Securing US Elections Against Cyber Threats
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Using HAVA Funds to Ensure Voters Can Safely Vote
Using HAVA Funds to Ensure Voters Can Safely Vote INTRODUCTION In the midst of the COVID-19 pandemic, for many people, voting may seem like a choice between exercising their constitutional right and protecting their own health and safety. Vote-by-mail early voting, safe polling place procedures, and other protections must be expanded to make sure no one has to make that choice. Making sure our elections are not only highly accessible, but reliable, will take significant resources. Election officials must purchase new equipment, hire additional staff, and rent extra space—all of which cost money that they may not have budgeted for this year. To meet these needs, the Federal Government has approved some additional funding—HAVA Funds—that local and state public officials can use to ensure everyone can vote safely this year. There is still a need for additional appropriations of federal funds to support state and local election administration in 2020. WHAT ARE HAVA FUNDS? The Help America Vote Act (HAVA) was established to help states reform and bolster their election processes. States can generally request HAVA funding to protect poll workers, staff, and voters. Beyond protection, expenditures can include training and recruitment of workers. Additionally, as a result of COVID-19, funds can be requested to support vote by mail costs, temporary staff, and equipment, as well as other costs. As of March 27, 2020, a combined $825,000,000 has been appropriated to HAVA via the Consolidated Appropriations Act of 2020 and the Coronavirus Aid, Relief, and Economic Security (CARES) Act.1 Each state (and D.C.) receives an amount of funding based on voter population, as explained in the “How Much is Allocated Via HAVA Funds?” section. -

The Qanon Conspiracy
THE QANON CONSPIRACY: Destroying Families, Dividing Communities, Undermining Democracy THE QANON CONSPIRACY: PRESENTED BY Destroying Families, Dividing Communities, Undermining Democracy NETWORK CONTAGION RESEARCH INSTITUTE POLARIZATION AND EXTREMISM RESEARCH POWERED BY (NCRI) INNOVATION LAB (PERIL) Alex Goldenberg Brian Hughes Lead Intelligence Analyst, The Network Contagion Research Institute Caleb Cain Congressman Denver Riggleman Meili Criezis Jason Baumgartner Kesa White The Network Contagion Research Institute Cynthia Miller-Idriss Lea Marchl Alexander Reid-Ross Joel Finkelstein Director, The Network Contagion Research Institute Senior Research Fellow, Miller Center for Community Protection and Resilience, Rutgers University SPECIAL THANKS TO THE PERIL QANON ADVISORY BOARD Jaclyn Fox Sarah Hightower Douglas Rushkoff Linda Schegel THE QANON CONSPIRACY ● A CONTAGION AND IDEOLOGY REPORT FOREWORD “A lie doesn’t become truth, wrong doesn’t become right, and evil doesn’t become good just because it’s accepted by the majority.” –Booker T. Washington As a GOP Congressman, I have been uniquely positioned to experience a tumultuous two years on Capitol Hill. I voted to end the longest government shut down in history, was on the floor during impeachment, read the Mueller Report, governed during the COVID-19 pandemic, officiated a same-sex wedding (first sitting GOP congressman to do so), and eventually became the only Republican Congressman to speak out on the floor against the encroaching and insidious digital virus of conspiracy theories related to QAnon. Certainly, I can list the various theories that nest under the QAnon banner. Democrats participate in a deep state cabal as Satan worshiping pedophiles and harvesting adrenochrome from children. President-Elect Joe Biden ordered the killing of Seal Team 6. -

Election Assistance Commission Plans for Use of CARES Act Report to the Pandemic Response Accountability Committee
Election Assistance Commission Plans for Use of CARES Act Report to the Pandemic Response Accountability Committee The Coronavirus Aid, Relief and Economic Security (CARES) Act provided $400 million to the Election Assistance Commission (EAC) to allocate to states, the District of Columbia and U.S. Territories “to prevent, prepare for, and respond to coronavirus, domestically or internationally, for the 2020 Federal election cycle.” Section 15011 of the Act requires federal agencies to provide their plans for using the funds to the Pandemic Response Accountability Committee. This document provides that information. The CARES Act provided the funds to EAC under Section 101 of the Help America Vote Act (HAVA) which authorizes EAC to provide funds to states to “improve the administration of federal elections.” Therefore, EAC followed the requirements of Section 101 to allocate the funds to the states to address issues arising from the pandemic during the remaining primaries and the general election in November 2020. (See Appendix A for the State Allocation Chart). EAC issued Notices of Grant Award and guidance to the states on April 6, meeting the requirement in the CARES Act to obligate the funds within 30 days of passage of the Act. States were required to describe their anticipated usage of the funds in their Funding Request Letters (See Appendix B for anticipated state usage of the funds.) In the guidance to the states, EAC provided the following list of allowable activities: • Printing of additional ballots and envelopes for potential -

IBLJ V.26 Summer2021 Draft
VOLUME 26 SUMMER 2021 ILLINOIS BUSINESS LAW JOURNAL RAGE AGAINST THE VOTING MACHINE: DOMINION’S DEFAMATION LAWSUIT AGAINST SIDNEY POWELL ❖ Article ❖ Dr. Michael Conklin* I. INTRODUCTION On January 8, 2021, Dominion Voting Systems, Inc., filed a defamation lawsuit against Sidney Powell.1 The 124-page complaint—drafted by the law firm of noted libel attorney Tom Clare—is based on Powell’s claims that Dominion rigged the 2020 presidential election.2 This Article examines the relevant issues of false statement of fact, damages, causation, and actual malice. Additionally, a unique privilege that may be available to Powell is considered. II. FALSE STATEMENT OF FACT Some of Powell’s statements could be dismissed as either opinion or partial truths. Her claim that “there’s no way there was anything but widespread election fraud”3 could be classified as opinion since the word “widespread” is highly subjective and “election fraud” can refer to different occurrences. Additionally, recounts in Georgia did find discrepancies in the originally reported totals.4 So in a literal sense, the exact vote tallies originally reported were incorrect. However, the discrepancies * Powell Endowed Professor of Business Law, Angelo State University. 1. Complaint, US Dominion, Inc. v. Powell, No. 1:21-cv-00040 (D.D.C. Jan. 8, 2021). 2. Id. 3. Id. at 26. 4. Joe Walsh, Recount Trims Biden’s Lead in Georgia by over 1,000 Votes, FORBES (Nov. 17, 2020, 5:37 PM), https://www.forbes.com/sites/joewalsh/2020/11/17/recount-trims-bidens-lead- in-georgia-by-over-1000-votes/?sh=4d9080df9b84. 1 Rage Against the Voting Machine [Vol. -
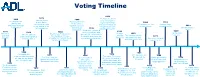
Voting Timeline
Voting Timeline 1922 1876 1865 1890 The Supreme Court Supreme Court rules that people of 13th Amendment: Wyoming becomes denies Native Japanese heritage 1964 1993 Slavery and the first state to th Americans the right and Asian Indians are 24 Amendment: Poll National Voter involuntary servitude legislate voting for 2013 to vote based on the ineligible to become taxes outlawed Registration Act is abolished th women in its Shelby County v. 14 Amendment 1918 naturalized citizens. constitution. World War I advanced Holder 1943 2002 1776 1868 1882 women’s suffrage and Chinese 1952 Help America White men 14th Amendment: The Chinese Exclusion Act granted U.S. citizenship for Exclusion The Immigration and Vote Act with land Citizenship is granted bars people of Chinese the Native Americans that 1971 Repeal Act Nationality Act and can vote to former slaves ancestry from naturalizing to served during World War I Age to vote lowered McCarran-Walter Act become U.S. citizens. from 21 to 18 1866 1961 Civil Rights Act: 1924 1877 23rd Amendment: 1984 All native-born Americans 1896 The Indian Citizenship Jim Crow Laws are DC can vote for 2006 are citizens, but do not Several southern Act grants citizenship to Voting Accessibility passed to keep African President Indiana becomes have the right to vote states pass Native Americans, but for the Elderly and Americans from voting the first state to "grandfather clauses" states pass various laws Handicapped Act 1863 pass Voter ID laws to prevent former to keep them from voting The Emancipation slaves and their 1965 2019 1945 2000 Proclamation was 1870 1887 descendants from 1920 Voting Rights Act: The Voting Rights World War II served as Residents in U.S. -

Case 1:10-Cv-06923-JSR Document 35 Filed 10/08/10 Page 1 of 3
Case 1:10-cv-06923-JSR Document 35 Filed 10/08/10 Page 1 of 3 UNITED STATES DISTRICT COURT THE SOUTHERN DISTRICT OF NEW YORK --------------------------------------------------------------X CONSERVATIVE PARTY OF NEW YORK STATE and WORKING FAMILIES PARTY, Civil Action No: Plaintiffs, 10-cv-6923 (JSR) - against - DECLARATION OF JOHN POULOS IN OPPOSITION NEW YORK STATE BOARD OF ELECTIONS; TO PLAINTIFFS’ MOTION JAMES A. WALSH, DOUGLAS A. KELLNER, FOR A PRELIMINARY EVELYN J. AQUILA, and GREGORY P. INJUNCTION____________ PETERSON, in their official capacities as Commissioners of the New York State Board of Elections; TODD D. VALENTINE and ROBERT A. BREHM, in their official capacities as Co-Executive Directors of the New York State Board of Elections, Defendants. --------------------------------------------------------------X JOHN POULOS, declares as follows: 1. I am the President of Dominion Voting System Corporation (hereinafter referred to as “Dominion”), and in such capacity am familiar with the facts and circumstances of the within proceeding. I have a degree in Electrical Engineering from the University of Toronto. I have 13 years’ experience in the hardware/software industry. I have held the position of President with Dominion for 8 years, and am very familiar with all of Dominion’s engineering efforts as it pertains to election equipment. As such, I am fully familiar with the Image Cast voting machines currently being used in the State of New York and which will be used in the upcoming election scheduled for November 2, 2010. 2. I submit this affidavit on behalf of defendants in opposition to plaintiffs’ Case 1:10-cv-06923-JSR Document 35 Filed 10/08/10 Page 2 of 3 motion for a preliminary injunction for an order enjoining the Board’s practice, in accordance with Election Law §9-112(4), of crediting a “double vote” for a single candidate to the candidate’s party line which appears first on the ballot. -

IN the UNITED STATES DISTRICT COURT for the DISTRICT of COLUMBIA US DOMINION, INC., DOMINION VOTING SYSTEMS, INC., and DOMINION
Case 1:21-cv-02130-CJN Document 1 Filed 08/10/21 Page 1 of 213 IN THE UNITED STATES DISTRICT COURT FOR THE DISTRICT OF COLUMBIA ) US DOMINION, INC., DOMINION ) VOTING SYSTEMS, INC., and ) DOMINION VOTING SYSTEMS ) CORPORATION ) c/o Cogency Global ) 1025 Vermont Ave, NW, Ste. 1130 ) Washington, DC 20005, ) ) Plaintiffs, ) ) v. ) Case No. ) HERRING NETWORKS, INC., d/b/a ) ONE AMERICA NEWS NETWORK ) 101 Constitution Ave., NW ) Washington, DC 20001, ) ) CHARLES HERRING ) 17353 Circa Oriente ) Rancho Santa Fe, California 92067, ) ) ROBERT HERRING, SR. ) 4289 Rancho Las Brisas Trail ) San Diego, California 92130, ) ) CHANEL RION ) 3211 Cherry Hill Lane, NW ) Washington, DC 20007, ) ) and ) ) CHRISTINA BOBB ) 565 Pennsylvania Ave., NW ) Apt. 803 ) Washington, DC 20001, ) ) Defendants. ) ) Case 1:21-cv-02130-CJN Document 1 Filed 08/10/21 Page 2 of 213 COMPLAINT AND DEMAND FOR JURY TRIAL April 18, 2021: “‘The majority of people [at OAN] did not believe the voter fraud claims being run on the air.’ . Mr. Golingan, the producer, said some OAN employees had hoped Dominion would sue the channel. ‘A lot of people said, “This is insane, and maybe if they sue us, we’ll stop putting stories like this out,”’ he said.” Former OAN Producer Marty Golingan, quoted in the New York times, and fired by OAN the day after the statements were published 1. On the actual facts, the November 2020 election was a huge success for Dominion. In jurisdiction after jurisdiction, in 28 states, in the midst of a highly disruptive pandemic, Dominion’s voting machines facilitated efficient and reliable voting with accurate tallying of votes. -

The State of the Right to Vote After the 2012 Election
S. HRG. 112–794 THE STATE OF THE RIGHT TO VOTE AFTER THE 2012 ELECTION HEARING BEFORE THE COMMITTEE ON THE JUDICIARY UNITED STATES SENATE ONE HUNDRED TWELFTH CONGRESS SECOND SESSION DECEMBER 19, 2012 Serial No. J–112–96 Printed for the use of the Committee on the Judiciary ( U.S. GOVERNMENT PRINTING OFFICE 81–713 PDF WASHINGTON : 2013 For sale by the Superintendent of Documents, U.S. Government Printing Office Internet: bookstore.gpo.gov Phone: toll free (866) 512–1800; DC area (202) 512–1800 Fax: (202) 512–2104 Mail: Stop IDCC, Washington, DC 20402–0001 COMMITTEE ON THE JUDICIARY PATRICK J. LEAHY, Vermont, Chairman HERB KOHL, Wisconsin CHUCK GRASSLEY, Iowa DIANNE FEINSTEIN, California ORRIN G. HATCH, Utah CHUCK SCHUMER, New York JON KYL, Arizona DICK DURBIN, Illinois JEFF SESSIONS, Alabama SHELDON WHITEHOUSE, Rhode Island LINDSEY GRAHAM, South Carolina AMY KLOBUCHAR, Minnesota JOHN CORNYN, Texas AL FRANKEN, Minnesota MICHAEL S. LEE, Utah CHRISTOPHER A. COONS, Delaware TOM COBURN, Oklahoma RICHARD BLUMENTHAL, Connecticut BRUCE A. COHEN, Chief Counsel and Staff Director KOLAN DAVIS, Republican Chief Counsel and Staff Director (II) C O N T E N T S STATEMENTS OF COMMITTEE MEMBERS Page Coons, Hon. Christopher A., a U.S. Senator from the State of Delaware ........... 6 Durbin, Hon. Dick, a U.S. Senator from the State of Illinois .............................. 4 Grassley, Hon. Chuck, a U.S. Senator from the State of Iowa ............................ 3 Leahy, Hon. Patrick J., a U.S. Senator from the State of Vermont .................... 1 prepared statement .......................................................................................... 178 Whitehouse, Hon. Sheldon, a U.S. Senator from the State of Rhode Island ..... -

The Help America Vote Act
THE HELP AMERICA VOTE ACT In response to the problems during the presidential elections of 2000, Congress passed the Help America Vote Act (“HAVA”) mandating significant changes in virtually every aspect of election administration. If HAVA is implemented properly in the 50 states, many provisions of the law hold great promise to improve the nation’s outdated voting procedures. HAVA’s new identification requirements, however, may severely threaten voters’ rights, particularly if implemented improperly. Ensuring that HAVA successfully promotes voting rights is complicated by the fact that the federal government left implementation almost entirely in the hands of the states. States have great latitude in how they meet HAVA’s minimum requirements, and they have the authority to institute idiosyncratic requirements that pose new barriers to voting. Advocates, concerned citizens, policy makers and election officials should maximize the opportunity offered by HAVA to improve the electoral process, while vigorously safeguarding voting rights. HAVA’s Key Provisions Voting Machines and Systems1 • HAVA authorizes federal funding for states to upgrade voting machines. States that accept this funding must eliminate and replace all punch card and lever voting machines, unless the machines can be adapted to meet heightened standards to ensure reliability, improved access for voters with disabilities and limited English proficiency, and other new federal requirements.2 • Voting machines must provide voters with an opportunity to privately and independently verify, change or correct the ballot before it is cast and counted. • States must ensure that at least one voting machine at every polling place meets enhanced requirements for accessibility for voters with disabilities. -

Election Fraud Facts & Details
Election Fraud Facts & Details Supporting Files for all items listed can be found at the following URL: https://ufile.io/by3q159v 1 FOREIGN INFLUENCE & NATIONAL SECURITY CONCERNS IN US ELECTIONS 1.1 The core software utilized by Dominion, the 2nd largest US voting machine vendor, originates from intellectual property of Smartmatic; a company that was founded in communist Venezuala with links to Chavez. A. Smartmatic Ties to Hugo Chávez Warned About in 2006 B. SmartMatic Sells Sequoia Voting Systems to US Holding Company After CFIUS Probe C. Sequoia Admits that while they can change the source code (e.g. Software), Smartmatic still owns the intellectual property of the software. D. Dominion Buys Sequoia from Smartmatic and Diebold from ES&S 1.2 ES&S, Dominion, and Hart Intercivic represent 92% of voting machine market and have a long history of significant security vulnerabilities that could be exploited by a nation state in ways that would be difficult to detect. E. Map - Voting Machine Usage in the US F. Defcon 27 - Voting Machine Hacking Village - Vulnerablity Report G. Defcon 26 - Voting Machine Hacking Village - Vulnerablity Report.pdf H. History of ES&S and Diebold (Now Dominion) Vulnerabilities and Voting Inconsistiencies I. Antrim-Michigan-Forensics-Report-121320-v2-Redacted 1.3 An affidavit and scholarly statistical paper attest to Smartmatic rigging Venezualian elections. Smartmatic has also been accused of rigging elections in the Philippines and India J. Venezuala Smartmatic Affidavit K. Statistical Science - 2011 - Volume 26 - Number 4 - Analysis of the 2004 Venezuala Referendum - Official Results Verses the Petition Signatures L. Smartmatic Voting Technology Firm Linked to Alleged Fraud in Elections in Philippines, Venezuela M. -

The Help America Vote Act and Election Administration: Overview and Selected Issues for the 2016 Election
The Help America Vote Act and Election Administration: Overview and Selected Issues for the 2016 Election Arthur L. Burris, Coordinator Section Research Manager Eric A. Fischer Senior Specialist in Science and Technology October 18, 2016 Congressional Research Service 7-5700 www.crs.gov RS20898 The Help America Vote Act and Election Administration: Overview for 2016 Summary The deadlocked November 2000 presidential election focused national attention on previously obscure details of election administration. Congress responded with the Help America Vote Act of 2002 (HAVA; P.L. 107-252). HAVA created the Election Assistance Commission (EAC), established a set of election administration requirements, and provided federal funding, but it did not supplant state and local control over election administration. Several issues have arisen or persisted in the years since HAVA was enacted. Some observers have criticized the EAC for being obtrusive, slow, ineffectual, or even unnecessary. Others believe that the agency is an important resource for improving the election administration. The EAC lacked a quorum of commissioners between 2011 and 2015. HAVA requires computerized state voter registration systems, and its voting-system requirements promote the use of electronic voting systems. However, those systems, especially the kinds that record votes directly into a computer’s memory (DREs), raise concerns about security and reliability. In response, many states have enacted requirements for paper ballot records that can be verified by the voter and used in recounts. All states now use paper-based optical scan systems for at least some voters, and most use them in at least some polling places. DRE systems are also used in most states, in many cases to meet HAVA accessibility requirements, but in several states to serve as the primary voting system in at least some jurisdictions. -

The Help America Vote Act and Election
The Help America Vote Act and Election Administration: Overview and Issues name redacted Analyst in Elections name redacted Senior Specialist in Science and Technology September 22, 2015 Congressional Research Service 7-.... www.crs.gov RS20898 The Help America Vote Act and Election Administration: Overview and Issues Summary The deadlocked November 2000 presidential election focused national attention on previously obscure details of election administration. Even before the U.S. Supreme Court had resolved the election in December, numerous bills to address the failings of the election system were introduced in Congress and state legislatures. The response at the federal level was the Help America Vote Act (HAVA; P.L. 107-252), enacted in 2002. HAVA created the Election Assistance Commission (EAC), established a set of election administration requirements, and provided federal funding, but did not supplant state and local control over election administration. Several issues have arisen or persisted in the years since HAVA was enacted. This report provides background information about HAVA and its provisions, the EAC, funding for the agency and for state programs to improve elections, and a number of enduring election administration issues. Some observers have criticized the EAC for being too obtrusive, or for being slow, ineffectual, or even unnecessary. Others believe that the agency is an important resource for improving the administration of elections and has been hampered by budgetary constraints and difficulties in the nomination process for commissioners. The agency was without commissioners from December 2011 to January 2015, when one Democratic and two Republican commissioners were sworn in. They had previously been confirmed by the Senate on December 16, 2014.