Anl-7826 Chinese Remainder Ind Interpolation
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Fast and Efficient Algorithms for Evaluating Uniform and Nonuniform
World Academy of Science, Engineering and Technology International Journal of Computer and Information Engineering Vol:13, No:8, 2019 Fast and Efficient Algorithms for Evaluating Uniform and Nonuniform Lagrange and Newton Curves Taweechai Nuntawisuttiwong, Natasha Dejdumrong Abstract—Newton-Lagrange Interpolations are widely used in quadratic computation time, which is slower than the others. numerical analysis. However, it requires a quadratic computational However, there are some curves in CAGD, Wang-Ball, DP time for their constructions. In computer aided geometric design and Dejdumrong curves with linear complexity. In order to (CAGD), there are some polynomial curves: Wang-Ball, DP and Dejdumrong curves, which have linear time complexity algorithms. reduce their computational time, Bezier´ curve is converted Thus, the computational time for Newton-Lagrange Interpolations into any of Wang-Ball, DP and Dejdumrong curves. Hence, can be reduced by applying the algorithms of Wang-Ball, DP and the computational time for Newton-Lagrange interpolations Dejdumrong curves. In order to use Wang-Ball, DP and Dejdumrong can be reduced by converting them into Wang-Ball, DP and algorithms, first, it is necessary to convert Newton-Lagrange Dejdumrong algorithms. Thus, it is necessary to investigate polynomials into Wang-Ball, DP or Dejdumrong polynomials. In this work, the algorithms for converting from both uniform and the conversion from Newton-Lagrange interpolation into non-uniform Newton-Lagrange polynomials into Wang-Ball, DP and the curves with linear complexity, Wang-Ball, DP and Dejdumrong polynomials are investigated. Thus, the computational Dejdumrong curves. An application of this work is to modify time for representing Newton-Lagrange polynomials can be reduced sketched image in CAD application with the computational into linear complexity. -

On Multivariate Interpolation
On Multivariate Interpolation Peter J. Olver† School of Mathematics University of Minnesota Minneapolis, MN 55455 U.S.A. [email protected] http://www.math.umn.edu/∼olver Abstract. A new approach to interpolation theory for functions of several variables is proposed. We develop a multivariate divided difference calculus based on the theory of non-commutative quasi-determinants. In addition, intriguing explicit formulae that connect the classical finite difference interpolation coefficients for univariate curves with multivariate interpolation coefficients for higher dimensional submanifolds are established. † Supported in part by NSF Grant DMS 11–08894. April 6, 2016 1 1. Introduction. Interpolation theory for functions of a single variable has a long and distinguished his- tory, dating back to Newton’s fundamental interpolation formula and the classical calculus of finite differences, [7, 47, 58, 64]. Standard numerical approximations to derivatives and many numerical integration methods for differential equations are based on the finite dif- ference calculus. However, historically, no comparable calculus was developed for functions of more than one variable. If one looks up multivariate interpolation in the classical books, one is essentially restricted to rectangular, or, slightly more generally, separable grids, over which the formulae are a simple adaptation of the univariate divided difference calculus. See [19] for historical details. Starting with G. Birkhoff, [2] (who was, coincidentally, my thesis advisor), recent years have seen a renewed level of interest in multivariate interpolation among both pure and applied researchers; see [18] for a fairly recent survey containing an extensive bibli- ography. De Boor and Ron, [8, 12, 13], and Sauer and Xu, [61, 10, 65], have systemati- cally studied the polynomial case. -

Mials P
Euclid's Algorithm 171 Euclid's Algorithm Horner’s method is a special case of Euclid's Algorithm which constructs, for given polyno- mials p and h =6 0, (unique) polynomials q and r with deg r<deg h so that p = hq + r: For variety, here is a nonstandard discussion of this algorithm, in terms of elimination. Assume that d h(t)=a0 + a1t + ···+ adt ;ad =06 ; and n p(t)=b0 + b1t + ···+ bnt : Then we seek a polynomial n−d q(t)=c0 + c1t + ···+ cn−dt for which r := p − hq has degree <d. This amounts to the square upper triangular linear system adc0 + ad−1c1 + ···+ a0cd = bd adc1 + ad−1c2 + ···+ a0cd+1 = bd+1 . adcn−d−1 + ad−1cn−d = bn−1 adcn−d = bn for the unknown coefficients c0;:::;cn−d which can be uniquely solved by back substitution since its diagonal entries all equal ad =0.6 19aug02 c 2002 Carl de Boor 172 18. Index Rough index for these notes 1-1:-5,2,8,40 cartesian product: 2 1-norm: 79 Cauchy(-Bunyakovski-Schwarz) 2-norm: 79 Inequality: 69 A-invariance: 125 Cauchy-Binet formula: -9, 166 A-invariant: 113 Cayley-Hamilton Theorem: 133 absolute value: 167 CBS Inequality: 69 absolutely homogeneous: 70, 79 Chaikin algorithm: 139 additive: 20 chain rule: 153 adjugate: 164 change of basis: -6 affine: 151 characteristic function: 7 affine combination: 148, 150 characteristic polynomial: -8, 130, 132, 134 affine hull: 150 circulant: 140 affine map: 149 codimension: 50, 53 affine polynomial: 152 coefficient vector: 21 affine space: 149 cofactor: 163 affinely independent: 151 column map: -6, 23 agrees with y at Λt:59 column space: 29 algebraic dual: 95 column -

CS321-001 Introduction to Numerical Methods
CS321-001 Introduction to Numerical Methods Lecture 3 Interpolation and Numerical Differentiation Professor Jun Zhang Department of Computer Science University of Kentucky Lexington, KY 40506-0633 Polynomial Interpolation Given a set of discrete values, how can we estimate other values between these data The method that we will use is called polynomial interpolation. We assume the data we had are from the evaluation of a smooth function. We may be able to use a polynomial p(x) to approximate this function, at least locally. A condition: the polynomial p(x) takes the given values at the given points (nodes), i.e., p(xi) = yi with 0 ≤ i ≤ n. The polynomial is said to interpolate the table, since we do not know the function. 2 Polynomial Interpolation Note that all the points are passed through by the curve 3 Polynomial Interpolation We do not know the original function, the interpolation may not be accurate 4 Order of Interpolating Polynomial A polynomial of degree 0, a constant function, interpolates one set of data If we have two sets of data, we can have an interpolating polynomial of degree 1, a linear function x x1 x x0 p(x) y0 y1 x0 x1 x1 x0 y1 y0 y0 (x x0 ) x1 x0 Review carefully if the interpolation condition is satisfied Interpolating polynomials can be written in several forms, the most well known ones are the Lagrange form and Newton form. Each has some advantages 5 Lagrange Form For a set of fixed nodes x0, x1, …, xn, the cardinal functions, l0, l1,…, ln, are defined as 0 if i j li (x j ) ij -

Lagrange & Newton Interpolation
Lagrange & Newton interpolation In this section, we shall study the polynomial interpolation in the form of Lagrange and Newton. Given a se- quence of (n +1) data points and a function f, the aim is to determine an n-th degree polynomial which interpol- ates f at these points. We shall resort to the notion of divided differences. Interpolation Given (n+1) points {(x0, y0), (x1, y1), …, (xn, yn)}, the points defined by (xi)0≤i≤n are called points of interpolation. The points defined by (yi)0≤i≤n are the values of interpolation. To interpolate a function f, the values of interpolation are defined as follows: yi = f(xi), i = 0, …, n. Lagrange interpolation polynomial The purpose here is to determine the unique polynomial of degree n, Pn which verifies Pn(xi) = f(xi), i = 0, …, n. The polynomial which meets this equality is Lagrange interpolation polynomial n Pnx=∑ l j x f x j j=0 where the lj ’s are polynomials of degree n forming a basis of Pn n x−xi x−x0 x−x j−1 x−x j 1 x−xn l j x= ∏ = ⋯ ⋯ i=0,i≠ j x j −xi x j−x0 x j−x j−1 x j−x j1 x j−xn Properties of Lagrange interpolation polynomial and Lagrange basis They are the lj polynomials which verify the following property: l x = = 1 i= j , ∀ i=0,...,n. j i ji {0 i≠ j They form a basis of the vector space Pn of polynomials of degree at most equal to n n ∑ j l j x=0 j=0 By setting: x = xi, we obtain: n n ∑ j l j xi =∑ j ji=0 ⇒ i =0 j=0 j=0 The set (lj)0≤j≤n is linearly independent and consists of n + 1 vectors. -

Mathematical Topics
A Mathematical Topics This chapter discusses most of the mathematical background needed for a thor ough understanding of the material presented in the book. It has been mentioned in the Preface, however, that math concepts which are only used once (such as the mediation operator and points vs. vectors) are discussed right where they are introduced. Do not worry too much about your difficulties in mathematics, I can assure you that mine a.re still greater. - Albert Einstein. A.I Fourier Transforms Our curves are functions of an arbitrary parameter t. For functions used in science and engineering, time is often the parameter (or the independent variable). We, therefore, say that a function g( t) is represented in the time domain. Since a typical function oscillates, we can think of it as being similar to a wave and we may try to represent it as a wave (or as a combination of waves). When this is done, we have the function G(f), where f stands for the frequency of the wave, and we say that the function is represented in the frequency domain. This turns out to be a useful concept, since many operations on functions are easy to carry out in the frequency domain. Transforming a function between the time and frequency domains is easy when the function is periodic, but it can also be done for certain non periodic functions. The present discussion is restricted to periodic functions. 1IIIt Definition: A function g( t) is periodic if (and only if) there exists a constant P such that g(t+P) = g(t) for all values of t (Figure A.la). -

Polynomial Interpolation
Numerical Methods 401-0654 6 Polynomial Interpolation Throughout this chapter n N is an element from the set N if not otherwise specified. ∈ 0 0 6.1 Polynomials D-ITET, ✬ ✩D-MATL Definition 6.1.1. We denote by n n 1 n := R t αnt + αn 1t − + ... + α1t + α0 R: α0, α1,...,αn R . P ∋ 7→ − ∈ ∈ the R-vectorn space of polynomials with degree n. o ≤ ✫ ✪ ✬ ✩ Theorem 6.1.2 (Dimension of space of polynomials). It holds that dim n = n +1 and n P P ⊂ 6.1 C∞(R). p. 192 ✫ ✪ n n 1 ➙ Remark 6.1.1 (Polynomials in Matlab). MATLAB: αnt + αn 1t − + ... + α0 Vector Numerical − Methods (αn, αn 1,...,α0) (ordered!). 401-0654 − △ Remark 6.1.2 (Horner scheme). Evaluation of a polynomial in monomial representation: Horner scheme p(t)= t t t t αnt + αn 1 + αn 2 + + α1 + α0 . ··· − − ··· Code 6.1: Horner scheme, polynomial in MATLAB format 1 function y = polyval (p,x) 2 y = p(1); for i =2: length (p), y = x y+p( i ); end ∗ D-ITET, D-MATL Asymptotic complexity: O(n) Use: MATLAB “built-in”-function polyval(p,x); △ 6.2 p. 193 6.2 Polynomial Interpolation: Theory Numerical Methods 401-0654 Goal: (re-)constructionofapolynomial(function)frompairs of values (fit). ✬ Lagrange polynomial interpolation problem ✩ Given the nodes < t < t < < tn < and the values y ,...,yn R compute −∞ 0 1 ··· ∞ 0 ∈ p n such that ∈P j 0, 1,...,n : p(t )= y . ∀ ∈ { } j j ✫ ✪ D-ITET, D-MATL 6.2 p. 194 6.2.1 Lagrange polynomials Numerical Methods 401-0654 ✬ ✩ Definition 6.2.1. -

A Low‐Cost Solution to Motion Tracking Using an Array of Sonar Sensors and An
A Low‐cost Solution to Motion Tracking Using an Array of Sonar Sensors and an Inertial Measurement Unit A thesis presented to the faculty of the Russ College of Engineering and Technology of Ohio University In partial fulfillment of the requirements for the degree Master of Science Jason S. Maxwell August 2009 © 2009 Jason S. Maxwell. All Rights Reserved. 2 This thesis titled A Low‐cost Solution to Motion Tracking Using an Array of Sonar Sensors and an Inertial Measurement Unit by JASON S. MAXWELL has been approved for the School of Electrical Engineering Computer Science and the Russ College of Engineering and Technology by Maarten Uijt de Haag Associate Professor School of Electrical Engineering and Computer Science Dennis Irwin Dean, Russ College of Engineering and Technology 3 ABSTRACT MAXWELL, JASON S., M.S., August 2009, Electrical Engineering A Low‐cost Solution to Motion Tracking Using an Array of Sonar Sensors and an Inertial Measurement Unit (91 pp.) Director of Thesis: Maarten Uijt de Haag As the desire and need for unmanned aerial vehicles (UAV) increases, so to do the navigation and system demands for the vehicles. While there are a multitude of systems currently offering solutions, each also possess inherent problems. The Global Positioning System (GPS), for instance, is potentially unable to meet the demands of vehicles that operate indoors, in heavy foliage, or in urban canyons, due to the lack of signal strength. Laser‐based systems have proven to be rather costly, and can potentially fail in areas in which the surface absorbs light, and in urban environments with glass or mirrored surfaces. -

The AMATYC Review, Fall 1992-Spring 1993. INSTITUTION American Mathematical Association of Two-Year Colleges
DOCUMENT RESUME ED 354 956 JC 930 126 AUTHOR Cohen, Don, Ed.; Browne, Joseph, Ed. TITLE The AMATYC Review, Fall 1992-Spring 1993. INSTITUTION American Mathematical Association of Two-Year Colleges. REPORT NO ISSN-0740-8404 PUB DATE 93 NOTE 203p. AVAILABLE FROMAMATYC Treasurer, State Technical Institute at Memphis, 5983 Macon Cove, Memphis, TN 38134 (for libraries 2 issues free with $25 annual membership). PUB TYPE Collected Works Serials (022) JOURNAL CIT AMATYC Review; v14 n1-2 Fall 1992-Spr 1993 EDRS PRICE MF01/PC09 Plus Postage. DESCRIPTORS *College Mathematics; Community Colleges; Computer Simulation; Functions (Mathematics); Linear Programing; *Mathematical Applications; *Mathematical Concepts; Mathematical Formulas; *Mathematics Instruction; Mathematics Teachers; Technical Mathematics; Two Year Colleges ABSTRACT Designed as an avenue of communication for mathematics educators concerned with the views, ideas, and experiences of two-year collage students and teachers, this journal contains articles on mathematics expoition and education,as well as regular features presenting book and software reviews and math problems. The first of two issues of volume 14 contains the following major articles: "Technology in the Mathematics Classroom," by Mike Davidson; "Reflections on Arithmetic-Progression Factorials," by William E. Rosentl,e1; "The Investigation of Tangent Polynomials with a Computer Algebra System," by John H. Mathews and Russell W. Howell; "On Finding the General Term of a Sequence Using Lagrange Interpolation," by Sheldon Gordon and Robert Decker; "The Floating Leaf Problem," by Richard L. Francis; "Approximations to the Hypergeometric Distribution," by Chltra Gunawardena and K. L. D. Gunawardena; aid "Generating 'JE(3)' with Some Elementary Applications," by John J. Edgeli, Jr. The second issue contains: "Strategies for Making Mathematics Work for Minorities," by Beverly J. -

Sparse Polynomial Interpolation and Testing
Sparse Polynomial Interpolation and Testing by Andrew Arnold A thesis presented to the University of Waterloo in fulfillment of the thesis requirement for the degree of Doctor of Philsophy in Computer Science Waterloo, Ontario, Canada, 2016 © Andrew Arnold 2016 I hereby declare that I am the sole author of this thesis. This is a true copy of the thesis, including any required final revisions, as accepted by my examiners. I understand that my thesis may be made electronically available to the public. ii Abstract Interpolation is the process of learning an unknown polynomial f from some set of its evalua- tions. We consider the interpolation of a sparse polynomial, i.e., where f is comprised of a small, bounded number of terms. Sparse interpolation dates back to work in the late 18th century by the French mathematician Gaspard de Prony, and was revitalized in the 1980s due to advancements by Ben-Or and Tiwari, Blahut, and Zippel, amongst others. Sparse interpolation has applications to learning theory, signal processing, error-correcting codes, and symbolic computation. Closely related to sparse interpolation are two decision problems. Sparse polynomial identity testing is the problem of testing whether a sparse polynomial f is zero from its evaluations. Sparsity testing is the problem of testing whether f is in fact sparse. We present effective probabilistic algebraic algorithms for the interpolation and testing of sparse polynomials. These algorithms assume black-box evaluation access, whereby the algorithm may specify the evaluation points. We measure algorithmic costs with respect to the number and types of queries to a black-box oracle. -

Sparse Polynomial Interpolation Codes and Their Decoding Beyond Half the Minimum Distance *
Sparse Polynomial Interpolation Codes and their Decoding Beyond Half the Minimum Distance * Erich L. Kaltofen Clément Pernet Dept. of Mathematics, NCSU U. J. Fourier, LIP-AriC, CNRS, Inria, UCBL, Raleigh, NC 27695, USA ÉNS de Lyon [email protected] 46 Allée d’Italie, 69364 Lyon Cedex 7, France www4.ncsu.edu/~kaltofen [email protected] http://membres-liglab.imag.fr/pernet/ ABSTRACT General Terms: Algorithms, Reliability We present algorithms performing sparse univariate pol- Keywords: sparse polynomial interpolation, Blahut's ynomial interpolation with errors in the evaluations of algorithm, Prony's algorithm, exact polynomial fitting the polynomial. Based on the initial work by Comer, with errors. Kaltofen and Pernet [Proc. ISSAC 2012], we define the sparse polynomial interpolation codes and state that their minimal distance is precisely the code-word length 1. INTRODUCTION divided by twice the sparsity. At ISSAC 2012, we have Evaluation-interpolation schemes are a key ingredient given a decoding algorithm for as much as half the min- in many of today's computations. Model fitting for em- imal distance and a list decoding algorithm up to the pirical data sets is a well-known one, where additional minimal distance. information on the model helps improving the fit. In Our new polynomial-time list decoding algorithm uses particular, models of natural phenomena often happen sub-sequences of the received evaluations indexed by to be sparse, which has motivated a wide range of re- an arithmetic progression, allowing the decoding for a search including compressive sensing [4], and sparse in- larger radius, that is, more errors in the evaluations terpolation of polynomials [23,1, 15, 13,9, 11]. -
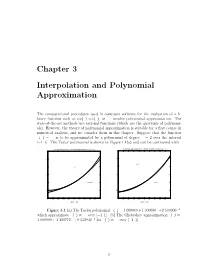
Chapter 3 Interpolation and Polynomial Approximation
Chapter 3 Interpolation and Polynomial Approximation The computational procedures used in computer software for the evaluation of a li- brary function such as sin(x); cos(x), or ex, involve polynomial approximation. The state-of-the-art methods use rational functions (which are the quotients of polynomi- als). However, the theory of polynomial approximation is suitable for a first course in numerical analysis, and we consider them in this chapter. Suppose that the function f(x) = ex is to be approximated by a polynomial of degree n = 2 over the interval [¡1; 1]. The Taylor polynomial is shown in Figure 1.1(a) and can be contrasted with 2 x The Taylor polynomial p(x)=1+x+0.5x2 which approximates f(x)=ex over [−1,1] The Chebyshev approximation q(x)=1+1.129772x+0.532042x for f(x)=e over [−1,1] 3 3 2.5 2.5 y=ex 2 2 y=ex 1.5 1.5 2 1 y=1+x+0.5x 1 y=q(x) 0.5 0.5 0 0 −1 −0.8 −0.6 −0.4 −0.2 0 0.2 0.4 0.6 0.8 1 −1 −0.8 −0.6 −0.4 −0.2 0 0.2 0.4 0.6 0.8 1 Figure 1.1(a) Figure 1.1(b) Figure 3.1 (a) The Taylor polynomial p(x) = 1:000000+ 1:000000x +0:500000x2 which approximate f(x) = ex over [¡1; 1]. (b) The Chebyshev approximation q(x) = 1:000000 + 1:129772x + 0:532042x2 for f(x) = ex over [¡1; 1].