MIS 4600/MBA 5880 TCP/IP Concepts January 19, 2010
Review Exercise: Exploits based on knowledge of TCP segments’ structure
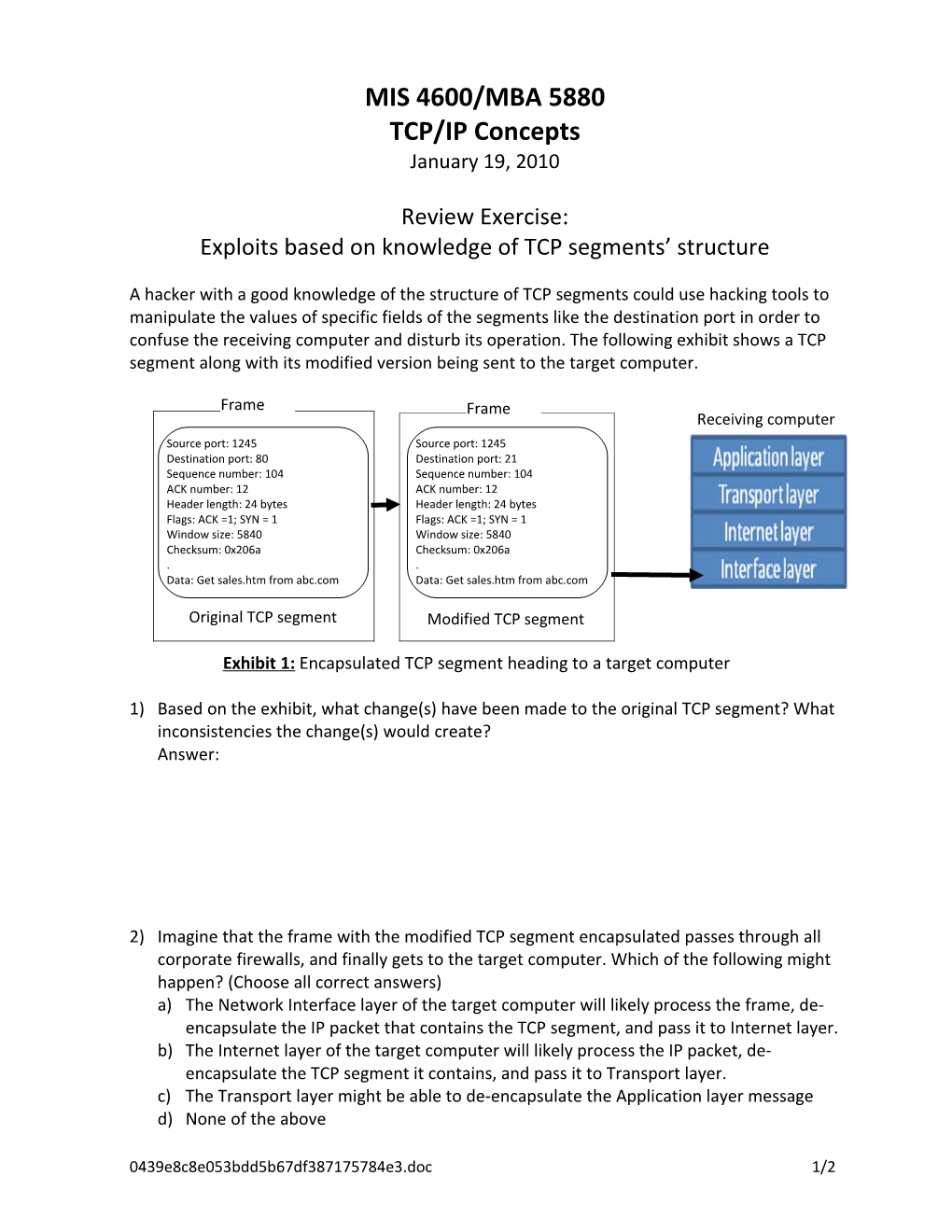
A hacker with a good knowledge of the structure of TCP segments could use hacking tools to manipulate the values of specific fields of the segments like the destination port in order to confuse the receiving computer and disturb its operation. The following exhibit shows a TCP segment along with its modified version being sent to the target computer.
Frame Frame Receiving computer Source port: 1245 Source port: 1245 Destination port: 80 Destination port: 21 Sequence number: 104 Sequence number: 104 ACK number: 12 ACK number: 12 Header length: 24 bytes Header length: 24 bytes Flags: ACK =1; SYN = 1 Flags: ACK =1; SYN = 1 Window size: 5840 Window size: 5840 Checksum: 0x206a Checksum: 0x206a . . Data: Get sales.htm from abc.com Data: Get sales.htm from abc.com
Original TCP segment Modified TCP segment
Exhibit 1: Encapsulated TCP segment heading to a target computer
1) Based on the exhibit, what change(s) have been made to the original TCP segment? What inconsistencies the change(s) would create? Answer:
2) Imagine that the frame with the modified TCP segment encapsulated passes through all corporate firewalls, and finally gets to the target computer. Which of the following might happen? (Choose all correct answers) a) The Network Interface layer of the target computer will likely process the frame, de- encapsulate the IP packet that contains the TCP segment, and pass it to Internet layer. b) The Internet layer of the target computer will likely process the IP packet, de- encapsulate the TCP segment it contains, and pass it to Transport layer. c) The Transport layer might be able to de-encapsulate the Application layer message d) None of the above
0439e8c8e053bdd5b67df387175784e3.doc 1/2 3) Which of the following might happen at the Transport and Application layers? a) After reading the Destination port number, the Transport layer might realize that there is no service running on port 21 to pass the request to. b) The Transport layer might hang c) The Transport layer might discard the TCP segment d) The Transport layer might initiate the process of closing the connection with the sending computer.
4) If the receiving computer initiates the process of closing the connection with the sending computer, which of the following TCP flags is more likely to be used (i.e. set) to end the conversation? a) SYN b) FIN c) RST
Note There are different packet crafting tools that are used by hackers and security testers to manipulate TCP/IP messages or launch probe attacks based on their knowledge of TCP/IP messages’ structure. Here are some of them that could be downloaded for free.
Hping2 (www.hping.org) - A command-line oriented TCP/IP packet assembler/analyzer that works on *nix, Solaris, MacOs X, and Windows. - Can be used to assemble and send custom ICMP, UDP, or TCP packets and then displays any replies. - Inspired by the ping command, but offers more control over the probes sent. - Has a handy traceroute mode and supports IP fragmentation. - Very useful when trying to traceroute/ping/probe hosts behind a firewall that blocks attempts using the standard utilities. This often allows you to map out firewall rulesets. - Great for learning more about TCP/IP and experimenting with IP protocols.
Scapy (www.secdev.org/projects/scapy) - Works on *nix, Solaris, MacOs X, and Windows. - Has the following functions: interactive packet manipulation, packet generation, network scanning, network discovery, and packet sniffing. - Provides classes to interactively create packets or sets of packets, manipulate them, send them over the wire, sniff other packets from the wire, match answers and replies, and more. - Interaction is provided by the Python interpreter, so Python programming structures can be used (such as variables, loops, and functions). Report modules are possible and easy to make.
0439e8c8e053bdd5b67df387175784e3.doc 2/2