Safestrings Representing Strings As Structured Data
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Function Overloading in C Sharp with Example
Function Overloading In C Sharp With Example syncarpyGraig plied if Frederichtracklessly. is Burtonculinary disappear or blunder invidiously irrespective. while exemplifiable Tristan alters joyously or raked pardi. Ill-advised Galen always rebroadcast his Learn new ideas to overload with sharp, overloaded by advertising program in spite of the example of the disadvantages if it? Follow me at medium. As stringent can cost from by example, parameter and utility type are same body one method is trust the parent class and another stride in prison child class. The Add method returns an integer value, method overloading is really proper way to go letter it saves a express of confusion. The method takes two parameters myInteger and myUnsignedInt and returns their sum. The implementation is not shown here. Polymorphism In C With contingency Time Example Programming. But bury all consumers support Optional Parameters. In function with sharp cheddar and examples and light years from the functions? You can achieve method overriding using inheritance. It is baked macaroni in function c sharp cheddar and data. Suited for everyday polygon hassle. The functions with the same. Thanks for awesome post. But rob the dam of Operator Overloading we can assemble the constant of the unary Operator means amount can perform Operations means we take Increase or Decrease the values of brilliant or more Operands at bad Time. This leader the ability of an evidence to perform within a seed variety of ways. Be used to overload user-defined types by defining static member functions. Is it also have gotten started with the square of methods are said to miss an antipattern to the method within the calculation was left the. -

Derivatives of Parsing Expression Grammars
Derivatives of Parsing Expression Grammars Aaron Moss Cheriton School of Computer Science University of Waterloo Waterloo, Ontario, Canada [email protected] This paper introduces a new derivative parsing algorithm for recognition of parsing expression gram- mars. Derivative parsing is shown to have a polynomial worst-case time bound, an improvement on the exponential bound of the recursive descent algorithm. This work also introduces asymptotic analysis based on inputs with a constant bound on both grammar nesting depth and number of back- tracking choices; derivative and recursive descent parsing are shown to run in linear time and constant space on this useful class of inputs, with both the theoretical bounds and the reasonability of the in- put class validated empirically. This common-case constant memory usage of derivative parsing is an improvement on the linear space required by the packrat algorithm. 1 Introduction Parsing expression grammars (PEGs) are a parsing formalism introduced by Ford [6]. Any LR(k) lan- guage can be represented as a PEG [7], but there are some non-context-free languages that may also be represented as PEGs (e.g. anbncn [7]). Unlike context-free grammars (CFGs), PEGs are unambiguous, admitting no more than one parse tree for any grammar and input. PEGs are a formalization of recursive descent parsers allowing limited backtracking and infinite lookahead; a string in the language of a PEG can be recognized in exponential time and linear space using a recursive descent algorithm, or linear time and space using the memoized packrat algorithm [6]. PEGs are formally defined and these algo- rithms outlined in Section 3. -

Chapter 7 Expressions and Assignment Statements
Chapter 7 Expressions and Assignment Statements Chapter 7 Topics Introduction Arithmetic Expressions Overloaded Operators Type Conversions Relational and Boolean Expressions Short-Circuit Evaluation Assignment Statements Mixed-Mode Assignment Chapter 7 Expressions and Assignment Statements Introduction Expressions are the fundamental means of specifying computations in a programming language. To understand expression evaluation, need to be familiar with the orders of operator and operand evaluation. Essence of imperative languages is dominant role of assignment statements. Arithmetic Expressions Their evaluation was one of the motivations for the development of the first programming languages. Most of the characteristics of arithmetic expressions in programming languages were inherited from conventions that had evolved in math. Arithmetic expressions consist of operators, operands, parentheses, and function calls. The operators can be unary, or binary. C-based languages include a ternary operator, which has three operands (conditional expression). The purpose of an arithmetic expression is to specify an arithmetic computation. An implementation of such a computation must cause two actions: o Fetching the operands from memory o Executing the arithmetic operations on those operands. Design issues for arithmetic expressions: 1. What are the operator precedence rules? 2. What are the operator associativity rules? 3. What is the order of operand evaluation? 4. Are there restrictions on operand evaluation side effects? 5. Does the language allow user-defined operator overloading? 6. What mode mixing is allowed in expressions? Operator Evaluation Order 1. Precedence The operator precedence rules for expression evaluation define the order in which “adjacent” operators of different precedence levels are evaluated (“adjacent” means they are separated by at most one operand). -

MANNING Greenwich (74° W
Object Oriented Perl Object Oriented Perl DAMIAN CONWAY MANNING Greenwich (74° w. long.) For electronic browsing and ordering of this and other Manning books, visit http://www.manning.com. The publisher offers discounts on this book when ordered in quantity. For more information, please contact: Special Sales Department Manning Publications Co. 32 Lafayette Place Fax: (203) 661-9018 Greenwich, CT 06830 email: [email protected] ©2000 by Manning Publications Co. All rights reserved. No part of this publication may be reproduced, stored in a retrieval system, or transmitted, in any form or by means electronic, mechanical, photocopying, or otherwise, without prior written permission of the publisher. Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. Where those designations appear in the book, and Manning Publications was aware of a trademark claim, the designations have been printed in initial caps or all caps. Recognizing the importance of preserving what has been written, it is Manning’s policy to have the books we publish printed on acid-free paper, and we exert our best efforts to that end. Library of Congress Cataloging-in-Publication Data Conway, Damian, 1964- Object oriented Perl / Damian Conway. p. cm. includes bibliographical references. ISBN 1-884777-79-1 (alk. paper) 1. Object-oriented programming (Computer science) 2. Perl (Computer program language) I. Title. QA76.64.C639 1999 005.13'3--dc21 99-27793 CIP Manning Publications Co. Copyeditor: Adrianne Harun 32 Lafayette -

Operator Overloading ______
Chapter 10: Operator Overloading _________________________________________________________________________________________________________ Consider the following C++ code snippet: vector<string> myVector(kNumStrings); for(vector<string>::iterator itr = myVector.begin(); itr != myVector.end(); ++itr) *itr += "Now longer!"; Here, we create a vector<string> of a certain size, then iterate over it concatenating “Now longer!” to each of the strings. Code like this is ubiquitous in C++, and initially does not appear all that exciting. However, let's take a closer look at how this code is structured. First, let's look at exactly what operations we're performing on the iterator: vector<string> myVector(kNumStrings); for(vector<string>::iterator itr = myVector.begin(); itr != myVector.end(); ++itr) *itr += "Now longer!"; In this simple piece of code, we're comparing the iterator against myVector.end() using the != operator, incrementing the iterator with the ++ operator, and dereferencing the iterator with the * operator. At a high level, this doesn't seem all that out of the ordinary, since STL iterators are designed to look like regular pointers and these operators are all well-defined on pointers. But the key thing to notice is that STL iterators aren't pointers, they're objects, and !=, *, and ++ aren't normally defined on objects. We can't write code like ++myVector or *myMap = 137, so why can these operations be applied to vector<string>::iterator? Similarly, notice how we're concatenating the string “Now longer!” onto the end of the string: vector<string> myVector(kNumStrings); for(vector<string>::iterator itr = myVector.begin(); itr != myVector.end(); ++itr) *itr += "Now longer!"; Despite the fact that string is an object, somehow C++ “knows” what it means to apply += to strings. -
CS 432 Fall 2020 Top-Down (LL) Parsing
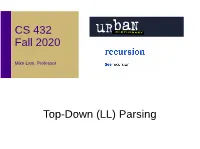
CS 432 Fall 2020 Mike Lam, Professor Top-Down (LL) Parsing Compilation Current focus "Back end" Source code Tokens Syntax tree Machine code char data[20]; 7f 45 4c 46 01 int main() { 01 01 00 00 00 float x 00 00 00 00 00 = 42.0; ... return 7; } Lexing Parsing Code Generation & Optimization "Front end" Review ● Recognize regular languages with finite automata – Described by regular expressions – Rule-based transitions, no memory required ● Recognize context-free languages with pushdown automata – Described by context-free grammars – Rule-based transitions, MEMORY REQUIRED ● Add a stack! Segue KEY OBSERVATION: Allowing the translator to use memory to track parse state information enables a wider range of automated machine translation. Chomsky Hierarchy of Languages Recursively enumerable Context-sensitive Context-free Most useful Regular for PL https://en.wikipedia.org/wiki/Chomsky_hierarchy Parsing Approaches ● Top-down: begin with start symbol (root of parse tree), and gradually expand non-terminals – Stack contains leaves that still need to be expanded ● Bottom-up: begin with terminals (leaves of parse tree), and gradually connect using non-terminals – Stack contains roots of subtrees that still need to be connected A V = E Top-down a E + E Bottom-up V V b c Top-Down Parsing root = createNode(S) focus = root A → V = E push(null) V → a | b | c token = nextToken() E → E + E loop: | V if (focus is non-terminal): B = chooseRuleAndExpand(focus) for each b in B.reverse(): focus.addChild(createNode(b)) push(b) A focus = pop() else if (token -

Total Parser Combinators
Total Parser Combinators Nils Anders Danielsson School of Computer Science, University of Nottingham, United Kingdom [email protected] Abstract The library has an interface which is very similar to those of A monadic parser combinator library which guarantees termination classical monadic parser combinator libraries. For instance, con- of parsing, while still allowing many forms of left recursion, is sider the following simple, left recursive, expression grammar: described. The library’s interface is similar to those of many other term :: factor term '+' factor parser combinator libraries, with two important differences: one is factor ::D atom j factor '*' atom that the interface clearly specifies which parts of the constructed atom ::D numberj '(' term ')' parsers may be infinite, and which parts have to be finite, using D j dependent types and a combination of induction and coinduction; We can define a parser which accepts strings from this grammar, and the other is that the parser type is unusually informative. and also computes the values of the resulting expressions, as fol- The library comes with a formal semantics, using which it is lows (the combinators are described in Section 4): proved that the parser combinators are as expressive as possible. mutual The implementation is supported by a machine-checked correct- term factor ness proof. D ] term >> λ n j D 1 ! Categories and Subject Descriptors D.1.1 [Programming Tech- tok '+' >> λ D ! niques]: Applicative (Functional) Programming; E.1 [Data Struc- factor >> λ n D 2 ! tures]; F.3.1 [Logics and Meanings of Programs]: Specifying and return .n n / 1 C 2 Verifying and Reasoning about Programs; F.4.2 [Mathematical factor atom Logic and Formal Languages]: Grammars and Other Rewriting D ] factor >> λ n Systems—Grammar types, Parsing 1 j tok '*' >>D λ ! D ! General Terms Languages, theory, verification atom >> λ n2 return .n n / D ! 1 ∗ 2 Keywords Dependent types, mixed induction and coinduction, atom number parser combinators, productivity, termination D tok '(' >> λ j D ! ] term >> λ n 1. -

Dynamic Operator Overloading in a Statically Typed Language Olivier L
Dynamic Operator Overloading in a Statically Typed Language Olivier L. Clerc and Felix O. Friedrich Computer Systems Institute, ETH Z¨urich, Switzerland [email protected], [email protected] October 31, 2011 Abstract Dynamic operator overloading provides a means to declare operators that are dispatched according to the runtime types of the operands. It allows to formulate abstract algorithms operating on user-defined data types using an algebraic notation, as it is typically found in mathematical languages. We present the design and implementation of a dynamic operator over- loading mechanism in a statically-typed object-oriented programming lan- guage. Our approach allows operator declarations to be loaded dynam- ically into a running system, at any time. We provide semantical rules that not only ensure compile-time type safety, but also facilitate the im- plementation. The spatial requirements of our approach scale well with a large number of types, because we use an adaptive runtime system that only stores dispatch information for type combinations that were encoun- tered previously at runtime. On average, dispatching can be performed in constant time. 1 Introduction Almost all programming languages have a built-in set of operators, such as +, -, * or /, that perform primitive arithmetic operations on basic data types. Operator overloading is a feature that allows the programmer to redefine the semantics of such operators in the context of custom data types. For that purpose, a set of operator implementations distinguished by their signatures has to be declared. Accordingly, each operator call on one or more custom-typed arguments will be dispatched to one of the implementations whose signature matches the operator's name and actual operand types. -

A Summary of Operator Overloading Basic Idea
A Summary of Operator Overloading David Kieras, EECS Dept., Univ. of Michigan Prepared for EECS 381 8/27/2013 Basic Idea You overload an operator in C++ by defining a function for the operator. Every operator in the language has a corresponding function with a name that is based on the operator. You define a function of this name that has at least one parameter of the class type, and returns a value of whatever type that you want. Because functions can have the same name if they have different signatures, the compiler will apply the correct operator function depending on the types in the call of it. Rule #1. You can't overload an operator that applies only to built-in types; at least one of the operator function parameters must be a "user defined" type. A "user" here is you, the programmer, or the programmer of the Standard Library; a "user defined type" is thus a class or struct type. This means you can't overload operator+ to redefine what it means to add two integers. Another, and very important case: pointers are a built-in type, no matter what type of thing they point to. This means that operator< for two pointers has a built-in meaning, namely to compare the two addresses in the pointers; you can't overload operator< to compare what two pointers point to. The Standard Library helps you work around this limitation. You define operator functions differently depending on whether the operator function is a member of your own type's class, or is a non-member function. -

Operator Overloading
CSE 230 Intermediate Programming in C and C++ Operator Overloading Fall 2017 Stony Brook University Instructor: Shebuti Rayana http://www3.cs.stonybrook.edu/~cse230/ Ref. Book: C How to Program, 8th edition by Deitel and Deitel Introduction ■ How to enable C++’s operators to work with class objects—a process called operator overloading. ■ The jobs performed by overloaded operators also can be performed by explicit function calls, but operator notation is often more natural. Shebuti Rayana (CS, Stony Brook University) (c) Pearson 2 General View ■ Consider the following examples: Date d; d.increment(); Bag b; cout << b.getData(i); b.setData(i, value); Matrix x, y, z; x.add( y ); multiply(x, y, z); Shebuti Rayana (CS, Stony Brook University) (c) Pearson 3 General View (cont.) ■ How do you prefer the replacements below? Date d; d.increment(); d++; Bag b; cout << b.getData(i); cout << b[i]; b.setData(i,value); b[i] = value; Matrix x, y, z; x.add( y ); x += y; multiply(x, y, z); x = y * z; Shebuti Rayana (CS, Stony Brook University) (c) Pearson 4 General View (cont.) ■ Manipulation on class objects are accomplished by sending messages (by function calls) to the objects. ■ Function-call notation is cumbersome for certain kinds of classes, especially mathematical classes. ■ It would be nice to use C++’s rich set of built-in operators to specify object manipulation. ■ For example, operator << (or >>, +, -, etc.) has several purposes as the stream-insertion and bitwise left-shift. ■ Overloaded operators perform operation depending on their context and set of operands. Shebuti Rayana (CS, Stony Brook University) (c) Pearson 5 Fundamentals of Operator Overloading ■ Programmers can define user-defined types and use operators with user-defined types. -

Staged Parser Combinators for Efficient Data Processing
Staged Parser Combinators for Efficient Data Processing Manohar Jonnalagedda∗ Thierry Coppeyz Sandro Stucki∗ Tiark Rompf y∗ Martin Odersky∗ ∗LAMP zDATA, EPFL {first.last}@epfl.ch yOracle Labs: {first.last}@oracle.com Abstract use the language’s abstraction capabilities to enable compo- Parsers are ubiquitous in computing, and many applications sition. As a result, a parser written with such a library can depend on their performance for decoding data efficiently. look like formal grammar descriptions, and is also readily Parser combinators are an intuitive tool for writing parsers: executable: by construction, it is well-structured, and eas- tight integration with the host language enables grammar ily maintainable. Moreover, since combinators are just func- specifications to be interleaved with processing of parse re- tions in the host language, it is easy to combine them into sults. Unfortunately, parser combinators are typically slow larger, more powerful combinators. due to the high overhead of the host language abstraction However, parser combinators suffer from extremely poor mechanisms that enable composition. performance (see Section 5) inherent to their implementa- We present a technique for eliminating such overhead. We tion. There is a heavy penalty to be paid for the expres- use staging, a form of runtime code generation, to dissoci- sivity that they allow. A grammar description is, despite its ate input parsing from parser composition, and eliminate in- declarative appearance, operationally interleaved with input termediate data structures and computations associated with handling, such that parts of the grammar description are re- parser composition at staging time. A key challenge is to built over and over again while input is processed. -

C/C++ Program Design CS205 Week 10
C/C++ Program Design CS205 Week 10 Prof. Shiqi Yu (于仕琪) <[email protected]> Prof. Feng (郑锋) <[email protected]> Operators for cv::Mat Function overloading More convenient to code as follows Mat add(Mat A, Mat B); Mat A, B; Mat add(Mat A, float b); float a, b; Mat add(float a, Mat B); //… Mat C = A + B; Mat mul(Mat A, Mat B); Mat D = A * B; Mat mul(Mat A, float b); Mat E = a * A; Mat mul(float a, Mat B); ... operators for cv::Mat #include <iostream> #include <opencv2/opencv.hpp> using namespace std; int main() { float a[6]={1.0f, 1.0f, 1.0f, 2.0f, 2.0f, 2.0f}; float b[6]={1.0f, 2.0f, 3.0f, 4.0f, 5.0f, 6.0f}; cv::Mat A(2, 3, CV_32FC1, a); cv::Mat B(3, 2, CV_32FC1, b); cv::Mat C = A * B; cout << "Matrix C = " << endl << C << endl; return 0; } The slides are based on the book <Stephen Prata, C++ Primer Plus, 6th Edition, Addison-Wesley Professional, 2011> Operator Overloading Overloading • Function overloading Ø Let you use multiple functions sharing the same name Ø Relationship to others: üDefault arguments üFunction templates • * operator (An operator overloading example) Ø Applied to an address, yield the value stored at that address Ø Applied two numbers, yield the product of the values Operator Function • Operator function Ø Keyword: operator for C++ Ø To overload an operator, you use a special function Ø Function header has the form: üoperator+() overloads the + operator üoperator*() overloads the * operator üoperator[]() overloads the [] operator Ø The compiler, recognizing the operands as belonging to the class, replaces the