'Delete' Key? Lenovo Did. Here's Why. 25 June 2009, by JESSICA MINTZ , AP Technology Writer
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Mul-T-Lock 2016 Product Catalog Mul-T-Lock High Security & Access Control Solutions
Mul-T-Lock 2016 Product Catalog Mul-T-Lock High Security & Access Control Solutions Effective January 1, 2016 TABLE OF CONTENTS Introduction 1 Grade 1 Hercular® Deadbolts 65 How to Order 4 Hercular® Anti-Ligature & Latch Locks 66 Multiple Platforms – A Security Level for Every Need 6 Grade 2 Cronus® Deadbolts 67 MT5®+ Platform Introduction 7 Locksets & Hardware 68 Interactive®+ Platform Introduction 8 Rim Locks 69 Integrator® Platform Introduction 9 Mortise Locks 70 Access Control, Keyless Entry & Smart Solutions 10 Lever & Knob Locks 71 WatchLock™ 11 Utility, Furniture & Retail Locks 73 Traka® Key & Asset Management Solutions 14 Padlocks 76 ENTR™ Smart Lock Solution 16 ArmaD Locks 79 Yale® Key Safes & Boxes 18 Mul-T-Lock Junior 82 CLIQ® E-Cylinders & Smart Key Solutions 20 Mul-T-Lock Parts 84 SMARTair® Access Control Solutions 26 Cylinder Parts - Pins 86 SMARTair® E-Motion Electronic Cabinet & Locker Locks 32 Cylinder Parts 100 Yale® Shine™ Glass Digital Door Locks 36 Hercular® Deadbolt Parts 138 Code-It™ Electronic Pushbutton Levers 38 Anti-Ligature Deadbolt & Gate Latch Lock Parts 142 GotU®+ Digital Door Viewers 40 Top Guard® Parts 143 Mul-T-Lock Keys, Keying Options & Services 42 Utility & Furniture Lock Parts 144 Keys & Cards 43 Padlock Parts 160 Services 47 Key Cutting Machine Parts 170 Machinery, Pinkits & Tools 48 Standard Ordering Form 174 Locksmith Tools 49 Master Keying Information 175 Cylinders 51 Key & Cylinder Maintenance 178 Mortise Cylinders 52 Warranty 180 Mogul Cylinders 52 Conditions of Sale 182 Rim Cylinders 53 Available Finishes 187 Large Format Interchangeable Cores 53 Knob, Lever and Deadbolt Replacement Cylinders 54 Foreign Cylinders 62 Deadbolts & Deadlatches 64 Established in 1973, Mul-T-Lock is a worldwide leader in the developing, manufacturing, and marketing of high security products for Institutional, Commercial, Industrial, and Residential customers. -

Mac Keyboard Shortcuts Cut, Copy, Paste, and Other Common Shortcuts
Mac keyboard shortcuts By pressing a combination of keys, you can do things that normally need a mouse, trackpad, or other input device. To use a keyboard shortcut, hold down one or more modifier keys while pressing the last key of the shortcut. For example, to use the shortcut Command-C (copy), hold down Command, press C, then release both keys. Mac menus and keyboards often use symbols for certain keys, including the modifier keys: Command ⌘ Option ⌥ Caps Lock ⇪ Shift ⇧ Control ⌃ Fn If you're using a keyboard made for Windows PCs, use the Alt key instead of Option, and the Windows logo key instead of Command. Some Mac keyboards and shortcuts use special keys in the top row, which include icons for volume, display brightness, and other functions. Press the icon key to perform that function, or combine it with the Fn key to use it as an F1, F2, F3, or other standard function key. To learn more shortcuts, check the menus of the app you're using. Every app can have its own shortcuts, and shortcuts that work in one app may not work in another. Cut, copy, paste, and other common shortcuts Shortcut Description Command-X Cut: Remove the selected item and copy it to the Clipboard. Command-C Copy the selected item to the Clipboard. This also works for files in the Finder. Command-V Paste the contents of the Clipboard into the current document or app. This also works for files in the Finder. Command-Z Undo the previous command. You can then press Command-Shift-Z to Redo, reversing the undo command. -

DEC Text Processing Utility Reference Manual
DEC Text Processing Utility Reference Manual Order Number: AA–PWCCD–TE April 2001 This manual describes the elements of the DEC Text Processing Utility (DECTPU). It is intended as a reference manual for experienced programmers. Revision/Update Information: This manual supersedes the DEC Text Processing Utility Reference Manual, Version 3.1 for OpenVMS Version 7.2. Software Version: DEC Text Processing Utility Version 3.1 for OpenVMS Alpha Version 7.3 and OpenVMS VAX Version 7.3 The content of this document has not changed since OpenVMS Version 7.1. Compaq Computer Corporation Houston, Texas © 2001 Compaq Computer Corporation COMPAQ, VAX, VMS, and the Compaq logo Registered in U.S. Patent and Trademark Office. OpenVMS is a trademark of Compaq Information Technologies Group, L.P. Motif is a trademark of The Open Group. PostScript is a registered trademark of Adobe Systems Incorporated. All other product names mentioned herein may be the trademarks or registered trademarks of their respective companies. Confidential computer software. Valid license from Compaq or authorized sublicensor required for possession, use, or copying. Consistent with FAR 12.211 and 12.212, Commercial Computer Software, Computer Software Documentation, and Technical Data for Commercial Items are licensed to the U.S. Government under vendor’s standard commercial license. Compaq shall not be liable for technical or editorial errors or omissions contained herein. The information in this document is provided "as is" without warranty of any kind and is subject to change without notice. The warranties for Compaq products are set forth in the express limited warranty statements accompanying such products. -
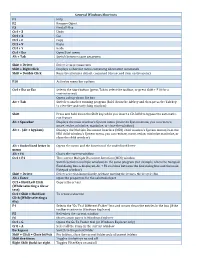
General Windows Shortcuts
General Windows Shortcuts F1 Help F2 Rename Object F3 Find all files Ctrl + Z Undo Ctrl + X Cut Ctrl + C Copy Ctrl + V Paste Ctrl + Y Redo Ctrl + Esc Open Start menu Alt + Tab Switch between open programs Alt + F4 Quit program Shift + Delete Delete item permanently Shift + Right Click Displays a shortcut menu containing alternative commands Shift + Double Click Runs the alternate default command ( the second item on the menu) Alt + Double Click Displays properties F10 Activates menu bar options Shift + F10 Opens a contex t menu ( same as righ t click) Ctrl + Esc or Esc Selects the Start button (press Tab to select the taskbar, or press Shift + F10 for a context menu) Alt + Down Arrow Opens a drop‐down list box Alt + Tab Switch to another running program (hold down the Alt key and then press the Tab key to view the task‐switching window) Alt + Shift + Tab Swit ch b ackward s b etween open appli cati ons Shift Press and hold down the Shift key while you insert a CD‐ROM to bypass the automatic‐ run feature Alt + Spacebar Displays the main window's System menu (from the System menu, you can restore, move, resize, minimize, maximize, or close the window) Alt + (Alt + hyphen) Displays the Multiple Document Interface (MDI) child window's System menu (from the MDI child window's System menu, you can restore, move, resize, minimize maximize, or close the child window) Ctrl + Tab Switch to t h e next child window o f a Multi ple D ocument Interf ace (MDI) pr ogram Alt + Underlined letter in Opens the menu and the function of the underlined letter -

Towards an Intelligent Multilingual Keyboard System
Towards an Intelligent Multilingual Keyboard System Tanapong Potipiti, Virach Sornlertlamvanich, Kanokwut Thanadkran National Electronics and Computer Technology Center, National Science and Technology Development Agency, Ministry of Science and Technology Environment, 22nd Floor Gypsum Metropolitan Tower 539/2 Sriayudhya Rd. Rajthevi Bangkok 10400 Thailand Email: [email protected], [email protected], [email protected] ABSTRACT 3 THE APPROACH This paper proposes a practical approach employing n-gram 3.1 Overview models and error-correction rules for Thai key prediction and In the traditional Thai keyboard input system, a key button with Thai-English language identification. The paper also proposes the help of language-switching key and the shift key can output rule-reduction algorithm applying mutual information to reduce 4 different characters. For example, in the Thai keyboard the ‘a’- the error-correction rules. Our algorithm reported more than key button can represent 4 different characters in different 99% accuracy in both language identification and key modes as shown in Table 1. prediction. Table 1: A key button can represent different characters in 1 INTRODUCTION different modes. For Thai users, there are always two annoyances while typing English Mode English Mode Thai Mode Thai Mode without Shift with Shift without Shift with Shift Thai-English bilingual documents, which are usual for Thais. ¢ § The first is when the users want to switch from typing Thai to ‘a’ ‘A’ ‘ ’‘’ English, they have to input a special key to tell the operating system to change the language mode. Further, if the language- However, using NLP technique, the Thai-English switching key is ignored, they have to delete the token just typed keyboard system which can predict the key users intend to type and re-type that token after language switching. -

Openvms: an Introduction
The Operating System Handbook or, Fake Your Way Through Minis and Mainframes by Bob DuCharme VMS Table of Contents Chapter 7 OpenVMS: An Introduction.............................................................................. 7.1 History..........................................................................................................................2 7.1.1 Today........................................................................................................................3 7.1.1.1 Popular VMS Software..........................................................................................4 7.1.2 VMS, DCL................................................................................................................4 Chapter 8 Getting Started with OpenVMS........................................................................ 8.1 Starting Up...................................................................................................................7 8.1.1 Finishing Your VMS Session...................................................................................7 8.1.1.1 Reconnecting..........................................................................................................7 8.1.2 Entering Commands..................................................................................................8 8.1.2.1 Retrieving Previous Commands............................................................................9 8.1.2.2 Aborting Screen Output.........................................................................................9 -

PC Basics Bronze Level
PC Basics Bronze Level Keyboard Call us on 03333 444019 Learning Guide Getting Started: Using the Keyboard The Keyboard is, along with the mouse, vital to controlling your computer. Keyboards work by translating your keystrokes into a signal that a computer can understand. Keyboards usually have a standard layout but there are some “special keys” and “shortcuts” which are helpful to know about: Light sensors (for Tab Key Function Keys Delete Number Lock and Caps Lock) Escape Caps Lock Backspace Space Bar Number Keys Shift Enter Control Alt Arrow Keys Menu Key Windows Key Tip : The keyboard shown above is the FULL version that would come as a separate piece of equipment when you have a DESKTOP computer. The keyboard that is built-in on LAPTOPS is sometimes a smaller version of the one above. Please see over for a full explanation of all the above keys and buttons… Learning Guide Keyboard Commands Tab: Tab is used to advance the cursor to the next “tab spot”, which could be in a form (on the Internet) or in a letter (word processor) Caps Lock: Locks the keyboard so that anything you type is in CAPITAL LETTERS. Usually the computer shows some kind of warning that you have pressed this key e.g. a light on the keyboard Shift: Holding down the Shift key (usually denoted with a ↑on the key) has a number of uses, both to type capital letters and to access the symbols on the upper part of a key, e.g. the £ sign above the number 3. There are Shift keys on both sides of the keyboard. -

Guide to the DEC Text Processing Utility
Guide to the DEC Text Processing Utility Order Number: AA–PWCBD–TE April 2001 This manual introduces the DEC Text Processing Utility (DECTPU). It is for experienced programmers as well as new users of DECTPU. Revision/Update Information: This manual supersedes the Guide to the DEC Text Processing Utility, Version 3.1 Software Version: OpenVMS Alpha Version 7.3 OpenVMS VAX Version 7.3 The content of this manual has not changed sinced OpenVMS Version 7.1 Compaq Computer Corporation Houston, Texas © 2001 Compaq Computer Corporation Compaq, VAX, VMS and the Compaq logo Registered in U.S. Patent and Trademark Office. OpenVMS is a trademark of Compaq Information Technologies Group, L.P. in the United States and other countries. PostScript is a registered trademark of Adobe Systems Incorporated. Motif is a registered trademark of the The Open Group. All other product names mentioned herein may be the trademarks or registered trademarks of their respective companies. Confidential computer software. Valid license from Compaq or authorized sublicensor required for possession, use, or copying. Consistent with FAR 12.211 and 12.212, Commercial Computer Software, Computer Software Documentation, and Technical Data for Commercial Items are licensed to the U.S. Government under vendor’s standard commercial license. Compaq shall not be liable for technical or editorial errors or omissions contained herein. The information in this document is provided "as is" without warranty of any kind and is subject to change without notice. The warranties for Compaq products are set forth in the express limited warranty statements accompanying such products. Nothing herein should be construed as constituting an additional warranty. -

Startup Keyboard Shortcuts Press the Key Or Key Combination Until The
Startup keyboard shortcuts Press the key or key combination until the expected function occurs/appears (for example, hold Option during startup until Startup Manager appears, or Shift until "Safe Boot" appears). Tip: If a startup function doesn't work and you use a third-party keyboard, connect an Apple keyboard and try again. Key or key combination What it does Option Display all bootable volumes (Startup Manager) Shift Perform Safe Boot (start up in Safe Mode) C Start from a bootable disc (DVD, CD) T Start in FireWire target disk mode N Start from NetBoot server X Force Mac OS X startup (if non-Mac OS X startup volumes are present) Command-V Start in Verbose Mode Command-S Start in Single User Mode To use a keyboard shortcut, or key combination, you press a modifier key with a character key. For example, pressing the Command key (the key with a symbol) and the "c" key at the same time copies whatever is currently selected (text, graphics, and so forth) into the Clipboard. This is also known as the Command-C key combination (or keyboard shortcut). A modifier key is a part of many key combinations. A modifier key alters the way other keystrokes or mouse clicks are interpreted by Mac OS X. Modifier keys include: Command, Control, Option, Shift, Caps Lock, and the fn key (if your keyboard has a fn key). Here are the modifier key symbols you can see in Mac OS X menus: (Command key) - On some Apple keyboards, this key also has an Apple logo ( ) (Control key) (Option key) - "Alt" may also appear on this key (Shift key) (Caps Lock) - Toggles Caps Lock on or off fn (Function key) Startup keyboard shortcuts Press the key or key combination until the expected function occurs/appears (for example, hold Option during startup until Startup Manager appears, or Shift until "Safe Boot" appears). -

Regulatory Guide 5.12, Revision 1
U.S. NUCLEAR REGULATORY COMMISSION October 2016 OFFICE OF NUCLEAR REGULATORY RESEARCH Revision 1 Technical Lead A. Tardiff REGULATORY GUIDE REGULATORY GUIDE 5.12 (Draft was issued as DG-5027, dated January 2015) GENERAL USE OF LOCKS IN THE PROTECTION AND CONTROL OF: FACILITIES, RADIOACTIVE MATERIALS, CLASSIFIED INFORMATION, CLASSIFIED MATTER, AND SAFEGUARDS INFORMATION A. INTRODUCTION Purpose This regulatory guide (RG) describes methods and procedures that the staff of the U.S. Nuclear Regulatory Commission (NRC) considers acceptable for the selection, use, and control of locking devices. Locks can be used in the protection of: areas, facilities, certain radioactive materials, and specific types of information (e.g., classified matter, National Security Information (NSI), Restricted Data (RD), Formerly Restricted Data (FRD), Safeguards Information (SGI)). Applicable Regulations • U.S. Code of Federal Regulations, “Domestic Licensing of Production and Utilization Facilities,” Part 50, Chapter I, Title 10, “Energy” (10 CFR Part 50), (Ref. 1). Specifically Section 10 CFR 50.34 "Contents of applications" requires under (c)(1) that "[e]ach applicant for an operating license for a production or utilization facility that will be subject to §§ 73.50 and 73.60 of this chapter must include a physical security plan" and under (c)(2) "[e]ach applicant for an operating license for a utilization facility that will be subject to the requirements of § 73.55 of this chapter must include a physical security plan…" • 10 CFR Part 50, Appendix R, “Fire Protection Program for Nuclear Power Facilities Operating Prior to January 1, 1979,” requires under III.N.4, that the fire brigade leader shall have ready access to keys for any locked fire doors. -

Master Lock Safety Series Catalogue
MASTER LOCK SAFETY SAFETY PADLOCKS LOCKOUT HASPS ELECTRICAL LOCKOUT VALVE LOCKOUT CABLE LOCKOUT & LOCK BOXES PADLOCK STATIONS & KITS TAGS 1 SAFETY LOCKOUT WHAT IS LOCKOUT? Lockout/tagout is an important safety procedure that involves shutting off the power to industrial machines or equipment during maintenance or repair. This procedure protects employees from risks caused by power sources. Used properly in conjunction with a well-planned lockout process, the safety padlock helps ensure that employees will not inadvertently activate a piece of equipment while someone else is working on it. 1 employee - 1 padlock - 1 key, this means all employees carry a unique key and no one else’s key can open another colleague’s safety padlock. SAFETY PADLOCK ORDERING PROCEDURES MASTER LOCK SAFETY LOCK MASTER Is your customer a Registered or Non Registered End User on the Master Lock Oracle Key Charting System? NO YES NON REGISTERED END USER REGISTERED END USER Recommended for small - medium end users. Recommended for large end users or end users with a concern about key code duplications. Orders will be supplied with randomly picked padlocks from the 108,000 key codes available. Orders will be registered with the Master Lock Oracle Note: Duplications may occur in subsequent orders. Key Charting System and will be assigned key codes to avoid the DANGER of key duplications. Stock: Ex Mayo Hardware warehouse. Ordering Process: No Special Ordering Requirements. Stock: Ex manufacturer 4-6 week lead time. Ordering Process: Special Ordering Requirements (Refer to below instructions). REGISTERED END USER SPECIAL ORDERING REQUIREMENT How do I register my End User? Simply arrange for your end user to complete the “MASTER LOCK KEY CHARTING REGISTRATION FORM” and forward with your official purchase order to Mayo Hardware Pty Ltd. -

Mul-T-Lock 2017 Price Catalog Mul-T-Lock High Security & Access Control Solutions
Mul-T-Lock 2017 Price Catalog Mul-T-Lock High Security & Access Control Solutions Effective January 1, 2017 TABLE OF CONTENTS Introduction 1 Large Format Interchangeable Cores 54 How to Order 4 Knob, Lever and Deadbolt Replacement Cylinders 55 Multiple Platforms – A Security Level for Every Need 6 Foreign Cylinders 65 MT5®+ Platform Introduction 7 Deadbolts & Deadlatches 68 Interactive®+ Platform Introduction 8 Grade 1 Hercular® Deadbolts 69 ClassicPro™ Platform Introduction 9 Hercular® Anti-Ligature & Latch Locks 72 Access Control, Keyless Entry & Smart Solutions 10 Grade 2 Cronus® Deadbolts 74 CLIQ® E-Cylinders & Smart Key Solutions 11 Locksets & Hardware 75 SMARTair® Access Control Solutions 17 Rim Locks 76 SMARTair® E-Motion Electronic Cabinet & Locker Locks 23 Mortise Locks 77 DONNA™ Multifamily and Hospitality 25 Lever & Knob Locks 78 Code-It™ Electronic Pushbutton Levers 27 Utility, Furniture & Retail Locks 80 KonnectLock™ (Formerly WatchLock™) 29 Padlocks 86 Traka® Key & Asset Management Solutions 32 ArmaD Locks 92 ENTR™ Smart Lock Solution 34 Mul-T-Lock Junior 95 GotU®+ Digital Door Viewers 37 Mul-T-Lock Parts 97 Yale® Real Living™ Residential Digital Locks 39 Cylinder Parts - Pins 100 Mul-T-Lock Keys, Keying Options & Services 41 Cylinder Parts 114 MT5®+ Keys & Cards 42 Hercular® Deadbolt Parts 152 Interactive®+ Keys & Cards 43 Anti-Ligature Deadbolt & Gate Latch Lock Parts 156 Old Interactive Keys 43 Top Guard® Parts 157 ClassicPro™ Keys & Cards 44 Utility & Furniture Lock Parts 158 Classic / Integrator® Keys & Cards 44 Padlock Parts 174 Services 46 Key Cutting Machine Parts 186 Machinery, Pinkits & Tools 47 Standard Ordering Form 190 Locksmith Tools 48 Master Keying Information 191 Cylinders 50 Key & Cylinder Maintenance 194 Mortise Cylinders 51 Warranty 196 Mogul Cylinders 51 Conditions of Sale 198 Rim Cylinders 53 Available Finishes 203 Established in 1973, Mul-T-Lock is a worldwide leader in the developing, manufacturing, and marketing of high security products for Institutional, Commercial, Industrial, and Residential customers.