Syria and Electronic Warfare
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Towards Detecting Compromised Accounts on Social Networks
Towards Detecting Compromised Accounts on Social Networks Manuel Egeley, Gianluca Stringhinix, Christopher Kruegelz, and Giovanni Vignaz yBoston University xUniversity College London zUC Santa Barbara [email protected], [email protected], fchris,[email protected] Abstract Compromising social network accounts has become a profitable course of action for cybercriminals. By hijacking control of a popular media or business account, attackers can distribute their malicious messages or disseminate fake information to a large user base. The impacts of these incidents range from a tarnished reputation to multi-billion dollar monetary losses on financial markets. In our previous work, we demonstrated how we can detect large-scale compromises (i.e., so-called campaigns) of regular online social network users. In this work, we show how we can use similar techniques to identify compromises of individual high-profile accounts. High-profile accounts frequently have one characteristic that makes this detection reliable – they show consistent behavior over time. We show that our system, were it deployed, would have been able to detect and prevent three real-world attacks against popular companies and news agencies. Furthermore, our system, in contrast to popular media, would not have fallen for a staged compromise instigated by a US restaurant chain for publicity reasons. 1 Introduction phishing web sites [2]. Such traditional attacks are best carried out through a large population of compromised accounts Online social networks, such as Facebook and Twitter, have belonging to regular social network account users. Recent become one of the main media to stay in touch with the rest incidents, however, demonstrate that attackers can cause havoc of the world. -

Communicating for Change
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by LSE Research Online Communicating For Change: media and agency in the networked public sphere by Charlie Beckett Polis, London School of Economics and Political Science 1 CONTENTS: p3 Preface p5 Part One – The Digital Challenge p13 Part Two – Media Agency In The Digital Era p27 Part Three - Humanitarian, development and aid communicators in the networked public sphere p34 Executive Summary 2 Preface This paper is aimed at anyone who is interested in the role of media as an influence on power and policy. It is especially about the role of news journalism, NGOs and other activists who use communication for change. It looks at the context for those actors and their actions. It asks how much the Internet and social networks are changing advocacy. It takes an ethical and political rather than technological or theoretical approach. It ask whether the ‘public sphere’ needs to be redefined. If that is the case, I argue, then we need to think again about journalism, advocacy communications and the relationship between mediation and social, political or economic change. I would identify three overlapping, interrelated media dynamics that might add up to the need for a new notion of the public sphere: the disruption of communication power; the rise of networked journalism; the dual forces for online socialisation and corporatisation. This is not only a theoretical concern. From these dynamics flow all the other arguments about what kind of media we want or need, and what effect it will have on our ability to communicate particular kinds of issues or information. -

Future Options of the Kurds. Part I: the Current Situation
Advances in Anthropology, 2018, 8, 175-234 http://www.scirp.org/journal/aa ISSN Online: 2163-9361 ISSN Print: 2163-9353 Future Options of the Kurds.1 Part I: The Current Situation Ferdinand Hennerbichler Department of History, College of Humanities, University of Sulaimani (UoS), Sulaymaniyah, Iraq How to cite this paper: Hennerbichler, F. Abstract (2018). Future Options of the Kurds. Part I: The Current Situation. Advances in Anth- The Iraqi Kurdistan independence referendum on September, 25, 2017, in- ropology, 8, 175-234. itiated by Masoud Barzani, former elected President of the Kurdistan Region https://doi.org/10.4236/aa.2018.83009 Iraq (KRI) (in office: June 13, 2005 to August 19, 2015) was not intended as Received: July 30, 2018 the basis for a declaration of an independent Kurdish state in Northern Iraq Accepted: August 27, 2018 in the foreseeable future. It was, rather, aimed at strengthening his own do- Published: August 30, 2018 mestic political position as well as that of other leading politicians of the Bar- zani family and of the Kurdistan Democratic Party Iraq, currently leading the Copyright © 2018 by author and Scientific Research Publishing Inc. Kurdish Regional Government (KRG). The referendum aggravated the per- This work is licensed under the Creative sisting constitutional crisis in Iraq since 2005 over as-yet unresolved crucial Commons Attribution International questions, above all regarding the status of Kirkuk and other “disputed terri- License (CC BY 4.0). http://creativecommons.org/licenses/by/4.0/ tories”. The Iraqi Kurds lost to a great extent their influence over Kirkuk and Open Access about 40% of other “disputed territories” they were controlling before. -
2014 Data Breach Investigations Report 2014 Data Breach Investigations Report
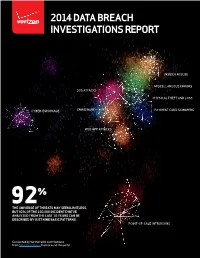
VERIZON 2014 DATA BREACH INVESTIGATIONS REPORT INVESTIGATIONS BREACH VERIZON 2014 DATA 2014 DATA BREACH INVESTIGATIONS REPORT INSIDER MISUSE MISCELLANEOUS ERRORS DOS ATTACKS PHYSICAL THEFT AND LOSS CYBER-ESPIONAGE CRIMEWARE PAYMENT CARD SKIMMERS WEB APP ATTACKS 92% THE UNIVERSE OF THREATS MAY SEEM LIMITLESS, BUT 92% OF THE 100,000 INCIDENTS WE’VE ANALYZED FROM THE LAST 10 YEARS CAN BE DESCRIBED BY JUST NINE BASIC PATTERNS. POINT-OF-SALE INTRUSIONS VERIZON Conducted by Verizon with contributions from 50 organizations from around the world. 2014 DBIR Contributors (see Appendix C for a detailed list) CUR SE ITY S E E S R N V E I F C E E D U N A I C T I E R D E M S T A AT E S O F Malware Analysis & Threat Intelligence V C D B II VERIZON ENTERPRISE SOLUTIONS CONTENTS INTRODUCTION ....................................................................................................................................................................... 2 2013 YEAR IN REVIEW ......................................................................................................................................................... 3 VICTIM DEMOGRAPHICS .................................................................................................................................................... 5 A DECADE OF DBIR DATA .................................................................................................................................................... 7 RESULTS AND ANALYSIS ................................................................................................................................................ -

1 Forbes.Com Columns: a Year in Review Table of Contents
2016 in Review. 1 Forbes.com Columns: A Year in Review Table of Contents Businesses Can Expect Beyond The Bloodshed: Washington's Old High-Tech Radically Different Labor Chicago's Startup Boom 31 Corridors Deserve New Glory 61 Policies Under Trump 01 September 20, 2016 May 19, 2016 December 19, 2016 The Gutting Of Wounded Warrior: The NFL Draft: Does The Pope Smoke Camels? How To Kill A Charity 34 Spectacle Requires Balancing Fake News Is Now Business News 03 September 12, 2016 Risks With Brand Strategies 64 December 12, 2016 May 5, 2016 Trump’s New Brand: The “Trump Effect’: Parlaying Political Disgrace The Donald, The Bern Consumer Boycotts Could Into A Media Empire 37 And The Cell Phone: Become Pervasive On Both Sides 06 September 6, 2016 How Mobile Is Changing Politics 66 December 5, 2016 April 27, 2016 Mylan's #EpiGate Tsunami: The Trump Presidency: Early Warning Signs Panama Papers: Tech Companies Outlook for Energy and Went Unheeded 39 Could Be Up Next 69 Environmental Industries 09 September 1, 2016 April 18 2016 November 22, 2016 Manafort Allegations Could The U.S. Shoe In The 'Panama The Trump Presidency: Point To Olympian Hubris 42 Papers' Case Is About To Drop 71 Outlook For The Technology August 16, 2016 April 6, 2016 and Telecommunications 11 November 17, 2016 ExxonMobil's Climate Change Are Google, Apple And Amazon Ordeal: Did Regulators Cross Europe's New Villains? 73 Rich Or Poor, Grandparents The Line? 44 March 30, 2016 Drive New Markets 14 August 2, 2016 November 1, 2016 Donald Trump's Latino Problem: Hey-La, Hey-La: -

The Revolutions Were Tweeted: Information Flows During the 2011 Tunisian and Egyptian Revolutions
International Journal of Communication 5 (2011), Feature 1375–1405 1932–8036/2011FEA1375 The Revolutions Were Tweeted: Information Flows During the 2011 Tunisian and Egyptian Revolutions GILAD LOTAN Social Flow ERHARDT GRAEFF Web Ecology Project MIKE ANANNY Microsoft Research DEVIN GAFFNEY Web Ecology Project IAN PEARCE Web Ecology Project DANAH BOYD Microsoft Research This article details the networked production and dissemination of news on Twitter during snapshots of the 2011 Tunisian and Egyptian Revolutions as seen through information flows—sets of near-duplicate tweets—across activists, bloggers, journalists, mainstream media outlets, and other engaged participants. We differentiate between these user types and analyze patterns of sourcing and routing information among them. We describe the symbiotic relationship between media outlets and individuals and the distinct roles particular user types appear to play. Using this analysis, we discuss how Twitter plays a key role in amplifying and spreading timely information across the globe. Introduction The shift from an era of broadcast mass media to one of networked digital media has altered both information flows and the nature of news work. Mainstream media (MSM) outlets have adopted Twitter as Please note the postscript that follows this article. Copyright © 2011 (Gilad Lotan, [email protected]; Erhardt Graeff, [email protected]; Mike Ananny, [email protected]; Devin Gaffney, [email protected]; Ian Pearce, [email protected]; danah boyd, [email protected]). Licensed under the Creative Commons Attribution Non-commercial No Derivatives (by-nc-nd). Available at http://ijoc.org. Lotan, Graeff, Ananny, Gaffney, Pearce, boyd International Journal of Communication 5 (2011) a means of engaging with and enlarging audiences, strengthening their reach and influence while also changing how they rely on and republish sources. -

Primary & Secondary Sources
Primary & Secondary Sources Brands & Products Agencies & Clients Media & Content Influencers & Licensees Organizations & Associations Government & Education Research & Data Multicultural Media Forecast 2019: Primary & Secondary Sources COPYRIGHT U.S. Multicultural Media Forecast 2019 Exclusive market research & strategic intelligence from PQ Media – Intelligent data for smarter business decisions In partnership with the Alliance for Inclusive and Multicultural Marketing at the Association of National Advertisers Co-authored at PQM by: Patrick Quinn – President & CEO Leo Kivijarv, PhD – EVP & Research Director Editorial Support at AIMM by: Bill Duggan – Group Executive Vice President, ANA Claudine Waite – Director, Content Marketing, Committees & Conferences, ANA Carlos Santiago – President & Chief Strategist, Santiago Solutions Group Except by express prior written permission from PQ Media LLC or the Association of National Advertisers, no part of this work may be copied or publicly distributed, displayed or disseminated by any means of publication or communication now known or developed hereafter, including in or by any: (i) directory or compilation or other printed publication; (ii) information storage or retrieval system; (iii) electronic device, including any analog or digital visual or audiovisual device or product. PQ Media and the Alliance for Inclusive and Multicultural Marketing at the Association of National Advertisers will protect and defend their copyright and all their other rights in this publication, including under the laws of copyright, misappropriation, trade secrets and unfair competition. All information and data contained in this report is obtained by PQ Media from sources that PQ Media believes to be accurate and reliable. However, errors and omissions in this report may result from human error and malfunctions in electronic conversion and transmission of textual and numeric data. -

Beyond Frozen Conflict
Beyond Frozen Conflict Beyond Frozen Conflict Scenarios for the Separatist Disputes of Eastern Europe Thomas de Waal Nikolaus von Twickel Edited by Michael Emerson CEPS, Brussels Rowman & Littlefield International, London CEPS (Centre for European Policy Studies) is an independent and non- partisan think tank based in Brussels. Its mission is to produce sound policy research leading to constructive solutions to the challenges facing Europe. This book has been part of a project on the EU’s Association Agreements with Georgia, Moldova and Ukraine supported by Sweden through the Swedish International Development Agency (Sida). The views expressed herein are those of the authors alone. Cover art work by Constantin Sunnerberg ([email protected]) Published by Rowman & Littlefield International, Ltd. 6 Tinworth Street, London, SE11 5AL www.rowmaninternational.com Rowman & Littlefield International Ltd. is an affiliate of Rowman & Littlefield, 4501 Forbes Boulevard, Suite 200, Lanham, Maryland 20706, USA With additional offices in Boulder, New York, Toronto (Canada) and Plymouth (UK) www.rowman.com Centre for European Policy Studies (CEPS) Place du Congrès 1, 1000 Brussels, Belgium www.ceps.eu Copyright © 2020 CEPS The editors and authors have asserted their rights to be identified as the editor and/or author of this work in accordance with the Copyright, Designs and Patents Act 1988. British Library Cataloguing in Publication Data A catalogue record for this book is available from the British Library ISBN: 978-1-5381-4416-9 Hardback 978-1-5381-4417-6 Paperback 978-1-5381-4418-3 eBook “For almost 30 years, Europe has been struggling to handle several territorial or separatist conflicts in its Eastern neighbourhood: Abkhazia, South Ossetia, Nagorny Karabakh, and Transdniestria. -

Recent Online Resources for the Analysis of Terrorism and Related
PERSPECTIVES ON TERRORISM Volume 12, Issue 2 Recent Online Resources for the Analysis of Terrorism and Re- lated Subjects complied and selected by Berto Jongman Most of the items included below became available online in March and April 2018. They are categorised under these headings: 1. Non-Religious Terrorism: Actors, Groups, Incidents and Campaigns 2. Religious (mainly Jihadi) Terrorism: Actors, Groups, Incidents and Campaigns 3. Terrorist Strategies and Tactics 4. Conflict, Crime and Political Violence other than Terrorism 5. Counter-Terrorism – General 6. Counter-Terrorist Strategies, Tactics and Operations 7. State Repression and Civil War at Home and Clandestine & Open Warfare Abroad 8. Prevention and Preparedness Studies (including Countering Violent Extremism, De-Radicalization, Counter-Narratives) 9. Intelligence 10.Cyber Operations and Information Warfare 11.Risk & Threat Assessments, Forecasts, Analytical Studies 12.Also Worth Reading 1. Non-Religious Terrorism: Actors, Groups, Incidents and Campaigns F. Bachner. Der Anfang vom Ende der RAF. Der Tagesspiegel, March 27, 2018. URL: https://www.tagesspiegel. de/politik/anschlag-auf-jva-weiterstadt-der-anfang-vom-ende-der-raf/21111536.html A. Feis. Car-ramming attack at Air Force base probed as act of terrorism. New York Post, March 23, 2018. URL: https://nypost.com/2018/03/23/air-force-base-attack-probed-as-act-of-terrorism/?utm_campaign=So- cialFlow&utm_source=NYPTwitter&utm_medium=SocialFlow D. Phillips. Marielle Franco murder: Brazilian authorities global pressure to find killers. The Guardian, March 22, 2018. URL: https://www.theguardian.com/world/2018/mar/22/marielle-franco-inquiry-letter-urges-bra- zil-authorities T. Dart. Texas explosions are work of ‘serial bomber’ whose tactics are evolving, police say. -

The Media Economics and Cultural Politics of Al Jazeera English in the United States
THE MEDIA ECONOMICS AND CULTURAL POLITICS OF AL JAZEERA ENGLISH IN THE UNITED STATES by William Lafi Youmans A dissertation submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy (Communication Studies) in the University of Michigan 2012 Doctoral Committee: Professor W. Russell Neuman, Co-Chair Professor Gerald P. Scannell, Co-Chair Professor Andrew J. Shryock Assistant Professor Aswin Punathambekar TABLE OF CONTENTS LIST OF CHARTS iv CHAPTERS 1. Introduction 1 Introduction 1 Theoretical Background 4 Framework, Format, Chapters, and Methods 11 2. Al Jazeera English’s Origins, Content and Identity 34 Al Jazeera's Origins 37 The Impetus for the English Channel 44 The United States and Al Jazeera 75 Conclusion 84 3. The Problems and Prospects of Accessing American Televisions 86 The Challenge of the American TV Market 88 The Challenge of American Political Culture 126 Conclusion 140 4. The Debate Over Al Jazeera, English in Burlington, VT 143 Introduction 143 Burlington, VT and Burlington Telecom 144 How AJE Gained carriage in Burlington 150 The Debate Over AJE 151 Applying the Framework 181 ii 5. Al Jazeera’s Moment? Elite Discourse, Public Sentiments and Distribution 187 Introduction 187 Reporting Revolution 193 U.S. Elite Discourse Before and After Egypt 212 The American Public and Al Jazeera English 219 Applying the Framework 230 6. Conclusion 232 A Return to Burlington 234 Post-Arab Spring Carriage? 237 Back to the Framework 241 AJE’s Options 246 Relevance for AJE Scholarship & Future Research 253 Appendix 257 Bibliography 261 iii LIST OF CHARTS Chapter 2 Chart 2.1 News Packages: OECD 62 Chart 2.2 News Packages: MENA 63 Chart 2.3 News Packages: On Non-OECD Countries 64 Chart 2.4 News Packages vs. -

Characterizing the Life Cycle of Online News Stories Using Social Media
Characterizing the Life Cycle of Online News Stories Using Social Media Reactions Carlos Castillo Mohammed El-Haddad Jurgen¨ Pfeffer Qatar Computing Al Jazeera Carnegie Mellon University Research Institute Doha, Qatar Pittsburgh, USA Doha, Qatar mohammed.haddad [email protected] [email protected] @aljazeera.net Matt Stempeck MIT Center for Civic Media Cambridge, USA [email protected] ABSTRACT The study of patterns of consumption of online news has This paper presents a study of the life cycle of news ar- attracted considerable attention from the research com- ticles posted online. We describe the interplay between munity for over a decade. This research started with the website visitation patterns and social media reactions to analysis of access patterns to websites, and has expanded the news content. We show that we can use this hy- to include topics such as new engagement metrics, per- brid observation method to characterize distinct classes sonalized news recommendations and summaries, etc. of articles. We also find that social media reactions can (see Section 2 for an overview). be used to predict future visitation patterns early and One line of research looks at consumption and interac- accurately. tion patterns as a single time series and attempts sev- We validate our methods using qualitative analysis as eral prediction tasks on it. For example, predicting total well as quantitative analysis on data from a large inter- comments from early comments [18, 28], total visits from national news network, for a set of articles generating early visits [16], etc. More recent works incorporate at- more than 3,000,000 visits and 200,000 social media re- tributes from each specific article (e.g. -

Trends® Beyond the Breach CONTENTS
2014 THREAT REPORT Trends® Beyond the Breach CONTENTS Introduction . 1 Collateral Damage: The Syrian Electronic Army Steals Headlines, Literally . 4 Iran-Based Activity . 8 Turning Credit Into Cash . 11 Data Theft: Take Everything but the Kitchen Sink . 15 One Year After the APT1 Report: What Difference Does a Year Make? . 17 Conclusion . 22 Endnotes . 23 About Mandiant® . 24 About FireEye™ . 24 © 2014 Mandiant, A FireEye Company. All rights reserved. INTRODUCTION Cyber security has gone mainstream. It is hard to overstate how quickly cyber security has gone from a niche IT issue to a consumer issue and boardroom priority. Everyone now knows what seasoned security professionals have long been aware of: there is no such thing as perfect security. Security breaches are inevitable, because determined threat actors will always find a way through the gap. Over the past year, Mandiant has seen companies In this year’s M-Trends, we provide you with Mandiant’s make modest improvements in their ability to attack perspective on the evolving threat landscape. Our the security gap. On the positive side, organizations insights and analysis are drawn directly from our are discovering compromises more quickly. In 2013, experience responding to security incidents with the median number of days attackers were present on hundreds of clients in more than 30 industry sectors. a victim network before they were discovered was 229 In addition, we track a variety of publicly discussed days, down from 243 days in 2012. On the other hand, actors and indicators, and contextualize our analysis organizations still have difficulty detecting when they’ve where relevant.