CA IDMS Best Practices Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

IDMS Conversion
IDMS Conversion The Modern Systems IDMS conversion includes the generation of a new relational database to replace the functionality, set relationships, indexes, and data structures that are currently part of the IDMS network database. The new target database can reside on or off the mainframe, and can use any of the standard relational database management systems (RDBMS): Microsoft SQL Server, Oracle or IBM DB2. Database Functionality DB-Shuttle™ provides The Modern Systems solution provides a complete replacement for all IDMS automated technology database functionality: that protects legacy assets, reduces • IDMS record layouts maintenance costs, • Group-level elements, Occurs and Redefines clauses within IDMS record provides agility and definitions flexibility, and enables • Set definitions (record-to-record relationships) Service-Oriented • System-owned indexes Architecture (SOA) • Bill-of-material structures within business-critical • Multi-member sets, multi-set relationships between two record types applications. • Duplicate CALC designations • Sorted sets, Chained sets and NEXT sets Relational Results The resulting database is fully relational. Primary keys, foreign keys and index definitions are automatically created. All constraints are generated into the resulting DDL. Table spaces, indexes, table names and column names are all generated according to your naming standards. Delivered Components As part of the delivery process, Modern Systems generates and delivers the following component types for installation in the new relational -

Miami-Dade County
MIAMI-DADE COUNTY Cognos Business Analytics and IDMS Integration at Miami-Dade County Abstract of the Program Miami-Dade County led the way as the first company in the world to successfully extract information from a CA IDMS network database using IBM Cognos Business Analytics. Miami- Dade County stores the majority of their critical data, such as Criminal Justice, Payroll, Traffic and Building information in CA IDMS mainframe databases and traditionally extracts this data using Computer Associates CA IDMS tools (CA ADS ADS/O and IDMS/Cobol/IDMS). Through the collaboration of CA Computer Associates, IBM, and Miami-Dade County, a driver was created for IBM Cognos to access this data directly by using Business Analytics tools without the need for exporting the data into a contemporary distributed environment. The problem or need for the program IDMS (Integrated Database Management System) is primarily a network (CODASYL) database management system for mainframes. Only CA tools could access IDMS data. IDMS mainframe technology did not have the capability to be accessed directly by contemporary business analytics software solutions. This limitation required data extraction, file transfer protocols, and script loading processes to expose IDMS, IMS, and DB2 mainframe data to contemporary technologies, including business analytics tools like IBM Cognos Analytics. Multiple data warehouses and operational data stores are loaded from the primary data sources originating from the IDMS mainframe platform and other relational data sources. More than 50 production IDMS databases are actively supported and used county-wide at Miami- Dade County. Access to data by the distributed world such as making the data available on an Oracle or MSSQL database requires adding multiple intermediate steps, using multiple technologies, and multiple points of failure to migrate data and make it available to analytic technologies. -

CASE STUDY GE CAPITAL ASSESSING, CONVERTING, & REPLATFORMING a MASSIVE BUSINESS CRITICAL APPLICATION with ASTONISHING RESULTS Introduction
CASE STUDY GE CAPITAL ASSESSING, CONVERTING, & REPLATFORMING A MASSIVE BUSINESS CRITICAL APPLICATION WITH ASTONISHING RESULTS Introduction GE Capital is the financial services unit of the American conglomerate General Electric, it provides commercial lending and leasing, as well as a range of financial services for consumers. Most of GE Capital’s commercial loans are to small and midsized companies, spread across multiple industries and geographies, and secured by tangible assets. GE Capital’s consumer lending activities are also diversified by product and geography and include operations in 55 countries. Project Summary GE Capital was looking to move their PMS suite of $ 2014 Net Income: $7.0 billion applications from ADS/O and COBOL/IDMS running 2014 Assets: $499 billion on a mainframe, to COBOL running with Oracle on Unix without changing the user interface in the Operations in 40+ Countries process. PMS was built by GE Capital in 1987 500,000+ Commercial Customers and began its life as a 20,000 account schedule system without any interfaces. 35,000+ Employees As with most homegrown systems, it was built out of necessity and to serve the business as it existed at the time. Over the decades, this small system grew in size and complexity to become the central nervous system of both GE Capital’s direct and indirect business units comprised of four highly customized implementations. With over 5 million account schedules, 382 interfaces, 1,700 concurrent users, and 3.5 million transactions per day running against 71 million lines of code, the PMS system had come a long way from its humble roots. -

DATABASE SYSTEMS: a BRIEF TIMELINE Event Consequence Pre-1960S 1945 Magnetic Tapes Developed (The First Medium Replaced Punch Cards and Paper Tape
DATABASE SYSTEMS: A BRIEF TIMELINE Event Consequence Pre-1960s 1945 Magnetic tapes developed (the first medium Replaced punch cards and paper tape. to allow searching). 1957 First commercial computer installed. 1959 McGee proposed the notion of generalized access to electronically stored data. 1959 IBM introduced the Ramac system. Read data in a non-sequential manner, and access to files became feasible. The '60s 1961 The first generalized DBMS-GE'S Integrated Formed the basis for Network Data Model Data Store (IDS)-designed by Bachman; developed by Conference on Data Systems wide distribution by 1964. Bachman Languages Database Task Group (CODASYL popularized data structure diagrams. DBTG). 1965- · Generalized file management systems Provided two-level conceptual/user view 1970 developed by numerous vendors. organization of data. · Information Management System (IMS) developed by IBM. Formed the basis for Hierarchical Data Model. · IMS DB/DC (database/data communication) System was the first Supported network views on top of the large-scale DB/DC system. hierarchies. · SABRE, developed by IBM and American Airlines. Allowed multiple-user access to data involving a communication network. The '70s Database technology experienced rapid Commercial systems followed CODASYL growth. DBTG Proposal, but none fully implemented it. IDMS system by B. F. Goodrich, Honeywell's IDS II, UNIVACs DMS 1100, Burroughs's DMS-II, CDCs DMS-170, Phillips's PHOLAS, and Digital's DBMS-11. Several integrated DB/DC systems: Cincom’s TOTAL plus ENVIRON/l. DBMS developed as an academic discipline and a research area. 1970 The relational model is developed by Ted Laid foundation for database theory. Codd, an IBM research fellow. -

Tcvision IBM Mainframe Integration Through Change Data Capture Fact Sheet
tcVISION IBM Mainframe Integration Through Change Data Capture Fact Sheet Mainframe data integration has taken on more urgency in recent years The tcVISION Solution as organizations seek to relocate mainframe workloads to lower-cost tcVISION is ready to meet new technologies and challenges. Thanks to platforms, modernize mainframe applications and leverage analytics for tcVISION’s flexible architecture, support for new targets—including AWS, customer insight and competitive advantage. These factors are driving specialty, NoSQL and analytic databases such as Exasol, IBM DB2 BLU adoption of Cloud (e.g., Amazon Web Services [AWS]) and Big Data as and MongoDB—, transport layers and protocols is being continuously strategic components in corporate technology architecture. added, quickly and with minimal effort. With tcVISION, real-time Cloud and Big Data integration can embrace both mainframe (IBM DB2, IMS/ tcVISION’s support for Cloud and Big Data as targets is fully integrated DB, DL/1, Software AG Adabas, CA IDMS, CA Datacom and alongside traditional Linux/Unix/Windows (LUW) targets such as Oracle VSAM), Cloud, and LUW (IBM DB2 LUW, Oracle, IBM Informix, Database, IBM DB2 LUW, Software AG Adabas LUW, IBM Informix, Sybase, Microsoft SQL Server, PostgreSQL, Software AG Adabas Sybase, Microsoft SQL Server, PostgreSQL and ODBC. LUW) sources. tcVISION can deliver replicated data to Cloud and Big Data targets Why tcVISION? through a variety of means: creating files, writing directly into Hadoop • Increasing number of enterprise applications that utilize their own HDFS, and via streaming using Apache Kafka as the transport layer. Data databases. can be packaged using standard JSON and CSV protocols. • Requirement for up-to-date information demands real-time, bi- directional data synchronization between mainframe and open systems. -

IDMS File Access Guide
IDMS File Access Guide Release 8.1.3 November 2013 IKAN Solutions N.V. Kardinaal Mercierplein 2 B-2800 Mechelen BELGIUM Copyright © 2013, IKAN Solutions N.V. No part of this document may be reproduced or transmitted in any form or by any means, electronically or mechanically, for any purpose, without the express written permission of IKAN Solutions N.V. MetaSuite, MetaStore Manager, MetaMap Manager and Generator Manager are trademarks of IKAN Solutions N.V. IDMS is a trademark of Computer Associates (CA Inc). Table of Contents Chapter 1 - About This Manual........................................................................... 1 1.1. Prerequisites ...........................................................................................................................................................1 1.2. Related Publications ...............................................................................................................................................1 Chapter 2 - MetaSuite File Access Overview...................................................... 3 Chapter 3 - CA-IDMS Concepts and Terminology .............................................. 4 3.1. Overview.................................................................................................................................................................4 3.2. CA-IDMS data structures........................................................................................................................................4 3.3. Records...................................................................................................................................................................4 -

CA-IDMS 15.0 Data Sharing Feature Allows Multiple Update Cvs
CA-IDMS 15.0 Data Sharing Feature Allows Multiple Update CVs by Judith Kruntorad CA-IDMS 15.0 offers significant scalability and Members of a Data Sharing Group can share update access availability enhancements to CA-IDMS clients. Through to an area provided that: exploitation of Coupling Facility structures in a Parallel • Data Sharing is enabled for the area Sysplex environment, CA-IDMS Central Versions are now • Associated files for the area are assigned to shared cache able to share update access to the same database areas. • Attributes for the area and associated files are identical Additional features are also provided for improved 24 x 7 in all systems functionality, improved performance and productivity, and enhanced SQL Internally, each participating CV must now functionality. perform global transaction and page locking as well as global deadlock detection and resolution A Data Sharing Group (DSG) is a new for shared areas whenever a contention occurs. concept introduced with CA-IDMS 15.0. This is managed through the use of Coupling There is no syntax required to define a Data Facility structures. A cache structure must be Sharing Group. Rather a Data Sharing Group defined for the buffers for the shared files and comes into existence when two or more CVs a list and a lock structure must be defined for are started with identical values for the new use with global locking. XCF group services SYSIDMS parm of DSGROUP=group-name. Members and signaling services are used by CA-IDMS for sending of a Data Sharing Group enjoy many privileges including and receiving messages and monitoring Data Sharing the ability to share update access to areas, share access to Member status. -

The Business Value of DB2 UDB for Z/OS
Front cover The Business Value of DB2 UDB for z/OS Learn about the synergy of DB2 with IBM Eserver zSeries and z/OS Discover how you can benefit from the richness in function Be ready for On Demand Business Paolo Bruni Paul Bartak Rick Butler Sreeni Janaki John Pashley ibm.com/redbooks International Technical Support Organization The Business Value of DB2 UDB for z/OS June 2005 SG24-6763-00 Note: Before using this information and the product it supports, read the information in “Notices” on page ix. First Edition (June 2005) This edition applies to IBM DB2 Universal Database for z/OS Version 8 (program number 5625-DB2). © Copyright International Business Machines Corporation 2005. All rights reserved. Note to U.S. Government Users Restricted Rights -- Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Notices . ix Trademarks . x Preface . xi The team that wrote this redbook. xii Become a published author . xiv Comments welcome. xiv Chapter 1. Evolution of the mainframe . 1 1.1 The evolution of z/Architecture . 2 1.1.1 Lower cost of entry to mainframes . 2 1.1.2 More options in pricing and performance . 2 1.1.3 Leveraging investment in existing applications . 3 1.2 Hardware. 4 1.3 Operating systems . 10 1.3.1 Value of z/OS . 10 1.3.2 Evolution of z/OS . 16 1.3.3 Other mainframe operating systems . 17 1.4 Processor . 18 1.5 Management . 19 1.6 Preparing new mainframers . 20 1.7 2000 through 2005: The era of on demand. -

Treat Your CA IDMS™ and CA Datacom® Developers to Eclipse-Based Development
MAINFRAME Treat Your CA IDMS™ and CA Datacom® Developers to Eclipse-Based Development David Ross Sr Principal Product Owner CA Technologies MFX137E For Informational Purposes Only Terms of This Presentation © 2017 CA. All rights reserved. All trademarks referenced herein belong to their respective companies. The presentation provided at CA World 2017 is intended for information purposes only and does not form any type of warranty. Some of the specific slides with customer references relate to customer's specific use and experience of CA products and solutions so actual results may vary. Certain information in this presentation may outline CA’s general product direction. This presentation shall not serve to (i) affect the rights and/or obligations of CA or its licensees under any existing or future license agreement or services agreement relating to any CA software product; or (ii) amend any product documentation or specifications for any CA software product. This presentation is based on current information and resource allocations as of November 1, 2017, and is subject to change or withdrawal by CA at any time without notice. The development, release and timing of any features or functionality described in this presentation remain at CA’s sole discretion. Notwithstanding anything in this presentation to the contrary, upon the general availability of any future CA product release referenced in this presentation, CA may make such release available to new licensees in the form of a regularly scheduled major product release. Such release may be made available to licensees of the product who are active subscribers to CA maintenance and support, on a when and if-available basis. -

CA IDMS Product Brief
Product Brief CA IDMS™ At a Glance Key Features CA IDMS™ is a cost-effective, reliable, highly-performant, and secure database management system for IBM Z that delivers outstanding business • Zowe Conformant REST API. value for hundreds of enterprises and government organizations around Flexibility to leverage modern the world. A powerful database engine providing network and relational tooling to address the skills access exploiting the latest hardware and software technologies including challenge and automate systems the IBM z Systems Integrated Information Processor (zIIP). management minimizing risk of system outages. Business Challenges • Zowe command line interface. Enabled use of modern scripting Data is a business’ most valuable asset fueling new apps and services languages. that differentiate it in the market. Because mission critical data lives on the mainframe, corporate database systems must be highly scalable to • Zowe CLI Plug-in. Enables users to interact with the mainframe in a handle ever-increasing business demands. These systems must be open familiar format. and extensible to support existing applications, and enable modern digital transformations without requiring costly rewrites and conversions. • Standard SQL. Query and update existing legacy databases without Companies need a reliable database repository with enterprise-wide, migration or conversion while high-volume workload and fault-tolerant capabilities. They also need preserving existing apps. transformation techniques designed to improve performance, scalability, • ODBC and JDBC drivers. Access platform support, standards compliance, and usability, while simultaneously data and reuse legacy application reducing costs. code through IDMS Server APIs. Without a unified way to get ahead of nonstop demands for data, your • MQ adapter. Interface for CA IDMS organization could continue to experience the following challenges: applications to send and receive messages that can be zIIP enabled. -

CA Datacom/DB
PRODUCT SHEET CA Datacom/DB CA Datacom®/DB Version 14.0 CA Datacom®/DB for z/OS is a high-performance relational database management system (RDBMS) for mainframe operating systems. CA Datacom/DB provides a central data repository for your enterprise-class applications that demand the highest service-level requirements. Overview Corporate database management systems must be highly scalable to handle the ever-increasing demand to support additional workload requirements. They must also be flexible enough to support existing applications while deploying new web-enabled technologies without requiring costly rewrites and conversions. CA Datacom/DB provides award-winning transaction processing performance for both existing and new workloads, helping you to consolidate business functions on a central data repository as needed by your business. Business value By exploiting the geometric growth of mainframe memory capacities and processor speeds, the CA Datacom/DB RDBMS is scalable to manage extremely high-volume workloads. The database engine also takes advantage of new hardware technologies with improved memory optimization techniques at each new release. The ability to scale to handle additional workloads, which is due to highly efficient CA Datacom/DB resource utilization techniques, has allowed some customers to delay or cancel plans for hardware upgrades. CA Datacom/DB Features Next-Generation Mainframe Management CA Datacom/DB has adopted key features that are designed to simplify your use of CA Datacom/DB and help your staff to install, configure and maintain it more quickly and effectively. CA Mainframe Software Manager™: CA Mainframe Software Manager (CA MSM) automates CA Datacom/DB acquisition, installation, deployment, configuration and maintenance and removes SMP/E complexities. -
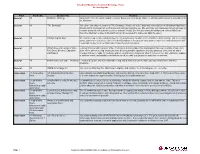
Broadcom Mainframe Technical Exchange: Plano Session Agenda Track Product(S)
Broadcom Mainframe Technical Exchange: Plano Session Agenda Track Product(s) Session Title Abstract General All Mainframe Strategy Vikas Sinha, Vice President, Global Customer Experience & Strategic Alliances, will discuss Broadcom's commitment to the Mainframe. General All "The Exchange" Join us to learn about the power of "The Exchange." Nicole will share about two innovations in the Broadcom Mainframe Division which stemmed from exchanges with customers just like you. She will share our continuous delivery strategy for releases designed with customers to meet customer needs. She will then share the background on how Mainframe Resource Intelligence came to life and how you can leverage it to make your daily life easier! General All Vitality Program Q&A We must develop creative solutions together, as a community, to address the mainframe skills shortage and successfully attract, grow and retain talent. Come hear how Broadcom is focusing on our customer experience and solving their skill needs with the launch of our Mainframe Vitality Residency program. General All What’s New with Customer Value, Learn what's new with Customer Value, Tech Docs, Services, Education and Support from representatives from each Tech Docs, Services, Education team. We're all here to help ensure you have the best possible experience with your products. Join us as we share and Support changes that we've made for the better and tell us what you're looking for when it comes to your doc, education, support or services needs, and anything else that we can do to make your Broadcom experience a success. General All Infrastructure as a code - workshop Let's do a deep dive into your mainframe setup and identify how can we make your operations faster and more productive.