Systems Security Engineering Cyber Resiliency Considerations for the Engineering of Trustworthy Secure Systems
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Systems Security Engineering Considerations for a Multidisciplinary Approach in the Engineering of Trustworthy Secure Systems
NIST Special Publication 800-160 VOLUME 1 Systems Security Engineering Considerations for a Multidisciplinary Approach in the Engineering of Trustworthy Secure Systems RON ROSS MICHAEL McEVILLEY JANET CARRIER OREN This publication contains systems security engineering considerations for ISO/IEC/IEEE 15288:2015, Systems and software engineering — System life cycle processes. It provides security-related implementation guidance for the standard and should be used in conjunction with and as a complement to the standard. This publication is available free of charge from: https://doi.org/10.6028/NIST.SP.800-160v1 NIST Special Publication 800-160 VOLUME 1 Systems Security Engineering Considerations for a Multidisciplinary Approach in the Engineering of Trustworthy Secure Systems RON ROSS Computer Security Division National Institute of Standards and Technology MICHAEL McEVILLEY The MITRE Corporation JANET CARRIER OREN Legg Mason This publication is available free of charge from: https://doi.org/10.6028/NIST.SP.800-160v1 November 2016 INCLUDES UPDATES AS OF 03-21-2018: PAGE XIII U.S. Department of Commerce Penny Pritzker, Secretary National Institute of Standards and Technology Willie May, Under Secretary of Commerce for Standards and Technology and Director SPECIAL PUBLICATION 800-160, VOLUME 1 SYSTEMS SECURITY ENGINEERING A Multidisciplinary Approach in the Engineering of Trustworthy Secure Systems ________________________________________________________________________________________________ Authority This publication has been developed by NIST to further its statutory responsibilities under the Federal Information Security Modernization Act (FISMA) of 2014, 44 U.S.C. § 3551 et seq., Public Law (P.L.) 113-283. NIST is responsible for developing information security standards and guidelines, including minimum requirements for federal information systems, but such standards and guidelines shall not apply to national security systems without the express approval of appropriate federal officials exercising policy authority over such systems. -

Practicing a Science of Security a Philosophy of Science Perspective
Practicing a Science of Security A Philosophy of Science Perspective Jonathan M. Spring Tyler Moore David Pym University College London The University of Tulsa University College London Gower Street 800 South Tucker Drive London WC1E 6BT London WC1E 6BT Tulsa, OK 74104-9700 Alan Turing Institute [email protected] [email protected] [email protected] ABSTRACT Experiments Structured observations of the empirical are untenable world Our goal is to refocus the question about cybersecurity re- Reproducibility Evaluate by repetition, replication, varia- search from ‘is this process scientific’ to ‘why is this scientific is impossible tion, reproduction, and/or corroboration process producing unsatisfactory results’. We focus on five No laws of common complaints that claim cybersecurity is not or can- Mechanistic explanation of phenomena nature not be scientific. Many of these complaints presume views to make nature intelligible No single associated with the philosophical school known as Logical Em- Specialization necessitates translation ontology piricism that more recent scholarship has largely modified or rejected. Modern philosophy of science, supported by mathe- ‘Just’ Both science and engineering are neces- matical modeling methods, provides constructive resources engineering sary to mitigate all purported challenges to a science of security. Table 1: Five common complaints raised by the science of cy- Therefore, we argue the community currently practices a bersecurity community and positive reframing from the phi- science of cybersecurity. A philosophy of science perspective losophy of science literature. suggests the following form of practice: structured observa- tion to seek intelligible explanations of phenomena, evaluating explanations in many ways, with specialized fields (including engineering and forensics) constraining explanations within Its proponents claim a science of security is needed for ongo- their own expertise, inter-translating where necessary. -

A Cybersecurity Testbed for Industrial Control Systems
A Cybersecurity Testbed for Industrial Control Systems R. Candell, D.M. Anand, and K. Stouffer National Institute of Standards and Technology, Gaithersburg MD, U.S.A [rick.candell, dhananjay.anand, keith.stouffer]@nist.gov Abstract — The National Institute of Standards and Technology (NIST) is developing a cybersecurity testbed for industrial control systems (ICS). The goal of this testbed is to measure the performance of an ICS when instrumented with cybersecurity protections in accordance with practices prescribed by prevailing standards and guidelines. This paper outlines the testbed design and lists research goals, use cases, and performance metrics currently being considered. The paper is also intended to initiate discussion between control and security practitioners – two groups that have had little interaction in the past. Research outcomes from the testbed will highlight specific cases where security technologies impact control performance, as well as motivate methods by which control engineers can leverage security engineering to design control algorithms that extend safety and fault tolerance to include advanced persistent threats. Keywords — industrial control systems, robotics, chemical process control, cybersecurity, industrial security, process resilience, penetration testing, process performance, measurement science, testbed, robotics, robot control, safety, supervisory control and data acquisition (SCADA) I. Introduction Given the increasing interest in security of industrial control systems (ICS) and the evolving nature of advanced persistent threats against critical industrial infrastructure [1], the National Institute of Standards and Technology (NIST) has been actively involved in developing standards for cyber and control systems security via several standards bodies. Examples of such standards and guidelines include [2] and [3]. A research testbed, currently in development at NIST, will provide a platform on which to apply cybersecurity strategies to use cases that are practically relevant to industry. -

Cyber Security Engineering, Bs
2016-2017 Volgenau School of Engineering CYBER SECURITY ENGINEERING, B.S. 2016 - 2017 Cyber Security Engineering is concerned with the development of cyber resilient systems which include the protection of the physical as well as computer and network systems. It requires a proactive approach in engineering design of physical systems with cyber security incorporated from the beginning of system development. Cyber security engineering is an important quantitative methodology to be used in all industries to include, but not limited to, transportation, energy, healthcare, infrastructure, finance, government (federal, state, and local), and defense. The program is focused on the cyber security engineering of integrated cyber-physical systems. This degree provides a foundation in cyber security engineering, and is most appropriate for students with a strong mathematics and science background. The program is administered by the Dean's Office, Volgenau School of Engineering. Cyber security engineers are part of integrated design and development teams for physical systems that require embedded cyber security design, working with engineers from other disciplines (e.g. civil, mechanical, electrical, systems engineers as well as computer scientists and software engineers). Cyber security engineers are engineers who know technology, but who also have in-depth exposure to the application/domain area. Not only do they provide technological solutions to cyber security problems of engineering systems posed by others, but by having an understanding of the application/domain, they can formulate potential security threats, propose appropriate solutions, and then provide leadership in the design of a system to resist and survive these threats. Because of their interdisciplinary training, cyber security engineers are expected to play an increasing role in attacking some of the most pressing current cyber security issues in the country. -

National Privacy Research Strategy
NATIONAL PRIVACY RESEARCH STRATEGY National Science and Technology Council Networking and Information Technology Research and Development Program June 2016 National Privacy Research Strategy About the National Science and Technology Council The National Science and Technology Council (NSTC) is the principal means by which the Executive Branch coordinates science and technology policy across the diverse entities that make up the Federal research and development (R&D) enterprise. One of the NSTC’s primary objectives is establishing clear national goals for Federal science and technology investments. The NSTC prepares R&D packages aimed at accomplishing multiple national goals. The NSTC’s work is organized under five committees: Environment, Natural Resources, and Sustainability; Homeland and National Security; Science, Technology, Engineering, and Mathematics (STEM) Education; Science; and Technology. Each of these committees oversees subcommittees and working groups that are focused on different aspects of science and technology. More information is available at www.whitehouse.gov/ostp/nstc. About the Office of Science and Technology Policy The Office of Science and Technology Policy (OSTP) was established by the National Science and Technology Policy, Organization, and Priorities Act of 1976. OSTP’s responsibilities include advising the President in policy formulation and budget development on questions in which science and technology are important elements; articulating the President’s science and technology policy and programs; and fostering strong partnerships among Federal, state, and local governments, and the scientific communities in industry and academia. The Director of OSTP also serves as Assistant to the President for Science and Technology and manages the NSTC. More information is available at www.whitehouse.gov/ostp. -

Systems Security Engineering Fact Sheet
The MITRE Corporation Systems Security Engineering The MITRE Corporation is using Systems Security Engineering (SSE) to ensure the U.S. Air Force fields and sustains resilient capabilities that provide mission assurance against evolving threats. SSE uses scientific and engineering principles to deliver assured system-level protection via a single, full-system/full life cycle view of system security. The Challenge Requirements DMS* Cyber attacks, and our ability to effectively deal with them, impact Cryptography Program our nation’s infrastructure, military Software Protection Assurance capabilities, and commercial and military industry partners. Cyber Anti- HW Supply Chain Risk Tamper technology is thoroughly embed- Assurance Management ded into everything we engineer, including both business and weap- Sustainment Other Information ons systems. The historical ways Assurance in which we acquire, operate, and *Diminishing Manufacturing Sources sustain our systems must change Typical security engineering approach: “As Is” because, given time, sophisticated and persistent attackers will get in. Holistic, integrated, program protection The Solution Systems Security Engineering (SSE) New thinking in the applica- tions of systems engineering is Systems Security Engineering Engineering (SSE) Instructions for required in the face of evolving CPI Identification Engineering threats. MITRE is working with Instructions for SSE Integrated our sponsors to address these Technical Process challenges in a holistic manner (SITP) Anti-Tamper that allows the -

Contribution to Study Period on Privacy Engineering Framework
PReparing Industry to Privacy-by-design by supporting its Application in REsearch Contribution to Study Period on Privacy Engineering Framework Project: PRIPARE Project Number: ICT -6106 Title: Contribution to Study Period on Privacy Engineering Framework Version: v1.0 Part of the Seventh Date: 06/08/2015 Framework Programme Confidentiality: Public Funded by the EC - DG CNECT Author/s: Antonio Kung, Christophe Jouvray (Trialog), Nicolas Notario, Alberto Crespo (Atos), Samuel Martin, José del Álamo (UPM), Carmela Troncoso (Gradiant). PRIPARE Contribution to Study Period on Privacy Engineering Framework v1.0 Table of Contents SUMMARY ..........................................................................................................4 LIST OF FIGURES ..................................................................................................5 ABBREVIATIONS AND DEFINITIONS .....................................................................5 1 INTRODUCTION ............................................................................................6 2 PRIVACY FRAMEWORK VERSUS PRIVACY ENGINEERING FRAMEWORK .........7 2.1 ABOUT FRAMEWORKS ................................................................................................ 7 2.2 POSITIONING PRIVACY ENGINEERING IN ORGANISATIONS..................................................... 7 2.3 WHY A PRIVACY ENGINEERING FRAMEWORK? ................................................................ 10 2.3.1 Need for Convergence of Terms.................................................................. -

Opening & Welcoming Remarks
Tuesday, April 10 – Wednesday, April 11, 2018, Washington, DC Opening & Welcoming Remarks Speaker 1 Joe Bhatia, President and CEO, ANSI Welcoming Remarks from ANSI Joe Bhatia has been president and CEO of the American National Standards Institute (ANSI) since January 2006. He previously served as executive vice president and COO of the international group at Underwriters Laboratories (UL). Mr. Bhatia serves as vice chairman of the Industry Trade Advisory Committee on Standards and Technical Trade Barriers (ITAC 16), a joint program of the U.S. Department of Commerce and U.S. Trade Representative. He is a member of the International Organization for Standardization (ISO) Council and its Council Standing Committee on Finance, and holds a seat on the Oakton Community College Education Foundation Board. In 2017 he concluded his term as president of the Pan American Standards Commission (COPANT), where he also served as vice president for four years. Speaker 2 Christoph Winterhalter, Chairman of the Executive Board of DIN Welcoming Remarks from DIN After studying computer science at the University of Karlsruhe Winterhalter started his career at ABB. After assignments in Norway, USA and Germany he took over the business units robot automation and robotics products. In 2010 he became director of the German Research Center of ABB until he was promoted global Product Group manager heading ABB’s global Machinery Controls and Automation business and later Hub Business Manager Control Technologies. Since July 2016 he is Chairman of the Executive Board of DIN. Speaker 3 Thomas Sentko, Standards Manager, International of DKE Welcoming remarks from DKE 2 Thomas studied electrical engineering/telecommunications at the University of Applied Sciences Darmstadt and graduated with the degree Dipl.Ing. -
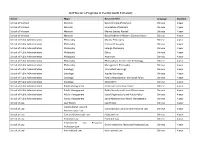
2019 Doctor's Programs in Central South University
2019 Doctor’s Programs in Central South University School Major Research Field Language Duration School of Marxism Marxism Basic Principle of Marxism Chinese 4 year School of Marxism Marxism Sinicization of Marxism Chinese 4 year School of Marxism Marxism Marxist Studies Abroad Chinese 4 year School of Marxism Marxism Basic Problem of Modern Chinese history Chinese 4 year School of Public Administration Philosophy Marxist Philosophy Chinese 4 year School of Public Administration Philosophy Chinese Philosophy Chinese 4 year School of Public Administration Philosophy Foreign Philosophy Chinese 4 year School of Public Administration Philosophy Ethics Chinese 4 year School of Public Administration Philosophy Aesthetics Chinese 4 year School of Public Administration Philosophy Philosophy of Science and Technology Chinese 4 year School of Public Administration Philosophy Management Philosophy Chinese 4 year School of Public Administration Sociology Theoretical Sociology Chinese 4 year School of Public Administration Sociology Applied Sociology Chinese 4 year School of Public Administration Sociology Public Administration and Social Policy Chinese 4 year School of Public Administration Sociology Social Work Chinese 4 year School of Public Administration Public Management Urban and Local Governance Chinese 4 year School of Public Administration Public Management Public Security and Hazard Governance Chinese 4 year School of Public Administration Public Management Social Organizations and Public Policy Chinese 4 year School of Public Administration -

Privacy Engineering for Social Networks
UCAM-CL-TR-825 Technical Report ISSN 1476-2986 Number 825 Computer Laboratory Privacy engineering for social networks Jonathan Anderson December 2012 15 JJ Thomson Avenue Cambridge CB3 0FD United Kingdom phone +44 1223 763500 http://www.cl.cam.ac.uk/ c 2012 Jonathan Anderson This technical report is based on a dissertation submitted July 2012 by the author for the degree of Doctor of Philosophy to the University of Cambridge, Trinity College. Technical reports published by the University of Cambridge Computer Laboratory are freely available via the Internet: http://www.cl.cam.ac.uk/techreports/ ISSN 1476-2986 Privacy engineering for social networks Jonathan Anderson In this dissertation, I enumerate several privacy problems in online social net- works (OSNs) and describe a system called Footlights that addresses them. Foot- lights is a platform for distributed social applications that allows users to control the sharing of private information. It is designed to compete with the performance of today’s centralised OSNs, but it does not trust centralised infrastructure to en- force security properties. Based on several socio-technical scenarios, I extract concrete technical problems to be solved and show how the existing research literature does not solve them. Addressing these problems fully would fundamentally change users’ interactions with OSNs, providing real control over online sharing. I also demonstrate that today’s OSNs do not provide this control: both user data and the social graph are vulnerable to practical privacy attacks. Footlights’ storage substrate provides private, scalable, sharable storage using untrusted servers. Under realistic assumptions, the direct cost of operating this storage system is less than one US dollar per user-year. -

Predictability for Privacy in Data Driven Government
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by University of Minnesota Law School Minnesota Journal of Law, Science & Technology Volume 20 Issue 1 Article 3 1-6-2019 Predictability for Privacy in Data Driven Government Jordan Blanke Mercer University Janine Hiller Virginia Tech Follow this and additional works at: https://scholarship.law.umn.edu/mjlst Part of the Administrative Law Commons, Privacy Law Commons, and the Science and Technology Law Commons Recommended Citation Jordan Blanke & Janine Hiller, Predictability for Privacy in Data Driven Government, 20 MINN. J.L. SCI. & TECH. 32 (2018). Available at: https://scholarship.law.umn.edu/mjlst/vol20/iss1/3 The Minnesota Journal of Law, Science & Technology is published by the University of Minnesota Libraries Publishing. Predictability for Privacy in Data Driven Government Jordan M. Blanke* and Janine S. Hiller† Abstract The Deferred Action for Childhood Arrivals program (DACA) required individuals to provide a great deal of personal information in order to participate and remain in the United States legally; could information in the same system now be used for deportations? More broadly, how should systems of data that are created legitimately by United States agencies and compiled for one reason, be used for other reasons? The increasing emphasis on “smart cities” that use data to efficiently provide and plan for service delivery will require the integration of data from multiple government and non- government sources, in ways that citizens may not expect. There are increasing calls for the federal government to open up and share the data collected for one reason for use in additional, unrelated ways, and to combine that data with data collected by commercial, private entities. -

Security Requirements Reusability and the SQUARE Methodology
Security Requirements Reusability and the SQUARE Methodology Travis Christian Faculty Advisor Nancy Mead September 2010 TECHNICAL NOTE CMU/SEI-2010-TN-027 CERT® Program Unlimited distribution subject to the copyright. http://www.sei.cmu.edu This report was prepared for the SEI Administrative Agent ESC/XPK 5 Eglin Street Hanscom AFB, MA 01731-2100 The ideas and findings in this report should not be construed as an official DoD position. It is published in the interest of scientific and technical information exchange. This work is sponsored by the U.S. Department of Defense. The Software Engineering Institute is a federally funded research and development center sponsored by the U.S. Department of Defense. Copyright 2010 Carnegie Mellon University. NO WARRANTY THIS CARNEGIE MELLON UNIVERSITY AND SOFTWARE ENGINEERING INSTITUTE MATERIAL IS FURNISHED ON AN ―AS-IS‖ BASIS. CARNEGIE MELLON UNIVERSITY MAKES NO WARRANTIES OF ANY KIND, EITHER EXPRESSED OR IMPLIED, AS TO ANY MATTER INCLUDING, BUT NOT LIMITED TO, WARRANTY OF FITNESS FOR PURPOSE OR MERCHANTABILITY, EXCLUSIVITY, OR RESULTS OBTAINED FROM USE OF THE MATERIAL. CARNEGIE MELLON UNIVERSITY DOES NOT MAKE ANY WARRANTY OF ANY KIND WITH RESPECT TO FREEDOM FROM PATENT, TRADEMARK, OR COPYRIGHT INFRINGEMENT. Use of any trademarks in this report is not intended in any way to infringe on the rights of the trademark holder. Internal use. Permission to reproduce this document and to prepare derivative works from this document for internal use is granted, provided the copyright and ―No Warranty‖ statements are included with all reproductions and derivative works. External use. This document may be reproduced in its entirety, without modification, and freely distributed in written or electronic form without requesting formal permission.