Optimization Possibilities
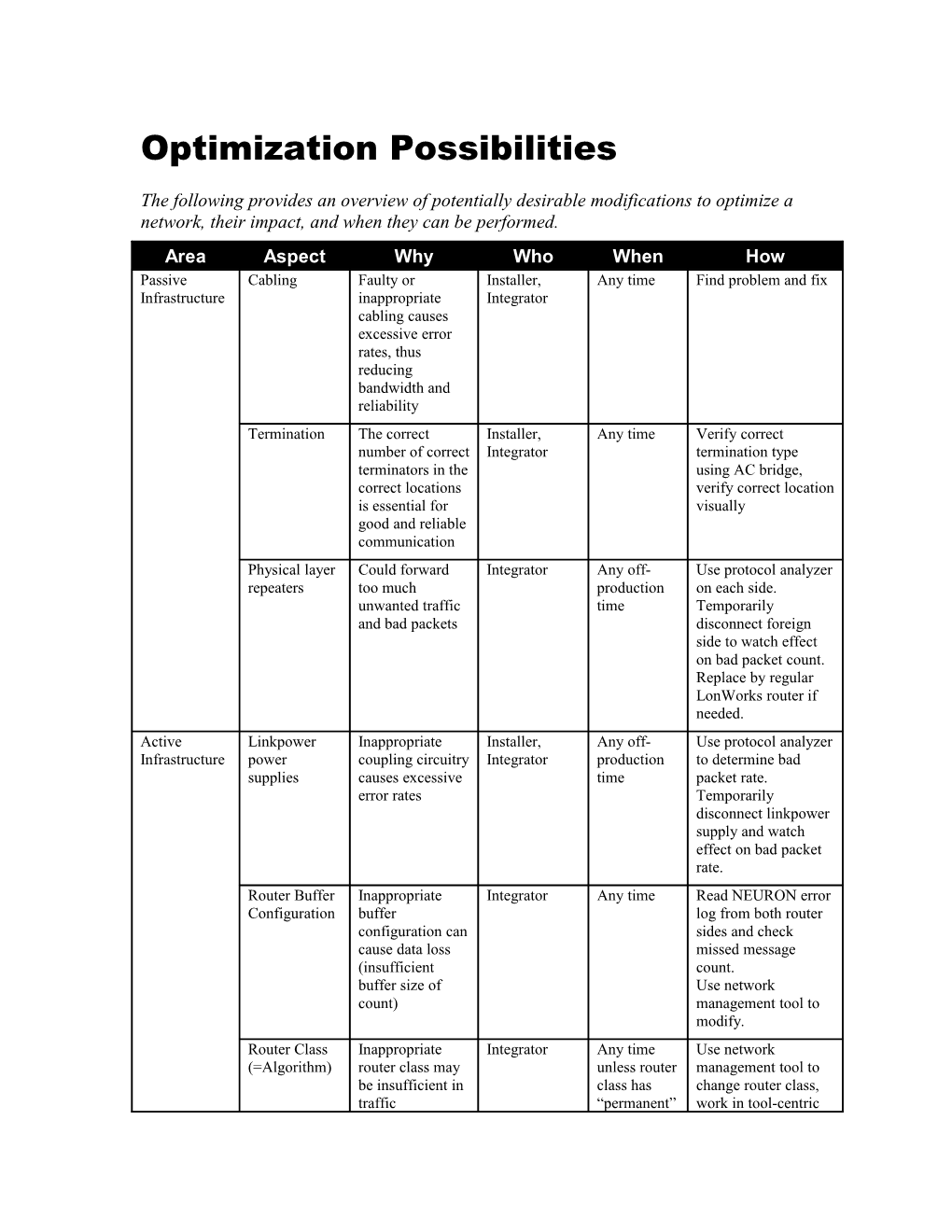
The following provides an overview of potentially desirable modifications to optimize a network, their impact, and when they can be performed. Area Aspect Why Who When How Passive Cabling Faulty or Installer, Any time Find problem and fix Infrastructure inappropriate Integrator cabling causes excessive error rates, thus reducing bandwidth and reliability Termination The correct Installer, Any time Verify correct number of correct Integrator termination type terminators in the using AC bridge, correct locations verify correct location is essential for visually good and reliable communication Physical layer Could forward Integrator Any off- Use protocol analyzer repeaters too much production on each side. unwanted traffic time Temporarily and bad packets disconnect foreign side to watch effect on bad packet count. Replace by regular LonWorks router if needed. Active Linkpower Inappropriate Installer, Any off- Use protocol analyzer Infrastructure power coupling circuitry Integrator production to determine bad supplies causes excessive time packet rate. error rates Temporarily disconnect linkpower supply and watch effect on bad packet rate. Router Buffer Inappropriate Integrator Any time Read NEURON error Configuration buffer log from both router configuration can sides and check cause data loss missed message (insufficient count. buffer size of Use network count) management tool to modify. Router Class Inappropriate Integrator Any time Use network (=Algorithm) router class may unless router management tool to be insufficient in class has change router class, traffic “permanent” work in tool-centric segmentation attribute order starting at the (repeater, tool location. bridge), or malfunctioning under certain topology conditions (learning) Area Aspect Why Who When How Application Processing Faster processing Device Hardware Hardware redesign Devices Power allows for more manufacturer design time network transactions to be processed Buffer Inappropriate Device Application Changes to some configuration buffer manufacturer compile time compiler directives in configuration can source code cause data loss (insufficient size or count) or waste of resources (buffers too large) Set and type SNVT type Device Application For a static interface, of network mismatch might manufacturer, compile time changes to the variables prevent from Integrator (static NEURON C source efficient bindings interfaces), code are required. (translator installation Changes to dynamic objects required) time (any interfaces can be type of done at install-time dynamic using an appropriate interface) network management tool, provided the device manufacturer did implement support for install- time SNVT typing or dynamic netowork variables within the device Transceiver Faster transceiver Device Device Hardware re-design Type would provide manufacturer hardware and application re- more bandwidth design and build application compile time Alias support Aliases allow for Device Application Minimum software and number of connections manufacturer compile time changes to NEURON available which would C code plus 4 byte aliases otherwise be EEPROM space per impossible alias. More complex changes for hosted devices required. Area Aspect Why Who When How Network Connection Properties must Integrator Any time See separate Variable and transport match but not document for Connections properties exceed guidance requirements Configuration Heartbeart, Properties must Integrator Any time See separate Properties Throttle, match but not document for Filters exceed guidance requirements on both sender and receiver side
Authentication Authentication is a special form of an acknowledged service between one writer node and from 1 to 63 reader nodes. Authentication is used by the reader nodes to verify the identity of the writer node. This type of service is useful, for example, if a node containing an electronic lock receives a message to open the lock. By using authentication, the electronic lock node can verify that the open message comes from the owner, not from someone attempting to break into the system. Authentication doubles the number of messages per transaction. Authentication may be used with acknowledged updates or network variable polls. It may not be used with unacknowledged or repeated updates. An acknowledged message normally requires two messages, an update and an acknowledgment.
Priority The priority feature is designed to guarantee priority delivery of a message even on a saturated channel. Note that there should be only one device for a given priority slot, otherwise the priority messages will necessarily collide. Note that priority slots should only be provided if you will use priority transport, since each priority slot allocates network bandwidth which could otherwise be used for regular traffic.