cleaning solutions; preferably water and mild soap. Important: Do not attempt to adjust the keyboard without releasing the latch handle and DO NOT PLACE ANY LUBRICATION or CLEANING FLUID IN THE BALL JOINT. THIS WILL VOID YOUR WARRANTY. Device Support As mobile devices continue to expand in the marketplace, the Windows XP SP2+ Goldtouch Go!2 will endeavor to support all possible devices Windows Vista through compliance with hardware standards. Windows 7 User Manual Windows 8 To obtain support, download guides, and to learn about Congratulations on your purchase of a Goldtouch Go!2 Mobile Keyboard. additional ergonomic and mobile ergonomic products from goldtouch, please visit our website at: Mac OS X 10.4+ You’re about to join the tens of thousands of people who’ve traded in their OEM keyboards for www.goldtouch.com. the most innovative, comfortable ergonomic keyboards ever designed. The technology behind the Goldtouch ergonomic keyboard is one that recognizes the unique needs of every individual, which vary according to body type, height, weight, shoulder width, hand position, and other health and lifestyle factors. -

'Delete' Key? Lenovo Did. Here's Why. 25 June 2009, by JESSICA MINTZ , AP Technology Writer
Who moved my 'Delete' key? Lenovo did. Here's why. 25 June 2009, By JESSICA MINTZ , AP Technology Writer Typewriter technology evolved. Mainframe computing led to function keys and others of uncertain use today. The PC era dawned. Yet many laws of keyboard layout remain sacred, like the 19-millimeter distance between the centers of the letter keys. Tom Hardy, who designed the original IBM PC of 1981, said companies have tried many times to change the sizes of keys. That first PC had a In this product image released by Lenovo, the Lenovo smaller "Shift" key than IBM's popular Selectric Thinkpad T400S Laptop keyboard, is shown. (AP typewriter did, and it was placed in a different spot, Photo/Lenovo) in part because the industry didn't think computers would replace typewriters for high-volume typing tasks. Lenovo put nearly a year of research into two IBM reversed course with the next version to quiet design changes that debuted on an updated the outcry from skilled touch-typists. ThinkPad laptop this week. No, not the thinner, lighter form or the textured touchpad - rather, the "Customers have responded with a resounding, extra-large "Delete" and "Escape" keys. 'Don't fool with the key unless you can you can improve it,'" said Hardy, now a design strategist It may seem like a small change, but David Hill, based in Atlanta. vice president of corporate identity and design at Lenovo, points out, "Any time you start messing PC makers relearned this lesson in the past year, around with the keyboard, people get nervous." as netbooks - tiny, cheap laptops - have become popular with budget-conscious consumers.