Blockchains How Crypto-Currencies Work
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Blockchain and the Creative Industries: Provocation Paper © Ellie Rennie, Jason Potts and Ana Pochesneva, 2019
Provocation Paper Blockchain and the Creative Industries Ellie Rennie, Jason Potts, Ana Pochesneva RMIT Blockchain Innovation Hub November 2019 This provocation paper has been prepared at the request of the Australia Council for the Arts, Screen Australia and the Australian Film, Television and Radio School. Table of contents Executive Summary .................................................................................................................................3 Introduction .................................................................................................................................................4 1 The creative industries today ...........................................................................................................5 1.1 Policy responses to date ..................................................................................................................5 1.2 Challenges facing creative practitioners ................................................................................5 1.2.1 Time factors ......................................................................................................................................6 1.2.2 Business skills ...................................................................................................................................6 1.2.3 Disintermediation ...........................................................................................................................6 1.3 Environment .........................................................................................................................................7 -

COTW: Punks & Dunks: NFT Volumes Soar
COTW: Punks & Dunks: NFT Volumes Soar After a frenzied but brief start to the year, NFTs have come roaring back in recent weeks, with record sales volumes, soaring corporate and venture investment, and a general re-entry into the cultural zeitgeist. We review NFT basics, analyze recent trends, and posit what the future may hold in this week’s Chart of the Week. ● NFT Overview: Fungibility is the characteristic of mutual interchangeability, where one is indifferent as to which exact unit one has, and examples include US dollars, gold, and airline points. Non-fungible items, by contrast, are those that are solely unique and therefore not freely interchangeable, such as an original painting, land, and baseball cards. Non-fungible tokens (NFTs) are unique digital assets that are stored on a blockchain (well, technically an ID number in a smart contract that points to the URL of a JSON metadata file is what is stored on the blockchain). As blockchain-based digital representations of ownership, NFTs bear typical cryptocurrency benefits, such as immutability, provable scarcity and provenance, standardization and interoperability, and programmability, and they make digital assets as real and as permanent as objects in the physical world. NFTs can represent ownership in unique items of value like digital art, domain names, intellectual property, and event tickets, can be employed in a variety of use cases like collectibles, gaming, media, music, and finance, and in the future will usher in new paradigms around content, ownership, value, and exchange. ● NFT History: Developers first began experimenting with NFTs through colored coins on the Bitcoin network in 2012, followed by Rare Pepe illustrations a few years later. -

NFT Yearly Report 2020, Fresh from the Oven!
NON-FUNGIBLE TOKENS YEARLY REPORT 2020 FREE EDITION MARKET RESEARCH. TRENDS DECRYPTION. PROJECT REVIEW. EVERYTHING YOU NEED TO KNOW ABOUT THE NFT ECOSYSTEM FOREWORDS The NFT Yearly Report 2020, fresh from the oven! The purpose of this report is to provide an overarching and detailed view of the Non-Fungible Token ecosystem during 2020. The exponential growth within the sector has been particularly impressive, especially given that the Crypto bear market was in full force during most of the early stages of development. There is little doubt that the loyal and tight knit groups who initially evolved around various NFT blockchain projects have since seen the contents of their wallets dramatically increase in value as the ecosystem evolved and NFT projects began to attract more and more outside and mainstream interest. This report is not meant for Non-Fungible experts but to help everyone in or outside the Non- Fungible Tokens ecosystem to better understand what is going on. What is the potential? Why should you care about NFT? 2020 has been an unprecedented year for most of the world's population, with many challenges to face, from a global pandemic and lockdown to political upheavals, riots and not to mention catastrophic natural disasters… we’ve had it all! In stark contrast and perhaps partially due to such turbulent global events, interest and investment in virtual economies and digital assets has boomed, more than ever seen before. Within the Non-Fungible Token ecosystem individual sectors have seen success, Art, Gaming and Digital Assets have all gained remarkable traction during 2020 with this once niche and experimental industry maturing into a force to be reckoned with. -

The Anti-Money Laundering Act and Crypto Collide: Non-Fungible Tokens
MAY 18, 2021 The Anti-Money Laundering Act For more information, contact: and Crypto Collide: Non-Fungible Katherine Kirkpatrick Tokens +1 312 764 6918 [email protected] Matthew B. Hanson As NFTs gain popularity, buyers and sellers should +1 202 626 2904 [email protected] consider the potential issues related to federal anti- Daniel R. Kahan money laundering laws. +1 202 626 9280 [email protected] While non-fungible tokens (“NFTs”) have existed for several years, the Steven J. Rizzi market for NFTs grew considerably during 2020 and into 2021, as a number +1 212 556 2269 of high-profile NFT sales grabbed headlines and well-known brands and [email protected] organizations began exploring the use of NFTs. Amid this continued growth Luke Roniger in adoption, and the expanding range of use cases, industry participants +1 512 457 2044 should make sure they are aware of the legal implications for issuing, [email protected] purchasing, and trading these new assets. Read Mills For now, existing laws and regulations will likely be applied to promote +1 202 626 2921 transparency and to address several aspects of NFTs, including the [email protected] potential investment value, the risk of speculation and volatile pricing, and potentially anonymous market participants. This article, which is the first in a multi-part series highlighting the legal and regulatory implications King & Spalding surrounding NFTs, explores the current state of play, potential risks, and Chicago, IL likely regulatory developments relating to NFTs and federal anti-money 110 N Wacker Drive laundering laws. Suite 3800 Chicago, IL 60606 WHAT ARE NFTs? Washington, D.C. -

Design Patterns for Smart Contracts in the Ethereum Ecosystem
Design Patterns for Smart Contracts in the Ethereum Ecosystem Maximilian Wohrer¨ and Uwe Zdun University of Vienna Faculty of Computer Science Wahringerstraße¨ 29, 1090 Vienna, Austria Email: fmaximilian.woehrer,[email protected] Abstract—The idea to digitally facilitate contract law and it is crucial that their implementation is correct and secure business practices through computer programs has led to the against attacks. Given these points, it is beneficial to have a notion of smart contracts. Today’s most prominent smart contract solid foundation of established design and coding guidelines ecosystem is Ethereum, a blockchain based distributed computing platform. Due to the inherent nature of blockchain based contract that promote the creation of correct and secure smart contracts, execution, missing low level programming abstractions, and the for example in the form of design patterns. Design patterns constant evolution of platform features and security considera- [1, 2] are a commonly used technique to encode design guide- tions, writing correct and secure smart contracts for Ethereum is lines or best practices. They express an abstract or conceptual a difficult task. Based on a Multivocal Literature Research and solution to a concrete, complex, and reoccurring problem. So an analysis of the gathered data based on qualitative research methods, we mined a number of design patterns providing design far, design patterns have not received a lot of attention in guidelines. We describe those patterns in detail and provide Ethereum research and information on Solidity design and exemplary code for better illustration. Our research shows that coding guidelines is scattered among different sources. In the patterns are widely used to address application requirements previous work [3] we have gathered security related design and common problems. -
![Eth Classic Price Forecast Update [06-07-2021] to Predict the Future of This Coin and Invest Likewise for Better Returns](https://docslib.b-cdn.net/cover/4431/eth-classic-price-forecast-update-06-07-2021-to-predict-the-future-of-this-coin-and-invest-likewise-for-better-returns-1744431.webp)
Eth Classic Price Forecast Update [06-07-2021] to Predict the Future of This Coin and Invest Likewise for Better Returns
1 Eth Classic Price Forecast Update [06-07-2021] To predict the future of this coin and invest likewise for better returns. Being an open-source blockchain, it features smart contract functionalities. Ethereum is a decentralized system that is fully autonomous. Ethereum CryptoPunks Are Selling for Outrageous Sums of Money. But critics aren t impressed. A CryptoPunk sold this morning for over 136,000. Such sales are a big step for the relatively small NFT sector, which accounts for less than 2 of the entire crypto market. The Story of the Constantinople Upgrade. Its purpose is to support the eventual transition away from Proof of Work towards Proof of Stake. This is the second time in Ethereum s history when block rewards have been reduced. With an average block time of. 2 cryptocurrency continuing to lead the market. The mid-caps were able to perform the best this week, and this is likely due to the mechanics of capital flow in crypto. The crypto market has been on fire lately, and we ve seen an explosive altseason thus far. To predict the future of this coin and invest likewise for better returns. Being an open-source blockchain, it features smart contract functionalities. Ethereum is a decentralized system that is fully autonomous. Ethereum CryptoPunks Are Selling for Outrageous Sums of Money. But critics aren t impressed. A CryptoPunk sold this morning for over 136,000. Such sales are a big step for the relatively small NFT sector, which accounts for less than 2 of the entire crypto market. The Story of the Constantinople Upgrade. -

Blockchain, Crypto and Nfts Are the Risky ‘Next Generation of Value Creation’ in Sports
4/3/2021 Blockchain, Bitcoin and NFTs are the risky 'next generation of value creation' in sports – The Athletic Blockchain, crypto and NFTs are the risky ‘next generation of value creation’ in sports By Bill Shea (/author/bill-shea/) Mar 30, 2021 135 Joining terms such as Wins Above Replacement and Player Efficiency Rating in the sports lexicon are phrases such as non-fungible token (NFT), blockchain and cryptocurrency. The language of Silicon Valley entered the sports industry this year on the back of the white- hot sports collectibles market (https://theathletic.com/2428346/2021/03/05/sports-cards- tom-brady-luka-doncic-andre-the-giant/) because of the enormous sums of money involved. Why? Simple: In an era with little or no in-game fan revenue because of pandemic health- safety protocols, concepts such as NFTs and blockchain are viewed by leagues, teams, owners and athletes as opportunities to make more money. https://theathletic.com/2484646/2021/03/30/bitcoin-crypto-nfts-ethereum-sports-business/ 1/45 4/3/2021 Blockchain, Bitcoin and NFTs are the risky 'next generation of value creation' in sports – The Athletic Fans can expect to see a growing wave of NFT promotions — would you value a bobblehead that exists solely on your iPhone? — and the possibility that future re-sale of tickets will occur on a blockchain that allows the team to get another cut of money. While the technology has been around for years, it’s only in the past couple of months that it’s widely entered both sports and the broader national culture. -

Coinpayments Digest 08/2021
I S S U E 8 / 2 0 2 1 W E E K 1 5 / 0 2 - 2 2 / 0 2 CoinPayments Digest weekly review of the most notable news and events in the cryptocurrency, payments & fintech industries IN THIS ISSUE Binance Coin becomes the third-largest crypto following parabolic rally Over $100M in crypto collectible NFTs sold in last 30 days Bitcoin Secures a $1 Trillion Market Cap for First Time Ever Tesla Has Already Profited More From $1.5 Billion Bitcoin The price of Bitcoin (BTC) has reached a new all-time high over Buy Than 2020 Car Sales $58,000, over the weekend pushing the coin’s total market capitalization above $1 trillion, according to crypto metrics platform CoinGecko. Market capitalization is the total number of coins currently in circulation multiplied by their current Janet Yellen Calls Bitcoin a market price—basically, the combined worth of all existing BTC. By various estimations, the value of all money in the ‘Highly Speculative Asset’ world is around $95 trillion—and now Bitcoin represents about 1% of that. While it’s not totally fair to compare Bitcoin to money (it can be seen as an asset instead), it provides one way to put it in perspective. Bitcoin’s (BTC) price has been grinding up nicely over the past few weeks, but the past 24 hours have seen a Football fan tokens on the significant correction. BTC price dropped by over $10,000 from march as Poland’s biggest $58,000 to under $48,000 birefly, a correction of almost 20%. -

Cryptokitties and the New Ludic Economy : How Blockchain Introduces Value, Ownership, and Scarcity in Digital Gaming
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Osuva This is a self-archived – parallel published version of this article in the publication archive of the University of Vaasa. It might differ from the original. CryptoKitties and the new ludic economy : how blockchain introduces value, ownership, and scarcity in digital gaming Author(s): Serada, Alesja; Sihvonen, Tanja; Harviainen, J. Tuomas Title: CryptoKitties and the new ludic economy : how blockchain introduces value, ownership, and scarcity in digital gaming Year: 2020 Version: Accepted manuscript Copyright ©2020 the author(s), licensee SAGE Publications. The article is protected by copyright and reuse is restricted to non- commercial and no derivative uses. Users may also download and save a local copy of an article accessed in an institutional repository for the user's personal reference. Please cite the original version: Serada, A., Sihvonen, T., & Harviainen, J.T. (2020). CryptoKitties and the new ludic economy : how blockchain introduces value, ownership, and scarcity in digital gaming. Games and culture. https://doi.org/10.1177/1555412019898305 CryptoKitties and the New Ludic Economy: How blockchain introduces value, ownership, and scarcity in digital gaming Abstract This article analyzes specific characteristics of value created through digital scarcity and blockchain-proven ownership in cryptogames. Our object of study is CryptoKitties, the first instance of a blockchain-based game that has garnered media recognition and financial interest. The objective of this article is to demonstrate the limits of scarcity in value construction for owners of CryptoKitties tokens, manifested as breedable virtual cats. Our work extends the trends set out by earlier cryptocurrency studies from the perspective of cultural studies. -

Nfts Conquer the Art Market
NFTs conquer the art market March 11, 2021 will go down in art history as a memorable date. A world record for digital art was set twice: first, the transac=on of a CryptoPunk worth US$ 8 million and, on the same day, the auc=on of Beeple's (aka Mike Winkelmann) "The First 5000 Days" at CHRISTIE's for US$ 69 million, which the Singapore-born collector known by the pseudonym Metakovan bought for his Crypto Fund Metapurse. Basically, it contains 5000 digital images created by the ar=st over the period of more than 13 years. Comparable to On Kawara, the ar=st consistently created an image every day and posted them on Instagram. Thus, Beeple instantly became one of the most expensive contemporary ar=sts of our =me. (Beeple, The First Emoji, 1-Sep-20) What makes the rise of the digital art market so special is a revolu=onary new technology, namely the NFT (non-fungible token). An NFT embodies digital ownership of an artwork stored in the cloud server and is secured via the blockchain. Actually, you only own a token that you have in a digital wallet. Unlike bitcoin or other cryptocurrencies, NFTs are not exchangeable. This technology makes it possible to securi=ze ownership of a digital artwork. Via so-called smart contracts, further rights such as ar=st royal=es on resale or other rights of use and copyright can also be specified in it as code. The majority of NFTs are traded on online sales plaaorms such as OpenSea, Rarible, Superrare or Niby Gateway. -

Q1 2021 Coingecko Crypto Report
CoinGecko Q1 2021 Cryptocurrency Report Index Founders’ Note 3 - Q1 2021 DeFi Exploits Market Landscape 4 Non-Fungible Tokens (NFTs) 32 - Q1 2021 Spot Markets Overview - NFT Hype is Real - Q1 2021 Top-5 Crypto Returns - NFT Categories - Q1 2021 Top-30 Coins Dominance - NFT Landscape - Q1 2021 Top-5 Stablecoins - NFT Marketplaces - NFT x DeFi Bitcoin Analysis 10 - NFT Goes Mainstream: Big Brands Riding the NFT Waves - Bitcoin Price vs. Trading Volume - High-Profile NFT Sales - Bitcoin Price Cycle 2016-2017 vs. 2020-2022 Exchanges 42 - Price Returns: Bitcoin vs. Major Asset Classes - Q1 2021 Top-10 Cryptocurrency Exchanges - Bitcoin Treasuries in Public Traded Companies in 2021 - Q1 2021 Top-10 Centralized Exchanges (CEX) - Market Capitalization: Bitcoin vs. Gold vs. Top-5 S&P 500 Q1 2021 Top-10 Decentralized Exchanges (DEX) Stocks - - Q1 2021 Derivatives Exchanges – Bitcoin Perpetual Swaps 16 DeFi Analysis Volume - Q1 2021 DeFi Overview - Q1 2021 Derivatives Exchanges – Bitcoin Perpetual Swaps - Q1 2021 DeFi Price Returns Open Interest - An Introduction to the DeFi Ecosystem CoinGecko Highlights 48 - An Introduction to Ethereum Killers - CoinGecko Premium and Premium+ - Binance Smart Chain - Directly adding tokens to MetaMask - Terra - Bitcoin Treasury Page - Redefining Algo-Stables - Categories Ranking Page - The Rise and Fall of Algo-Stablecoins - Mobile App: New Multi-Portfolio Management - New Algorithmic Contenders - 'How to Bitcoin' Book - An Introduction to Ethereum Scaling Solutions Analysts: Erina Azmi Lucius Fang Win Win Benjamin Hor Karmen Lee CoinGecko Q1 2021 Cryptocurrency Report 2 Founders’ Note Financial bubbles are indistinguishable from the adoption of new technology. The total crypto market capitalization continues to surge higher in Q1 2021 with no ceiling in sight. -
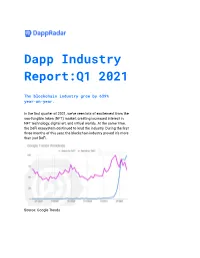
Dapp Industry Report:Q1 2021
Dapp Industry Report:Q1 2021 The blockchain industry grew by 639% year-on-year. In the first quarter of 2021, we’ve seen lots of excitement from the non-fungible token (NFT) market, creating increased interest in NFT technology, digital art, and virtual worlds. At the same time, the DeFi ecosystem continued to lead the industry. During the first three months of this year, the blockchain industry proved it’s more than just DeFi. Source: Google Trends High Ethereum gas prices continued to be an issue for all verticals. Multiple DeFi, NFT, and game dapps announced their expansion to other chains. The dominant narrative in the sector remained the emergence of the multichain paradigm. Ethereum contenders were active as ever. Binance Smart Chain (BSC) proved to be the largest competitor to Ethereum during Q1. Several top DeFi dapps moved or announced an expansion to BSC. NFT and game dapps were more in favor of choosing Polygon or Flow. The first quarter of 2021 was marked with record-high sales in the NFT market. Both new and existing NFT projects hit unseen sales. While the highest transaction volume was generated by NBA Top Shot, the most memorable was an art piece by Beeple which was sold for more than $69 million. Finally, the Ethereum DeFi ecosystem remained the largest in terms of total value locked (TVL), doubling its TVL in the first three months of 2021. On the other hand, the BSC DeFi ecosystem TVL grew 30 times during the same timeframe. Key takeaways ● The blockchain industry grew by 639% year-on-year, reaching 458,000 daily unique active wallets across all chains in Q1 2021.