INSTALLATION & CONFIGURATION OF RODC-Read Only Domain Controller- Part 2
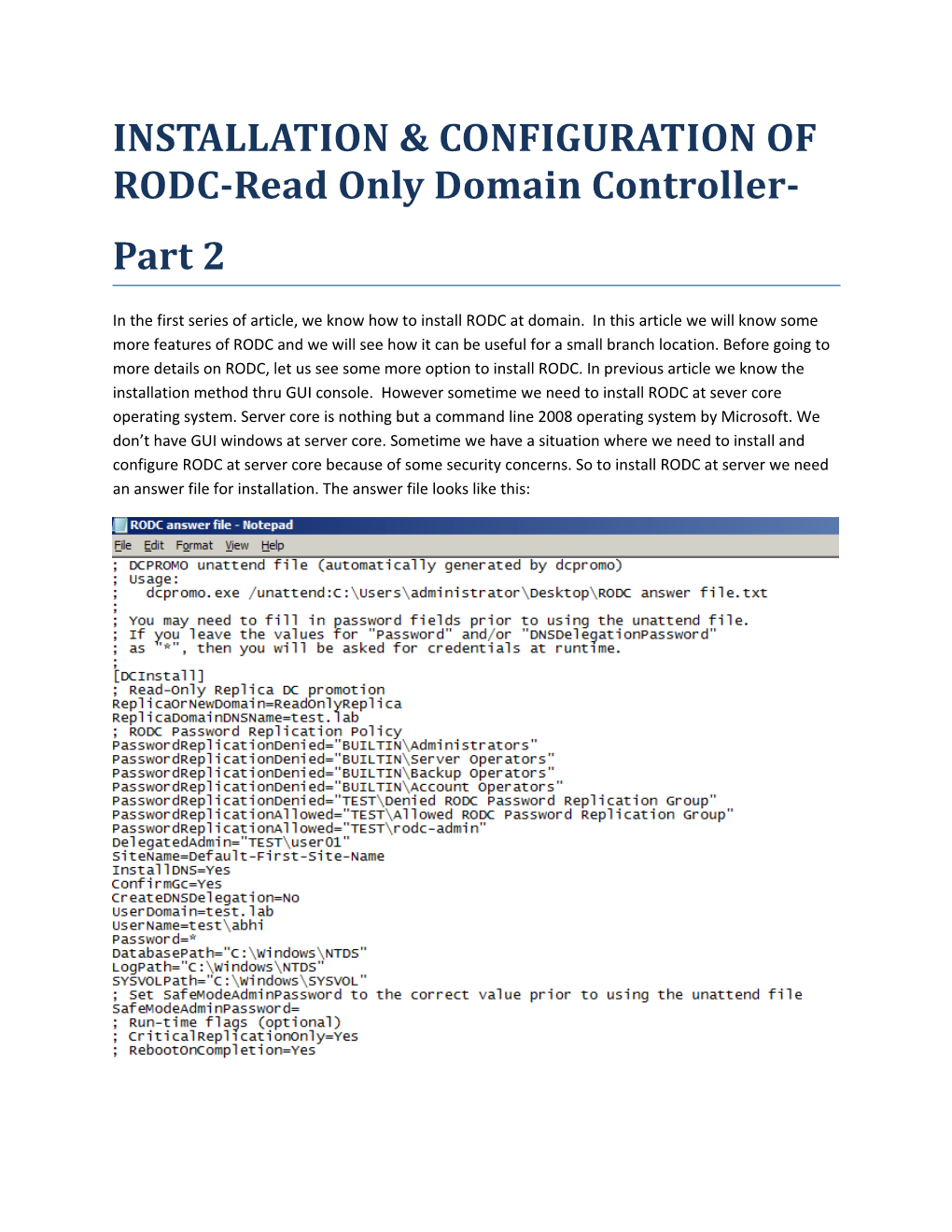
In the first series of article, we know how to install RODC at domain. In this article we will know some more features of RODC and we will see how it can be useful for a small branch location. Before going to more details on RODC, let us see some more option to install RODC. In previous article we know the installation method thru GUI console. However sometime we need to install RODC at sever core operating system. Server core is nothing but a command line 2008 operating system by Microsoft. We don’t have GUI windows at server core. Sometime we have a situation where we need to install and configure RODC at server core because of some security concerns. So to install RODC at server we need an answer file for installation. The answer file looks like this: To install from this answer file, run the command “dcpromo.exe /unattend: answer file path”
So we have our RODC server ready at our network. We will some of the properties of RODC server. Open the active directory console and go to the Domain Controllers OU and select RODC and go to the properties of RODC.
In the general tab of RODC properties, we have some general description of RODC. The full computer name, DNS name DC type, Site, description and also we have NTDS Settings there. Click on NTDS settings.
NTDS setting properties will tell some basic descriptions of the server, like the server where it is Replicate from, the attribute tab which measures the server attributes and characteristics, its canonical object name, security permission tab etc. Now we will see the delegation tab of RODC Server. This will allow services to be act on behalf of another user. If you want to allow services to be delegated for a user or computer, click Add button. Now we have very important tab of the RODC server, the ‘Password replication Policy” tab which store users and computer password according to the policy set. If you want to store user name and password click add and to see the advanced version click Advanced. Advanced tab will show policy usage and if you want to prepopulate any user or computer password for RODC server click prepopulate password
So we have seen some of the important properties of RODC server. We also had seen how to store the user and computer password to RODC. In active directory like user account we have a separate user name and password for the computer account.
So let’s we do an example to show how RODC will be used in branch location scenario. We have a domain controller in main office and we have to set the RODC at branch location.
Let’s assume that for some reason wan connection has been failed and RODC site lost the connectivity with the main site read-write domain controller. In this case, we will see how RODC will allow user to login into the domain without contacting read-write domain controller. So let’s begin:
To demonstrate this example we installed one more member server “MS1” at branch location with an ip address of 192.168.1.2
Now we have all connection live, we can easily log into the MS1 server. We logged into the member server with user account “user01” In above picture we found that hostname is MS1, and logon account name is “user01”. Now we will see this server has been authenticated by which domain controller. To get this information we run “set” from command window. From the output we know that currently this server has been authenticated by domain controller “AD” which is read –write domain controller in our case. Normally this would be happen for every case, whenever any computer/user has been logged into the domain, this will contact domain controller which have read write database. So the question came then why we need RODC, this will help to cache the credentials and store the password. In next we will see how new domain user has been logged into the server when connectivity with read-write domain controller down. So lets’ create a new user in domain “user04” which we are going to user for demonstrate purpose. To begin this, first we disconnect the connectivity with read-write domain controller so that it will not able to contact RODC and it will not use for any server authentication. So we have seen that our RODC server will not able to contact the read-write domain controller. To continue this lets try to log into the member server “MS1” with newly configured domain account “user04”. We received following error states that system cannot log you on now because the domain TEST is not available.
To log into this server without read-write domain controller we have to store the computer and user password at RODC and need to set the allow policy, so that computer has been allow to authenticate without read-write domain controller. Once we store the computer password at RODC, let’s try to login into the member server now.
And here we go………. We have successfully logged into the domain server in absence of read- write domain controller. From the above figure it shows that read-write domain controller is still down and we are able to login the member server and it’s authenticate by the RODC server.
In this article we learn some of the important properties of RODC and also we learn how to use to password replication policy at the RODC server.