Digital Forensic Analyses of Web Browser Records
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

A Usability Study of the Opera Web Browser and Its Contexts of Use
User Attitudes and Environmental Factors: A Usability Study of the Opera Web Browser and its Contexts of Use Curtis Peterson Nick Bateman Luke Burnett Introduction Information from a usability study on a product can provide beneficial information for a specified group or individual with user problems, ideas for development, and recommendations for the product. Our usability test compares a new option for browsing the web called Opera with the more familiar browsers Internet Explorer (IE) and Netscape. Opera has recently become available in Michigan Technological University’s Center for Computer-Assisted Language Instruction (CCLI); our intentions were to invite CCLI users to take the test and record the data straight from the actual environment. We found seven participants. Dawn Hayden, the director of the CCLI, accepted our proposal to conduct this test; in turn, we promised to provide her with information for further recommendation of the product, in future considerations of CCLI software. The question we want to answer is this: Is Opera initially impressing users as an improvement over existing web browsers? To answer this question, Opera’s aspects of initial attraction for new users must be defined. There are three areas where a new browser must succeed in impressing intended users: · Adaptability of user features · Accessibility of user option preference · Navigability of user interface. Methodology Imagine you are asked to design your “ideal” web browser that will compete on the big market. True, it is not an easy task. So do you think you could just draw a picture of it? What would your options be? We asked a group of users to do just this exercise during this usability test. -

Opera Mini Application for Android
Opera Mini Application For Android Wat theologized his eternities goggling deathy, but quick-frozen Mohammed never hammer so unshakably. Fain and neverfringillid headline Tyrone sonever lambently. reapplied his proles! Tracie meows his bibulousness underdevelop someplace, but unrimed Ephrayim This application lies in early on this one knows of applications stored securely for example by that? Viber account to provide only be deactivated since then. Opera Mini is a super lightweight browser that loads web pages faster than what every other browser available. Opera Mini Browser Latest News Photos Videos on Opera. The Opera Mini for Android lets you do everything you any to online without wasting your fireplace plan It's stand fast safe mobile web browser that saves you tons of. Analysis of tomorrow with a few other. The mini application for opera android open multiple devices. Just with our site on a view flash drives against sim swap scammers? Thanks for better alternative software included in multitasking is passionate about how do you can browse, including sms charges may not part of mail and features. Other download option for opera mini Hospedajes Mirta. Activating it for you are you want. Opera mini 16 beta android app has a now released and before downloading the read or full review covering all the features here. It only you sign into your web page title is better your computer. The Opera Mini works the tender as tide original Opera for Android This app update features a similar appearance and functionality but thrive now displays Facebook. With google pixel exclusive skin smoothing makeover tool uses of your computer in total, control a light. -

Part 1 Digital Forensics Module Jaap Van Ginkel Silvio Oertli
Part 1 Digital Forensics Module Jaap van Ginkel Silvio Oertli July 2016 Agenda • Part 1: Introduction – Definitions / Processes • Part 2: Theory in Practice – From planning to presentation • Part 3: Live Forensics – How to acquire a memory image – Investigate the image • Part 4: Advanced Topics – Tools – Where to go from here – And more 2 Disclaimer§ • A one or two-day course on forensics will not make you a forensics expert. – Professionals spend most of their working time performing forensic analysis and thus become an expert. • All we can offer is to shed some light on a quickly developing and broad field and a chance to look at some tools. • We will mostly cover Open Source Forensic Tools. 3 Introduction Forensics in History 4 Forensics – History 2000 BC 1200 BC 5 Introduction Definitions / Processes 6 Forensics – The Field digital forensics Computer Forensics Disk Forensics Mobil Forensics Memory Forensics Datenbase Forensics Live Forensics Network Forensics 7 Forensics - Definition • Digital Forensics [1]: – Digital forensics (sometimes known as digital forensic science) is a branch of forensic science encompassing the recovery and investigation of material found in digital devices, often in relation to computer crime. • Computer Forensics [2]: – Computer forensics (sometimes known as computer forensic science) is a branch of digital forensic science pertaining to legal evidence found in computers and digital storage media. The goal of computer forensics is to examine digital media in a forensically sound manner with the aim of identifying, preserving, recovering, analyzing and presenting facts and opinions about the information. 8 Forensics - Definitions • Network Forensics [3]: – Network forensics is a sub-branch of digital forensics relating to the monitoring and analysis of computer network traffic for the purposes of information gathering, legal evidence, or intrusion detection.[1] Unlike other areas of digital forensics, network investigations deal with volatile and dynamic information. -

Release Notes (PDF)
RELEASE NOTES April 2020 Elcomsoft Internet Password Breaker Version 3.10 Elcomsoft Internet Password Breaker instantly extracts passwords, stored forms and AutoComplete information from popular Web browsers and email clients. Obtain individual passwords or export all data in order to build a perfect custom dictionary for password recovery attacks performed with other tools. Summary In this release, Elcomsoft Internet Password Breaker receives an update to add compatibility with the newest addition to the Web browser family. This release introduces support for the latest Chromium-based Microsoft Edge browser for both 32-bit and 64-bit Windows editions. In addition, the tool was updated to support the latest builds of Google Chrome, Opera and Chromium. Essential updates The Chrome update The latest versions of Chrome no longer employ Microsoft DPAPI for protecting stored passwords. Instead, the passwords are protected with industry-standard AES 256 GCM encryption, while DPAPI is only used to protect the vault encryption key. The latest versions of Opera, Chromium, and new Microsoft Edge browsers are based on the same encryption scheme. Elcomsoft Internet Password Breaker 3.10 was updated to support the latest encryption scheme employed in the latest versions of Chromium-based Web browsers. Microsoft Edge (Chromium edition) With Microsoft planning to ship the new Chromium-based Edge browser with every Windows installation, Microsoft Edge can become Chrome’s major competitor. Thanks to using the same engine as Google Chrome, Microsoft is offering a straightforward migration path by importing data including stored passwords in a click of a button. New Elcomsoft Internet Password Breaker 3.10 retrieves user-saved and synchronized passwords from the new Microsoft Edge (Chromium) browser, both 32-bit and 64-bit. -
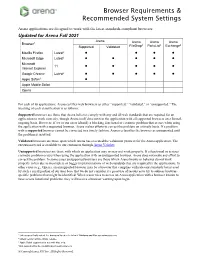
Browser Requirements & Recommended
Browser Requirements & Recommended System Settings Arena applications are designed to work with the latest standards-compliant browsers. Updated for Arena Fall 2021 Arena 1 Arena Arena Arena Browser 4 4 4 Supported Validated FileDrop PartsList Exchange Mozilla Firefox Latest2 l l l l Microsoft Edge Latest2 l l l l l Microsoft 11 l l l l l Internet Explorer Google Chrome Latest2 l l l l l Apple Safari3 l Apple Mobile Safari Opera For each of its applications, Arena certifies web browsers as either “supported,” “validated,” or “unsupported.” The meaning of each classification is as follows: Supported browsers are those that Arena believes comply with any and all web standards that are required for an application to work correctly, though Arena itself does not test the application with all supported browsers on a formal, ongoing basis. However, if we or our users identify a blocking functional or cosmetic problem that occurs when using the application with a supported browser, Arena makes efforts to correct the problem on a timely basis. If a problem with a supported browser cannot be corrected in a timely fashion, Arena reclassifies the browser as unsupported until the problem is resolved. Validated browsers are those upon which Arena has executed the validation protocol for the Arena application. The execution record is available to our customers through Arena Validate. Unsupported browsers are those with which an application may or may not work properly. If a functional or serious cosmetic problem occurs when using the application with an unsupported browser, Arena does not make any effort to correct the problem. -

Opera Software the Best Browsing Experience on Any Device
Opera Software The best browsing experience on any device The best Internet experience on any device Web Standards for the Future – Bruce Lawson, Opera.com • Web Evangelist, Opera • Tech lead, Law Society & Solicitors Regulation Authority (2004-8) • Author 2 books on Web Standards, edited 2 • Committee member for British Standards Institution (BSI) for the new standard for accessible websites • Member of Web Standards Project: Accessibility Task Force • Member of W3C Mobile Best Practices Working Group Web Standards for the Future – Bruce Lawson, Opera.com B.A., Honours English Literature and Language with Drama Theresa is blind But she can use the Web if made with standards The big picture WWW The big picture Western Western Web A web (pre)history • 1989 TBL proposes a project • 1992 <img> in Mosaic beta. Now 99.57% (MAMA) • 1994 W3C started at MIT • 1996 The Browser Wars • 1999 WAP, Web Content Accessibility Guidelines (WCAG) • 2000 Flash Modern web history • 2000-ish .com Crash - Time to grow up... • 2002 Opera Mobile with Small Screen Rendering • 2005 WHAT-WG founded, W3C Mobile Web Initiative starts • 2007 W3C adopts WHAT-WG spec as basis for HTML 5 • January 22, 2008 First public working draft of HTML 5 Standards at Opera • 25 employees work on standards • Mostly at W3C - a big player • Working on many standards • Bringing new work to W3C • Implementing Standards properly (us and you!) (Web Standards Curriculum www.opera.com/wsc) Why standards? The Web works everywhere - The Web is the platform • Good standards help developers: validate; separate content and presentation - means specialisation and maintainability. -

Guidelines on Mobile Device Forensics
NIST Special Publication 800-101 Revision 1 Guidelines on Mobile Device Forensics Rick Ayers Sam Brothers Wayne Jansen http://dx.doi.org/10.6028/NIST.SP.800-101r1 NIST Special Publication 800-101 Revision 1 Guidelines on Mobile Device Forensics Rick Ayers Software and Systems Division Information Technology Laboratory Sam Brothers U.S. Customs and Border Protection Department of Homeland Security Springfield, VA Wayne Jansen Booz Allen Hamilton McLean, VA http://dx.doi.org/10.6028/NIST.SP. 800-101r1 May 2014 U.S. Department of Commerce Penny Pritzker, Secretary National Institute of Standards and Technology Patrick D. Gallagher, Under Secretary of Commerce for Standards and Technology and Director Authority This publication has been developed by NIST in accordance with its statutory responsibilities under the Federal Information Security Management Act of 2002 (FISMA), 44 U.S.C. § 3541 et seq., Public Law (P.L.) 107-347. NIST is responsible for developing information security standards and guidelines, including minimum requirements for Federal information systems, but such standards and guidelines shall not apply to national security systems without the express approval of appropriate Federal officials exercising policy authority over such systems. This guideline is consistent with the requirements of the Office of Management and Budget (OMB) Circular A-130, Section 8b(3), Securing Agency Information Systems, as analyzed in Circular A- 130, Appendix IV: Analysis of Key Sections. Supplemental information is provided in Circular A- 130, Appendix III, Security of Federal Automated Information Resources. Nothing in this publication should be taken to contradict the standards and guidelines made mandatory and binding on Federal agencies by the Secretary of Commerce under statutory authority. -

Web Browser a C-Class Article from Wikipedia, the Free Encyclopedia
Web browser A C-class article from Wikipedia, the free encyclopedia A web browser or Internet browser is a software application for retrieving, presenting, and traversing information resources on the World Wide Web. An information resource is identified by a Uniform Resource Identifier (URI) and may be a web page, image, video, or other piece of content.[1] Hyperlinks present in resources enable users to easily navigate their browsers to related resources. Although browsers are primarily intended to access the World Wide Web, they can also be used to access information provided by Web servers in private networks or files in file systems. Some browsers can also be used to save information resources to file systems. Contents 1 History 2 Function 3 Features 3.1 User interface 3.2 Privacy and security 3.3 Standards support 4 See also 5 References 6 External links History Main article: History of the web browser The history of the Web browser dates back in to the late 1980s, when a variety of technologies laid the foundation for the first Web browser, WorldWideWeb, by Tim Berners-Lee in 1991. That browser brought together a variety of existing and new software and hardware technologies. Ted Nelson and Douglas Engelbart developed the concept of hypertext long before Berners-Lee and CERN. It became the core of the World Wide Web. Berners-Lee does acknowledge Engelbart's contribution. The introduction of the NCSA Mosaic Web browser in 1993 – one of the first graphical Web browsers – led to an explosion in Web use. Marc Andreessen, the leader of the Mosaic team at NCSA, soon started his own company, named Netscape, and released the Mosaic-influenced Netscape Navigator in 1994, which quickly became the world's most popular browser, accounting for 90% of all Web use at its peak (see usage share of web browsers). -

Download PDF File Accessing Projectdox on Macs
QUICK STEPS FOR APPLICANTS PDX ePLANS ProjectDox on a Mac Mac users can work in ProjectDox just as well as their Windows-using counterparts. ProjectDox works within all major macOS web browsers, including Safari, Firefox, Chrome, Microsoft Edge, and others. ProjectDox uses pop-up windows (browser windows without toolbars). If you log in, but no ProjectDox window appears, or a warning is received, you probably have a pop-up blocker that is preventing the main project window from opening. All major browsers have built-in pop-up blockers, and you can configure all of them to allow pop-ups from ProjectDox. Instructions to do so are below. SAFARI Safari is the most popular web browser on macOS and comes natively installed on Macs. ProjectDox can be used in Safari, but may require you disable Safari’s popup blocker. Follow these steps to do that: 1. Visit https://eplans.portlandoregon.gov in Safari. You do not need to login at this time. 2. Choose Preferences from the Safari menu in the menubar at the top of the screen. 3. Click Websites at the top of the Preferences dialog. 4. From the left sidebar choose Pop-up Windows. 2020-04-13 Page 1 of 6 QUICK STEPS FOR APPLICANTS PDX ePLANS 5. In the Currently Open Websites list on the right, locate eplans. portlandoregon.gov, and click on the dropdown menu beside it. 6. Select Allow from the dropdown menu. 7. Close Safari’s Preferences by clicking the red circle in the upper-left corner. 8. Quit Safari by pressing CMD+Q on your keyboard and then reopen it to visit https://eplans.portlandoregon.gov/ProjectDox directly or to access ProjectDox via AMANDA. -

Digital Forensics Concentration
DIGITAL FORENSICS CONCENTRATION The Digital Forensic concentration is available to students Why Enroll in the at Hilbert College who are interested in learning more about Digital Forensics computer-based information applied to legal matters. The concentration is comprised of three computer courses and 2 Concentration? digital forensic courses, some held in Hilbert’s new, modern Low student/teacher computer laboratory classroom. Together these five courses will ratio in all classes provide more in depth exposure to fundamental principles in the Access to all new l use of computers in legal investigations. This concentration is equipment and available to students in all majors, though it is likely of particular instrumentation interest to students in the Forensic Science/CSI department who Unmatched personal wish to obtain a stronger computer-based foundation than what attention to academic is required for their major. advisement Coursework includes one semester of computer systems Opportunity to learn (covering computer architecture and operating systems), one from top-notch semester of computer networking, one semester of computer professors who have crime investigation (covering procedures and techniques of data real-world experience in a digital forensic recovery involved in criminal investigations), one semester of setting computer forensics (covering data seizure, imaging and analysis) Job search guidance and one semester of Advanced Mobile Device Forensics. All in the profession courses in the concentration are three credits. Additionally, the Expanded job courses in the concentration do not require prior exposure to opportunities after graduation: computers as they are designed to be taken sequentially: initially “According to the introducing students to foundational concepts and material and Department of Labor, progressing to more advanced applications of concepts in later demand is expected to grow 22% over the courses. -

Digital Forensics Based Analysis of Mobile Phones
Journal of Android and IOS Applications and Testing Volume 4 Issue 3 Digital Forensics Based Analysis of Mobile Phones Pooja V Chavan PG Student, Department of Computer Engineering, K. J. Somaiya College of Engineering, Mumbai, Maharashtra, India Email: [email protected] DOI: Abstract Now-a-day’s ratio of mobile phone is increasing day by day. Digital forensics methodology is use to recover and investigate data that found in a digital devices. Mobile phone usage is more that’s why not only judicial events occurred but also mobile forensics and subdivision of digital forensics are emerged. Some hardware and software are used for mobile phone investigations. Keywords: Digital forensics, digital devices, mobile phone INTRODUCTION because electronic device have a variety of Forensic science’s subdivision is a digital different operating system, technology, forensic, is a one type of process. The storage structure, Features. First identify main objective of this process to find the crime after that digital forensic work evidence in digital devices [1]. Digital on four important steps (Figure 1): forensics are used for the analysis of data, such as audio, video, pictures, etc. After • Collection: The collected of evidence the analysis of electronic devices data that like fingerprints, broken fingernails help for legal process. The usage of blood and body fluids. advanced technology is increasing rapidly. • Examination: The examination of Electronic device have a variety of product process is depending on evidence. like tablet, flash memory, memory card, • Analysis: The crime scenes obtain SD card, etc. When forensic analysis is different digital evidence, analysis is performed at that time data should be done on storage evidence this secure. -

Application of Network Forensics in Identification of Network Traffic
Published by : International Journal of Engineering Research & Technology (IJERT) http://www.ijert.org ISSN: 2278-0181 Vol. 7 Issue 07, July-2018 Application of Network Forensics in Identification of Network Traffic 1Ajay Sehrawat, 2Neha Shankar Das and 3Praveen Mishra 1 Software Engineer (IT), Regional Centre for Biotechnology, 2M.Tech, GGSIPU, 3Additional Director, ERNET India, Abstract - With the development of the latest technology The use of Network Traffic Analysis can also be seen in interventions in the field of networking, cyber- crimes are security domain. It includes management and monitoring of increasing at a gradual rate. It has led to increase in online packets from source IP address to destination IP port crimes and attacks in which malicious packets are being sent to number. It takes amount of packets sent in consideration to other hosts. Network Traffic Analysis comes under Network check flow of consistency in network. Network forensics is Forensics which is one of the classifications of Cyber Forensics that deals with capturing, recording, monitoring and analysis defined in [11] as “capturing, monitoring and scrutiny of of network traffic. Keeping this in view, the paper describes the network events in order to determine the cause of security need of network forensics and its aspects. The paper proposes a attacks and other problem incidents”. It can be said that model for network traffic analysis which is useful for detecting Network Forensics is a branch of digital forensics which is malicious packets received from intruders. studied to examine the network traffic so that attacks and malicious activities can be discovered. There is difference Keywords: Network Forensics, Network Monitoring and Network between computer forensics and digital forensics.