PURCHASING/PAYABLE FRAUD Managing Billing Schemes
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Principles of MICROECONOMICS an Open Text by Douglas Curtis and Ian Irvine
with Open Texts Principles of MICROECONOMICS an Open Text by Douglas Curtis and Ian Irvine VERSION 2017 – REVISION B ADAPTABLE | ACCESSIBLE | AFFORDABLE Creative Commons License (CC BY-NC-SA) advancing learning Champions of Access to Knowledge OPEN TEXT ONLINE ASSESSMENT All digital forms of access to our high- We have been developing superior on- quality open texts are entirely FREE! All line formative assessment for more than content is reviewed for excellence and is 15 years. Our questions are continuously wholly adaptable; custom editions are pro- adapted with the content and reviewed for duced by Lyryx for those adopting Lyryx as- quality and sound pedagogy. To enhance sessment. Access to the original source files learning, students receive immediate per- is also open to anyone! sonalized feedback. Student grade reports and performance statistics are also provided. SUPPORT INSTRUCTOR SUPPLEMENTS Access to our in-house support team is avail- Additional instructor resources are also able 7 days/week to provide prompt resolu- freely accessible. Product dependent, these tion to both student and instructor inquiries. supplements include: full sets of adaptable In addition, we work one-on-one with in- slides and lecture notes, solutions manuals, structors to provide a comprehensive sys- and multiple choice question banks with an tem, customized for their course. This can exam building tool. include adapting the text, managing multi- ple sections, and more! Contact Lyryx Today! [email protected] advancing learning Principles of Microeconomics an Open Text by Douglas Curtis and Ian Irvine Version 2017 — Revision B BE A CHAMPION OF OER! Contribute suggestions for improvements, new content, or errata: A new topic A new example An interesting new question Any other suggestions to improve the material Contact Lyryx at [email protected] with your ideas. -

Defining Assets When Purchasing an Existing Business By: Evan L
Defining Assets When Purchasing An Existing Business By: Evan L. Randall, Esq. and Jessica A. Neville, Esq. Thousands of businesses are purchased every year. The motivations for purchasing a business are as varied as the number of buyers: to expand the buyer’s existing business with a similar operation or to create new opportunities through a complimentary business. Perhaps the buyer seeks to change careers or add income to an existing one. And there is always the notion that buying an existing business avoids some of the risk associated with opening a new business. Business purchases are typically structured in one of two ways: a stock transfer or an asset purchase. A stock purchase involves buying the stock (or membership interest) of the company that owns the business. Typically, liabilities are assumed as well. An asset purchase involves just the assets of a company. In either format, determining what is being acquired is critical. This article focuses on some of the important categories of assets to consider in a business purchase: real estate, personal property, and intellectual property. Real Estate For many businesses (especially retail and restaurants) the real estate may be the most substantial asset. The seller either owns or leases the property, and there are different considerations for each alternative. If real estate is part of the sale, it will likely represent the bulk of the purchase price. If the business operates in leased premises, the seller would assign the lease to the buyer, and it is very likely that the landlord will need to consent to the assignment. -

Purchasing and Supply Chain Management 1 : Section 1
The Strategic Context for Competent Procurement 1. Introduction This study note is set in the context of the examination of those elements in the organisation that either have a significant impact on purchasing and supply management strategies or thinking and approaches that can make significant contributions to corporate strategy and the achievement of overall organisational corporate objectives. This section of module A attempts to examine the facets of organisational and business level strategy and seeks to set them in the context of purchasing and supply chain management in respect of their ability to aid or facilitate effectiveness and competence for the organisation. 2. Strategic Context Strategy is a very wide subject; there are many aspects to consider in the development of strategies and in making strategic decisions. No single definition exists for the term ‘strategy’. An investigation of the meaning of strategy has provided a summary of some of the definitions found in various texts: “ Strategy is not a detailed plan or program of instructions; it is a unifying theme that gives coherence and direction to the actions and decisions of an individual or organisation.” Grant 1998. A strategy according to this author is a plan for deploying resources in order to gain a better position for instance, competitively in the market. Strategy also can define what business the company is in or is to be in and the kind of company it is or is to be. “ What business is all about is . competitive advantage . .. The sole purpose of strategic planning is to enable a company to gain as efficiently as possible, a sustainable edge over its competitors. -

Commodity Lead Buyer Department: Purchasing Reports To
Position Description Job Title: Commodity Lead Buyer Department: Purchasing Reports to: Corporate Purchasing Manager Location: Greenfield, IN Prepared by: Corporate Purchasing Manager Approved By: Engineering & Purchasing Director Approval Date: April 15, 2016 SUMMARY Work closely with internal stakeholders and external suppliers to develop and implement strategic commodity plans for all assigned categories at the lowest total cost. This includes the development and coordination of key procurement strategies with the tactical/logistical buying team. ESSENTIAL DUTIES AND RESPONSIBILITIES • Lead the development of and execution of category management strategies for all assigned categories/commodities • In line with strategic objectives, lead the negotiations to select, appoint and steer a supply base that progresses the company objectives on quality, cost, delivery and innovation • Work with internal stakeholders to define requirements for sourcing objectives • Evaluate competitive offers and present sourcing options that meet business requirements • Partner with Global Category Leads on global sourcing projects • Ensure all selected suppliers are compliant to service level agreements • Lead the category and supplier spend management activities with respective spend areas • Conduct in depth cost and spend analysis in order to develop cost savings initiatives through various cost reduction options • Carry out administrative responsibilities that effectively manage projects and contracting activities • Lead and expedite vendor selection and purchasing decisions through appropriate competitive bid and strategic sourcing processes (leverage practices, bundling tools, etc) • Achieve all cost reduction savings targets • Monitor, manage and report on achievements on key purchasing indicators in line with department requirements • Immediately respond to unforeseen supply failures, working with manufacturing and supplier to avoid supply chain interruptions. Modernfold, Inc. -

Procurement Vs Purchasing: What Is the Difference?
Procurement vs Purchasing: What Is The Difference? Mark Twain said, “The difference between the almost right word and the right word is really a large matter—it’s the difference between the lightning bug and the lightning.” While purchasing may get materials in the door, professional procurement strategies can reduce a company’s purchase spend by an average of 8 to 12 percent per year, significantly impacting liquidity. Knowing the difference between procurement and purchasing pays off. https://planergy.com/blog/procurement-vs-purchasing/ 1 / 8 What is Purchasing? Purchasing is a simple transaction, when companies pay for and receive goods or services. Purchasing can be considered a subset of procurement. For a small business with no procurement department, this may mean a phone call to an office supply store when the supply of pens runs low or a new computer is needed. Small businesses often lack the purchasing power of a major enterprise and have no leverage with which to negotiate. A simple purchasing process is generally performed on a transactional basis with little strategy: 1. Placing the order Without strategy, goods and services are ordered as needed. Reactive purchasing comes with a host of money-wasting issues. Businesses that buy on demand without approved purchase orders (PO) typically lack oversight and budget control. 2. Supplier communications Most companies have a established list of suppliers they work with to purchase supplies. 3. Receiving of goods or services Purchasing requires receipt of goods and services. Good purchasing strategy includes protocols for recording and tracking purchases. https://planergy.com/blog/procurement-vs-purchasing/ 2 / 8 4. -

Accounts Payable Policy University of Iowa Purchasing Department Cover | Page
Payment Processing for Purchase Order Invoices Contents Payment Process ............................................................................................................................................................................... 1 Invoices ............................................................................................................................................................................................. 1 Invoice Number ...................................................................................................................................................................................... 1 Short Payments ...................................................................................................................................................................................... 1 Credit Memos ........................................................................................................................................................................................ 2 Voucher Reports ................................................................................................................................................................................ 2 Adjustment Voucher .............................................................................................................................................................................. 2 Delinquent Voucher Reports ................................................................................................................................................................. -

Roswell Purchasing Policy
PURCHASING POLICY Revision Dates: August, 2007; June, 2009; February, 2013; April, 2015 City of Roswell Purchasing Policy TABLE OF CONTENTS I. Introduction Purpose Mission Scope Exceptions Ethics in Purchasing Freedom of Information Definitions II. Responsibilities Purchasing Agent Responsibilities Purchasing Manager Responsibilities Department Head Responsibilities Department Liaison Responsibilities Department Agent Responsibilities Disciplinary Actions for Violations III Purchasing Thresholds IV. Non-Competitive Procurements Sole Source Procurement Sole Brand Procurement Direct Negotiation Emergency Procurement Costs Under the Competitive Threshold Direct Negotiation through the use of Public Entity Contracts V. Competitive Procurements Invitation to Bid Request for Informal Quote Request for Proposals Quality Based Selections Request for Qualifications Multi-step Solicitations Online Reverse Auction 2 City of Roswell Purchasing Policy VI. Protests VII. Guidelines for Promoting Sustainability through the Purchasing Process Policy Requirements and Preferences VIII. Procurement Card (P-Card) Program IX. Capital Assets, Property, and Surplus X. Qualifications Based Selection for Projects Using Federal Aid Highway Program (FAHP) Funding XI. Contract Document Process 3 City of Roswell Purchasing Policy I. INTRODUCTION PURPOSE This Policy is intended to establish the methods by which the City procures goods and services and enters into contracts. This document will clarify purchasing functions and outline purchasing -

PEOPLESOFT USER MANUAL for PURCHASING June 22, 2021 Revised SAN DIEGO COMMUNITY COLLEGE DISTRICT PEOPLESOFT USER MANUAL for PURCHASING
PEOPLESOFT USER MANUAL FOR PURCHASING June 22, 2021 Revised SAN DIEGO COMMUNITY COLLEGE DISTRICT PEOPLESOFT USER MANUAL FOR PURCHASING Table of Contents TOPIC PAGE Notice on Supplier Gifts and Gratuities………………………………………………………...……1 Cal-card Program Information………………………………………………………………………..2 Frequently Asked Questions (FAQs)………………………………………………………...………4 PeopleSoft (PS) Supplier Intake Process ................................................................................ 9 Suppliers (establishing a supplier before creating a requisition) ....................... ……………....10 Information to gather prior to creating a requisition……………………………………………….20 Requisitions (creating a requisition)………………………………………………………………..22 Process after a requisition has been submitted ...................................................................... 40 Change Orders (changing a requisition) ................................................................................. 41 Direct Connect Orders (ordering from Office Solutions) ......................................................... 47 Direct Connect Orders (ordering from Grainger)………………………………………………….56 Template Language - Blanket Orders……………………………………………………………...66 ARMA Rules (naming convention for requisition line item descriptions) ................................. 70 Category Codes (explains purchasing codes used in PeopleSoft) ……………………............72 Confirmation Form (justification form for purchases made without a PO) …………..………...79 Status Definitions (explains purchasing codes used in PeopleSoft) ...................................... -
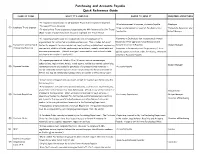
Purchasing and Accounts Payable Quick Reference Guide
Purchasing and Accounts Payable Quick Reference Guide NAME OF FORM WHAT IT'S USED FOR WHERE TO SEND IT REQUIRED SIGNATURES •To request reimbursement for all Employee Travel & Entertainment Expenses •If reimbursement is required, Accounts Payable •Employee •To request Travel Advances (1) Employee Travel Expense •If no reimbursement is required, Purchasing Card •Immediate Supervisor and •To substantiate Travel Expenses charged using the MU Corporate Card for Travel Coordinator Budget Manager (Must include original receipts to document expenses; see Travel Policy) •To request payments made to individuals who are not employees or to •Payments to Individuals (not incorporated), Human organizations for contracted or professional services. This includes, but is not Resources (After approval, Human Resources will Payment for Contracted & limited to, payments for services such as, legal, auditing, architectural, engineering, forward to Accounts Payable) •Budget Manager (2) Professional Services contractors, athletic officials, performers, entertainers, models, consultants and •Payments to Partnerships and Corporations, if to be insurance premiums etc. (Attach an original invoice and/or contract and include applied against a purchase order, Purchasing, otherwise purchase order number if applicable) directly to Accounts Payable. •To request payments not listed in (1) or (2) above, such as memberships, subscriptions, registrations, hotels, travel agents, vehicle/bus rentals, advertising, •Budget Manager (3) Expense Voucher reimbursements to employees for purchases of business related materials in •Accounts Payable excess of $75.00 and non-employee travel reimbursements. (Reimbursements of $75 or less may be reimbursed by Department or Cashier's Office Petty Cash) •All purchases of supplies and equipment, except for supplies purchased using the Purchasing Card. -

Purchasing and Payment Policy and Procedures
Responsible University Officials: Executive Vice President Vice President of Financial Operations and Treasurer Responsible Offices: Procurement and Payment Services Origination Date: December 1, 2008 Purchasing and Payment Policy and Procedures Policy Statement Northwestern University (NU) supports sustaining and promoting a procurement environment based on the understanding that departments and schools are in the best position to determine what they need to run their programs. Policies, procedures, and processes are meant to support their need to get products and services in a timely and cost effective manner, while also making sure appropriate business processes are followed. Procurement and Payment Services (PPS), which is part of Financial Operations, is the single point of contact for all centralized procurement and payment activities. Purchasing and Payment Services is considered the procurement expert at NU, setting the overall strategy regarding how purchases and payments should be made. Procurement and Payment Services consists of Vendor File Management, Purchasing, e-Procurement, Accounts Payable, Procurement Card, e-Payment, and Business Diversity. Reason for Policy / Purpose Considerable authority has been delegated to departments and schools to make purchasing decisions. This requires that employees involved at every step of the process take full responsibility for understanding NU’s policies and procedures regarding purchasing, payment, and vendor relations. Purchasing decisions are business decisions made on behalf of NU and therefore should be made with the utmost consideration for what is in the best interest of NU. Purchases also need to be made in the most efficient and cost effective manner. Following policy and procedures ensures that appropriate business processes occur when dealing with outside vendors. -

Ten Questions to Ask Before You Buy Cargo Insurance
Ten Questions To Ask Before You Buy Cargo Insurance UPS Capital Insurance Agency, Inc. UPS and the UPS brandmark are trademarks of United Parcel Service of America, Inc. Cargo Insurance Defined The international shipping industry is responsible for the carriage of 90 percent of global trade in goods.1 And there is approximately US$1.43 billion worth of containerized goods moving through U.S. ports every day.2 It is no wonder, then, that more and more companies are purchasing Cargo Insurance to protect against physical loss or damage to goods from external causes such as theft, natural disaster, inclement weather, and shipping accidents. Whether you are currently working with an insurance provider or are considering Cargo Insurance for the first time, UPS Capital Insurance Agency, Inc. suggests you ask the following questions to ensure your goods are properly protected: 1. Is your Cargo Insurance provider experienced in supply chain management and transportation, or are you buying Cargo Insurance from your general liability protection provider? Consider buying insurance from a provider with expertise in multiple modes of transportation, customs brokerage, and moving goods internationally. Make sure your provider has the background knowledge and know-how to fully protect your goods. 2. If you already have Cargo Insurance, does your current provider protect your goods via all modes of transportation – ship, airplane, train, and truck? No matter how your goods are transported, make sure that your insurance provider offers complete protection and uniform rates. For instance, if your goods come off a ship and are loaded onto a truck to be transported to their final destination, often the insurance rates and coverage limits may differ. -

Public Purchasing Requirements
STATE PURCHASING REQUIREMENTS INDIANA STATE BOARD OF ACCOUNTS INTRODUCTION TO INDIANA CODE 5-22 • IC 5-22-1-1: “Except as provided in this chapter, this article applies to every expenditure of public funds by a governmental body.” • IC 5-22-3-3: “A governmental body may adopt rules to regulate purchases of the governmental body. A rule adopted under this subsection may: (1) supplement this article; and (2) not be inconsistent with this article.” INTRODUCTION TO INDIANA CODE 5-22 CONTINUED • IC 5-22-4-5 and IC 5-22-4-6 • The individuals designated by the purchasing agency are the purchasing agents for the governmental body. • A purchasing agency may have more than one purchasing agent. • IC 5-22-4-7 • Allows governmental bodies, under IC 36-1-7 (Interlocal Agreement), to form cooperative purchasing organizations. • Requires cooperative purchasing organizations to follow IC 5- 22. • The cooperative purchasing organization becomes the purchasing agency for the governmental body for that particular purchase. The individual designated by the cooperative purchasing organization becomes the purchasing agent for the governmental body for that particular purchase. PURCHASES OF SERVICES • IC 5-22-6-1: “The purchasing agency of a governmental body may purchase services using any procedure the governmental body or the purchasing agency of the governmental body considers appropriate.” • IC 5-22-2-30: “”Services” means the furnishing of labor, time, or effort by a person, not involving the delivery of specific supplies other than printed documents or other items that are merely incidental to the required performance.” PURCHASE OF SUPPLIES – COMPETITIVE BIDDING • IC 5-22-2-38: “(a) “Supplies” means any property.