HTC AMERICA Inc., ) a Corporation
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

1 STIPULATED ADDENDUM to the PROTECTIVE ORDER CASE NUMBERS 18-CV-01885-HSG; 18-CV-01886-HSG; 18-CV-01887-HSG [All Counsel Listed
Case 4:18-cv-01887-HSG Document 303 Filed 09/11/18 Page 1 of 9 1 [All counsel listed on signature page] 2 IN THE UNITED STATES DISTRICT COURT FOR THE NORTHERN DISTRICT OF CALIFORNIA 3 OAKLAND DIVISION 4 KONINKLIJKE PHILIPS N.V., 5 U.S. PHILIPS CORPORATION, Case No. 4:18-cv-01885-HSG (and related cases) 6 Plaintiffs, v. STIPULATED ADDENDUM TO 7 THE PROTECTIVE ORDER; ACER INC., ORDER 8 ACER AMERICA CORPORATION, 9 Defendants. 10 MICROSOFT CORPORATION, 11 Intervenor-Plaintiff, 12 v. 13 KONINKLIJKE PHILIPS N.V., U.S. PHILIPS CORPORATION, 14 Intervenor-Defendants. 15 16 KONINKLIJKE PHILIPS N.V., U.S. PHILIPS CORPORATION, 17 Intervenor- 18 Defendants/Counterclaim Plaintiffs in Intervention 19 v. 20 MICROSOFT CORPORATION 21 Intervenor- Plaintiff/Counterclaim 22 Defendant in Intervention 23 AND 24 MICROSOFT MOBILE INC. 25 Counterclaim Defendant in Intervention 26 27 28 1 STIPULATED ADDENDUM TO THE PROTECTIVE ORDER CASE NUMBERS 18-CV-01885-HSG; 18-CV-01886-HSG; 18-CV-01887-HSG Case 4:18-cv-01887-HSG Document 303 Filed 09/11/18 Page 2 of 9 1 KONINKLIJKE PHILIPS N.V., 2 U.S. PHILIPS CORPORATION, Related Case No. 4:18-cv-01886-HSG 3 Plaintiffs, v. 4 ASUSTEK COMPUTER INC., 5 ASUS COMPUTER INTERNATIONAL, 6 Defendants. 7 MICROSOFT CORPORATION, 8 Intervenor-Plaintiff, 9 v. 10 KONINKLIJKE PHILIPS N.V., U.S. PHILIPS CORPORATION, 11 Intervenor-Defendants. 12 13 KONINKLIJKE PHILIPS N.V., U.S. PHILIPS CORPORATION, 14 Intervenor- 15 Defendants/Counterclaim Plaintiffs in Intervention 16 v. 17 MICROSOFT CORPORATION 18 Intervenor- Plaintiff/Counterclaim 19 Defendant in Intervention 20 AND 21 MICROSOFT MOBILE INC. -

Android (Operating System) 1 Android (Operating System)
Android (operating system) 1 Android (operating system) Android Home screen displayed by Samsung Nexus S with Google running Android 2.3 "Gingerbread" Company / developer Google Inc., Open Handset Alliance [1] Programmed in C (core), C++ (some third-party libraries), Java (UI) Working state Current [2] Source model Free and open source software (3.0 is currently in closed development) Initial release 21 October 2008 Latest stable release Tablets: [3] 3.0.1 (Honeycomb) Phones: [3] 2.3.3 (Gingerbread) / 24 February 2011 [4] Supported platforms ARM, MIPS, Power, x86 Kernel type Monolithic, modified Linux kernel Default user interface Graphical [5] License Apache 2.0, Linux kernel patches are under GPL v2 Official website [www.android.com www.android.com] Android is a software stack for mobile devices that includes an operating system, middleware and key applications.[6] [7] Google Inc. purchased the initial developer of the software, Android Inc., in 2005.[8] Android's mobile operating system is based on a modified version of the Linux kernel. Google and other members of the Open Handset Alliance collaborated on Android's development and release.[9] [10] The Android Open Source Project (AOSP) is tasked with the maintenance and further development of Android.[11] The Android operating system is the world's best-selling Smartphone platform.[12] [13] Android has a large community of developers writing applications ("apps") that extend the functionality of the devices. There are currently over 150,000 apps available for Android.[14] [15] Android Market is the online app store run by Google, though apps can also be downloaded from third-party sites. -

Select Smartphones and Tablets with Qualcomm® Quick Charge™ 2.0 Technology
Select smartphones and tablets with Qualcomm® Quick Charge™ 2.0 technology + Asus Transformer T100 + Samsung Galaxy S6 + Asus Zenfone 2 + Samsung Galaxy S6 Edge + Droid Turbo by Motorola + Samsung Note 4 + Fujitsu Arrows NX + Samsung Note Edge + Fujitsu F-02G + Sharp Aquos Pad + Fujitsu F-03G + Sharp Aquos Zeta + Fujitsu F-05F + Sharp SH01G/02G + Google Nexus 6 + Sony Xperia Z2 (Japan) + HTC Butterfly 2 + Sony Xperia Z2 Tablet (Japan) + HTC One (M8) + Sony Xperia Z3 + HTC One (M9) + Sony Xperia Z3 Tablet + Kyocera Urbano L03 + Sony Xperia Z4 + LeTV One Max + Sony Xperia Z4 Tablet + LeTV One Pro + Xiaomi Mi 3 + LG G Flex 2 + Xiaomi Mi 4 + LG G4 + Xiaomi Mi Note + New Moto X by Motorola + Xiaomi Mi Note Pro + Panasonic CM-1 + Yota Phone 2 + Samsung Galaxy S5 (Japan) These devices contain the hardware necessary to achieve Quick Charge 2.0. It is at the device manufacturer’s discretion to fully enable this feature. A Quick Charge 2.0 certified power adapter is required. Different Quick Charge 2.0 implementations may result in different charging times. www.qualcomm.com/quickcharge Qualcomm Quick Charge is a product of Qualcom Technologies, Inc. Updated 6/2015 Certified Accessories + Air-J Multi Voltage AC Charger + Motorola TurboPower 15 Wall Charger + APE Technology AC/DC Adapter + Naztech N210 Travel Charger + APE Technology Car Charger + Naztech Phantom Vehicle Charger + APE Technology Power Bank + NTT DOCOMO AC Adapter + Aukey PA-U28 Turbo USB Universal Wall Charger + Power Partners AC Adapter + CellTrend Car Charger + Powermod Car Charger -

PAEW-0059 Korea Semiconductor Industry Association
Comments of the Korea Semiconductor Industry Association On Patent Assertion Entity (PAE) Activities April 5, 2013 The Korea Semiconductor Industry Association (KSIA) welcomes the opportunity to submit these comments to the U.S. Department of Justice, Antitrust Division, and the U.S. Federal Trade Commission, regarding the activities of Patent Assertion Entities (PAEs). The KSIA hopes that these comments are helpful to the agencies’ analysis of this important issue and respectfully requests that these comments be taken into account as policies are developed to address these serious concerns. The KSIA is an industry association, based in Seoul, Korea, which represents more than 300 companies in the semiconductor manufacturing sector, involved in all aspects of semiconductor device manufacturing as well as semiconductor equipment, materials, and design. Many of its member companies are world leaders in developing advanced semiconductor technologies. The KSIA's primary objectives include promotion of its members’ products and the further advancement of technological development in Korea's semiconductor industry. The KSIA is dedicated to providing opportunities for promoting cooperation among its members and members of international organizations in the areas of device, equipment and material suppliers. The world’s semiconductor industry, of which KSIA members are an important part, plays a vital role in the technological advancement and increased efficiency of nearly every facet of society. In addition to the well-known advances in computers, -

SECOND AMENDED COMPLAINT 3:14-Cv-582-JD
Case 3:14-cv-00582-JD Document 51 Filed 11/10/14 Page 1 of 19 1 EDUARDO G. ROY (Bar No. 146316) DANIEL C. QUINTERO (Bar No. 196492) 2 JOHN R. HURLEY (Bar No. 203641) PROMETHEUS PARTNERS L.L.P. 3 220 Montgomery Street Suite 1094 San Francisco, CA 94104 4 Telephone: 415.527.0255 5 Attorneys for Plaintiff 6 DANIEL NORCIA 7 UNITED STATES DISTIRCT COURT 8 NORTHERN DISTRICT OF CALIFORNIA 9 DANIEL NORCIA, on his own behalf and on Case No.: 3:14-cv-582-JD 10 behalf of all others similarly situated, SECOND AMENDED CLASS ACTION 11 Plaintiffs, COMPLAINT FOR: 12 v. 1. VIOLATION OF CALIFORNIA CONSUMERS LEGAL REMEDIES 13 SAMSUNG TELECOMMUNICATIONS ACT, CIVIL CODE §1750, et seq. AMERICA, LLC, a New York Corporation, and 2. UNLAWFUL AND UNFAIR 14 SAMSUNG ELECTRONICS AMERICA, INC., BUSINESS PRACTICES, a New Jersey Corporation, CALIFORNIA BUS. & PROF. CODE 15 §17200, et seq. Defendants. 3. FALSE ADVERTISING, 16 CALIFORNIA BUS. & PROF. CODE §17500, et seq. 17 4. FRAUD 18 JURY TRIAL DEMANDED 19 20 21 22 23 24 25 26 27 28 1 SECOND AMENDED COMPLAINT 3:14-cv-582-JD Case 3:14-cv-00582-JD Document 51 Filed 11/10/14 Page 2 of 19 1 Plaintiff DANIEL NORCIA, having not previously amended as a matter of course pursuant to 2 Fed.R.Civ.P. 15(a)(1)(B), hereby exercises that right by amending within 21 days of service of 3 Defendants’ Motion to Dismiss filed October 20, 2014 (ECF 45). 4 Individually and on behalf of all others similarly situated, Daniel Norcia complains and alleges, 5 by and through his attorneys, upon personal knowledge and information and belief, as follows: 6 NATURE OF THE ACTION 7 1. -

In the United States District Court for the Northern District of Texas Wichita Falls Division
Case 7:14-cv-00014-O Document 284 Filed 05/28/15 Page 1 of 15 PageID 16355 IN THE UNITED STATES DISTRICT COURT FOR THE NORTHERN DISTRICT OF TEXAS WICHITA FALLS DIVISION § SUMMIT 6 LLC, § § Plaintiff, § § v. § § HTC CORPORATION et. al, § Civil Action No. 7:14-cv-00014-O § Defendants. § § § SUMMIT 6 LLC, § § Plaintiff, § § Civil Action No. 7:14-cv-00106-O v. § § APPLE INC. § § Defendant. § § ORDER Before the Court are Defendants Apple Inc. (“Apple”), Twitter, Inc. (“Twitter”)1, Motorola Mobility, LLC (“Motorola”), and HTC Corporation and HTC America, Inc.’s (“HTC”) (collectively, “Defendants”) Rule 12(c) Motion for Judgment on the Pleadings and Brief and Appendix in Support (ECF Nos. 263–64), filed March 16, 2015; Plaintiff’s Response (ECF No. 271), filed April 6, 2015; and Defendants’ Reply (ECF No. 275), filed April 20, 2015; and Defendants’ Motion for a Hearing (ECF No. 278), filed May 1, 2015. Having considered the motion, related briefing, pleadings, and applicable law, the Court finds that Defendants’ Motion for Judgment on the Pleadings should be 1 The Court has since dismissed all claims against Defendant Twitter per the Joint Stipulation of Dismissal (ECF No. 283), filed May 21, 2015. Case 7:14-cv-00014-O Document 284 Filed 05/28/15 Page 2 of 15 PageID 16356 and is hereby DENIED. Accordingly, Defendants’ Motion for a Hearing is DENIED as moot. I. BACKGROUND On February 18, 2014, Summit 6 filed this patent infringement lawsuit alleging infringement against application developer Twitter and four mobile device manufacturers and their affiliates, namely, Apple, HTC, Motorola, and LG Electronics, Inc., LG Electronics USA, Inc., and LG Electronics MobileComm USA, Inc. -
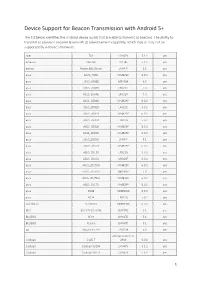
Device Support for Beacon Transmission with Android 5+
Device Support for Beacon Transmission with Android 5+ The list below identifies the Android device builds that are able to transmit as beacons. The ability to transmit as a beacon requires Bluetooth LE advertisement capability, which may or may not be supported by a device’s firmware. Acer T01 LMY47V 5.1.1 yes Amazon KFFOWI LVY48F 5.1.1 yes archos Archos 80d Xenon LMY47I 5.1 yes asus ASUS_T00N MMB29P 6.0.1 yes asus ASUS_X008D MRA58K 6.0 yes asus ASUS_Z008D LRX21V 5.0 yes asus ASUS_Z00AD LRX21V 5.0 yes asus ASUS_Z00AD MMB29P 6.0.1 yes asus ASUS_Z00ED LRX22G 5.0.2 yes asus ASUS_Z00ED MMB29P 6.0.1 yes asus ASUS_Z00LD LRX22G 5.0.2 yes asus ASUS_Z00LD MMB29P 6.0.1 yes asus ASUS_Z00UD MMB29P 6.0.1 yes asus ASUS_Z00VD LMY47I 5.1 yes asus ASUS_Z010D MMB29P 6.0.1 yes asus ASUS_Z011D LRX22G 5.0.2 yes asus ASUS_Z016D MXB48T 6.0.1 yes asus ASUS_Z017DA MMB29P 6.0.1 yes asus ASUS_Z017DA NRD90M 7.0 yes asus ASUS_Z017DB MMB29P 6.0.1 yes asus ASUS_Z017D MMB29P 6.0.1 yes asus P008 MMB29M 6.0.1 yes asus P024 LRX22G 5.0.2 yes blackberry STV100-3 MMB29M 6.0.1 yes BLU BLU STUDIO ONE LMY47D 5.1 yes BLUBOO XFire LMY47D 5.1 yes BLUBOO Xtouch LMY47D 5.1 yes bq Aquaris E5 HD LRX21M 5.0 yes ZBXCNCU5801712 Coolpad C106-7 291S 6.0.1 yes Coolpad Coolpad 3320A LMY47V 5.1.1 yes Coolpad Coolpad 3622A LMY47V 5.1.1 yes 1 CQ CQ-BOX 2.1.0-d158f31 5.1.1 yes CQ CQ-BOX 2.1.0-f9c6a47 5.1.1 yes DANY TECHNOLOGIES HK LTD Genius Talk T460 LMY47I 5.1 yes DOOGEE F5 LMY47D 5.1 yes DOOGEE X5 LMY47I 5.1 yes DOOGEE X5max MRA58K 6.0 yes elephone Elephone P7000 LRX21M 5.0 yes Elephone P8000 -

HTC Partnering with Other Chip Makers for Cheaper Smartphones
Dec 01, 2013 09:09 GMT HTC partnering with other chip makers for cheaper smartphones HTC is partnering with other chip makers for cheaper smartphones. According to FocusTaiwan, “Taipei, Nov. 27 (CNA) Taiwan's HTC Corp. is thinking of making more smartphones with chips other than those of its long- time partner Qualcomm Inc., in an effort to tackle the stiff competition from low-cost phone manufacturers. “The strategy was backed by the announcement Wednesday of four mid- range HTC Desire phones in Taiwan, which will go on sale at between NT$7,900 (US$267) and NT$13,900 via the country's three major telecom operators. “Among the four new models, only the 4.3-inch Desire 300 carries a Qualcomm MSM8225 dual-core 1GHz processor. “The Desire 501, also a 4.3-inch model, is powered by an ST-Ericsson U8520 dual-core 1.15GHz processor, while the dual-SIM Desire 601 sports a Broadcom Java quad-core 1.2GHz processor, and the Desire 700 carries a Spreadtrum Shark quad-core 1.2GHz processor, according to HTC.” Head of China and North Asia President at HTC, Jack Tong, told reporters, “From the perspective of Qualcomm, MediaTek Inc. and other chipmakers, they should be thinking about how to take advantage of the overall trend to secure and expand their ground in the market. So there's likely to be a restructuring.” Tong added, “HTC will evaluate the situation. If most players in the industry are seeking high performance to cost, then we would not be able to ignore such a trend despite good design and applications.” Can HTC get its mojo back by partnering with other chip makers? Drop a comment below. -

Albert Shih ASSOCIATE
Albert Shih ASSOCIATE Litigation Palo Alto [email protected] 650-849-3022 FOCUS AREAS EXPERIENCE Albert Shih is an associate in the Palo Alto office of Wilson Sonsini Goodrich & Rosati, Litigation where his practice focuses on intellectual property litigation and counseling. He has litigated Patent Litigation more than 25 patent cases before federal district courts, the International Trade Commission, and Judicial Arbitration and Mediation Services, including a $31 million judgment obtained for his client in the field of telecommunication protocol. He also regularly advises clients on company intellectual property strategy, technology transactions, licensing negotiation, FRAND-rate setting for standard-essential patents, and patent prosecution matters. Prior to law school, Albert was a design engineer at Intel, where he taught courses at Intel University on chipset design. His field experience and knowledge allow him to understand and appreciate the unique business and technical perspective associated with leaders and innovators in the field of mobile telecommunication protocol, baseband processor, liquid crystal display, semiconductor fabrication, digital signal processors, digital receivers and tuners, image sensors, Internet security software, and various digital and analog circuit designs. Educated in Taiwan and Singapore in his early years, Albert is fluent in Mandarin Chinese. CREDENTIALS Education J.D., Loyola Law School, Los Angeles B.S., Electrical Engineering, University of Michigan, Ann Arbor Associations and Memberships Member, American Bar Association, Intellectual Property Section Member, American Intellectual Property Law Association Member, Asia Pacific Intellectual Property Association Member, International Trade Commission Trial Lawyer Association Honors Named to the 2015-2018 editions of the "Rising Stars" list published by Northern California Super Lawyers Admissions State Bar of California U.S. -

HTC U11 Life 2 Contents Contents
User guide HTC U11 life 2 Contents Contents Features you'll enjoy Edge Sense 11 What's special with Camera 11 Immersive sound 12 HTC Alexa 12 HTC Sense Companion 13 Fingerprint sensor 13 Truly personal 14 Boost+ 15 Android 7 Nougat 16 Unboxing and setup HTC U11 life overview 18 Card tray 19 nano SIM card 20 Storage card 22 Charging the battery 26 Water and dust resistant 26 Switching the power on or off 28 Setting up HTC U11 life for the first time 29 Adding your social networks, email accounts, and more 30 Fingerprint scanner 30 Your first week with your new phone HTC Sense Home 32 Sleep mode 32 Lock screen 33 Motion gestures 33 Touch gestures 35 Getting to know your settings 38 Using Quick Settings 39 Capturing your phone's screen 40 Travel mode 40 Restarting HTC U11 life (Soft reset) 40 Notifications 41 Motion Launch 43 Selecting, copying, and pasting text 46 Entering text 46 How can I type faster? 47 Getting help and troubleshooting 49 Edge Sense What is Edge Sense? 50 Taking camera shots using Edge Sense 51 3 Contents Changing the action to take when you squeeze the phone 51 Enabling Advanced mode 52 Typing with your voice with Edge Sense 53 Adjusting the squeeze force level 53 HTC Alexa What is HTC Alexa? 54 Setting up HTC Alexa 54 Using HTC Alexa 55 HTC Sense Companion What is HTC Sense Companion? 56 Setting up HTC Sense Companion 56 Viewing the detail cards 57 Updates Software and app updates 58 Installing a software update 59 Installing an application update 59 Installing app updates from Google Play Store 59 Home screen layout -

HTC-5G-HUB Datasheet Overview
HTC-5G-HUB Datasheet Get a Quote Overview Related 5G Routers Model Speed Wi-Fi 6 CPU Support 5G Bands 4G LTE 5G: 1.65Gbps/ 250Mbps Huawei 5G CPE Pro H112-372 N Balong 5000 5G: n41/ n77/ n78/ n79 LTE: B1/3/5/7/8/18/19/20/28/32/34/38/39/40/41/42/43 4G : 1.6Gbps/ 150Mbps 5G: 1.65Gbps/ 250Mbps Huawei 5G CPE Pro H112-370 Y Balong 5000 5G: n78 LTE: B1/3/5/7/8/18/19/20/28/32/34/38/39/40/41/42/43 4G: 1.6Gbps/ 150Mbps 5G: 5G: 3.6Gbps/ 250Mbps n1/ 3/ 5/ 7/ 28/ 38/ 40(2300– Huawei 5G CPE Pro 2 H122-373 Y Balong 5000 LTE: B1/3/5/7/8/20/28/32/34/38/39/40(2300–2390 MHz)/41/42/43 4G: 1.6Gbps/ 150Mbps 2390 MHz)/ 41/ 77/ 78/ 79/ 80/ 84 5G: 1.65Gbps/ 250Mbps Huawei 5G CPE Win H312-371 N Balong 5000 5G: n41/ n77/ n78/ n79 LTE: B1/3/5/7/8/18/19/20/28/32/34/38/39/40/41/42/43 4G: 1.6Gbps/ 150Mbps 5G: 1.65Gbps/ 250Mbps LTE FDD: B1, B3, B5, B7, B8, B20, B28, B32 Huawei 5G Mobile WiFi E6878-870 N Balong 5000 5G: n41/ n77/ n78/ n79 4G: 300Mbps/ 75Mbps LTE TDD: B34, B38, B39, B40, B41, B42 5G: 1.65Gbps/ 250Mbp LTE FDD: B1, B3, B5, B7, B8, B20, B28, B32 Huawei 5G Mobile WiFi Pro E6878-370 N Balong 5000 5G: n41/ n77/ n78/ n79 4G: 300Mbps/ 75Mbps LTE TDD: B34, B38, B39, B40, B41, B42 ZTE 5G CPE Indoor WiFi MC801 5G: 2.8Gbps Y Qualcomm Snapdragon X50 5G: n41/ n77/ n78/ n79 4G LTE™: Global FDD and TDD, 600MHz~3.8GHz, CAT20 5G: n41/78/79/1/28 ZTE 5G CPE MC801A WiFi 6 Router 5G: 4.6Gbps Y Qualcomm Snapdragon X55 4G LTE™: Global FDD and TDD, 600MHz~3.8GHz, CAT22 4G: B1/3/5/8/28/34/39/40 5G: NSA 4.1Gbps/ 660Mbps OPPO 5G CPE T1 SA 2.1Gbps/ 900Mbps Y Qualcomm Snapdragon X55 5G: n1/ n41/ n78/ n79 FDD-LTE: B1/3/5/8/28 TDD-LTE: B34/38/39/40/41 4G: 2.0Gbps/ 210Mbps Learn More: 5G Devices Command the rapid speeds of the future with the HTC 5G Hub. -

David B. Yoffie Harvard Business School
David B. Yoffie Harvard Business School ©David B. Yoffie, not for distribution or reproduction without permission HTC was one of a dozen great success stories of the last decade from Taiwan ◦ Jumped on a big, new emerging arena ◦ Three strategic bets Microsoft, then Google’s Android Network operators vs. Handset mfgs Horizontal vs. vertical (next slide) ©David B. Yoffie, not for distribution or reproduction without permission Vertical vs. Horizontal App Store Operating system Operating App Store system Hardware Hardware Chips ©David B. Yoffie, not for distribution or reproduction without permission 350% HTC Corporation 300% Apple Inc. Nokia Corporation 250% Research In Motion Limited HTC Samsung Electronics Co. Ltd. 200% 150% Apple 100% 50% 0% Samsung -50% -100% Source: S&P Capital IQ Slides restricted to HBS Strategy & Technology students 2012 ©David B. Yoffie, not for distribution or reproduction without permission Apple S&P 500 Samsung HTC Slides restricted to HBS Strategy & Technology students 2012 ©David B. Yoffie, not for distribution or reproduction without permission How many smartphones estimated for 2014? ~1.2 billion from 900m in 2013 (according to IDC) What’s the average wholesale price of smartphone? -$250 (down from $344 in 2011); what’s Apple? -$650 How much time/day did the average user spend on a smartphone in 2013? 1 hour, 7 minutes up from 22 minutes in 2011 How many times per day does the average smartphone user check their phone? 150! ©David B. Yoffie, not for distribution or reproduction without permission Comp advantages ◦ Strong products HTC One ◦ Carrier focus Established relations with key distribution channel ◦ Rapid pdt dev capabilities Faster than competition Sense Proprietary UI ◦ Low cost mfg base ◦ Growing fast in China ◦ Google, Msft partnerships ©David B.