An Empirical Study on the Intrinsic Privacy of Stochastic Gradient Descent Stephanie L
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Complexity Theory and Its Applications in Linear Quantum
Louisiana State University LSU Digital Commons LSU Doctoral Dissertations Graduate School 2016 Complexity Theory and its Applications in Linear Quantum Optics Jonathan Olson Louisiana State University and Agricultural and Mechanical College, [email protected] Follow this and additional works at: https://digitalcommons.lsu.edu/gradschool_dissertations Part of the Physical Sciences and Mathematics Commons Recommended Citation Olson, Jonathan, "Complexity Theory and its Applications in Linear Quantum Optics" (2016). LSU Doctoral Dissertations. 2302. https://digitalcommons.lsu.edu/gradschool_dissertations/2302 This Dissertation is brought to you for free and open access by the Graduate School at LSU Digital Commons. It has been accepted for inclusion in LSU Doctoral Dissertations by an authorized graduate school editor of LSU Digital Commons. For more information, please [email protected]. COMPLEXITY THEORY AND ITS APPLICATIONS IN LINEAR QUANTUM OPTICS A Dissertation Submitted to the Graduate Faculty of the Louisiana State University and Agricultural and Mechanical College in partial fulfillment of the requirements for the degree of Doctor of Philosophy in The Department of Physics and Astronomy by Jonathan P. Olson M.S., University of Idaho, 2012 August 2016 Acknowledgments My advisor, Jonathan Dowling, is apt to say, \those who take my take my advice do well, and those who don't do less well." I always took his advice (sometimes even against my own judgement) and I find myself doing well. He talked me out of a high-paying, boring career, and for that I owe him a debt I will never be able to adequately repay. My mentor, Mark Wilde, inspired me to work hard without saying a word about what I \should" be doing, and instead leading by example. -

Haystack Hunting Hints and Locker Room Communication∗
Haystack Hunting Hints and Locker Room Communication∗ Artur Czumaj † George Kontogeorgiou ‡ Mike Paterson § Abstract We want to efficiently find a specific object in a large unstructured set, which we model by a random n-permutation, and we have to do it by revealing just a single element. Clearly, without any help this task is hopeless and the best one can do is to select the element at random, and 1 achieve the success probability n . Can we do better with some small amount of advice about the permutation, even without knowing the object sought? We show that by providing advice of just one integer in 0; 1; : : : ; n 1 , one can improve the success probability considerably, by log n f − g a Θ( log log n ) factor. We study this and related problems, and show asymptotically matching upper and lower bounds for their optimal probability of success. Our analysis relies on a close relationship of such problems to some intrinsic properties of random permutations related to the rencontres number. 1 Introduction Understanding basic properties of random permutations is an important concern in modern data science. For example, a preliminary step in the analysis of a very large data set presented in an unstructured way is often to model it assuming the data is presented in a random order. Un- derstanding properties of random permutations would guide the processing of this data and its analysis. In this paper, we consider a very natural problem in this setting. You are given a set of 1 n objects ([n 1], say ) stored in locations x ; : : : ; x − according to a random permutation σ of − 0 n 1 [n 1]. -
Discrete Uniform Distribution
Discrete uniform distribution In probability theory and statistics, the discrete uniform distribution is a symmetric probability discrete uniform distribution wherein a finite number of values are Probability mass function equally likely to be observed; every one of n values has equal probability 1/n. Another way of saying "discrete uniform distribution" would be "a known, finite number of outcomes equally likely to happen". A simple example of the discrete uniform distribution is throwing a fair die. The possible values are 1, 2, 3, 4, 5, 6, and each time the die is thrown the probability of a given score is 1/6. If two dice are thrown and their values added, the resulting distribution is no longer uniform because not all sums have equal probability. Although it is convenient to describe discrete uniform distributions over integers, such as this, one can also consider n = 5 where n = b − a + 1 discrete uniform distributions over any finite set. For Cumulative distribution function instance, a random permutation is a permutation generated uniformly from the permutations of a given length, and a uniform spanning tree is a spanning tree generated uniformly from the spanning trees of a given graph. The discrete uniform distribution itself is inherently non-parametric. It is convenient, however, to represent its values generally by all integers in an interval [a,b], so that a and b become the main parameters of the distribution (often one simply considers the interval [1,n] with the single parameter n). With these conventions, the cumulative distribution function (CDF) of the discrete uniform distribution can be expressed, for any k ∈ [a,b], as Notation or Parameters integers with Support pmf Contents CDF Estimation of maximum Random permutation Mean Properties Median See also References Mode N/A Estimation of maximum Variance This example is described by saying that a sample of Skewness k observations is obtained from a uniform Ex. -

Official Journal of the Bernoulli Society for Mathematical Statistics And
Official Journal of the Bernoulli Society for Mathematical Statistics and Probability Volume Twenty Five Number Two May 2019 ISSN: 1350-7265 CONTENTS MAMMEN, E., VAN KEILEGOM, I. and YU, K. 793 Expansion for moments of regression quantiles with applications to nonparametric testing GRACZYK, P. and MAŁECKI, J. 828 On squared Bessel particle systems EVANS, R.J. and RICHARDSON, T.S. 848 Smooth, identifiable supermodels of discrete DAG models with latent variables CHAE, M. and WALKER, S.G. 877 Bayesian consistency for a nonparametric stationary Markov model BELOMESTNY, D., PANOV, V. and WOERNER, J.H.C. 902 Low-frequency estimation of continuous-time moving average Lévy processes ZEMEL, Y. and PANARETOS, V.M. 932 Fréchet means and Procrustes analysis in Wasserstein space CASTRO, R.M. and TÁNCZOS, E. 977 Are there needles in a moving haystack? Adaptive sensing for detection of dynamically evolving signals DAHLHAUS, R., RICHTER, S and WU, W.B. 1013 Towards a general theory for nonlinear locally stationary processes CHEN, X., CHEN, Z.-Q., TRAN, K. and YIN, G. 1045 Properties of switching jump diffusions: Maximum principles and Harnack inequalities BARBOUR, A.D., RÖLLIN, A. and ROSS, N. 1076 Error bounds in local limit theorems using Stein’s method BECHERER, D., BILAREV, T. and FRENTRUP, P. 1105 Stability for gains from large investors’ strategies in M1/J1 topologies OATES, C.J., COCKAYNE, J., BRIOL, F.-X. and GIROLAMI, M. 1141 Convergence rates for a class of estimators based on Stein’s method IRUROZKI, E., CALVO, B. and LOZANO, J.A. 1160 Mallows and generalized Mallows model for matchings LEE, J.H. -
Kernels of Mallows Models Under the Hamming Distance for Solving the Quadratic Assignment Problem
Kernels of Mallows Models under the Hamming Distance for solving the Quadratic Assignment Problem Etor Arzaa, Aritz Péreza, Ekhiñe Irurozkia, Josu Ceberiob aBCAM - Basque Center for Applied Mathematics, Spain bUniversity of the Basque Country UPV/EHU, Spain Abstract The Quadratic Assignment Problem (QAP) is a well-known permutation-based combinatorial opti- mization problem with real applications in industrial and logistics environments. Motivated by the challenge that this NP-hard problem represents, it has captured the attention of the optimization community for decades. As a result, a large number of algorithms have been proposed to tackle this problem. Among these, exact methods are only able to solve instances of size n < 40. To overcome this limitation, many metaheuristic methods have been applied to the QAP. In this work, we follow this direction by approaching the QAP through Estimation of Distribution Algorithms (EDAs). Particularly, a non-parametric distance-based exponential probabilistic model is used. Based on the analysis of the characteristics of the QAP, and previous work in the area, we introduce Kernels of Mallows Model under the Hamming distance to the context of EDAs. Conducted experiments point out that the performance of the proposed algorithm in the QAP is superior to (i) the classical EDAs adapted to deal with the QAP, and also (ii) to the specific EDAs proposed in the literature to deal with permutation problems. 1. Introduction The Quadratic Assignment Problem (QAP) [41] is a well-known combinatorial optimization prob- lem. Along with other problems, such as the traveling salesman problem, the linear ordering problem and the flowshop scheduling problem, it belongs to the family of permutation-based (a permutation is a bijection of the set f1; :::; ng onto itself) problems [15]. -

Permanental Partition Models and Markovian Gibbs Structures
PERMANENTAL PARTITION MODELS AND MARKOVIAN GIBBS STRUCTURES HARRY CRANE Abstract. We study both time-invariant and time-varying Gibbs distributions for configura- tions of particles into disjoint clusters. Specifically, we introduce and give some fundamental properties for a class of partition models, called permanental partition models, whose distribu- tions are expressed in terms of the α-permanent of a similarity matrix parameter. We show that, in the time-invariant case, the permanental partition model is a refinement of the cele- brated Pitman-Ewens distribution; whereas, in the time-varying case, the permanental model refines the Ewens cut-and-paste Markov chains [J. Appl. Probab. (2011), 3:778–791]. By a special property of the α-permanent, the partition function can be computed exactly, allowing us to make several precise statements about this general model, including a characterization of exchangeable and consistent permanental models. 1. Introduction Consider a collection of n distinct particles (labeled i = 1;:::; n) located at distinct positions x1;:::; xn in some space . Each particle i = 1;:::; n occupies an internal state yi, which may change over time. Jointly,X the state of the system at time t 0 depends on the ≥ positions of the particles x1;:::; xn and the interactions among these particles. We assume that, with the exception of their positions in , particles have identical physical properties X and, thus, the pairwise interaction between particles at positions x and x0 is determined only by the pair (x; x0). In this setting, we model pairwise interactions by a symmetric function K : [0; 1] with unit diagonal, K(x; x) = 1 for all x , where K(x; x ) X × X ! 2 X 0 quantifies the interaction between particles at locations x and x0. -
Cost Efficient Frequency Hopping Radar Waveform for Range And
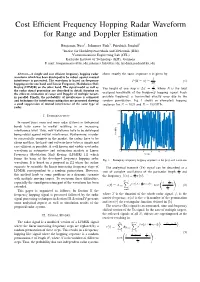
Cost Efficient Frequency Hopping Radar Waveform for Range and Doppler Estimation Benjamin Nuss1, Johannes Fink2, Friedrich Jondral2 1Institut fur¨ Hochfrequenztechnik und Elektronik (IHE) 2Communications Engineering Lab (CEL) Karlsruhe Institute of Technology (KIT), Germany E-mail: [email protected], johannes.fi[email protected], [email protected] Abstract—A simple and cost efficient frequency hopping radar chose exactly the same sequence π is given by waveform which has been developed to be robust against mutual 1 interference is presented. The waveform is based on frequency P (Π = π) = . (1) hopping on the one hand and Linear Frequency Modulation Shift N! Keying (LFMSK) on the other hand. The signal model as well as The height of one step is ∆f = B , where B is the total the radar signal processing are described in detail, focusing on N the efficient estimation of range and Doppler of multiple targets occupied bandwidth of the frequency hopping signal. Each in parallel. Finally, the probability of interference is estimated possible frequency is transmitted exactly once due to the and techniques for interference mitigation are presented showing random permutation. Fig. 1 shows an exemplary hopping a good suppression of mutual interference of the same type of sequence for N = 1024 and B = 150 MHz. radar. 150 I. INTRODUCTION In recent years more and more radar systems in unlicensed 100 bands have come to market resulting in an increasing interference level. Thus, new waveforms have to be developed being robust against mutual interference. Furthermore, in order f in MHz 50 to successfully compete in the market, the radars have to be cheap and thus, the hard- and software have to be as simple and cost efficient as possible. -

Table of Contents
A Comprehensive Course in Geometry Table of Contents Chapter 1 - Introduction to Geometry Chapter 2 - History of Geometry Chapter 3 - Compass and Straightedge Constructions Chapter 4 - Projective Geometry and Geometric Topology Chapter 5 - Affine Geometry and Analytic Geometry Chapter 6 - Conformal Geometry Chapter 7 - Contact Geometry and Descriptive Geometry Chapter 8 - Differential Geometry and Distance Geometry Chapter 9 - Elliptic Geometry and Euclidean Geometry Chapter 10 WT- Finite Geometry and Hyperbolic Geometry _____________________ WORLD TECHNOLOGIES _____________________ A Course in Boolean Algebra Table of Contents Chapter 1 - Introduction to Boolean Algebra Chapter 2 - Boolean Algebras Formally Defined Chapter 3 - Negation and Minimal Negation Operator Chapter 4 - Sheffer Stroke and Zhegalkin Polynomial Chapter 5 - Interior Algebra and Two-Element Boolean Algebra Chapter 6 - Heyting Algebra and Boolean Prime Ideal Theorem Chapter 7 - Canonical Form (Boolean algebra) Chapter 8 -WT Boolean Algebra (Logic) and Boolean Algebra (Structure) _____________________ WORLD TECHNOLOGIES _____________________ A Course in Riemannian Geometry Table of Contents Chapter 1 - Introduction to Riemannian Geometry Chapter 2 - Riemannian Manifold and Levi-Civita Connection Chapter 3 - Geodesic and Symmetric Space Chapter 4 - Curvature of Riemannian Manifolds and Isometry Chapter 5 - Laplace–Beltrami Operator Chapter 6 - Gauss's Lemma Chapter 7 - Types of Curvature in Riemannian Geometry Chapter 8 - Gauss–Codazzi Equations Chapter 9 -WT Formulas -

Enumerative Combinatorics: Class Notes
Enumerative Combinatorics: class notes Darij Grinberg May 4, 2021 (unfinished!) Status: Chapters 1 and 2 finished; Chapter 3 outlined. Contents 1. Introduction7 1.1. Domino tilings . .8 1.1.1. The problem . .8 1.1.2. The odd-by-odd case and the sum rule . 12 1.1.3. The symmetry and the bijection rule . 14 1.1.4. The m = 1 case . 18 1.1.5. The m = 2 case and Fibonacci numbers . 19 1.1.6. Kasteleyn’s formula (teaser) . 26 1.1.7. Axisymmetric domino tilings . 28 1.1.8. Tiling rectangles with k-bricks . 31 1.2. Sums of powers . 38 1.2.1. The sum 1 + 2 + ... + n ....................... 38 1.2.2. What is a sum, actually? . 42 1.2.3. Rules for sums . 48 1.2.4. While at that, what is a finite product? . 53 1.2.5. The sums 1k + 2k + ... + nk .................... 54 1.3. Factorials and binomial coefficients . 58 1.3.1. Factorials . 58 1.3.2. Definition of binomial coefficients . 59 1.3.3. Fundamental properties of the binomial coefficients . 61 1.3.4. Binomial coefficients count subsets . 69 1.3.5. Integrality and some arithmetic properties . 74 1.3.6. The binomial formula . 78 1.3.7. Other properties of binomial coefficients . 86 1.4. Counting subsets . 93 1.4.1. All subsets . 93 1 Enumerative Combinatorics: class notes page 2 1.4.2. Lacunar subsets: the basics . 94 1.4.3. Intermezzo: SageMath . 97 1.4.4. Counting lacunar subsets . 102 1.4.5. Counting k-element lacunar subsets . -

Mallows and Generalized Mallows Model for Matchings
Submitted to Bernoulli arXiv: arXiv:0000.0000 Mallows and Generalized Mallows Model for Matchings EKHINE IRUROZKI1,* BORJA CALVO1,** and JOSE A. LOZANO1,† 1University of the Basque Country E-mail: *[email protected]; **[email protected]; †[email protected] The Mallows and Generalized Mallows Models are two of the most popular probability models for distributions on permutations. In this paper we consider both models under the Hamming distance. This models can be seen as models for matchings instead of models for rankings. These models can not be factorized, which contrasts with the popular MM and GMM under Kendall’s-τ and Cayley distances. In order to overcome the computational issues that the models involve, we introduce a novel method for computing the partition function. By adapting this method we can compute the expectation, joint and conditional probabilities. All these methods are the basis for three sampling algorithms, which we propose and analyze. Moreover, we also propose a learning algorithm. All the algorithms are analyzed both theoretically and empirically, using synthetic and real data from the context of e-learning and Massive Open Online Courses (MOOC). Keywords: Mallows Model, Generalized Mallows Model, Hamming, Matching, Sampling, Learn- ing. 1. Introduction Permutations appear naturally in a wide variety of domains, from Social Sciences [47] to Machine Learning [8]. Probability models over permutations are an active research topic in areas such as preference elicitation [7], information retrieval [17], classification [9], etc. Some prominent examples of these are models based on pairwise preferences [33], Placket-Luce [34], [42], and Mallows Models [35]. One can find in the recent literature on distributions on permutations both theoretical discussions and practical applications, as well as extensions of all the aforementioned models. -

Some Algebraic Identities for the Alpha-Permanent
SOME ALGEBRAIC IDENTITIES FOR THE α-PERMANENT HARRY CRANE Abstract. We show that the permanent of a matrix is a linear combinationofdeterminants of block diagonal matrices which are simple functions of the original matrix. To prove this, we first show a moregeneral identity involving α-permanents: for arbitrary complex numbers α and β, we show that the α-permanent of any matrix can be expressed as a linear combination of β-permanents of related matrices. Some other identities for the α-permanent of sums and products of matrices are shown, as well as a relationship between the α-permanent and general immanants. We conclude with a discussion of the computational complexity of the α-permanent and provide some numerical illustrations. 1. Introduction The permanent of an n × n C-valued matrix M is defined by n (1) per M := Mj,σ(j), σX∈Sn Yj=1 where Sn denotes the symmetric group acting on [n] := {1,..., n}. Study of the perma- nent dates to Binet and Cauchy in the early 1800s [11]; and much of the early interest in permanents was in understanding how its resemblance of the determinant, n (2) det M := sgn(σ) Mj,σ(j), σX∈Sn Yj=1 where sgn(σ) istheparityof σ ∈ Sn, reconciled with some stark differences between the two. An early consideration, answered in the negative by Marcus and Minc [8], was whether there exists a linear transformation T such that per TM = det M for any matrix M. In his seminal paper on the #P-complete complexity class, Valiant remarked about the perplexing arXiv:1304.1772v1 [math.CO] 4 Apr 2013 relationship between the permanent and determinant, We do not know of any pair of functions, other than the permanent and determinant, for which the explicit algebraic expressions are so similar, and yet the computational complexities are apparently so different. -

A Generalization of the “Probl`Eme Des Rencontres”
1 2 Journal of Integer Sequences, Vol. 21 (2018), 3 Article 18.2.8 47 6 23 11 A Generalization of the “Probl`eme des Rencontres” Stefano Capparelli Dipartimento di Scienze di Base e Applicate per l’Ingegneria Universit´adi Roma “La Sapienza” Via A. Scarpa 16 00161 Roma Italy [email protected] Margherita Maria Ferrari Department of Mathematics and Statistics University of South Florida 4202 E. Fowler Avenue Tampa, FL 33620 USA [email protected] Emanuele Munarini and Norma Zagaglia Salvi1 Dipartimento di Matematica Politecnico di Milano Piazza Leonardo da Vinci 32 20133 Milano Italy [email protected] [email protected] Abstract In this paper, we study a generalization of the classical probl`eme des rencontres (problem of coincidences), where you are asked to enumerate all permutations π ∈ 1This work is partially supported by MIUR (Ministero dell’Istruzione, dell’Universit`ae della Ricerca). 1 S with k fixed points, and, in particular, to enumerate all permutations π S n ∈ n with no fixed points (derangements). Specifically, here we study this problem for the permutations of the n + m symbols 1, 2, ..., n, v , v , ..., v , where v 1 2 m i 6∈ 1, 2,...,n for every i = 1, 2,...,m. In this way, we obtain a generalization of the { } derangement numbers, the rencontres numbers and the rencontres polynomials. For these numbers and polynomials, we obtain the exponential generating series, some recurrences and representations, and several combinatorial identities. Moreover, we obtain the expectation and the variance of the number of fixed points in a random permutation of the considered kind.