Security Assessment Supporting Information Addendum VACSB HIPAA Steering Committee
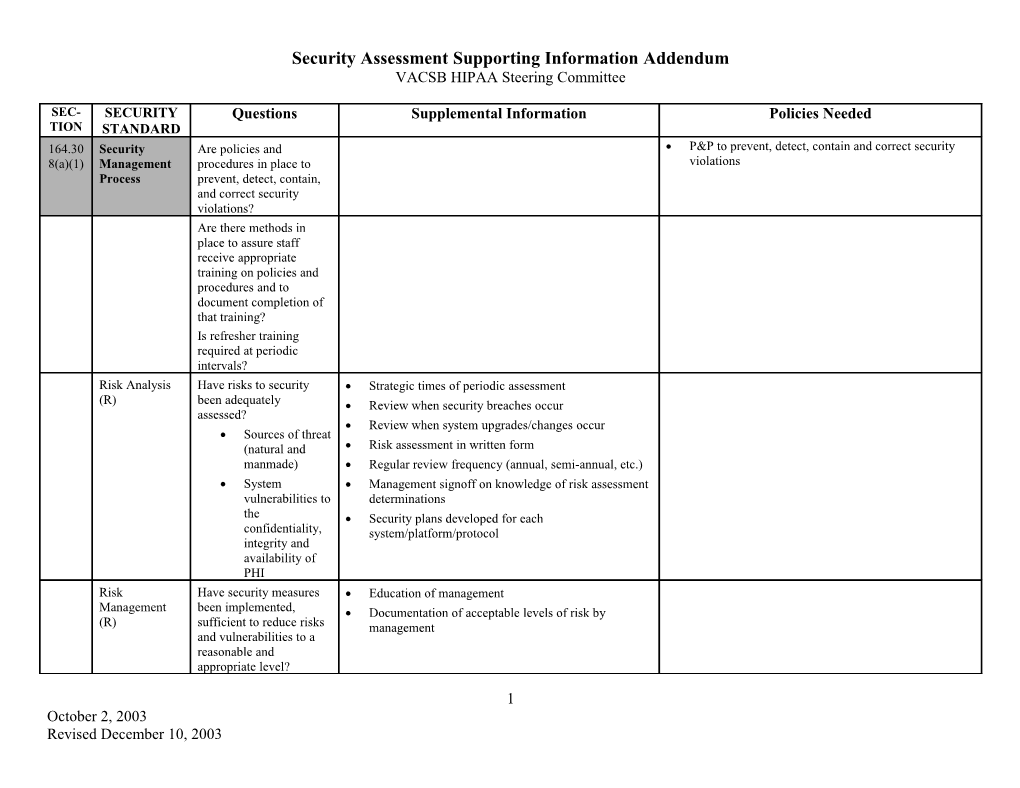
SEC- SECURITY Questions Supplemental Information Policies Needed TION STANDARD 164.30 Security Are policies and P&P to prevent, detect, contain and correct security 8(a)(1) Management procedures in place to violations Process prevent, detect, contain, and correct security violations? Are there methods in place to assure staff receive appropriate training on policies and procedures and to document completion of that training? Is refresher training required at periodic intervals? Risk Analysis Have risks to security Strategic times of periodic assessment (R) been adequately Review when security breaches occur assessed? Review when system upgrades/changes occur Sources of threat (natural and Risk assessment in written form manmade) Regular review frequency (annual, semi-annual, etc.) System Management signoff on knowledge of risk assessment vulnerabilities to determinations the Security plans developed for each confidentiality, system/platform/protocol integrity and availability of PHI Risk Have security measures Education of management Management been implemented, Documentation of acceptable levels of risk by (R) sufficient to reduce risks management and vulnerabilities to a reasonable and appropriate level?
1 October 2, 2003 Revised December 10, 2003 -- D R A F T -- Security Assessment/ Risk Analysis Tool VACSB HIPAA Steering Committee SEC- SECURITY Questions Supplemental Information Policies Needed TION STANDARD Does top management understand the risk to systems under their control and have they determined the acceptable level of risk? Sanction Policy Is there a policy that HR policies Written sanction policy for security incidents (R) addresses appropriate Include disciplinary actions sanctions against workforce members who Can system administrator or privacy officer invoke fail to comply with the disciplinary action on employees not within their agency’s policies and supervisory purview? procedures? Information Are system activity logs Security Incident reports and follow up/resolution P&P for regular review of information system System Activity monitored? How often? activity records (audit logs, access reports, and Management knowledge of security incident security incident tracking reports) Review (R) By whom? issues Look for activity in system for times when organization or department not open Look for activity in system that is outside the assigned security level of the user Look for unusual drops or spikes in disk space utilization by user Look for users who do not log off at the end of their shift (i.e., users that are logged on all night) Look for users that have sign-ons logged for days they were not working Look for unusual activity in security management areas or high level table maintenance or system profile accesses Look for users with NO activity within a specified time period; remove accesses as appropriate based on inactive accounts 164.30 Assigned Who is the assigned Level in organization for security officer (i.e., one September 5, 2003 Revised December 10, 2003 Page 2 of 13 -- D R A F T -- Security Assessment/ Risk Analysis Tool VACSB HIPAA Steering Committee SEC- SECURITY Questions Supplemental Information Policies Needed TION STANDARD 8(a)(2) Security Security Officer level down from CEO, two levels down, etc.) Responsibility responsible for the (R) development and implementation of security policies and procedures? What other staff, if any, carry primary responsibility for system security? 164.30 Workforce P&P to ensure that all members of the workforce 8(a)(3) Secu have appropriate access to electronic PHI rity P&P to prevent those workforce members who should not have access to electronic PHI
Authorization Are procedures Access methods for all workforce members P&P relative to supervising workforce members and/or implemented for the (contract, intern, employee, student, volunteer, who do not have access to electronic PHI and who Supervision (A) authorization and/or etc.) to electronic systems and information may work in locations where electronic PHI may be accessed supervision of staff Processes for auditing outstanding access devices accessing electronic PHI? (keys, swipe cards, etc.) Formal process for security access request, change, or delete Supervisory sign-off on security requests. Security officer sign-off on all security add, change, or delete requests Required screen saver/terminal locking If available, review access by client ID or other identifier by user for appropriateness Monitor all access to high profile or VIP client records Workforce Are procedures User training on security policy/procedure, with Procedures to determine that the access of a Clearance implemented to signoff of understanding workforce member to ePHI information is Procedure determine that staff ‘s appropriate access to electronic PHI September 5, 2003 Revised December 10, 2003 Page 3 of 13 -- D R A F T -- Security Assessment/ Risk Analysis Tool VACSB HIPAA Steering Committee SEC- SECURITY Questions Supplemental Information Policies Needed TION STANDARD is appropriate?
Termination Are adequate policies and Retrieval of keys, badges, other access Procedures for terminating access to ePHI when Procedures (A) procedures in place and instruments the employment of a workforce member ends or as required by determinations made implemented, to Immediate disabling of electronic accounts terminated access to PHI without removing user files as staff exit employment? Immediate change to coded lock access entry doors Termination of electronic badge permissions Policy for involvement of MIS staff prior to taking action in adverse termination procedure to mitigate potential damage to information or systems via retaliation Policy for immediate notification from HR to MIS staff in all terminations 164.30 Information 8(a)(4) Access Management Isolating Health If there is a relationship Written policies/procedures Care with a Heath Care Make policies/procedures part of or an addendum Clearinghouse Clearinghouse, are to contractual agreement Function (R) policies and procedures implemented that protect Assure Business Associate Agreement in place the PHI from unauthorized access? Access Are policies and Set standard templates based on job duties or P&P to grant access to electronic PHI (through Authorization procedures implemented position type for access access to a workstation, transaction, program, process, or other mechanism) (A) for granting access to Document deviations with security officer electronic PHI? approval for deviations from standard access templates Document access rules for client information that is not on the person’s caseload, in the person’s September 5, 2003 Revised December 10, 2003 Page 4 of 13 -- D R A F T -- Security Assessment/ Risk Analysis Tool VACSB HIPAA Steering Committee SEC- SECURITY Questions Supplemental Information Policies Needed TION STANDARD unit, etc. Requirements for no PHI on workstation (all PHI to be saved on central servers on network with physical security measure implemented) For non-networked equipment, assure physical security requirements are in place to limit access to equipment for non-authorized persons Policies on storing removable media (i.e., diskettes, CD’s, zip disks, memory sticks, etc.) Laptop security – encrypted databases, security system for boot, etc. Ethics document, access not required for job duties is not permitted Document and test interconnected systems for ability to share information only as defined Process of auto lockout by the application for too many incorrect password attempts Background checks for staff, especially sensitive positions like MIS, database administrators, etc. Disabling of “guest” or temporary access accounts Policy against shared user accounts Access Have policies and MIS staff particularly identify who has access to P&P to establish, document, review, and modify a Establishment procedures been what systems, files, programs, etc. user’s right of access to a workstation, transaction, program or process and implemented that Review MIS staff access to assure one person Modification establish, document, does not have access to all methods available to (A) review and modify each destroy electronic information (ex., separation of user’s right of access to a duties of system administrator from person workstation, transaction, responsible for and who has physical custody of program or process? backups) Access levels reviewed, audited, modified, and documented on a periodic basis September 5, 2003 Revised December 10, 2003 Page 5 of 13 -- D R A F T -- Security Assessment/ Risk Analysis Tool VACSB HIPAA Steering Committee SEC- SECURITY Questions Supplemental Information Policies Needed TION STANDARD 164.30 Security 8(a)(5) Awareness and Training Security Do users routinely view How security updates are communicated to user Reminders (A) screens reminding them community (newsletters, E-mail, paper, signoff of their responsibilities to document, etc.) maintain the privacy of Privacy policy displayed on web site consumer information and the security of electronic data? Protection from What procedures are in Virus software Malicious place for guarding Virus software updates regularly (who is Software (A) against, detecting and responsible) reporting harmful software? Alert checks enabled by security officer or staff with security product vendor for immediate action upon identification of new threat? Backup processes in place and operational, tested periodically Firewall protection to trusted network Regular updates to firewall protection Procedures for isolation of and mitigation of harmful element if found Procedures for software upgrade, patch, installation to segregate live systems from test/development area Log-In What procedures are in Intrusion Detection Software P&P for monitoring login attempts and reporting discrepancies Monitoring (A) place for monitoring Access log reviews login attempts and reporting discrepancies? Remove or turn off modems (policy issue)
Password Are users required to Require periodic password changes, no longer P&P for creating, changing and safeguarding Management change their network and than 90 days apart passwords (A) system passwords September 5, 2003 Revised December 10, 2003 Page 6 of 13 -- D R A F T -- Security Assessment/ Risk Analysis Tool VACSB HIPAA Steering Committee SEC- SECURITY Questions Supplemental Information Policies Needed TION STANDARD periodically? Do the Password parameters built into password function parameters of the Password policy (no names, user ID’s, phone passwords meet industry numbers, etc. as passwords) standards? Password content (number of characters, numbers, length, etc.) 164.30 Security P&P to address security incidents – see response 8(a)(6) Incid and reporting parameters ent Proc edur e Response and How are suspected or Security Incident procedure Reporting (R) known security incidents Security Incident response team defined with identified and addressed? contact list for after hours contact as necessary Are security incidents Determination of whether law enforcement should and their outcomes be involved documented? Policy for workforce and MIS staff on requirements for reporting suspected security incidents or breaches What are mitigation strategies? Training of staff to recognize a security incident 164.30 Contingency P&P for responding to an emergency or other 8(a)(7) Plan occurrence (ex: fire, vandalism, system failure, and natural disaster) that damages systems containing ePHI
Data Backup Are procedures in place Print image files Procedures for creating and maintaining retrievable exact copies of your ePHI Plan (R) to create and maintain Backups retrievable extract copies of electronic PHI? Definition of critical infrastructure requirements Adequate system, technical, and user documentation Disaster Are procedures in place Backups and frequency, responsible party Procedures to restore any loss of data September 5, 2003 Revised December 10, 2003 Page 7 of 13 -- D R A F T -- Security Assessment/ Risk Analysis Tool VACSB HIPAA Steering Committee SEC- SECURITY Questions Supplemental Information Policies Needed TION STANDARD Recovery Plan to recover any loss of Backup logs utilized with labeled media (R) data? identifiers, date, person performing backup, whether successful, and content and type of backup (incremental vs. full, only certain directories, bootable, etc.) Offsite backups and rotation frequency Emergency Are procedures in place Contingency plan for operations without Procedures to enable continuation of critical Mode to enable continuation of electronic system availability business processes for protection of the security of Operation Plan critical business ePHI while operating in emergency mode (R) processes for protection of electronic PHI while operating in emergency mode? Testing and Are procedures in place Test contingency plan Procedures for periodic testing and revision of contingency plan Revision to periodically test and Test backup/restore functions Procedure (A) revise contingency plans? Applications Which applications and and Data what data are critical to Criticality supporting the Analysis (A) contingency plans? 164.30 Evaluation Have contingency plans Document testing activities, frequency, and 8(a)(8) been tested? outcome How often will they be Change procedures, retest if problems found, tested in the future? document 164.30 Business 8(b)(1) Associate Contracts and Other Written Are there BA Maintain list and file of documents Contract or Agreements established Identify responsible party for keeping information Other with all relevant up to date Arrangement contractors? (R) Institute review process for all contractors on a periodic basis (annual?) September 5, 2003 Revised December 10, 2003 Page 8 of 13 -- D R A F T -- Security Assessment/ Risk Analysis Tool VACSB HIPAA Steering Committee SEC- SECURITY Questions Supplemental Information Policies Needed TION STANDARD 164.31 Facility Access P&P to limit physical access to its electronic 0(a)(1) Co information systems and the facility or facilities in ntr which they are housed, while ensuring that ols properly authorized access is allowed
Contingency Are procedures in place Who, what, when, how Procedures that allow facility access in support of restoration of lost data under the disaster recovery plan Operations (A) that allow facility access Replacement equipment procurement process in support of restoration and emergency mode operations plan in the even of an of lost data under the emergency disaster recovery plan and emergency mode operations plan in the event of an emergency? Facility Is the information Locked access to sensitive areas (systems, phone P&P to safeguard the facility and the equipment Security Plan systems equipment closets, patch panels, etc.) therein from unauthorized physical access, tampering, and theft (A) protected from Documentation of who has access to sensitive unauthorized physical areas access, tampering and theft? Documentation of access (in/out) of staff to sensitive areas Access Control Are procedures in place Use of identification badges and policy for Procedures to control and validate a person’s access to and Validation to control and validate a wearing/displaying them facilities based on their role or function, including Procedures (A) person’s access to visitor control, and control of access to software Culture supportive of stopping unknown persons programs for testing and revision facilities based on their to inquire on purpose for being in restricted area role or function? Sign in sheets for entry by visitors Do the procedures include visitor control Escorts for visitors and control of access to Access control by vendors software programs for System change control policies/procedures by testing and revision? internal staff and vendors Maintenance Is there documentation of Maintenance records log P&P to document repairs and modifications to the Records (A) repairs and modifications physical components of a facility which are Electronic equipment maintenance logs (including related to security (ex: hardware, locks, doors, to the physical person and company name making repair) components of a facility, walls)
September 5, 2003 Revised December 10, 2003 Page 9 of 13 -- D R A F T -- Security Assessment/ Risk Analysis Tool VACSB HIPAA Steering Committee SEC- SECURITY Questions Supplemental Information Policies Needed TION STANDARD which are related to security? (E.g., hardware, walls, doors and locks.) 164.31 Workstation Do policies and Policies on prohibiting installation of software on P&P that specify the proper functions to be performed, 0(b) Use procedures adequately workstations by end users the manner in which those functions are to be (R) specify the proper performed, and the physical attributes of the Prohibition on use/installation of personal surroundings of a specific workstation or class of functions to be software on organizational assets performed, the manner in workstation that can access ePHI which those functions are Prohibition on disabling anti-virus or other to be performed, and the security software on the workstation physical attributes of the Policies on user responsibility for maintaining surroundings of confidentiality of passwords workstations that can Policies on user responsibility for security access PHI? breaches occurring under their password access Policies on unattended logged-on workstations Policies on location of workstations and visibility by unauthorized persons (e.g., public)
164.31 Workstation Are physical safeguards Screen savers 0(c) Security (R) in place to restrict access External device limitations (disk drives, etc.) to authorized users? Physical access limitations (locked offices, etc.) 164.31 Device and P&P that govern the receipt and removal of hardware 0(d)(1) Medi and electronic media that contain ePHI into and out of a a facility, and the movement of these items within the Cont facility rols Disposal (R) Are policies and Device inventory P&P for disposing of hardware and electronic media containing ePHI procedures in place to Disposition policy for disk drives address the final disposition of electronic Policies for PHI on hand-held devices and laptops PHI, and/or the hardware Policies for PHI on removable media, whether it or electronic media on can be taken off premises, how to destroy, etc. September 5, 2003 Revised December 10, 2003 Page 10 of 13 -- D R A F T -- Security Assessment/ Risk Analysis Tool VACSB HIPAA Steering Committee SEC- SECURITY Questions Supplemental Information Policies Needed TION STANDARD which it is stored? Policies with hardware vendors on destruction of data on media when replaced Media Re-use Are procedures in place Procedures for removal of ePHI from electronic (R) for the removal of PHI medial before the media are made available for re- from electronic media use before they are made available for re-use? Accountability Is a record maintained of Inventory change list (A) the movements of Storage media library, check in, check out hardware and electronic media? Offsite backup transport policies, how protected from unauthorized access (locked/sealed bag, etc.) Data Back-up Is a retrievable, exact Policy on support requirements and Storage (A) copy of electronic PHI created, prior to movement of equipment? 164.31 Access Control Technical P&P for electronic information systems that 2(a)(1) maintain ePHI to allow access only to those persons or software programs that have been granted access rights in our information access P&P
Unique User Is each user assigned a Unique user ID Identification unique name and/or Prohibit reuse of user IDs (R) number for identification and tracking? Emergency Are procedures in place Documentation of access Procedures for obtaining necessary ePHI during an emergency Access for obtaining necessary “Break the glass” procedures Procedure (R) electronic PHI during an emergency? Automatic Log- Are there procedures in Passworded screen savers, etc. off (A) place that terminate an electronic session after a predetermined time of inactivity? September 5, 2003 Revised December 10, 2003 Page 11 of 13 -- D R A F T -- Security Assessment/ Risk Analysis Tool VACSB HIPAA Steering Committee SEC- SECURITY Questions Supplemental Information Policies Needed TION STANDARD Encryption and Are there mechanisms to Policies on what information must be encrypted Decryption (A) encrypt and decrypt and for what purpose electronic PHI? E-mail encryption/internet communications encryption 164.31 Audit Controls Are mechanisms 2(b) (R) (hardware, software and/or procedural) in place that record and examine activity in information systems that contain or use PHI? 164.31 Integrity P&P to protect ePHI from improper alteration or 2(c)(1) destruction
Mechanism to Are electronic Change management processes in applications Authenticate mechanisms in place to Audit trail of data changes (who, what, from what Electronic corroborate that value to what value) Protected electronic PHI has not Health been altered or destroyed Information (A) in an unauthorized manner? 164.31 Person or Are procedures in place Process for verification of identity for phone calls Procedures to verify that a person or entity seeking 2(d) Entity to verify that a person or or visits access to ePHI is the one claimed Authentication entity seeking access to Standard letter to send back including (R) electronic PHI is the one authorization form claimed? Passwords, keycards, biometric, or other authentication methods 164.31 Transmission 2(e)(1) Secu rity Integrity Are there security Message authentication Controls (A) measures to ensure that electronically transmitted September 5, 2003 Revised December 10, 2003 Page 12 of 13 -- D R A F T -- Security Assessment/ Risk Analysis Tool VACSB HIPAA Steering Committee SEC- SECURITY Questions Supplemental Information Policies Needed TION STANDARD PHI is not improperly modified without detection until disposed of? Encryption (A) Is a mechanism in place to encrypt electronic PHI whenever deemed appropriate? Organizational Requirements Business P&P to establish and manage contracts with your Associate Business Associates in accordance with the Agreements requirements of the Privacy and Security Regulations (required)
Requirements for Group Health Plans Documentatio n Time Limit P&P specifying that all documents required by Privacy (required) and Security Regulations are retained for at least 6 years from the date of its creation or the date when it was last in effect, whichever is later
Availability (required) Updates (required)
September 5, 2003 Revised December 10, 2003 Page 13 of 13