Enhancing Legacy Software System Analysis by Combining Behavioural and Semantic Information Sources
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Convergence of Modeling and Programming
The Convergence of Modeling and Programming: Facilitating the Representation of Attributes and Associations in the Umple Model-Oriented Programming Language by Andrew Forward PhD Thesis Presented to the Faculty of Graduate and Postdoctoral Studies in partial fulfillment of the requirements for the degree Doctor of Philosophy (Computer Science1) Ottawa-Carleton Institute for Computer Science School of Information Technology and Engineering University of Ottawa Ottawa, Ontario, K1N 6N5 Canada © Andrew Forward, 2010 1 The Ph.D. program in Computer Science is a joint program with Carleton University, administered by the Ottawa Carleton Institute for Computer Science Acknowledgements A very special, and well-deserved, thank you to the following: a) Dr. Timothy C. Lethbridge. Tim has been a mentor of mine for several years, first as one of my undergraduate professors, later as my Master’s supervisor. Tim has again helped to shape my approach to software engineering, research and academics during my journey as a PhD candidate. b) The Complexity Reduction in Software Engineering (CRUISE) group and in particular Omar Badreddin and Julie Filion. Our weekly meetings, work with IBM, and the collaboration with the development of Umple were of great help. c) My family and friends. Thank you and much love Ayana; your support during this endeavor was much appreciated despite the occasional teasing about me still being in school. To my mom (and editor) Jayne, my dad Bill, my sister Allison and her husband Dennis. And, to my friends Neil, Roy, Van, Rob, Pat, and Ernesto – your help will be forever recorded in my work. Finally a special note to Ryan Lowe, a fellow Software Engineer that helped to keep my work grounded during our lengthy discussion about software development – I will miss you greatly. -

An Open Source Software Selection Process and a Case Study
AN OPEN SOURCE SOFTWARE SELECTION PROCESS AND A CASE STUDY A Record of Study by GUOBIN HE Submitted to the Office of Graduate Studies of Texas A&M University in partial fulfillment of the requirements for the degree of DOCTOR OF ENGINEERING August 2007 Major Subject: Engineering College of Engineering AN OPEN SOURCE SOFTWARE SELECTION PROCESS AND A CASE STUDY A Record of Study by GUOBIN HE Submitted to the Office of Graduate Studies of Texas A&M University in partial fulfillment of the requirements for the degree of DOCTOR OF ENGINEERING Approved by: Chair of Committee, Dick B. Simmons Committee Members, William M. Lively Jianer Chen Sheng-Jen Hsieh John Fierstien Head of Doctor of Engineering Programs, N.K. Anand August 2007 Major Subject: Engineering College of Engineering iii ABSTRACT An Open Source Software Selection Process and a Case Study. (August 2007) Guobin He, B.S., National University of Defense Technology; M.S., Beijing University of Aeronautics and Astronautics Chair of Advisory Committee: Dr. Dick B. Simmons In this study, I design an empirical open source software selection process, which reuses some ideas from Commercial Off-the-Shelf selection methods and addresses the characteristics of the open source software. Basically, it consists of three basic steps: identification, screening and evaluation. The identification step is to find all possible alternatives to open source software that can meet the high level requirements. The next step is screening, in which the refined requirements are applied to filter the alternatives. The evaluation step is based on the Analytic Hierarchy Process, in which the alternatives are inspected from functional suitability, source code, support strength and popularity. -

UML Modelleme Araçlarının Pratik Kullanım Için Analizi
UML Modelleme Araçlarının Pratik Kullanım için Analizi Mert Ozkaya1 and Ferhat Erata2 1 Yeditepe Üniversitesi , Ataşehir, İstanbul [email protected] 2 UNIT Bilgi Teknolojileri R&D Ltd., Bornova, Izmir [email protected] Özet. Günümüzde, Unified Modeling Language(UML) pratisyenler tarafından en sık tercih edilen yazılım sistemi modelleme ve tasarlama notasyonu olarak kabul edilmektedir. UML, aynı zamanda, birçok yazılım modelleme aracı tarafın- dan desteklenmektedir, ve bu araçlar sayesinde, pratisyenler yazılım sistem- lerini kolayca UML notasyonunu kullanarak modelleyebilir ve analiz, yazılım kodu üretme, ve işbirliği gibi birçok faydalı değişik işlemler gerçekleştirebilirler. Bu çalışmada, tanınan 11 farklı UML modelleme aracını pratisyenlerin UML’i benimsemeleri açısından önemli olduğunu düşündüğümüz bir grup gereksinim bakımından analiz ettik. Bu gereksinimler başlıca, modellerin tasarımı, model analizi, modelden kod üretme, iş-birliği halinde modelleme, ve genişletilebilir- lik olmaktadır. Model tasarımı gereksinimi, modelleme araçlarının UML diya- gramlarına olan destekleri, yazılım modelleme bakış-açılarına olan destekleri, ve büyük ve karmaşık yazılım modellerinin tasarımına olan destekleri açıların- dan ele alınmaktadır. Model analizi gereksinimi, simülasyon ve doğrulama (hem önceden tanımlanmış doğrulama hem de kullanıcı tanımlı doğrulama) gereksin- imlerine olan destek bakımından incelenmektedir. İş-birliği halinde modelleme gereksinimi ise, senkron ve asenkron olarak çoklu kullanıcı desteği, görev yöne- -

Seminario De Herramientas
Seminario de Herramientas Instalación y uso básico de una herramienta UML: BOUML Otras herramientas del laboratorio Laura Barros Computadores y Tiempo Real ProConDis 2009 1 1 Características Herramienta UML 2.0 Software libre. Puede ser redistribuida y/o modificada bajo los términos de la Licencia Pública General (General Public License, GNU). Permite especificar y generar código C++, Java, IDL, PHP y Python. Multiplataforma: Linux, Windows, MacOS Es rápida y no consume mucha memoria Instalación : Descargar el programa: http://bouml.free.fr/download.html Windows: Bouml_4.15_setup.exe z Ejecutar el Setup y seguir las instrucciones. Linux: existen paquetes para las distribuciones principales. Manual de usuario: http://bouml.free.fr/doc/index.html Santander, 2009 BOUML L.Barros 2 2 Crear un proyecto nuevo Al iniciar BOUML nos pide un identificador del desarrollador (BOUML_ID): si varios desarrolladores van a trabajar con el mismo modelo, se debe especificar esta variable de entorno Windows: start > settings > control panel > system > advanced > environmentvariables. Crear el proyecto: Project => New Guardar el proyecto: se indica el directorio donde se guardará el proyecto. Nota: la carpeta debe llamarse como el fichero .prj Indicar lenguaje de desarrollo: Pestaña Languages=> Java default definition Santander, 2009 BOUML L.Barros 3 3 Pantalla principal Elementos estructurales Diagramas Documentación Santander, 2009 BOUML L.Barros 4 4 Ejemplo de uso: Creación de un diagrama de clases Generar una vista de clases: Botón derecho en el -

Execution of UML Models: a Systematic Review of Research and Practice
Software & Systems Modeling https://doi.org/10.1007/s10270-018-0675-4 REGULAR PAPER Execution of UML models: a systematic review of research and practice Federico Ciccozzi1 · Ivano Malavolta2 · Bran Selic3 Received: 11 July 2017 / Revised: 23 March 2018 / Accepted: 31 March 2018 © The Author(s) 2018 Abstract Several research efforts from different areas have focused on the execution of UML models, resulting in a diverse and complex scientific body of knowledge. With this work, we aim at identifying, classifying, and evaluating existing solutions for the execution of UML models. We conducted a systematic review in which we selected 63 research studies and 19 tools among over 5400 entries by applying a systematic search and selection process. We defined a classification framework for characterizing solutions for UML model execution, and we applied it to the 82 selected entries. Finally, we analyzed and discussed the obtained data. From the analyzed data, we drew the following conclusions: (i) There is a growing scientific interest on UML model execution; (ii) solutions providing translational execution clearly outnumber interpretive solutions; (iii) model-level debugging is supported in very few cases; (iv) only a few research studies provide evidence of industrial use, with very limited empirical evaluations; (v) the most common limitation deals with coverage of the UML language. Based on these observations, we discuss potential research challenges and implications for the future of UML model execution. Our results provide a concise overview of states of the art and practice for UML model execution intended for use by both researchers and practitioners. Keywords UML · Model execution · Code generation · Model compilation · Model interpretation · Systematic review 1 Introduction support concepts specific to individual domains, organiza- tions, or projects. -

A Model-Driven Architecture Based Evolution Method and Its Application in an Electronic Learning System
A Model-Driven Architecture based Evolution Method and Its Application in An Electronic Learning System PhD Thesis Yingchun Tian Software Technology Research Laboratory De Montfort University October, 2012 To my husband, Delin Jing and my mum, Ning Zhang for their love and support Declaration Declaration I declare that the work described in this thesis was originally carried out by me during the period of registration for the degree of Doctor of Philosophy at De Montfort University, U.K., from October 2008 to December 2011. It is submitted for the degree of Doctor of Philosophy at De Montfort University. Apart from the degree that this thesis is currently applying for, no other academic degree or award was applied for by me based on this work. I Acknowledgements Acknowledgements For many years I had been dreaming about receiving a PhD, I would like to thank many people who helped me in achieving this dream in different ways since I undertook the work of this thesis. My deepest gratitude goes to my supervisor, Professor Hongji Yang, for his guidance, support and encouragement throughout my PhD career. He always provided me with many invaluable comments and suggestions for the improvement of the thesis. I am grateful for his leading role fostering my academic, professional and personal growth. Many thanks go to Professor Hussein Zedan and Doctor Wenyan Wu, for examining my PhD thesis and providing many helpful suggestions. My research career will benefit tremendously from the research methodologies to which Professor Zedan and Doctor Wu introduced me. I would like to thank colleagues in Software Technology Research Laboratory at De Montfort University, for their support and feedback, and for providing such a stimulating working atmosphere, Professor Hussein Zedan, Doctor Feng Chen, Doctor Amelia Platt, Doctor Antonio Cau, and many other colleagues. -
Braintool V2.0 for Software Modeling in UML
Applied Computer Systems doi: 10.1515/acss-2014-0011 _______________________________________________________________________________________________ 2014/16 BrainTool v2.0 for Software Modeling in UML Oksana Nikiforova1, Ludmila Kozacenko2, Dainis Ungurs3, Dace Ahilcenoka4, Andrejs Bajovs5, Nadezda Skindere6, Konstantins Gusarovs7, Maris Jukss8, 1–7Riga Technical University, Latvia, 8McGill University, Canada Abstract – It is a modern trend to develop a CASE tool for this paper is to present current research results achieved in the system modeling with an ability to transform models defined in transformation of the two-hemisphere model into the UML different notations and also to generate a program code. Such a diagrams and to introduce the tool supporting the approach. system modeling tool tries to bridge the gap between the system specification and the software components. A tool called The paper is structured as follows. The required BrainTool has been developed for generation of the UML functionality and main components of the tool suitable for diagrams from the initial presentation of problem domain by the system modeling and model transformation at the different two-hemisphere model. The paper presents the main components levels of abstraction are specified in Section II. The of BrainTool and compares it to other system modeling tools. components needed to implement such a tool are defined in Section III, where they are expressed by the components of Keywords – BrainTool, system modeling tool, two-hemisphere model, Unified Modeling Language (UML). BrainTool – the tool for the creation of the two-hemisphere model, UML diagrams generation and export them to some UML compatible tool. The authors analyse the variety of I. INTRODUCTION modern system modelling and code generation tools and define the position of BrainTool among them in Section IV. -
Open Source Tools for Programming Open
Open Source Software (List compiled by Mr. S. Baskar, CEO, LinuXpert Systems, Chennai) OPEN SOURCE TOOLS FOR PROGRAMMING * Git - Version Control System * Eclipse - C/C++/Java/PHP IDE * IntelliJ - Platform Developer Tools * NetBeans - C/C++/Java/HTML5 IDE * .NET Core - A Free Cross Platform * Ruby on Rails - For Web Applications * Node.js® - JavaScript Runtime * Bootstrap - Toolkit for HTML, CSS & JS * TensorFlow - Machine Learning Lib * Ansible - Automation for Everyone OPEN SOURCE TOOLS FOR SECURITY * Nmap - Free Security Scanner * OpenVAS - Vulnerability Scanner * Metasploit - Penetration Testing * Wireshark Network Protocol Analyser * Snort - Network Intrusion Detection * OSSEC - Intrusion Detection System * Kali - Advanced Penetration Testing * Nikto2 - Web Server Scanner * Nessus - Vulnerability Assessment * John the Ripper Password Cracker OPEN SOURCE TOOLS FOR EMBEDDED SYSTEMS * Yocto Project - Make Embedded Linux * FreeRTOS™ - X Platform RTOS Kernel * GNU Embedded Toolchain for ARM * uClibc - C library for Embedded Linux Page 1 Open Source Software (List compiled by Mr. S. Baskar, CEO, LinuXpert Systems, Chennai) * BusyBox - For use in Embedded Linux * Buildroot - Embedded Linux Easy now * STM32CubeIDE - Multi-OS Dev Tool * PSoC® Creator™ - PSoC Design IDE * OpenEmbedded - Frmwork for e-Linux * ARM Mbed OS for Internet of Things OPEN SOURCE DATABASES * MySQL Relational Database * PostgreSQL Relational Database * MariaDB Relational Database * SQLite Embedded Database * Apache Cassandra Database * Timescale Database for IoT * Neo4J - Leader in Graph Databases * MongoDB Non-Relational Database * CouchDB - from Big Data to Mobile * RethinkDB for the Realtime Web * CockroachDB - Ultra-resilient SQL OPEN SOURCE TOOLS FOR MODELLING (1) * StarUML3 - Agile & Concise Modelling * ArgoUML - UML Modelling Tool * BOUML - Free UML 2 Toolbox * Eclipse UML Generators * Dia - Draw Structured Diagrams * GenMyModel - Online Modeling * Umbrello - The UML Modeller * Papyrus - Modeling Environment Page 2 Open Source Software (List compiled by Mr. -
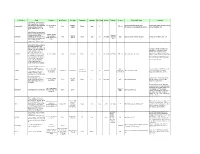
Othertoolcriteria.Pdf
Tool/Project What Relevance Host Project Principals Framework Language Dev. Team Activity Platform License Project Web Pages Comments A Java-based open source free UML modelling tool, follows the UML standard. Can forward and low (too small, too Unaligned http://amateras.sourceforge.jp/cgi- Limited UML (Class, Use case, Activity, AmaterasUML None Eclipse Java 2 EPL 1.0 reverse engineer Java code. limited) (Japan) bin/fswiki_en/wiki.cgi?page=AmaterasUML and Seq diagrams only) Eclipse Public License -v 1.0 EPL . AndroMDA is a code generation framework that follows the model medium (generic driven architecture (MDA) Windows code generation Matthias AndroMDA paradigm. It takes a UML model None Maven Java 15 Increasing (.NET)/any BSD http://www.andromda.org/index.php Complements existing UML tools facility, but limited in Bohlen from a CASE-tool and generates Java scope) classes and deployable components (J2EE or other). UML plugin for Eclipse based on the popular ArgoUML open source tool; Reverse engineering reused the original code base from and code generation available in ArgoUML but combined it with the multiple languages included Eclipse UML 2 project sources; Java, C++, PHP, and others. however, the migration to UML 2 and ArgoEclipse Also supports model generation low (just starting) Own Tom Morris Eclipse Java 5 Increasing any Eclipse EPL 1.0 http://argoeclipse.tigris.org/ Eclipse is in its early stages and it is not for AndroMDA for MDA/MDD clear how big the community is, but it style development; Supports all seems relatively small now (students standard UML diagram types and a few enthusiasts) and includes an innovative design critiquing facility to provide feedback during design. -

Universidad Americana Facultad De Ingeniería
UNIVERSIDAD AMERICANA FACULTAD DE INGENIERÍA Diseño y desarrollo de un Sistema de registro y control de socios, usuarios y aranceles de la sociedad de gestión NICAUTOR Br. María Gabriela Conrado García. Monografía para optar al grado de: Ingeniero en Sistemas Profesor tutor: Ing. Pablo Hurtado Managua, Nicaragua, Junio, 2008 Dedicatoria El presente trabajo está dedicado a los seres más importantes de mi vida: En primer lugar a Dios, puesto que el me concedió la vida y sabiduría necesaria para elaborarlo, En segundo lugar a mi madre a quien le debo todo lo que soy, En tercer lugar a mi sobrina Hillary, quien con su nacimiento ha inspirado mis deseos de superarme. Agradecimiento Son muchas las personas que han influido en la culminación de este logro, sin embargo quiero hacer referencia a las siguientes: Dios en primer lugar, quien ha sido el motor de mi vida, la luz que guía mi sendero y el proveedor de todas las bendiciones que han llegado a mi vida. Gracias Jesucristo por permitirme cumplir una mas de mis metas. A mi madre, con quien tengo una deuda in cuantificable, ya que con sacrificio y esmero me proveyó no solo de bienes materiales sino de amor, comprensión y apoyo. Este logro también es de ella. A mi tutor el Ingeniero Pablo hurtado quien me apoyo en todo momento compartiendo conmigo sus conocimientos y brindándome su ayuda incondicional no dudando en ningún momento de mi capacidad. A todos mis amigos quienes han compartido conmigo largas horas de sacrificio y abnegación, apoyándome cuando las inclemencias de la vida me sacudieron con mayor fuerza. -
1 Repcovtempl STR IES
Data State of Play Compliance Testing and Interoperability Checking S. Viganó TXT e-solutions M. Millot European Commission DG JRC, Institute for Environment and Sustainability EUR 23045 EN - 2007 The mission of the Institute for Environment and Sustainability is to provide scientific-technical support to the European Union’s Policies for the protection and sustainable development of the European and global environment. European Commission Joint Research Centre Institute for Environment and Sustainability Contact information Michel Millot Address: European Commission, Joint Research Centre, Institute for Environment and Sustainability Spatial Data Infrastructure Unit T.P. 262 Via E. Fermi, 2749 I-21027 Ispra (VA) ITALY E-mail: [email protected] Tel.: +39-0332786146 Fax: +39-0332786325 http://ies.jrc.ec.europa.eu http://www.jrc.ec.europa.eu Stefano Viganó Address: TXT e-solutions Via Frigia, 27 I-20126 Milano (MI) ITALY E-Mail: [email protected] Tel. +39-02257711 Fax.+39-022578994 http://www.txtgroup.com/it/index.shtml Legal Notice Neither the European Commission nor any person acting on behalf of the Commission is responsible for the use which might be made of this publication. Europe Direct is a service to help you find answers to your questions about the European Union Freephone number (*): 00 800 6 7 8 9 10 11 (*) Certain mobile telephone operators do not allow access to 00 800 numbers or these calls may be billed. A great deal of additional information on the European Union is available on the Internet. It can be accessed through the Europa server http://europa.eu/ 2 JRC 41822 EUR 23045 EN ISBN 978-92-79-07817-0 ISSN 1018-5593 DOI 10.2788/55339 Luxembourg: Office for Official Publications of the European Communities © European Communities, 2007 Reproduction is authorised provided the source is acknowledged Printed in Italy 3 Table of Contents 1. -

UML-Presentationbouml
Présentation de BOUML © 2013-2019 tv <[email protected]> - v.1.1 Qu’est-ce que BOUML ? BOUML est un logiciel de création de diagrammes UML (norme 2.0). Il est multilingue, supporte la génération de code et la rétro-ingénierie. UML (Unified Modeling Language) est un langage de modélisation graphique à base de pictogrammes. Il est utilisé pour le développement logiciel en orientée objet. [Wikipedia] L’ergonomie et la richesse graphique de BOUML sont parfois limitées, tout au moins en comparaison de modeleurs UML plus conventionnels comme StarUML ou ArgoUML. Par contre, il est jugé extrêmement efficace pour la « rétro-modélisation » (créer un modèle UML à partir de codes sources) et pour le développement roundtrip (faire des aller-retour entre modèle UML et code source). BOUML permet ainsi de générer automatiquement du code à partir des diagrammes de classes UML, ainsi que de reconstruire ces derniers à partir de sources existantes, pour les langages C++, Java, PHP et MYSQL. Pour les langages Python et IDL, il peut générer du code mais ne permet pas la rétro-conception UML. https://www.bouml.fr/ À quoi sert BOUML ? BOUML est utilisé pour spécifier, visualiser, modifier et construire les documents nécessaires au bon développement d’un logiciel orienté objet. Avec BOUML, il est également possible de générer automatiquement une partie du code (génération de squelette de code par exemple en langage Java, C++, PHP, ...) à partir des divers documents réalisés. Il est possible de l’utiliser avec un système de gestion de version tel que SVN. Nativement, il supporte la synchronisation de plusieurs utilisateurs sur le même projet.