A Review on Cloud Computing Security
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Nasuni Cloud File Services™ the Modern, Cloud-Based Platform to Store, Protect, Synchronize, and Collaborate on Files Across All Locations at Scale
Data Sheet Data Sheet Nasuni Cloud File Services Nasuni Cloud File Services™ The modern, cloud-based platform to store, protect, synchronize, and collaborate on files across all locations at scale. Solution Overview What is Nasuni? Nasuni® Cloud File Services™ enables organizations to Nasuni Cloud File Services is a software-defined store, protect, synchronize and collaborate on files platform that leverages the low cost, scalability, and across all locations at scale. Licensed as stand-alone or durability of Amazon Simple Storage Service (Amazon bundled services, the Nasuni platform modernizes S3) and Nasuni’s cloud-based UniFS® global file system primary and archive file storage, file backup, and to transform file storage. disaster recovery, while offering advanced capabilities Just like device-based file systems were needed to for multi-site file synchronization. It is also the first make disk storage usable for storing files, Nasuni UniFS platform that automatically reduces costs as files age so overcomes obstacles inherent in Amazon S3 related to data never has to be migrated again. latency, file retrieval, and organization to make object With Nasuni, IT gains a more scalable, affordable, storage usable for storing files, with key features like: manageable, and highly available file infrastructure that • Fast access to files in any edge location. meets cloud-first objectives and eliminates tedious NAS • Legacy application support, without app rewrites. migrations and forklift upgrades. End users gain limitless capacity for group shares, project directories, and home • Familiar hierarchical folder structure for fast search. drives; LAN-speed access to files in any edge location; • Unified platform for primary and archive file storage and fast recovery of files to any point in time. -

Nasuni for Business Continuity
+1.857.444.8500 Solution Brief nasuni.com [email protected] Nasuni for Business Continuity Summary of Nasuni Modern Cloud File Services Enables Remote Access to Critical Capabilities for Business File Assets and Remote Administration of File Infrastructure Continuity and Remote Work Anytime, Anywhere A key part of business continuity is main- Consolidation of Primary File Data in Remote File Access taining access to critical business con- Cloud Storage with Fast, Edge Access Anywhere, Anytime tent no matter what happens. Files are Highly resilient file storage is a funda- through standard drive the fastest-growing business content in mental building block for continuous file mappings or Web almost every industry. Providing remote file access. Nasuni stores the “gold copies” browser access, then, is a first step toward supporting of all file data in cloud object storage such Object Storage Dura- a “Work From Anywhere” model that can as Azure Blob, Amazon S3, or Google bility, Scalability, and sustain business operations through one-off Cloud Storage instead of legacy block Economics using Azure, hardware failures, local outages, regional storage. This approach leverages the AWS, and Google cloud office disasters, or global pandemics. superior durability, scalability, and availability storage of object storage to provision limitless file A remotely accessible file infrastructure sharing capacity, at substantially lower cost. Built-in Backup with that enables remote work must also be Better RPO/RTO with remotely manageable. IT departments Nasuni Edge Appliances – lightweight continuous file versioning must be able to provision new file storage virtual machines that cache copies of just to cloud storage capacity, create file shares, map drives, the frequently accessed files from cloud Rapid, Low-Cost DR recover data, and more without needing storage – can be deployed for as many that restores file shares skilled administrators “on the ground” in a offices as needed to give workers access in <15 minutes without datacenter or back office. -

Nasuni for Pharmaceuticals
+1.857.444.8500 Solution Brief nasuni.com [email protected] Nasuni for Pharmaceuticals Faster Collaboration Accelerate Research Collaboration with the Power of the Cloud between global research Now more than ever, pharmaceutical Nasuni Cloud File Storage for and manufacturing companies need to collaborate efficiently Pharmaceuticals locations across research and development centers, Major pharmaceutical companies have manufacturing facilities, and regulatory Unlimited Cloud solved their unstructured data storage, management centers. Critical research Storage On-Demand sharing, security, and protection challeng- and manufacturing processes generate in Microsoft Azure, AWS, es with Nasuni. terabytes of unstructured data that needs to IBM Cloud, Google be shared quickly — and protected securely. Immutable Storage in the Cloud Cloud or others elimi- Nasuni enables pharmaceutical com- nates on-premises NAS For IT, this requirement puts a tangible panies to consolidate all their file data in & file servers stress on traditionally siloed storage hard- cloud object storage (e.g. Microsoft Azure 50% Cost Savings ware and network bandwidth resources. Blob Storage, Amazon S3, Google Cloud when compared to Supporting unstructured data sharing Storage) instead of trapping it in silos of traditional NAS & backup forces IT to add storage capacity at an traditional, on-premises file servers or Net- solutions unpredictable rate, then bolt on expensive work-Attached Storage (NAS). Free from networking capabilities. Yet failing to keep physical device constraints, the combina- End-to-End Encryption up can impact both business and re- tion of Nasuni and cloud object storage secures research and search progress. Long delays waiting for offers limitless, scalable capacity at lower manufacturing data research files and manufacturing data to costs than on-premises storage. -

THE EMERGING CLOUD ECOSYSTEM: Cyber Security Plus LI/RD
Day 2, Thursday, 2012 Jan 19, 09.00 hrs SESSION 4: Security in the Cloud THE EMERGING CLOUD ECOSYSTEM: cyber security plus LI/RD Tony Rutkowski, Yaana Technologies 7th ETSI Security Workshop, 18‐19 Jan 2011 © ETSI 2012. All rights reserved Outline Security as a Business opportunity: A winning driver to ensure technology success and increase confidence and trust amongst end‐users ! CtCurrent Clou d dldevelopment s Cyber security and LI/RD developments Business opportunities 2 ETSI/Security Workshop (7) S4 The Basics: a new cloud‐based global communications infrastructure is emerging Global network architectures are profoundly, rapidly changing • PSTNs/mobile networks are disappearing • Internet is disappearing • Powerful end user devices for virtual services are becoming ubiquitous • End user behavior is nomadic • Huge data centers optimized for virtual services combined with local access bandwidth are emerging worldwide as the new infrastructure These changes are real, compelling, and emerging rapidly Bringing about a holistic “cloud” ecosystem is occupying idindustry in almost every venue around the world 3 ETSI/Security Workshop (7) S4 The Basics: a new cloud‐virtualized global communications architecture Virtualized Line or air Access, IdM & transport Intercloud Other cloud virtualization services, devices interfaces cloud virtualization services services especially for application support Access, IdM & transport General services Intercloud General Access, IdM & transport services General Intercloud Access, IdM & transport services -

Data Protection and Collaboration in Cloud Storage
Technical Report 1210 Charting a Security Landscape in the Clouds: Data Protection and Collaboration in Cloud Storage G. Itkis B.H. Kaiser J.E. Coll W.W. Smith R.K. Cunningham 7 July 2016 Lincoln Laboratory MASSACHUSETTS INSTITUTE OF TECHNOLOGY LEXINGTON, MASSACHUSETTS This material is based on work supported by the Department of Homeland Security under Air Force Contract No. FA8721-05-C-0002 and/or FA8702-15-D-0001. Approved for public release: distribution unlimited. This report is the result of studies performed at Lincoln Laboratory, a federally funded research and development center operated by Massachusetts Institute of Technology. This material is based on work supported by the Department of Homeland Security under Air Force Contract No. FA8721-05- C-0002 and/or FA8702-15-D-0001. Any opinions, findings and conclusions or recommendations expressed in this material are those of the authors and do not necessarily reflect the views of Department of Homeland Security. © 2016 MASSACHUSETTS INSTITUTE OF TECHNOLOGY Delivered to the U.S. Government with Unlimited Rights, as defined in DFARS Part 252.227-7013 or 7014 (Feb 2014). Notwithstanding any copyright notice, U.S. Government rights in this work are defined by DFARS 252.227-7013 or DFARS 252.227-7014 as detailed above. Use of this work other than as specifically authorized by the U.S. Government may violate any copyrights that exist in this work. Massachusetts Institute of Technology Lincoln Laboratory Charting a Security Landscape in the Clouds: Data Protection and Collaboration in Cloud Storage G. Itkis B. Kaiser J. Coll W. Smith R. -

Egnyte + Alberici Case Study
+ Customer Success From the Office to the Project Site, How Alberici Uses Egnyte to Keep Teams in Sync Egnyte has opened new doors of possibilities where we didn’t have access out in the field previously. The VDC and BIM teams utilize Egnyte to sync huge files offline. They have been our largest proponents of Egnyte. — Ron Borror l Director, IT Infrastructure $2B + Annual Revenue Introduction Solving complex challenges on aggressive timelines is in the DNA of Alberici Corporation, a diversified construction company 17 that works in industrial and commercial markets globally. Regional Offices When longtime client General Motors Company called on Alberici for an urgent design-build request to transform an 100 86,000 square-foot warehouse into an emergency ventilator Average Number manufacturing facility during the COVID-19 pandemic, they of Projects answered the call. Within just two weeks, the transformed facility produced its first ventilator and, within a month, it was making 500 life-saving devices a day. AT A GLANCE Drawing on their more than 100-years of experience successfully completing complex projects like the largest hydroelectric plant on the Ohio River, automotive assembly plants for leading car manufacturers, and SSM Health Saint Louis University Hospital, Alberici was ready to act fast. Engineering News-Record recently ranked Alberici as the 31st- largest construction company in the United States with annual revenues of $2B. Nearly 80 percent of Alberici’s business is generated by repeat clients, a testament to their service and quality and the foundation for consistent growth. www.egnyte.com | © 2020 by Egnyte Inc. All rights reserved. -

Ph.D. Thesis Security Policies for Cloud Computing Dimitra A. Georgiou
UNIVERSITΥ OF PIRAEUS ΠΑΝΕΠΙΣΤΗΜΙΟ ΠΕΙΡΑΙΩΣ School of Information and Communication Technologies Department of Digital Systems Systems Security Laboratory Ph.D. Thesis Security Policies for Cloud Computing A dissertation submitted for the degree of Doctor of Philosophy in Computer Science By Dimitra A. Georgiou PIRAEUS 2017 Advisory Committee Costas Lambrinoudakis, Professor (Supervisor) University of Piraeus -------------------------------------------------------------------------------- Sokratis Katsikas, Professor University of Piraeus -------------------------------------------------------------------------------- Christos Xenakis, Associate Professor University of Piraeus -------------------------------------------------------------------------------- UNIVERSITY OF PIRAEUS 2017 2 Examination Committee Costas Lambrinoudakis, Professor University of Piraeus -------------------------------------------------------------------------------- Sokratis Katsikas, Professor University of Piraeus -------------------------------------------------------------------------------- Christos Xenakis, Associate Professor University of Piraeus -------------------------------------------------------------------------------- Stefanos Gritzalis, Professor University of the Aegean (Member) -------------------------------------------------------------------------------- Spyros Kokolakis, Associate Professor University of the Aegean (Member) -------------------------------------------------------------------------------- Aggeliki Tsohou, Assistant Professor -

Magic Quadrant for Secure Web Gateways
15/11/2019 Gartner Reprint Licensed for Distribution Magic Quadrant for Secure Web Gateways Published 11 November 2019 - ID G00380121 - 35 min read By Analysts Lawrence Orans, John Watts, Peter Firstbrook Rapid growth of cloud-based secure web gateway services has become a disruptive force in the market. SWG vendors are adding cloud access security broker, remote browser isolation, firewall and other advanced features to enhance the security of their platforms. Market Definition/Description The rapid adoption of SaaS applications such as Microsoft Office 365, Salesforce and others is driving enterprises to adopt cloud-based secure web gateway (SWG) services. Enterprises are rearchitecting their WANs so that web traffic from remote offices flows directly to the internet (via local internet breakout connections), instead of backhauling it over expensive MPLS links to a centralized data center. As part of this rearchitecture, enterprises are utilizing cloud-based security stacks, so that web traffic from remote offices first flows through a cloud security service (mostly SWG services) before it reaches its final internet destination. A secondary driver for the adoption of these cloud services is the need to protect mobile laptops when they are off the corporate network. We continue to see interest from enterprises seeking to integrate cloud access security broker (CASB) and SWG functionality. SWG vendors are responding to this trend, by either acquiring CASB technology or partnering with CASB providers (mainly Microsoft and its Cloud App Security service) to deliver more tightly integrated CASB and SWG solutions. CASB vendor Netskope is also addressing this trend, as it continues the development of its SWG solution introduced in 2018. -
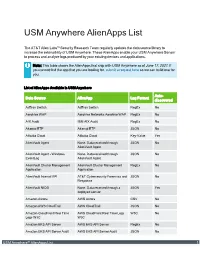
USM Anywhere Alienapps List
USM Anywhere AlienApps List The AT&T Alien Labs™ Security Research Team regularly updates the data source library to increase the extensibility of USM Anywhere. These AlienApps enable your USM Anywhere Sensor to process and analyze logs produced by your existing devices and applications. Note: This table shows the AlienApps that ship with USM Anywhere as of June 17, 2021. If you cannot find the app that you are looking for, submit a request here so we can build one for you. List of AlienApps Available in USM Anywhere Auto- Data Source AlienApp Log Format discovered AdTran Switch AdTran Switch RegEx No Aerohive WAP Aerohive Networks Aerohive WAP RegEx No AIX Audit IBM AIX Audit RegEx No Akamai ETP Akamai ETP JSON No Alibaba Cloud Alibaba Cloud Key-Value Yes AlienVault Agent None. Data received through JSON No AlienVault Agent AlienVault Agent - Windows None. Data received through JSON No EventLog AlienVault Agent AlienVault Cluster Management AlienVault Cluster Management RegEx No Application Application AlienVault Internal API AT&T Cybersecurity Forensics and JSON No Response AlienVault NIDS None. Data received through a JSON Yes deployed sensor Amazon Aurora AWS Aurora CSV No Amazon AWS CloudTrail AWS CloudTrail JSON No Amazon CloudFront Real Time AWS CloudFront Real Time Logs W3C No Logs W3C W3C Amazon EKS API Server AWS EKS API Server RegEx No Amazon EKS API Server Audit AWS EKS API Server Audit JSON No USM Anywhere™ AlienApps List 1 List of AlienApps Available in USM Anywhere (Continued) Auto- Data Source AlienApp Log Format discovered -

Informatica Economică Vol
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Directory of Open Access Journals 96 Informatica Economică vol. 17, no. 2/2013 Syncing Mobile Applications with Cloud Storage Services Paul POCATILU, Cătălin BOJA, Cristian CIUREA Department of Economic Informatics and Cybernetics The Bucharest University of Economic Studies [email protected], [email protected], [email protected] Cloud data storage is an option available almost on any mobile platform. Nowadays, there are multiple solutions for syncing data in mobile applications. The aim of the paper is to analyze mobile application developers’ possibilities for syncing content using major free cloud storage providers. The paper describes the cloud computing in mobile context and highlights cloud providers APIs. Experimental results are analyzed in order to identify the best cloud storage solution for syncing mobile applications, depending on the operating system on which they are implemented. Keywords: Cloud Computing, Mobile Application, Data Synchronization, Application Programming Interface, REST, OAuth Introduction Apple provides by default a 5 GB free 1 We are living in the era of agile and storage plan for every iOS user. always-available data storage [1], where it is very important to have instant and permanently access to the data, personal and private, with which we are operating at work or at home. The development of mobile technologies and the spectacular growth of mobile devices users created this opportunity to quickly read our emails, to view our documents from shared folders, to access all the data saved in the cloud directly from the personal smart-phone or tablet. -

File Servers: Is It Time to Say Goodbye? Unstructured Data Is the Fastest-Growing Segment of Data in the Data Center
File Servers: Is It Time to Say Goodbye? Unstructured data is the fastest-growing segment of data in the data center. A significant portion of data within unstructured data is the data that users create though office productivity and other specialized applications. User data also often represents the bulk of the organization’s intellectual property. Traditionally, user data is stored on either file servers or network-attached storage (NAS) systems, which IT tries to locate solely at a primary data center. Initially, the problem that IT faced with storing unstructured data was keeping up with its growth, which leads to file server or NAS sprawl. Now the problem IT faces in storing file data is that users are no longer located in a single primary headquarters. The distribution of employees exacerbates file server sprawl. It also makes it almost impossible for collaboration on the data between locations. IT has tried various workarounds like routing everyone to a single server via a virtual private network (VPN), which leads to inconsistent connections and unacceptable performance. Users rebel and implement workarounds like consumer file sync and share, which puts corporate data at risk. Organizations are looking to the cloud for alternatives. Still, most cloud solutions are either attempts to harden file sync and share or are Cloud-only NAS implementations that don’t allow for cloud latency. Nasuni A File Services Platform Built for the Cloud Nasuni is a global file system that enables distributed organizations to work together as if they were all in a single office. It leverages the cloud as a primary storage point but integrates on-premises edge appliances, often running as virtual machines, to overcome cloud latency issues. -

Security As a Service & Microsoft
Security as a Service & Microsoft 365 Nils Ullmann June 2020 This model worked well in the old world Internal networks were built and optimized to connect users to apps in the data center Perimeter security appliances to protect the network Outbound Inbound Gateway Gateway FW / IPS Global LB Workforce Customers URL Filter DDoS Antivirus Ext. FW/IPS Workforce DLP Customers RAS (VPN) APJ SSL EU Internal FW DC Sandbox DC Internal LB DNS Trusted Network NA DC Securing your cloud transformation This model worked well in the old world Internal networks were built and optimized to connect users to apps in the data center Perimeter security appliances to protect the network User Outbound Inbound Board My internet is faster at home!Gateway Gateway How secure are we? FW / IPS Global LB Workforce Customers URL Filter DDoS Antivirus Ext. FW/IPS Workforce DLP Customers RAS (VPN) APJ SSL EU Internal FW DC DC CEO Sandbox Internet Security Assessment Internal LB DNS Why does it take so long! Trusted Network External Attack Surface Assessment NA DC Securing your cloud transformation An opportunity for IT to empower the business The cloud is the new data center Application Facilitates collaboration Transformation New business models Simplifies IT Data Center to Cloud Trusted Network NA DC EU DC Securing your cloud transformation The Problem: Microsoft 365 5 ©2020 Zscaler, Inc. All rights reserved. This model worked well in the old world Internal networks were built and optimized to connect users to apps in the data center Perimeter security appliances to protect the network Outbound Inbound Gateway Gateway FW / IPS Global LB Workforce Customers URL Filter DDoS Antivirus Ext.