Investigation Handbook
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Proquest Dissertations
A Changing Sense of Place in Canadian Daily Newspapers: 1894-2005 By Carrie Mersereau Buchanan A.B. Bryn Mawr College M.J. Carleton University, School of Journalism and Communication A thesis submitted to The Faculty of Graduate Studies and Research in partial fulfillment of the requirements for the degree of Doctor of Philosophy School of Journalism and Communication Faculty of Public Affairs Carleton University Ottawa, Ontario December 2009 © Carrie Mersereau Buchanan 2009 Library and Archives Bibliotheque et 1*1 Canada Archives Canada Published Heritage Direction du Branch Patrimoine de I'edition 395 Wellington Street 395, rue Wellington Ottawa ON K1A 0N4 OttawaONK1A0N4 Canada Canada Your file Voire r6f6rence ISBN: 978-0-494-67869-5 Our file Notre reference ISBN: 978-0-494-67869-5 NOTICE: AVIS: The author has granted a non L'auteur a accorde une licence non exclusive exclusive license allowing Library and permettant a la Bibliotheque et Archives Archives Canada to reproduce, Canada de reproduce, publier, archiver, publish, archive, preserve, conserve, sauvegarder, conserver, transmettre au public communicate to the public by par telecommunication ou par Nntemet, preter, telecommunication or on the Internet, distribuer et vendre des theses partout dans le loan, distribute and sell theses monde, a des fins commerciales ou autres, sur worldwide, for commercial or non support microforme, papier, electronique et/ou commercial purposes, in microform, autres formats. paper, electronic and/or any other formats. The author retains copyright L'auteur conserve la propriete du droit d'auteur ownership and moral rights in this et des droits moraux qui protege cette these. Ni thesis. Neither the thesis nor la these ni des extraits substantiels de celle-ci substantial extracts from it may be ne doivent etre imprimes ou autrement printed or otherwise reproduced reproduits sans son autorisation. -
Minutes of the Administration Committee
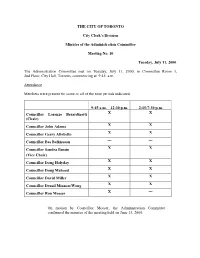
THE CITY OF TORONTO City Clerk’s Division Minutes of the Administration Committee Meeting No. 10 Tuesday, July 11, 2000. The Administration Committee met on Tuesday, July 11, 2000, in Committee Room 1, 2nd Floor, City Hall, Toronto, commencing at 9:45: a.m. Attendance Members were present for some or all of the time periods indicated. 9:45 a.m. – 12:30 p.m. 2:15-7:30 p.m. Councillor Lorenzo Berardinetti XX (Chair) Councillor John Adams XX Councillor Gerry Altobello XX Councillor Bas Balkissoon --- --- Councillor Sandra Bussin XX (Vice Chair) Councillor Doug Holyday XX Councillor Doug Mahood XX Councillor David Miller XX Councillor Denzil Minnan-Wong XX Councillor Ron Moeser X --- On motion by Councillor Moeser, the Administration Committee confirmed the minutes of the meeting held on June 13, 2000. - 2 - Administration Committee Minutes Tuesday, July 11, 2000 10.1 City of Toronto By-Law Governing Retention Periods for Records in the Custody and Control of the Toronto Police Services Board and the Toronto Police Service. The Administration Committee had before it the following: (i) a report (April 4, 2000) from the Chairman of the Toronto Police Services Board, recommending the enactment of a by-law establishing retention periods for records in the custody and control of the Toronto Police Services Board and the Toronto Police Service; and (ii) a communication (June 13, 2000) from Mr. Ted Tibor Berger advising that he has grave concerns respecting the City of Toronto By-law governing retention periods for records in the custody and control of the Toronto Police Services Board and the Toronto Police Service; and forwarding comments in regard thereto. -

Fort York News
Fort York News Rear Admiral Jennifer Bennett, OMM CD Quarterly Newsletter of Fort York Branch No.165 Spring 2015 Photo: Sgt. Peter Moon Photo: T. Sleightholm Page 2 Fort York News Winter 2015 Fort York Calendar 2015 Executive 2015 Thursday 26 March…………… Luncheon, President……………………… LCdr Donna Murakami RCMI 1st Vice President…..……. LCol Evelyn Kelly Wednesday 22 April…………… AGM, 2nd Vice President……….. Col Fred McCague Toronto Hunt Immediate Past President... Cdr Ed Sparling Thursday, 21 May……………... Garden Party, Secretary……………………… LW Joyce Lloyd McLean House Treasurer……………………… Malcolm Hamilton Thursday 25 June……………… Change of Membership Chair……….. Pte Glenn Carter Command, RCMI Chaplain……………………….. Maj Gillian Federico District D, Zone 5 Rep…… Pte Glenn Carter Dinner Reservations Events Co-Ordinator…….. Maj George Chabrol When making your dinner meeting reservation with our F.Y. News/Historian……….Terry Sleightholm Events Chair, Major George Chabrol, please include the Messing……………………….. F/Lt Chuck Casson names of your guests. It will greatly assist him with his Poppy Fund Chair…………. LCdr Ed Sparling record keeping. Sgt-at-Arms………………….. Capt Larry Rose Newsletter Staff Public Relations……………. Sgt Peter Moon Editor/Publisher…………. Terry Sleightholm Remembrancer…………….. Capt Greg Bailey Proofreaders……………….. Sgt Peter Moon Sunnybrook Liaison………. Col Jim Hubel LCdr Donna Murakami Service Bureau…………….. HCol Gil Taylor Photography………………. Sgt Peter Moon, Terry R.C.M.I. Liaison…………….. Susan Cook Sleightholm Members-at-Large……….. PO Bill Milne Printing…………………….. LCdr Donna Murakami Lt(N) Paul Costello LW Joyce Lloyd Lt Norm Gardner Our New Address Name Tags Please note that Fort York Branch 165 has a new mailbox address: Fort York Legion Branch 165 If you require a name tag, please contact Capt Stu Kellock 1421 Yonge Street and he will arrange to have one made for you. -

Minutes of the Council of the City of Toronto January 2, 1998
Appendix A MINUTES OF THE COUNCIL OF THE CITY OF TORONTO INAUGURAL MEETING FRIDAY, JANUARY 2, 1998 The Members of the first Council of the new City of Toronto, for the three-year term commencing January 1, 1998, met at 1:00 p.m. in the Council Chamber, City Hall, Toronto. The City Clerk, Mrs. Novina Wong, presided in accordance with the provisions of subsection 51(2) of the Municipal Act, R.S.O. 1990, as amended. The meeting opened with the singing of the National Anthem by Mr. Robert Pilon. 1 Members present at this meeting: Mayor: Lastman. Councillors: Adams, Altobello, Ashton, Augimeri, Balkissoon, Berardinetti, Berger, Bossons, Brown, Bussin, Cho, Chong, Chow, Davis, Disero, Duguid, Faubert, Filion, Flint, Fotinos, Gardner, Giansante, Holyday, Jakobek, Johnston, Jones, Kelly, Kinahan, King, Korwin-Kuczynski, Layton, Lindsay Luby, Li Preti, Mahood, Mammoliti, McConnell, Mihevc, Miller, Minnan-Wong, Moeser, Moscoe, Nunziata, O’Brien, Ootes, Pantalone, Prue, Saundercook, Sgro, Shaw, Shiner, Silva, Sinclair, Tzekas, Walker - 55. 2 The City Clerk called upon Rabbi Dr. David Monson, Rabbi Emeritus of Beth Sholom Synagogue, to give the invocation. 3 The City Clerk welcomed the Members of Council to the Inaugural Meeting of the Council of the new City of Toronto, and reported that she had in her possession certificates from the Clerks of the former Area Municipalities, and the Chief Returning Officer for the 1997 Municipal Election, certifying as to the persons elected and entitled to be Members of the City Council, i.e. Mel Lastman, Mayor -

Putting a Face to the Organizations in Our
Norm Gardner Owner/Artist Bobbi Farrer Co-owner STORIES THAT INSPIRE Success from one industry to the next 16 FACES PUTTING A FACE TO & the stories THE ORGANIZATIONS behind them IN OUR COMMUNITY Editor’s Letter Interviewing each and every newcomers alike, Kamloops’ one of them reinforces what business community is vast we’ve all known for decades. and diverse and includes the Kamloops is a special place. businesses you’ll read about A place where the vibrant in the upcoming pages -- business community supports Denali Landscaping (page 14), and shapes society and vice Sweet Spot Cupcakes (page versa. 10), Martin & Martin Lawyers (page 28), Jones Brothers Yes, the city has a spectacular Construction (page 24), location at the confluence Psychocity Tattoo (page 08) of the North and South and River City Nissan (page 30). Thompson rivers, nestled in mountains with enviable All the other leaders, weather. But, it’s the people, businesses and organizations businesses, government, profiled in these pages also organizations, institutions contribute to the fabric of and community groups Kamloops in their own special that make Kamloops a way. community. A community with an outstanding standard of After all, as I’ve already said, living and quality of life full of Kamloops is a special place. opportunities, recreation and YOUR STORY amenities. We all know why we live here. IS OUR BUSINESS And others want a piece of the You’ll be inspired as you action. That’s why as people read about the people in reflect on their lives in other the next 30 pages of this cities, some come to the Steve MacNaull magazine. -

MINUTES of the PUBLIC MEETING of the Toronto Police Services Board Held on AUGUST 30, 2001 at 1:30 PM in the Auditorium, 40 College Street, Toronto, Ontario
MINUTES OF THE PUBLIC MEETING of the Toronto Police Services Board held on AUGUST 30, 2001 at 1:30 PM in the Auditorium, 40 College Street, Toronto, Ontario. PRESENT: Norman Gardner, Chairman A. Milliken Heisey, Q.C., Member Mayor Mel Lastman, Member Allan Leach, Member Emilia Valentini, Member ALSO PRESENT: Julian Fantino, Chief of Police H.W.O. Doyle, Solicitor, City of Toronto Deirdre Williams, Board Administrator #P215. The Minutes of the Meeting held on JULY 20, 2001 were approved with the exception of Minute No. P200/01 which was amended by removing reference to the charitable tax receipts. THIS IS AN EXTRACT FROM THE MINUTES OF THE PUBLIC MEETING OF THE TORONTO POLICE SERVICES BOARD HELD ON AUGUST 30, 2001 #P216. EXTENSION OF APPOINTMENT - BOARD MEMBER EMILIA VALENTINI The Board was in receipt of the attached report AUGUST 07, 2001 from The Honourable David Turnbull, Solicitor General, regarding the extended appointment of Board Member Emilia Valentini. The Board received the foregoing. THIS IS AN EXTRACT FROM THE MINUTES OF THE PUBLIC MEETING OF THE TORONTO POLICE SERVICES BOARD HELD ON AUGUST 30, 2001 #P217. INTERNATIONAL ASSOCIATION OF CHIEFS OF POLICE CONFERENCE The Board was in receipt of the attached report AUGUST 8, 2001 from Douglas Fyfe, President & Chief Executive Officer, Tourism Toronto, regarding the International Association of Chiefs of Police Conference that will take place in Toronto in October 2001. Mr. Fyfe and Insp. Mike Sale, IACP Conference Chairman, were in attendance and discussed details about this conference with the Board. The Board received the foregoing. THIS IS AN EXTRACT FROM THE MINUTES OF THE PUBLIC MEETING OF THE TORONTO POLICE SERVICES BOARD HELD ON AUGUST 30, 2001 #P218. -

The History and the Future of the Politics of Policing
1 THE HISTORY AND THE FUTURE OF THE POLITICS OF POLICING By Margaret E. Beare1 Abstract This chapter examines the operational realities of the police executive linkages— beyond the official dictates of the law and the desired position expressed in ideological discourses on police independence. Paper draws primarily on historical and criminological literature and research, and public inquiries. The central argument of this paper is that, while there may be a somewhat clear- cut division between the’ policy’ versus the ‘operational’ control of the police by the State in law and in rhetoric, the reality is quite different. The relationship between the State and the police is a dynamic relationship that changes to reflect the nature of the policing that is being carried-out, the political interests of the party in power, and to some extent the personalities of the key players within both the police services and in politics at a specific period in time. This research indicates that looking for the ‘smoking gun’—i.e. the memo or document that in writing acknowledges a directive from the executive to the police— sidesteps the reality of the on-going partnerships between politics and policing. Introduction Much current controversy surrounding policing centres around two issues: the relationship between the police and politics and the question of accountability. Dianne Martins paper has addressed the issue of accountability and while the two issues overlap, I shall be looking specifically at the political question. An understanding of the organizational workings of the police is essential to any attempt to reconcile the tensions between the dictates of police autonomy and the restraints imposed on the police. -

Saving Lives: a Lt E R N Atives to the Use of Lethal Fo Rce by Police
among all members of society was the funda- among all members of society was the funda- mental principle upon which the Urban Alliance mental principle upon which the Urban Alliance on Race Relations was founded in 1975; and on Race Relations was founded in 1975; and Whereas the Queen Street Patients Council is Whereas the Queen Street Patients Council is an organization comprised entirely of consumer/ an organization comprised entirely of consume survivors which SAVIseeks to advocateNG on behalf LIV of survivorsEES:S: which seeks to advocate on behalf of its members to promote better understanding its members to promote better understanding among all of societyAL asTERN to the self-identifiedAATIVamongESES all of society as to the self-identified needs of consumers/survivors; and needs of consumers/survivors; and Whereas it is recognizedTO thatT theH issueE ofUSE the Whereas it is recognized that the issue of the use of lethal force by police is a subject of use of lethal force by police is a subject of concern to all inOF society andLETHAL that concerns concernFORCE to all in society and that concerns over police use of lethal force have contributed over police use of lethal force have contributed to a strained relationshipBY P betweenOLICE the police to a strained relationship between the police and members of black communities; and and members of black communities; and Whereas this Conference on the Alternatives Whereas this Conference on the Alternatives to the Use of Lethal Force by Police is intended to the Use of Lethal Force by -

Lloydminster Historical Profile
2 JUNE / JULY 2004 June/July 2004 Volume 16 Number 6 Publisher’s Commentary 5 The realities of a slow news day Blue Line Magazine Securing the Campus Community 6 12A-4981 Hwy 7 East Ste 254 A safe community is a minimal expectation Markham, ON L3R 1N1 Canada Positive contacts key to policing university 8 Ph: 905 640-3048 Fax: 905 640-7547 eMail: [email protected] Securing a small campus in a small town 10 — Publisher — CORRESPONDENCE 11 Morley S. Lymburner eMail: [email protected] Policing the meridian 12 Lloydminister has a policing style like no other — General Manager — Mary Lymburner, M.Ed. Earning trust key to ending crisis 14 eMail: [email protected] — Editor — A step back from the edge 16 Mark Reesor A recipe for building community confi dence eMail: [email protected] DISPATCHES 18 — News Editor — Les Linder DEEP BLUE 20 eMail: [email protected] What makes a good cop good? — Advertising — Mary Lymburner Canada’s anti-terrorism plan 22 How prepared are we when it comes to Dean Clarke anti-terrorism? Inspite of innovative RCMP Bob Murray Sudden death in restained subjects 24 concepts such as those shown on the cover of eMail: [email protected] this month’s edition, the promise is far greater New Calgary rescue system saves lives 26 — Pre-press Production — than the activity. On Page 22 of this month’s Del Wall Surviving an aircraft ditching 26 edition staff writer Les Linder gives a realistic overview of current studies and issues in rela- — Contributing Editors — tion to these pressing concerns. -

The Following Draft Minutes of the Special Meeting of the Toronto Police Services Board Held on April 29, 2013 Are Subject to Ad
The following draft Minutes of the special meeting of the Toronto Police Services Board held on April 29, 2013 are subject to adoption at its next regularly scheduled meeting. MINUTES OF THE SPECIAL PUBLIC MEETING of the Toronto Police Services Board held on APRIL 29, 2013 at 4:00 PM in Council Chambers, Toronto City Hall, Toronto, Ontario. PRESENT: Dr. Alok Mukherjee, Chair Mr. Michael Thompson, Councillor & Vice-Chair Mr. Michael Del Grande, Councillor & Member Ms. Marie Moliner, Member Dr. Dhun Noria, Member Ms. Frances Nunziata, Councillor & Member ABSENT: Mr. Andrew Pringle, Member ALSO PRESENT: Mr. William Blair, Chief of Police Mr. Albert Cohen, City of Toronto - Legal Services Division Ms. Karlene Bennett, Acting Board Administrator THIS IS AN EXTRACT FROM THE MINUTES OF THE SPECIAL PUBLIC MEETING OF THE TORONTO POLICE SERVICES BOARD HELD ON APRIL 29, 2013 #P125 PUBLIC CONSULTATION – PROFESSIONAL STANDARDS PRIORITY The Board was in receipt of the following report April 05, 2013 from Alok Mukherjee, Chair: Subject: PUBLIC CONSULTATION - PROFESSIONAL STANDARDS PRIORITY Recommendation: It is recommended that the Board determine whether there is a need to establish a Toronto Police Service priority focussed on integrity, ethics, professional standards and enhanced customer service. Financial Implications: There are no financial implications arising from the recommendation contained in this report. Background/Purpose: At its meeting held on March 27, 2013, the Board approved the following motion: 2014-2016 BUSINESS PLAN THAT, as part of the public consultations that will be held by the Board and the Toronto Police Service during the development of the 2014 - 2016 Business Plan, the Board host a public consultation meeting on the evening of Monday, April 29 at City Hall to focus on whether there is a need for the Board to establish a Toronto Police Service priority related to integrity, ethics, professional standards and enhanced customer service. -

Council Motion on Racial Profiling in Toronto
CITY CLERK Clause embodied in Report No. 1 of the Policy and Finance Committee, as adopted by the Council of the City of Toronto at its regular meeting held on February 4, 5 and 6, 2003. 16 Update - Council Motion on Racial Profiling in Toronto (City Council at its regular meeting held on February 4, 5 and 6, 2003, amended this Clause by adding thereto the following: “It is further recommended that the Chief Administrative Officer, as part of the reporting process, be requested to convene a meeting, such meeting to include the Chief of Police and the Commissioners of Community and Neighbourhood Services and Economic Development, Culture and Tourism, with other senior staff and Commissioners requested to attend.”) The Policy and Finance Committee recommends the adoption of the report (January 10, 2003) from the Chief Administrative Officer subject to amending the Recommendations contained therein to read as follows: “It is recommended: (1) in addition to the directions of Toronto City Council in the Notice of Motion approved at its meeting on October 31, 2002, the Toronto Police Services Board provide City Council with the reports that have been requested on the implementation of the Toronto Police Service race relations initiatives and that the Toronto Police Services Board also be requested to invite the Diversity Advocate, and other Members of Council of the Reference Group on Access and Equity, to attend the Board meeting at which the aforementioned report is considered; (2) the Task Force on Community Safety include race relations issues as part of its consideration of community safety issues and work with the Community Advisory Committee on Race and Ethnic Relations and community organizations as appropriate; (3) the Chief Administrative Officer be requested to maintain a watching brief on the matter of racial profiling and report to Council regularly; and (4) the appropriate City officials be authorized and directed to take the necessary action to give effect thereto.” Toronto City Council 2 Policy and Finance Committee February 4, 5 and 6, 2003 Report No. -

THE CITY of TORONTO Clerk's Department Minutes of The
THE CITY OF TORONTO Clerk's Department Minutes of the Emergency and Protective Services Committee Tuesday, April 21, 1998 The Emergency and Protective Services Committee met on Tuesday, April 21, 1998, in Committee Room A, 2nd Floor, Metro Hall, 55 John Street, Toronto, commencing at 9:30 a.m. Members Present: Councillor Dennis Fotinos, Chair Councillor Brian Ashton Councillor Milton Berger Councillor Brad Duguid Councillor Joanne Flint Councillor Norman Gardner Councillor Mario Giansante Councillor Doug Holyday Councillor Denzil Minnan-Wong Councillor Frances Nunziata Confirmation of Minutes. On motion by Councillor Holyday, the Minutes of the meeting of the Emergency and Protective Services Committee held on March 24 and 25, 1998, were confirmed. 41. By-law to amend By-law No. 20-85 - Stolen Property in Possession of Pawnbrokers. The Emergency and Protective Services Committee had before it a report (March 18, 1998) from Councillor Norman Gardner, Chairman, Toronto Police Services Board, advising that the Toronto Police Services Board on February 26, 1998, recommended that Schedule 25 of By-Law No. 20-85 be amended to include the following: a) regulating second hand shops; b) requiring proper photo identification from clients; c) having a minimum age for customers; d) strengthen the penalty section for non-compliance with the act; and e) give officers: search, seizure, and disposition authority for stolen property located at these businesses. -2- Emergency and Protective Services Committee Minutes Tuesday, April 21, 1998. The Committee referred the foregoing matter to the City Solicitor and the General Manager, Toronto Licensing Commission, for a report thereon to the next meeting of the Emergency and Protective Services Committee to be held on May 22, 1998.