Contents 1. Preface 2. Introduction
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Meshing for the Finite Element Method
Meshing for the Finite Element Method Summer Seminar ISC5939 .......... John Burkardt Department of Scientific Computing Florida State University http://people.sc.fsu.edu/∼jburkardt/presentations/. mesh 2012 fsu.pdf 10/12 July 2012 1 / 119 FEM Meshing Meshing Computer Representations The Delaunay Triangulation TRIANGLE DISTMESH MESH2D Files and Graphics 1 2 2 D Problems 3D Problems Conclusion 2 / 119 MESHING: The finite element method begins by looking at a complicated region, and thinking of it as a mesh of smaller, simpler subregions. The subregions are simple, (perhaps triangles) so we understand their geometry; they are small because when we approximate the differential equations, our errors will be related to the size of the subregions. More, smaller subregions usually mean less total error. After we compute our solution, it is described in terms of the mesh. The simplest description uses piecewise linear functions, which we might expect to be a crude approximation. However, excellent results can be obtained as long as the mesh is small enough in places where the solution changes rapidly. 3 / 119 MESHING: Thus, even though the hard part of the finite element method involves considering abstract approximation spaces, sequences of approximating functions, the issue of boundary conditions, weak forms and so on, ...it all starts with a very simple idea: Given a geometric shape, break it into smaller, simpler shapes; fit the boundary, and be small in some places. Since this is such a simple idea, you might think there's no reason to worry about it much! 4 / 119 MESHING: Indeed, if we start by thinking of a 1D problem, such as modeling the temperature along a thin strand of wire that extends from A to B, our meshing problem is trivial: Choose N, the number of subregions or elements; Insert N-1 equally spaced nodes between A and B; Create N elements, the intervals between successive nodes. -

New Development in Freefem++
J. Numer. Math., Vol. 20, No. 3-4, pp. 251–265 (2012) DOI 10.1515/jnum-2012-0013 c de Gruyter 2012 New development in freefem++ F. HECHT∗ Received July 2, 2012 Abstract — This is a short presentation of the freefem++ software. In Section 1, we recall most of the characteristics of the software, In Section 2, we recall how to to build the weak form of a partial differential equation (PDE) from the strong form. In the 3 last sections, we present different examples and tools to illustrated the power of the software. First we deal with mesh adaptation for problems in two and three dimension, second, we solve numerically a problem with phase change and natural convection, and the finally to show the possibilities for HPC we solve a Laplace equation by a Schwarz domain decomposition problem on parallel computer. Keywords: finite element, mesh adaptation, Schwarz domain decomposition, parallel comput- ing, freefem++ 1. Introduction This paper intends to give a small presentation of the software freefem++. A partial differential equation is a relation between a function of several variables and its (partial) derivatives. Many problems in physics, engineering, mathematics and even banking are modeled by one or several partial differen- tial equations. Freefem++ is a software to solve these equations numerically in dimen- sions two or three. As its name implies, it is a free software based on the Finite Element Method; it is not a package, it is an integrated product with its own high level programming language; it runs on most UNIX, WINDOWS and MacOs computers. -

An XFEM Based Fixed-Grid Approach to Fluid-Structure Interaction
TECHNISCHE UNIVERSITAT¨ MUNCHEN¨ Lehrstuhl fur¨ Numerische Mechanik An XFEM based fixed-grid approach to fluid-structure interaction Axel Gerstenberger Vollstandiger¨ Abdruck der von der Fakultat¨ fur¨ Maschinenwesen der Techni- schen Universitat¨ Munchen¨ zur Erlangung des akademischen Grades eines Doktor-Ingenieurs (Dr.-Ing.) genehmigten Dissertation. Vorsitzender: Univ.-Prof. Dr.-Ing. habil. Nikolaus A. Adams Prufer¨ der Dissertation: 1. Univ.-Prof. Dr.-Ing. Wolfgang A. Wall 2. Prof. Peter Hansbo, Ph.D. University of Gothenburg / Sweden Die Dissertation wurde am 14. 4. 2010 bei der Technischen Universitat¨ Munchen¨ eingereicht und durch die Fakultat¨ fur¨ Maschinenwesen am 21. 6. 2010 ange- nommen. Zusammenfassung Die vorliegende Arbeit behandelt ein Finite Elemente (FE) basiertes Festgit- terverfahren zur Simulation von dreidimensionaler Fluid-Struktur-Interak- tion (FSI) unter Berucksichtigung¨ großer Strukturdeformationen. FSI ist ein oberflachengekoppeltes¨ Mehrfeldproblem, bei welchem Stuktur- und Fluid- gebiete eine gemeinsame Oberflache¨ teilen. In dem vorgeschlagenen Festgit- terverfahren wird die Stromung¨ durch eine Eulersche Betrachtungsweise be- schrieben, wahrend¨ die Struktur wie ublich¨ in Lagrangscher Betrachtungs- weise formuliert wird. Die Fluid-Struktur-Grenzflache¨ kann sich dabei un- abhangig¨ von dem ortsfesten Fluidnetz bewegen, so dass keine Fluidnetzver- formungen auftreten und beliebige Grenzflachenbewegungen¨ moglich¨ sind. Durch die unveranderte¨ Lagrangsche Strukturformulierung liegt der Schwer- punkt der Arbeit -

Scientific Computing WS 2019/2020 Lecture 1 Jürgen Fuhrmann
Scientific Computing WS 2019/2020 Lecture 1 Jürgen Fuhrmann [email protected] Lecture 1 Slide 1 Me I Name: Dr. Jürgen Fuhrmann (no, not Prof.) I Affiliation: Weierstrass Institute for Applied Analysis and Stochastics, Berlin (WIAS); Deputy Head, Numerical Mathematics and Scientific Computing I Contact: [email protected] I Course homepage: http://www.wias-berlin.de/people/fuhrmann/teach.html I Experience/Field of work: I Numerical solution of partial differential equations (PDEs) I Development, investigation, implementation of finite volume discretizations for nonlinear systems of PDEs I Ph.D. on multigrid methods I Applications: electrochemistry, semiconductor physics, groundwater… I Software development: I WIAS code pdelib (http://pdelib.org) I Languages: C, C++, Python, Lua, Fortran, Julia I Visualization: OpenGL, VTK Lecture 1 Slide 2 Admin stuff I Lectures: Tue 10-12 FH 311, Thu 10-12 MA269 I Consultation: Thu 12-13 MA269, more at WIAS on appointment I There will be coding assignments in Julia I Unix pool I Installation possible for Linux, MacOSX, Windows I Access to examination I Attend ≈ 80% of lectures I Return assignments I Slides and code will be online, a script is being developed from the slides. I See course homepage for literature, specific hints during course Lecture 1 Slide 3 Thursday lectures in MA269 (UNIX Pool) https://www.math.tu-berlin.de/iuk/lehrrechnerbereich/v_menue/ lehrrechnerbereich/ I Working groups of two students per account/computer I Please sign up to the account list provided -
Freefem++ Is a Open Source Program of the Finite Element Method to Solve
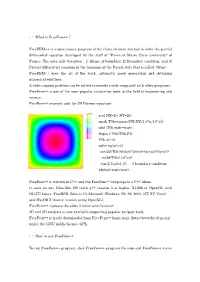
□ What is FreeFem++ ? FreeFEM++ is a open source program of the finite element method to solve the partial differential equation developed by the staff of "Pierre et Marie Curie university" of France. The user only describes , 1) Shape of boundary, 2) Boundary condition, and 3) Partial differential equation in the language of the Pascal style that is called "Gfem". FreeFEM++ does the all of the work, automatic mesh generation and obtaining numerical solutions. A wide-ranging problem can be solved extremely easily compared with other programs. FreeFem++ is one of the most popular simulation tools in the field of engineering and science. FreeFem++ example code for 2D Poisson equation: real NX=20, NY=20 ; mesh T0h=square(NX,NY,[1.0*x,1.0*y]); plot (T0h,wait=true); fespace V0h(T0h,P1); V0h u0,v0; solve eq(u0,v0) =int2d(T0h)(dx(u0)*dx(v0)+dy(u0)*dy(v0)) -int2d(T0h)(1.0*v0) +on(2,3,u0=1.0); // boundary condition plot(u0,wait=true); FreeFem++ is written in C++ and the FreeFem++ language is a C++ idiom. It runs on any Unix-like OS (with g++ version 3 or higher, X11R6 or OpenGL with GLUT) Linux, FreeBSD, Solaris 10, Microsoft Windows (95, 98, 2000, NT, XP, Vista) and MacOS X (native version using OpenGL). FreeFem++ replaces the older freefem and freefem+. 2D and 3D analysis is now available supporting popular pre/post tools. FreeFem++ is freely downloaded from FreeFem++ home page (http://www/freefem.org) under the GNU public license, GPL. □ How to run FreeFem++ To run FreeFem++ program, click FreeFem++ program file icon and FreeFem++ starts automatically. -

Evaluation of Gmsh Meshing Algorithms in Preparation of High-Resolution Wind Speed Simulations in Urban Areas
The International Archives of the Photogrammetry, Remote Sensing and Spatial Information Sciences, Volume XLII-2, 2018 ISPRS TC II Mid-term Symposium “Towards Photogrammetry 2020”, 4–7 June 2018, Riva del Garda, Italy EVALUATION OF GMSH MESHING ALGORITHMS IN PREPARATION OF HIGH-RESOLUTION WIND SPEED SIMULATIONS IN URBAN AREAS M. Langheinrich*1 1 German Aerospace Center, Weßling, Germany Remote Sensing Technology Institute Department of Photogrammetry and Image Analysis [email protected] Commission II, WG II/4 KEY WORDS: CFD, meshing, 3D, computational fluid dynamics, spatial data, evaluation, wind speed ABSTRACT: This paper aims to evaluate the applicability of automatically generated meshes produced within the gmsh meshing framework in preparation for high resolution wind speed and atmospheric pressure simulations for detailed urban environments. The process of creating a skeleton geometry for the meshing process based on level of detail (LOD) 2 CityGML data is described. Gmsh itself offers several approaches for the 2D and 3D meshing process respectively. The different algorithms are shortly introduced and preliminary rated in regard to the mesh quality that is to be expected, as they differ inversely in terms of robustness and resulting mesh element quality. A test area was chosen to simulate the turbulent flow of wind around an urban environment to evaluate the different mesh incarnations by means of a relative comparison of the residuals resulting from the finite-element computational fluid dynamics (CFD) calculations. The applied mesh cases are assessed regarding their convergence evolution as well as final residual values, showing that gmsh 2D and 3D algorithm combinations utilizing the Frontal meshing approach are the preferable choice for the kind of underlying geometry as used in the on hand experiments. -

Pipenightdreams Osgcal-Doc Mumudvb Mpg123-Alsa Tbb
pipenightdreams osgcal-doc mumudvb mpg123-alsa tbb-examples libgammu4-dbg gcc-4.1-doc snort-rules-default davical cutmp3 libevolution5.0-cil aspell-am python-gobject-doc openoffice.org-l10n-mn libc6-xen xserver-xorg trophy-data t38modem pioneers-console libnb-platform10-java libgtkglext1-ruby libboost-wave1.39-dev drgenius bfbtester libchromexvmcpro1 isdnutils-xtools ubuntuone-client openoffice.org2-math openoffice.org-l10n-lt lsb-cxx-ia32 kdeartwork-emoticons-kde4 wmpuzzle trafshow python-plplot lx-gdb link-monitor-applet libscm-dev liblog-agent-logger-perl libccrtp-doc libclass-throwable-perl kde-i18n-csb jack-jconv hamradio-menus coinor-libvol-doc msx-emulator bitbake nabi language-pack-gnome-zh libpaperg popularity-contest xracer-tools xfont-nexus opendrim-lmp-baseserver libvorbisfile-ruby liblinebreak-doc libgfcui-2.0-0c2a-dbg libblacs-mpi-dev dict-freedict-spa-eng blender-ogrexml aspell-da x11-apps openoffice.org-l10n-lv openoffice.org-l10n-nl pnmtopng libodbcinstq1 libhsqldb-java-doc libmono-addins-gui0.2-cil sg3-utils linux-backports-modules-alsa-2.6.31-19-generic yorick-yeti-gsl python-pymssql plasma-widget-cpuload mcpp gpsim-lcd cl-csv libhtml-clean-perl asterisk-dbg apt-dater-dbg libgnome-mag1-dev language-pack-gnome-yo python-crypto svn-autoreleasedeb sugar-terminal-activity mii-diag maria-doc libplexus-component-api-java-doc libhugs-hgl-bundled libchipcard-libgwenhywfar47-plugins libghc6-random-dev freefem3d ezmlm cakephp-scripts aspell-ar ara-byte not+sparc openoffice.org-l10n-nn linux-backports-modules-karmic-generic-pae -

Fast Tetrahedral Mesh Generation and Segmentation of an Atlas-Based Heart Model Using a Periodic Uniform Grid
pp. 1–11 (2018) Fast tetrahedral mesh generation and segmentation of an atlas-based heart model using a periodic uniform grid E. Vasilev∗, D. Lachinov∗, A. Grishin∗, and V. Turlapov∗ Abstract — A fast procedure for generation of regular tetrahedral finite element mesh for objects with complex shape cavities is proposed. The procedure like LBIE-Mesher can generate tetrahedral meshes for the volume interior to a polygonal surface, or for an interval volume between two surfaces having a complex shape and defined in STL-format. This procedure consists of several stages: generation of a regular tetrahedral mesh that fills the volume of the required object; generation of clipping for the uniform grid parts by a boundary surface; shifting vertices of the boundary layer to align onto the surface. We present a sequential and parallel implementation of the algorithm and compare their performance with existing generators of tetrahedral grids such as TetGen, NETGEN, and CGAL. The current version of the algorithm using the mobile GPU is about 5 times faster than NETGEN. The source code of the developed software is available on GitHub. Keywords: FE-mesh generation, tetrahedral mesh, regular mesh, segmentation, human heart model- ling, fast generation MSC 2010: 65M50 This research addresses the problem of fast generation of regular three-dimensional tetrahedral mesh with complex shape cavities. Current existing open-source soft- ware packages do not have such capabilities. For digital medicine, an important example of objects with cavities having a complex shape is the human heart. For a qualitative simulation of the electrical activity of the human heart and obtaining reliable results, a reasonably detailed model of the heart should be used, which will accurately approximate the real heart. -

A Methodology for Applying Three Dimensional Constrained Delaunay Tetrahedralization Algorithms on MRI Medical Images
A Methodology for Applying Three Dimensional Constrained Delaunay Tetrahedralization Algorithms on MRI Medical Images By Feras Wasef Abutalib, B.Eng. (Computer) Computational Analysis and Design Laboratory Department of Electrical Engineering McGill University, Montreal, Quebec, Canada December, 2007 A thesis submitted to the Faculty of Graduate Studies and Research in partial fulfillment of the requirements of the degree of Master of Engineering © Feras Abu Talib, 2007 Library and Bibliothèque et 1+1 Archives Canada Archives Canada Published Heritage Direction du Bran ch Patrimoine de l'édition 395 Wellington Street 395, rue Wellington Ottawa ON K1A ON4 Ottawa ON K1A ON4 Canada Canada Your file Votre référence ISBN: 978-0-494-51441-2 Our file Notre référence ISBN: 978-0-494-51441-2 NOTICE: AVIS: The author has granted a non L'auteur a accordé une licence non exclusive exclusive license allowing Library permettant à la Bibliothèque et Archives and Archives Canada to reproduce, Canada de reproduire, publier, archiver, publish, archive, preserve, conserve, sauvegarder, conserver, transmettre au public communicate to the public by par télécommunication ou par l'Internet, prêter, telecommunication or on the Internet, distribuer et vendre des thèses partout dans loan, distribute and sell theses le monde, à des fins commerciales ou autres, worldwide, for commercial or non sur support microforme, papier, électronique commercial purposes, in microform, et/ou autres formats. paper, electronic and/or any other formats. The author retains copyright L'auteur conserve la propriété du droit d'auteur ownership and moral rights in et des droits moraux qui protège cette thèse. this thesis. Neither the thesis Ni la thèse ni des extraits substantiels de nor substantial extracts from it celle-ci ne doivent être imprimés ou autrement may be printed or otherwise reproduits sans son autorisation. -

A Three-Dimensional Finite Element Mesh Generator with Built-In Pre- and Post-Processing Facilities
INTERNATIONAL JOURNAL FOR NUMERICAL METHODS IN ENGINEERING Int. J. Numer. Meth. Engng 2009; 0:1{24 Prepared using nmeauth.cls [Version: 2002/09/18 v2.02] This is a preprint of an article accepted for publication in the International Journal for Numerical Methods in Engineering, Copyright c 2009 John Wiley & Sons, Ltd. Gmsh: a three-dimensional finite element mesh generator with built-in pre- and post-processing facilities Christophe Geuzaine1, Jean-Fran¸cois Remacle2∗ 1 Universit´ede Li`ege,Department of Electrical Engineering And Computer Science, Montefiore Institute, Li`ege, Belgium. 2 Universite´ catholique de Louvain, Institute for Mechanical, Materials and Civil Engineering, Louvain-la-Neuve, Belgium SUMMARY Gmsh is an open-source three-dimensional finite element grid generator with a build-in CAD engine and post-processor. Its design goal is to provide a fast, light and user-friendly meshing tool with parametric input and advanced visualization capabilities. This paper presents the overall philosophy, the main design choices and some of the original algorithms implemented in Gmsh. Copyright c 2009 John Wiley & Sons, Ltd. key words: Computer Aided Design, Mesh generation, Post-Processing, Finite Element Method, Open Source Software 1. Introduction When we started the Gmsh project in the summer of 1996, our goal was to develop a fast, light and user-friendly interactive software tool to easily create geometries and meshes that could be used in our three-dimensional finite element solvers [8], and then visualize and export the computational results with maximum flexibility. At the time, no open-source software combining a CAD engine, a mesh generator and a post-processor was available: the existing integrated tools were expensive commercial packages [41], and the freeware or shareware tools were limited to either CAD [29], two-dimensional mesh generation [44], three-dimensional mesh generation [53, 21, 30], or post-processing [31]. -

Numerical Methods for Coupled Population Balance Systems Applied to the Dynamical Simulation of Crystallization Processes
Chapter 1 Numerical Methods for Coupled Population Balance Systems Applied to the Dynamical Simulation of Crystallization Processes Robin Ahrens, Zahra Lakdawala, Andreas Voigt, Viktoria Wiedmeyer, Volker John, Sabine Le Borne, Kai Sundmacher Abstract Uni- and bi-variate crystallization processes are considered that are modeled with population balance systems (PBSs). Experimental results for uni-variate processes in a helically coiled flow tube crystallizer are presented. A survey on numerical methods for the simulation of uni-variate PBSs is provided with the emphasis on a coupled stochastic-deterministic method. In Robin Ahrens Hamburg University of Technology, Faculty of Electrical Engineering, Informatics and Mathematics, Institute of Mathematics, Am Schwarzenberg-Campus 3, 21073 Hamburg, Germany, e-mail: [email protected] Zahra Lakdawala Weierstrass Institute for Applied Analysis and Stochastics (WIAS), Mohrenstr. 39, 10117 Berlin, Germany, e-mail: [email protected] Andreas Voigt, Otto-von-Guericke-University Magdeburg, Department Process Systems Engineering, Uni- versit¨atsplatz2, 39106 Magdeburg, Germany, e-mail: [email protected] Viktoria Wiedmeyer ETH Zurich, Institute of Process Engineering, Sonneggstrasse 3, 8092 Zurich, Switzerland, e-mail: [email protected] Volker John Weierstrass Institute for Applied Analysis and Stochastics (WIAS), Mohrenstr. 39, 10117 Berlin, Germany, and Freie Universit¨atBerlin, Department of Mathematics and Computer Science, Arnimallee 6, 14195 Berlin, Germany, e-mail: [email protected] Sabine Le Borne Hamburg University of Technology, Faculty of Electrical Engineering, Informatics and Mathematics, Institute of Mathematics, Am Schwarzenberg-Campus 3, 21073 Hamburg, Germany, e-mail: [email protected] Kai Sundmacher Otto-von-Guericke-University Magdeburg, Department Process Systems Engineering, Uni- versit¨atsplatz2, 39106 Magdeburg, Germany, and Max Planck Institute for Dynamics of Complex Technical Systems, Process Systems Engineering, Sandtorstr. -

EIT-MESHER – Segmented FEM Mesh Generation and Refinement
Preprints (www.preprints.org) | NOT PEER-REVIEWED | Posted: 22 May 2020 doi:10.20944/preprints202005.0351.v1 EIT-MESHER – Segmented FEM Mesh generation and refinement Paper Authors 1. Dowrick, Thomas1; 2. Avery, James2; 3. Faulkner, Mayo3; 4. Holder, David3; 5. Aristovich, Kirill3 Paper Author Roles and Affiliations 1. Wellcome/EPSRC Centre for Surgical and Interventional Sciences, University College London, UK 2. Department of Surgery and Cancer, Imperial College London, London, UK 3. Medical Physics and Biomedical Engineering, University College London, UK Abstract EIT-MESHER (https://github.com/EIT-team/Mesher) is C++ software, based on the CGAL library, which generates high quality Finite Element Model tetrahedral meshes from binary masks of 3D volume segmentations. Originally developed for biomedical applications in Electrical Impedance Tomography (EIT) to address the need for custom, non-linear refinement in certain areas (e.g. around electrodes), EIT-MESHER can also be used in other fields where custom FEM refinement is required, such as Diffuse Optical Tomography (DOT). Keywords Finite Element Models, C++, Electrical Impedance Tomography, Diffuse Optical Tomography, Mesh Generation Introduction The EIT-MESHER (https://github.com/EIT-team/Mesher) is a C++ based open source software which generates stable, good quality meshes (Figure 1) for solving the EIT forward solution. The software is based on the CGAL geometry processing kernel (https://www.cgal.org/) and utilises the extended Delaunay triangulation over binary domains in combination with a number of flexible post-triangulation optimisers [1]. In addition, the software performs user- defined mesh refinement, specific to the requirements of Electrical Impedance Tomography. The input to the software is a binary 3D mask (or segmentation) of the desired object, and the output is the fully optimised mesh ready for calculation of the forward problem.