Aspects of Cooperation Between Csirts and Le
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Final Report September 2020
Coronavirus Commission for Safety and Quality in Nursing Homes Commission Final Report September 2020 Approved for Public Release; Distribution Unlimited 20-2378. © 2020 The MITRE Corporation. All Rights Reserved. Commission Final Report NOTICE This document was produced for the U. S. Government under Contract Number 75FCMC19F0012, and is subject to Federal Acquisition Regulation Clause 52.227-14, Rights in Data-General. No other use other than that granted to the U. S. Government, or to those acting on behalf of the U. S. Government under that Clause is authorized without the express written permission of The MITRE Corporation. For further information, please contact The MITRE Corporation, Contracts Management Office, 7515 Colshire Drive, McLean, VA 22102-7539, (703) 983-6000. Approved for Public Release; Distribution Unlimited 20-2378. © 2020 The MITRE Corporation. All Rights Reserved. Commission Final Report Coronavirus Commission for Safety and Quality in Nursing Homes Morgan Jane Katz, MD, MHS Assistant Professor of Medicine, Johns Hopkins Commission Members University, Maryland Roya Agahi, RN, MS HCM, WCC Beverley L. Laubert, MA Chief Nursing Officer, CareRite, New York State Long-Term Care Ombudsman, State Department of Aging, Ohio Lisa M. Brown, PhD, ABPP Professor of Psychology, Rosie D. Lyles, MD, MHA, MSc, FACA Palo Alto University, California Director of Clinical Affairs, Medline Industries, Mark Burket Illinois CEO, Platte Health Center Avera, South Dakota Jeannee Parker Martin, MPH, BSN, RN Eric M. Carlson, JD President and CEO, LeadingAge California Directing Attorney, Justice in Aging, California G. Adam Mayle, CHFM, CHC, CHE (does not endorse this report) Administrative Director of Facilities, Memorial Michelle Dionne-Vahalik, DNP, RN Healthcare System, Florida Associate Commissioner, State Health and Human David A. -

Onebeacon Technology Insurance Whitepaper Template (2016)
Autonomous Vehicles: Why Drive When the Vehicle Drives You Author: Tushar Nandwana, Information Technology Risk Control Published: June 2020 Executive Summary The idea of being effortlessly chauffeured by self-driving cars or autonomous vehicles (AV), has been a dream of futurists for several decades. They envision a time where we will simply input our destination and be safely driven there while we do work, relax, watch a movie, or even take a nap. Commercially, trucks will self-drive in platoon formations 24 hours a day transporting goods from one part of the country to another. Google was one of the first companies focusing on autonomous technology to hit a major milestone in 2009 when Google’s Waymo first demonstrated a 1,000 mile drive in a prototype, self-driving Toyota Prius. Since then, major automotive companies, along with hundreds of new companies, have entered into the self-driving arena. Both Waymo and Voyage now have fully self-driving robo- taxi fleets operating in specific communities in Florida, Arizona and California. There have been highly successful self-driving trucking tests by companies such as TuSimple and the now defunct Starsky Robotics. Firms tout new achievements in AV technology weekly, but for now, almost all operate in a test mode capacity as they develop data to further increase the safety and reliability of their AV systems. Reliable and unwavering safety of these systems remains elusive due to a high level of complexity. It will likely be upwards of three years minimum before we see a commercially viable AV platform that meets the necessary safety and reliability standards, likely a level 4 (L4). -

NVIDIA Technical Overview | GPU-Accelerated Signal Processing
TECHNICAL OVERVIEW GPU-ACCELERATED SIGNAL PROCESSING Delivering Real-Time, Low-Latency, and High-Performance Computing with the NVIDIA Aerial SDK A FIREHOSE OF SENSOR DATA AND SPEED-OF-LIGHT COMPUTE With high-throughput and low-latency demands, signal processing applications—from software-defined radio and communications systems to speech processing and beyond—have traditionally relied on special accelerators like FPGAs and ASICs to deliver real-time performance. Programming these devices, however, has remained a huge challenge, and the development-to-deployment cycle is prone to restarts. Additionally, as the signal processing community extends into applications of artificial intelligence and machine learning for intelligent networks, anomaly detection, and spectrum awareness, the seamless connection to software frameworks like PyTorch, NVIDIA RAPIDS™, and TensorFlow is critical. 5G, in particular, ushers in a new era in wireless communications that delivers more than 10X lower latency and 1,000X the bandwidth when compared to previous 3rd Generation Partnership Project (3GPP) standards: all while supporting millions of connected devices per square kilometer. As developers and decision-makers look toward the future, NVIDIA GPUs lead the way with a focus on fast input/output (I/O) handling, programmability, compute performance, and enablement of both AI training and inference for signal processing workloads. Whether at the edge, in a data center, or in the cloud, the NVIDIA Aerial™ SDK delivers a collection of state-of-the-art signal processing solutions for Python, CUDA®, and C++ developers alike. NVIDIA AERIAL: BIGGER, STRONGER, MORE PRODUCTIVE In 2019, NVIDIA announced Aerial—a software package targeted to the 5G signal processing surrounding virtual radio access networks (vRAN). -

RFI Response: AI Standards
©2019 The MITRE Corporation. All Rights Reserved. Approved for Public Release. Distribution Unlimited. Case Number 18-2319-33 MP190421 June 10, 2019 Response of The MITRE Corporation to the National Institute of Standards and Technology (NIST) Request for Information on Artificial Intelligence Standards For additional information about this response, please contact: Duane Blackburn, S&T Policy Analyst The MITRE Corporation 7596 Colshire Drive McLean, VA 22102-7539 [email protected] (434) 964-5023 i Table of Contents Introduction .................................................................................................................................................. 1 AI Technical Standards and related tools development: status and plans ................................................ 2 1.0 AI technical standards and tools that have been developed, and the developing organization, including the aspects of AI these standards and tools address, and whether they address sector-specific needs or are cross-sector in nature...................................................................... 2 2.0 Reliable sources of information about the availability and use of AI technical standards and tools .............................................................................................................................................. 4 3.0 The needs for AI technical standards and related tools. How those needs should be determined, and challenges in identifying and developing those standards and tools ............... 5 5.0 Any -

Ten Strategies of a World-Class Cybersecurity Operations Center Conveys MITRE’S Expertise on Accumulated Expertise on Enterprise-Grade Computer Network Defense
Bleed rule--remove from file Bleed rule--remove from file MITRE’s accumulated Ten Strategies of a World-Class Cybersecurity Operations Center conveys MITRE’s expertise on accumulated expertise on enterprise-grade computer network defense. It covers ten key qualities enterprise- grade of leading Cybersecurity Operations Centers (CSOCs), ranging from their structure and organization, computer MITRE network to processes that best enable effective and efficient operations, to approaches that extract maximum defense Ten Strategies of a World-Class value from CSOC technology investments. This book offers perspective and context for key decision Cybersecurity Operations Center points in structuring a CSOC and shows how to: • Find the right size and structure for the CSOC team Cybersecurity Operations Center a World-Class of Strategies Ten The MITRE Corporation is • Achieve effective placement within a larger organization that a not-for-profit organization enables CSOC operations that operates federally funded • Attract, retain, and grow the right staff and skills research and development • Prepare the CSOC team, technologies, and processes for agile, centers (FFRDCs). FFRDCs threat-based response are unique organizations that • Architect for large-scale data collection and analysis with a assist the U.S. government with limited budget scientific research and analysis, • Prioritize sensor placement and data feed choices across development and acquisition, enteprise systems, enclaves, networks, and perimeters and systems engineering and integration. We’re proud to have If you manage, work in, or are standing up a CSOC, this book is for you. served the public interest for It is also available on MITRE’s website, www.mitre.org. more than 50 years. -

Planning for On-Campus Education During COVID-19
PLANNING FOR ON-CAMPUS K-12 EDUCATION DURING COVID-19 AUGUST 6, 2020 PLANNING FOR ON-CAMPUS K-12 EDUCATION DURING COVID-19 AUTHORS Rich Byrne, MITRE Corporation Gail H. Cassell, Harvard Medical School, Brigham and Women’s Hospital, Boston Matthew E. Downs, MITRE Corporation Florida International University John Halamka, Mayo Clinic Shayri M. Kansagra, MITRE Corporation Leavitt Partners Rakhee Palekar, MITRE Corporation Neelima Ramaraju, LLamasoft Kunal J. Rambhia, MITRE Corporation Kippy Rudy, Center for Mind and Culture Jay Schnitzer, MITRE Corporation Taylor Wilkerson, MITRE Corporation COALITION REVIEWERS Hannah Darrington, Leavitt Partners Mark R. Ginsberg, George Mason University Leigha Witt Humphries, Oak Ridge Associated Universities John Poelman, Leavitt Partners Jennifer Tyrell, Oak Ridge Associated Universities The complex decision-making regarding reopening of schools compels careful thought, planning, and collaboration, within and across communities. Through this document, the COVID-19 Healthcare Coalition provides clarifications, interpretations, and estimates that can be used as a resource by school leaders to develop and implement plans for returning to on-campus learning, in the context of the COVID-19 pandemic. This document summarizes guiding principles and lessons learned, to provide current information (as of publication date) as well as additional resources to facilitate discussions and decisions regarding return to on-campus learning policies. The reopening of schools—either to virtual or on-campus learning—is approaching quickly. Communities should give particular consideration to the socioeconomic challenges and disparities within their districts; the need for transparency in development and implementation of plans; and the provision of funding and resources to schools, teachers, and other school staff to ensure safety and efficacy of on-campus or virtual-learning environments. -

FFRDC Research and Development Survey: Fiscal Year 2012 Detailed Statistical Tables | NSF 14-302 | January 2014
FFRDC Research and Development Survey: Fiscal Year 2012 Detailed Statistical Tables | NSF 14-302 | January 2014 Ronda Britt Project Officer Research and Development Statistics Program (703) 292-7765 General Notes The data presented in this report were compiled from the National Science Foundation (NSF) FY 2012 Federally Funded Research and Development Center (FFRDC) Research and Development Survey. ICF International currently conducts the survey under contract to NSF. The reference period of this annual survey is the fiscal year of the surveyed FFRDC. The survey collects the separately budgeted R&D expenditures by source of funding and type of cost reported by FFRDCs. The FFRDC survey is administered in conjunction with the Higher Education Research and Development (HERD) Survey, previously the Survey of Research and Development Expenditures at Universities and Colleges (Academic R&D Survey). Prior to FY 2009, the resulting FFRDC data were published in the Academic R&D Expenditures series of detailed statistical tables. The FY 2008 FFRDC data were published both in the Academic R&D Expenditures report and separately in a FY 2008 report, establishing a new detailed statistical tables series solely for FFRDC data. Terms used are defined below. • Separately budgeted R&D expenditures. All funds expended for activities specifically organized to produce research outcomes. These activities are either commissioned by an agency external to the FFRDC or are separately budgeted by the FFRDC. • Expenditures. Funds actually spent by the FFRDC during its fiscal year. • Federally funded research and development centers. R&D-performing organizations that range in organizational structure from traditional contractor-owned/contractor-operated or government- owned/contractor-operated to structures in which degrees of contractor/government control and ownership vary. -

Federal It Modernization Summit December 13, 2018 | Marriott Metro Center | Washington, D.C
FEDERAL IT MODERNIZATION SUMMIT DECEMBER 13, 2018 | MARRIOTT METRO CENTER | WASHINGTON, D.C. On behalf of the Advanced Technology Academic Research Center, I am proud to announce the release of a White Paper documenting the MITRE-ATARC IT Modernization Collaboration Symposium held on December 13, 2018 in Washington, D.C. in conjunction with the ATARC Federal IT Modernization Summit. I would like to take this opportunity to recognize the following session leads for their contributions: MITRE Chair: Mano Malayanur Challenge Area 1: Cloud Adoption Industry Vice Chairs Shad Imam, Principal Cloud Engineer, Mulesoft Gaurav Pal, CEO and Founder, StackArmor MITRE Chair Howard Small, Principal Software Systems Engineer, MITRE Challenge Area 2: Contact Center of the Future Industry Chair Brian Boardman, Salesforce Practice Lead, IBM MITRE Chair Bruce Patterson, Principal Network Systems & Distributed Systems Engineer, MITRE Challenge Area 3: Customer Experience Industry Vice Chairs Jamie Bowerman, Senior Lead Technologist, Booz Allen Hamilton Lisa Waple, Director of Customer Experience, CGI MITRE Chair Tamara Ambrosio-Hemphill, Co-Department Head, MITRE Challenge Area 4: Data & Analytics Government Chair Pam Hird, Project Manager, USDA Industry Vice Chairs Chris Roberts, Solution Architect, Quest Software Pete Tseronis, Former CTO of DOE MITRE Chair Vidyababu Kuppusamy, Lead Software Systems Engineer, MITRE Challenge Area 5: IT Infrastructure Optimization Government Chair Mike Cassidy, CTO, DOJ Industry Vice Chairs Stephen Kovac, VP of Global -

Identifying Factors That Influence Trust in Automated Cars and Medical Diagnosis Systems
The Intersection of Robust Intelligence and Trust in Autonomous Systems: Papers from the AAAI Spring Symposium Identifying Factors that Influence Trust in Automated Cars and Medical Diagnosis Systems Michelle S. Carlson The MITRE Corporation, 202 Burlington Road, Bedford, MA 01730 [email protected] Munjal Desai Google Inc., 1600 Amphitheater Parkway, Mountain View, CA 94043 [email protected] Jill L. Drury The MITRE Corporation, 202 Burlington Road, Bedford, MA 01730 [email protected] Hyangshim Kwak United States Military Academy, West Point, NY 10997 [email protected] Holly A. Yanco The MITRE Corporation, 202 Burlington Road, Bedford, MA 01730 [email protected] Abstract 1. Introduction Our research goals are to understand and model the factors The past two decades have seen an increase in the number that affect trust in automation across a variety of application domains. For the initial surveys described in this paper, we of robot systems in use, and the trend is still continuing. selected two domains: automotive and medical. Specifically, According to a survey, 2.2 million domestic service robots we focused on driverless cars (e.g., Google Cars) and were sold in 2010 and the number is expected to rise to automated medical diagnoses (e.g., IBM’s Watson). There 14.4 million by 2014 (IFR 2011). Not only is the number were two dimensions for each survey: the safety criticality of robots in use increasing, but the number of application of the situation in which the system was being used and name-brand recognizability. We designed the surveys and domains that utilize robots is also increasing. -

Cyber Exercise Playbook
Cyber Exercise Jason Kick Playbook The views, opinions and/or findings contained in this report are those of The MITRE Corporation and should not be construed as an official government position, policy, or decision, unless designated by other documentation. November 2014 Approved for Public Release; Distribution Unlimited. 14-3929 This technical data was produced for the U.S. Government under Contract No. W15P7T-13-C-A802, and is subject to the Rights in Technical Data-Noncommercial Items clause at DFARS 252.227- 7013 (NOV 1995). ©2014 The MITRE Corporation. All rights reserved. MP140714 Wiesbaden, Germany Approved By Mr. Charles Best Date Project Leader ii Abstract This paper provides an overview of the cyber exercise process from inception to reporting. It introduces the terminology and life cycle of a cyber exercise and then focuses on the planning and execution aspects of such exercises, to include objectives, scenarios, reporting and assessment procedures, network architecture, tools, and lessons learned from utilizing the scenarios outlined during an exercise with Partner Nations. Reading this document and reviewing the reference materials should enable exercise planners to understand the purpose, objectives, planning, and execution processes for conducting cyber exercises. iii This page intentionally left blank. iv Acknowledgements Several MITRE staff members contributed to this paper, either by reviewing it or by writing certain sections. Thank you to everyone who took part in ensuring this paper’s accuracy and completeness, especially: • Mr. Nathan Adams • Mr. Dan Aiello • Mr. Charles Best • Mrs. Margaret MacDonald • Mr. John Modrich • Mr. Scott Wilson Several staff of the US Army also reviewed this paper. -

MITRE the MITRE Corporation's Center for Advanced Aviation
The MITRE Corporation’s Center for Advanced Aviation System Development he MITRE Corporation’s Center for Advanced MITRE/CAASD adds value to all ATM modernization Aviation System Development (MITRE/CAASD) programs and helps accomplish national objectives for Tis a federally funded research and development evolving ATM systems to be capable of handling center (FFRDC) sponsored by the Federal Aviation anticipated increases in traffic and greater diversity of Administration (FAA). The MITRE Corporation, a not- aircraft. for-profit national resource provides systems engineering, research and development, and MITRE/CAASD focus areas include: information technology support to governments around the globe. MITRE/CAASD supports the FAA and other • Architecture and System Engineering civil aviation authorities from its facilities in McLean, • Airport Capacity Improvements Virginia, about 20 minutes from Washington, D.C. • Advanced Decision Support Systems • Global Communications, Navigation, and Surveillance • Collaborative Decision Making • Modeling, Simulation, and Advanced Development MITRE/CAASD is committed to working in partnership with civil aviation organizations throughout the world to develop harmonized and integrated systems that promote safe and efficient global air traffic management. Our innovations in areas such as advanced automation systems for controller training, performance-based air traffic management systems for increased controller productivity and increased user benefits, conflict probe and resolution, the application of -
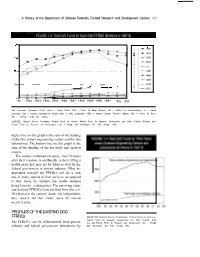
A History of the Department of Defense Federally Funded Research and Development Centers 137
A History of the Department of Defense Federally Funded Research and Development Centers 137 c I ---------------------------- ------ ----- -- 1oo- ----- -------- ------------------------ --- - -u-- o 1981 1982 1983 1984 1985 1986 1987 1988 1989 1990 1991 1992 1993 KEY: Aerospace =Aerospace Center; Arroyo = Arroyo Center; CNA = Center for Naval Analyses; IDA = lnstitute for DefenseAnalyses, LL = Lincoln Laboratory; LMI = Logistics Management Institute; Mitre = Mitre Corporation; NDRI = National Defense Research institute, PAF = Project Air Force; SEI = Software Engineering Institute. SOURCES. National Science Foundation, Federal Funds for Science, Federal Funds for Research, Development, and Other Scientific Activities, and Federal Funds for Research and Development, vols. I through XLII (Washington, DC. 1952 through 1994). higher line on this graph is the sum of the funding of the two system engineering centers and the two laboratories. The bottom line on this graph is the sum of the funding of the six study and analysis centers. The centers continued existence, over 50 years after their creation, is attributable to their filling a useful niche that may not be filled as well by the federal government or private industry. What in- dependent research the FFRDCs still do is now one of many aspects of their services, as opposed to their reason for existence (the notable exception being Lincoln, a laboratory). The surviving study and analysis FFRDCs have evolved from the con- flict between the centers’ desire for independent, basic research and their clients’ desire for concrete useful results. PROFILES OF THE EXISTING DOD FFRDCs SOURCES: National Science Foundation, Federal Funds for Science, Federal Funds for Research, Development, and Other Scientific Activi- The FFRDCs can be differentiated from private ties, and Federal Funds for Research and Development, vols.