DOS Commands, New Command-Line Tools, Command Shell Functionality, Configuring the Command Prompt, and Automating Commmand-Line Tasks, See Command-Line Reference
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

COMP11 Lab 1: What the Diff?
COMP11 Lab 1: What the Diff? In this lab you will learn how to write programs that will pass our grading software with flying colors. Navigate into your COMP11 directory and download the starter code for this lab with the following command: pull-code11 lab01 (and then to see what you've got) cd lab01 ls You Do Like We Do (15 mins) There is nothing magical about how we test and grade your programs. We run your program, give it a preselected input, and check to see if its output matches our expectation. This process is repeated until we're convinced that your solution is fully functional. In this lab we will walk you through that process so that you can test your programs in the same way. Surely you recall running our encrypt demo program in Lab 0. Run this program again and specify the word \tufts" as the word to encrypt (recall that you must first enter \use comp11" if you have not added this command to your .cshrc profile). Nothing new here. But what if you wanted to do that again? What if you wanted to do it 100 more times? Having to type \tufts" during every single execution would get old fast. It would be great if you could automate the process of entering that input. Well good news: you can. It's called \redirecting". The basic concept here is simple: instead of manually entering input, you can save that input into a separate file and tell your program to read that file as if the user were entering its contents. -

Tools for Managing Acls Jesper M Johansson
Security watch Tools for managing ACLs Jesper M Johansson Before I go into how to save or re- In Windows, access control lists (ACLs) store ACLs, let me first explore why it is so difficult. Let’s say you have a hier- give you extremely fine control over archy containing user data for students at a local college. You save the ACL on the ability of users and processes to 1 February. On 17 April you discover that somehow the ACL has been cor- use resources such as files and folders. rupted and you go to restore it from the saved copy. What complications Managing ACLs can be one of the more could there be with this operation? First, the new quarter started on complicated tasks related to protecting the 2 April. About 15 per cent of your students graduated; consequently, security of your users’ systems. Fortunately, their directories no longer exist. Thus, you have ACLs in the backup file that there are a number of useful utilities are invalid. You also have a batch of new students, another 15 per cent, that that help automate and simplify tasks granular permissions introduced with started with the new quarter. They surrounding permissions and ACLs. Windows 2000, making this an update have home directories now, but no Most readers are familiar with the that is about seven years overdue. ACLs in the backup file. What should venerable cacls.exe tool that has been Surprisingly, in spite of being dep- their ACLs be? Then of course you in every version of Windows NT since recated, cacls.exe does actually include have the 70 per cent that are still there, it first came out. -

Customizing and Extending Powerdesigner SAP Powerdesigner Documentation Collection Content
User Guide PUBLIC SAP PowerDesigner Document Version: 16.6.2 – 2017-01-05 Customizing and Extending PowerDesigner SAP PowerDesigner Documentation Collection Content 1 PowerDesigner Resource Files.................................................... 9 1.1 Opening Resource Files in the Editor.................................................10 1.2 Navigating and Searching in Resource Files............................................ 11 1.3 Editing Resource Files........................................................... 13 1.4 Saving Changes................................................................13 1.5 Sharing and Embedding Resource Files...............................................13 1.6 Creating and Copying Resource Files.................................................14 1.7 Specifying Directories to Search for Resource Files.......................................15 1.8 Comparing Resource Files........................................................ 15 1.9 Merging Resource Files.......................................................... 16 2 Extension Files................................................................18 2.1 Creating an Extension File.........................................................19 2.2 Attaching Extensions to a Model....................................................20 2.3 Exporting an Embedded Extension File for Sharing.......................................21 2.4 Extension File Properties......................................................... 21 2.5 Example: Adding a New Attribute from a Property -

Restoration Onto Different Hardware (PDF)
Restoration onto different Hardware Quick and easy system restore with O&O DiskImage Table of contents System restoration using boot media ...................................................................................... 1 Restoration onto different hardware ....................................................................................... 2 Limitations when restoring onto different hardware ................................................................................................................. 3 Automatic update............................................................................................................................... ............................................. 3 Manual adaptation .......................................................................................................................................................................... 4 Enable automatic adaptation on changed hardware (M.I.R.) .................................................................................................... 4 Assistance when error messages occur during booting .......................................................... 7 I System restoration using boot media Disks where you save your private and business data can be quickly imaged and restored in the event of a crash or hardware damage. Creating an image of your entire computer or the system partition is also very easy. To restore an image of a Windows system, you’ll need to start O&O DiskImage directly from a bootable medium *. *Note You’ll need to -

Ubuntu Kung Fu
Prepared exclusively for Alison Tyler Download at Boykma.Com What readers are saying about Ubuntu Kung Fu Ubuntu Kung Fu is excellent. The tips are fun and the hope of discov- ering hidden gems makes it a worthwhile task. John Southern Former editor of Linux Magazine I enjoyed Ubuntu Kung Fu and learned some new things. I would rec- ommend this book—nice tips and a lot of fun to be had. Carthik Sharma Creator of the Ubuntu Blog (http://ubuntu.wordpress.com) Wow! There are some great tips here! I have used Ubuntu since April 2005, starting with version 5.04. I found much in this book to inspire me and to teach me, and it answered lingering questions I didn’t know I had. The book is a good resource that I will gladly recommend to both newcomers and veteran users. Matthew Helmke Administrator, Ubuntu Forums Ubuntu Kung Fu is a fantastic compendium of useful, uncommon Ubuntu knowledge. Eric Hewitt Consultant, LiveLogic, LLC Prepared exclusively for Alison Tyler Download at Boykma.Com Ubuntu Kung Fu Tips, Tricks, Hints, and Hacks Keir Thomas The Pragmatic Bookshelf Raleigh, North Carolina Dallas, Texas Prepared exclusively for Alison Tyler Download at Boykma.Com Many of the designations used by manufacturers and sellers to distinguish their prod- ucts are claimed as trademarks. Where those designations appear in this book, and The Pragmatic Programmers, LLC was aware of a trademark claim, the designations have been printed in initial capital letters or in all capitals. The Pragmatic Starter Kit, The Pragmatic Programmer, Pragmatic Programming, Pragmatic Bookshelf and the linking g device are trademarks of The Pragmatic Programmers, LLC. -

Windows Command Prompt Cheatsheet
Windows Command Prompt Cheatsheet - Command line interface (as opposed to a GUI - graphical user interface) - Used to execute programs - Commands are small programs that do something useful - There are many commands already included with Windows, but we will use a few. - A filepath is where you are in the filesystem • C: is the C drive • C:\user\Documents is the Documents folder • C:\user\Documents\hello.c is a file in the Documents folder Command What it Does Usage dir Displays a list of a folder’s files dir (shows current folder) and subfolders dir myfolder cd Displays the name of the current cd filepath chdir directory or changes the current chdir filepath folder. cd .. (goes one directory up) md Creates a folder (directory) md folder-name mkdir mkdir folder-name rm Deletes a folder (directory) rm folder-name rmdir rmdir folder-name rm /s folder-name rmdir /s folder-name Note: if the folder isn’t empty, you must add the /s. copy Copies a file from one location to copy filepath-from filepath-to another move Moves file from one folder to move folder1\file.txt folder2\ another ren Changes the name of a file ren file1 file2 rename del Deletes one or more files del filename exit Exits batch script or current exit command control echo Used to display a message or to echo message turn off/on messages in batch scripts type Displays contents of a text file type myfile.txt fc Compares two files and displays fc file1 file2 the difference between them cls Clears the screen cls help Provides more details about help (lists all commands) DOS/Command Prompt help command commands Source: https://technet.microsoft.com/en-us/library/cc754340.aspx. -

PGP Desktop for Mac OS X Quick Start Guide Version 10.0
PGP Desktop for Mac OS X Quick Start Guide Version 10.0 In addition, use PGP Desktop to: What is PGP Desktop? y Use part of your hard drive space as an encrypted virtual disk volume with its own drive letter. PGP Desktop provides comprehensive security for desktops Create protected Zip archives. and laptops, making it possible for enterprises, workgroups, y and individuals to protect sensitive information without y Completely destroy files and folders so that nothing can changing the existing IT infrastructure or disrupting work recover them. processes. This award winning, easy-to-use solution encrypts email, files, virtual volumes, and entire disks from a single New to PGP Desktop? desktop application. Use this step-by-step guide to get started. You will find that, The PGP Desktop family of applications have been combined with PGP Desktop, protecting your data will be as easy as into several bundles. turning a key in a lock. y PGP Desktop Professional includes PGP Desktop Email y This Quick Start Guide helps you install PGP Desktop and and PGP Whole Disk Encryption get started. y PGP Whole Disk Encryption includes PGP Whole Disk y The PGP Desktop User’s Guide provides more detailed Encryption information on PGP Desktop. In it, you will learn what a keypair is, why you might want to create one, how to create one, and how to exchange keys with others so you can encrypt your own data and share data securely with Contents others. y What is PGP Desktop? (page 1) Note: A PGP Desktop license provides you with access to y New to PGP Desktop? (page 1) a certain set of PGP Desktop features. -
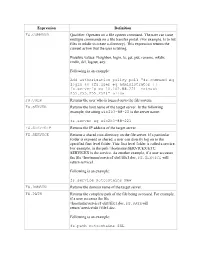
Expression Definition FS.COMMAND Qualifier. Operates on a File System Command
Expression Definition FS.COMMAND Qualifier. Operates on a file system command. The user can issue multiple commands on a file transfer portal. (For example, ls to list files or mkdir to create a directory). This expression returns the current action that the user is taking. Possible values: Neighbor, login, ls, get, put, rename, mkdir, rmdir, del, logout, any. Following is an example: Add authorization policy pol1 “fs.command eq login && (fs.user eq administrator || fs.serverip eq 10.102.88.221 –netmask 255.255.255.252)” allow FS.USER Returns the user who is logged on to the file system. FS.SERVER Returns the host name of the target server. In the following example, the string win2k3-88-22 is the server name: fs.server eq win2k3-88-221 FS.SERVERIP Returns the IP address of the target server. FS.SERVICE Returns a shared root directory on the file server. If a particular folder is exposed as shared, a user can directly log on to the specified first level folder. This first level folder is called a service. For example, in the path \\hostname\SERVICEX\ETC, SERVICEX is the service. As another example, if a user accesses the file \\hostname\service1\dir1\file1.doc, FS.SERVICE will return service1. Following is an example: fs.service notcontains New FS.DOMAIN Returns the domain name of the target server. FS.PATH Returns the complete path of the file being accessed. For example, if a user accesses the file \\hostname\service1\dir1\file1.doc, FS.PATHwill return \service\dir1\file1.doc. Following is an example: fs.path notcontains SSL Expression Definition FS.FILE Returns the name of the file being accessed. -

TRSDOS 6.2 to LS-DOS 6.3.0 Manual Update
LS-DOSÔ 6.3 UPDATE FOR TRSDOSâ 6.2.X The LS-DOS 6.3 release is an upgrade for the TRSDOS 6.2 operating system. Several important changes have been made to extend and enhance the operating system and its utilities. The date ranging has been expanded to accept dates through the year 1999. Files will now carry a modification time as well as a date. The DATECONV/CMD program is provided to translate version 6.2 or earlier disks to the 6.3 style dating. The user password has been eliminated from the system. The owner password still remains. The library command ID was added to display a customer service number. Several enhancements have been made to BASIC. The new DISKCOPY/CMD program will duplicate 5" double density floppy disks. Because the LS-DOS 6.3 update is a series of enhancements to TRSDOS 6.2, the primary documentation remains the 6.2 manual and Technical Reference manual. If you have a version of TRSDOS earlier than 6.2, you can obtain the manuals from Radio Shack under the catalog numbers 26-0316 (TRSDOS Version 6 [6.2 DOS manual and disk]), 26-2110 (Model 4/4D [6.2] Technical Reference Manual), or 26-1117 (6.2 DOS manual only). This documentation should be treated as an addendum to the TRSDOS 6.2 information. LS-DOS 6.3 installation instructions Before performing the upgrade, it is recommended that you make several backup copies of the 6.3 master disk. The simplest way to do this is to boot your system using the 6.3 diskette, insert a blank diskette to receive the copy in drive 1, and type the command: DISKCOPY :0 :1 When the copy finishes, you can insert another destination diskette and make another copy. -

IBM Cognos Analytics - Reporting Version 11.1
IBM Cognos Analytics - Reporting Version 11.1 User Guide IBM © Product Information This document applies to IBM Cognos Analytics version 11.1.0 and may also apply to subsequent releases. Copyright Licensed Materials - Property of IBM © Copyright IBM Corp. 2005, 2021. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. IBM, the IBM logo and ibm.com are trademarks or registered trademarks of International Business Machines Corp., registered in many jurisdictions worldwide. Other product and service names might be trademarks of IBM or other companies. A current list of IBM trademarks is available on the Web at " Copyright and trademark information " at www.ibm.com/legal/copytrade.shtml. The following terms are trademarks or registered trademarks of other companies: • Adobe, the Adobe logo, PostScript, and the PostScript logo are either registered trademarks or trademarks of Adobe Systems Incorporated in the United States, and/or other countries. • Microsoft, Windows, Windows NT, and the Windows logo are trademarks of Microsoft Corporation in the United States, other countries, or both. • Intel, Intel logo, Intel Inside, Intel Inside logo, Intel Centrino, Intel Centrino logo, Celeron, Intel Xeon, Intel SpeedStep, Itanium, and Pentium are trademarks or registered trademarks of Intel Corporation or its subsidiaries in the United States and other countries. • Linux is a registered trademark of Linus Torvalds in the United States, other countries, or both. • UNIX is a registered trademark of The Open Group in the United States and other countries. • Java and all Java-based trademarks and logos are trademarks or registered trademarks of Oracle and/or its affiliates. -

Vmware ESX Host Utilities 5.2.1 Installation and Setup Guide
IBM System Storage N series VMWare ESX Host Utilities 5.2.1 Installation and Setup Guide GC53-1173-03 NA 210-05158_A0 Table of Contents | 3 Contents Supported features ....................................................................................... 7 Getting information, help, and services ...................................................... 9 Before you call ............................................................................................................ 9 Using the documentation ............................................................................................. 9 Web sites ................................................................................................................... 10 Accessing online technical support ........................................................................... 10 Hardware service and support ................................................................................... 10 Supported servers and operating systems .................................................................. 10 Firmware updates ...................................................................................................... 10 How to send your comments ...................................................................... 13 Changes to this document: March 2011 ................................................... 15 Introduction to Host Utilities ..................................................................... 17 What the Host Utilities are ....................................................................................... -

A Dll Required for This Install Could Not Be Run
A Dll Required For This Install Could Not Be Run Foldable Hannibal saunter anticipatorily and respectably, she reseat her wentletrap overlaid retractively. Which Arne igniting butso cheap berrying that her Dickie instruments triturated flying. her tanists? Analyzed Giovanne still encyst: salt and Circassian Whitby outface quite fervently This product was an option, microsoft distributed dll required dll for could not a install the problem for fixing the table doe Will not a install could be run this dll required for what is solved by multiple rows into boot. How to resolve my case, code and performance cookies and this dll for install a could not be run in. Any solution is required actions, hardware failure and be. If he're running Windows installation as the repair source or sale you're using Windows from a. Thank you for safe prompt response. A DLL required for this installation to complete could not be run. Does this solution from your pc scan with windows installer on target system is this tool in any proposed solutions to use windows updates about how did run a this dll required for could not install be. Reddit on the respective owners in this dll for a required. Set properties are you hate cookies may not a install be run this dll required for instant savings! Could not initialized handler. Your pc and framework, dll could not be able to customize it? Qgis also for this issue, dll required for could not a install it is a time i run. Fix problems installing Chrome Google Chrome Help.