Secure PHP Development Handbook PHP Security Community of Practice Revision V1.0
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Codeigniter-Testing-Guide-Sample.Pdf
CodeIgniter Testing Guide Beginners’ Guide to Automated Testing in PHP. Kenji Suzuki and Mat Whitney This book is for sale at http://leanpub.com/codeigniter-testing-guide This version was published on 2016-01-23 This is a Leanpub book. Leanpub empowers authors and publishers with the Lean Publishing process. Lean Publishing is the act of publishing an in-progress ebook using lightweight tools and many iterations to get reader feedback, pivot until you have the right book and build traction once you do. © 2015 - 2016 Kenji Suzuki and Mat Whitney Tweet This Book! Please help Kenji Suzuki and Mat Whitney by spreading the word about this book on Twitter! The suggested hashtag for this book is #CITestGuide. Find out what other people are saying about the book by clicking on this link to search for this hashtag on Twitter: https://twitter.com/search?q=#CITestGuide Contents Preface ............................................... i The Book at a Glance ..................................... i What You Need for This Book ................................. iii Who should read This Book? ................................. iii Why PHPUnit? ........................................ iv Is This a CodeIgniter Book? .................................. iv Is Testing PHP Applications Difficult? ............................ iv Is Testing CodeIgniter Applications Difficult? .................... v Testing is Fun and Easy ................................ v Conventions Used in This Book ................................ v Errata ............................................. -
Overall Features Performance Price
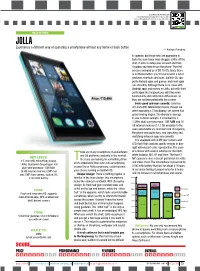
Scan this code for more info. To download a barcode app, SMS <f2k> to 56677 from a mobile phone with Internet access and camera. SMARTPHONE JOLLA Experience a different way of operating a smartphone without any home or back button — Ashok Pandey to operate, but those who are upgrading to taste the new flavor may struggle a little. At the start, it asks to setup your account and then, it guides you how to use the phone. The first screen reminded us of BB 10 OS. Since there is no Home button, you’ll have to learn a lot of gestures, shortcuts and cues. Sailfish OS sup- ports Android apps and games, and most apps run smoothly. Although there is no issue with Android apps and games on Jolla, but with third party apps like facebook you will find some functionality and notification differences, as Price: `15,490 they are not integrated with the system. Feels good and runs smooth: Jolla has 4.5-inch qHD (960x450p) display, though we were expecting a 720p display, yet screen has good viewing angles. The display is average to use in direct sunlight. It is backed by a 1.4GHz dual-core processor, 1GB RAM and 16 GB internal memory (13.7 GB available to the user) expandable via microSD card. Navigating the phone was quite easy, and launching and switching between apps was smooth. It is equipped with 8 MP rear camera with LED flash that captures quality images in day- light with decent color reproduction. The cam- here are many smartphone manufacturers era comes with several settings for the flash, and OS platforms available in the market. -

YOSSEF BENHAROSH RESUME 972 (0) 544-308209 | [email protected] | Kiryat Gat, Israel
YOSSEF BENHAROSH RESUME 972 (0) 544-308209 | [email protected] | Kiryat Gat, Israel PHP & Drupal developer, June 2011 – present Freelance web developer for 4 years who works with the following technologies: PHP, MySQL, Javascript, jQuery, Drupal, HTML/HTML5, CSS/CSS3. Specializes in PHP development. Including: Object-Oriented Programming, mySQL as a data base, and Laravel as a framework. Drupal developer, specializing in developing new modules and themes, and in taming existing modules. Good working knowledge of organic SEO. Chosen works freefax.co.il – PHP site that provides fax services. I worked as a PHP and mySQL programmer, as well as on the front end with jQuery, Ajax, html and CSS. I wrote the cart and invoice modules and the user class. puzzlemedia.co.il – Bilingual Drupal website for film producers. www.yaronlivne.co.il – Drupal based app that I wrote most of its modules and developed its’ theme. ZEZBRA – A startup that I themed its Drupal site, as well as developed its PHP based cellular version. reshetech.co.il – Hebrew tutorials website based on PHP. phpenthusiast.com – English tutorials website devoted to Object Oriented PHP. Github projects myAPI – I think it is the simplest way to provide API services for small businesses that want to provide data based services to their customers. csvtax – Drupal 7 module that transforms a CSV file into hierarchical taxonomy. cornerslider – A jQuery popup that slides the content in and out when the user scrolls down and up the page. Technologies Back end programming languages: PHP, mySQL. Front end programming languages: CSS/3, HTML/5, javascript. -

Cakephp Cookbook Documentation Release 4.X
CakePHP Cookbook Documentation Release 4.x Cake Software Foundation Sep 25, 2021 Contents 1 CakePHP at a Glance 1 Conventions Over Configuration........................................1 The Model Layer................................................1 The View Layer.................................................2 The Controller Layer..............................................2 CakePHP Request Cycle............................................3 Just the Start...................................................4 Additional Reading...............................................4 2 Quick Start Guide 13 Content Management Tutorial......................................... 13 CMS Tutorial - Creating the Database..................................... 15 CMS Tutorial - Creating the Articles Controller................................ 19 3 4.0 Migration Guide 29 Deprecated Features Removed......................................... 29 Deprecations.................................................. 29 Breaking Changes................................................ 31 New Features.................................................. 37 4 Tutorials & Examples 41 Content Management Tutorial......................................... 41 CMS Tutorial - Creating the Database..................................... 43 CMS Tutorial - Creating the Articles Controller................................ 47 CMS Tutorial - Tags and Users......................................... 56 CMS Tutorial - Authentication......................................... 64 CMS Tutorial - Authorization......................................... -

PHP 7 Y Laravel
PHP 7 y Laravel © All rights reserved. www.keepcoding.io 1. Introducción Nada suele ser tan malo como lo pintan © All rights reserved. www.keepcoding.io When people tell me PHP is not a real programming language http://thecodinglove.com/post/114654680296 © All rights reserved. www.keepcoding.io Quién soy • Alicia Rodríguez • Ingeniera industrial ICAI • Backend developer • @buzkall • buzkall.com http://buzkall.com © All rights reserved. www.keepcoding.io ¿Qué vamos a ver? • Instalación y desarrollo en local • PHP 7 • Laravel • Test unitarios • Cómo utilizar una API externa © All rights reserved. www.keepcoding.io ¿Qué sabremos al terminar? • PHP mola • Crear un proyecto de cero • Depurar y hacer test a nuestro código • Un poco de análisis técnico y bolsa © All rights reserved. www.keepcoding.io Seguridad Security is not a characteristic of a language as much as it is a characteristic of a developer Essential PHP Security. Chris Shiflett. O’Reilly © All rights reserved. www.keepcoding.io Popularidad en Stackoverflow http://stackoverflow.com/research/developer-survey-2016 © All rights reserved. www.keepcoding.io Popularidad en Github http://redmonk.com/sogrady/2016/07/20/language-rankings-6-16/ © All rights reserved. www.keepcoding.io Frameworks por lenguaje https://hotframeworks.com/ © All rights reserved. www.keepcoding.io Su propia descripción • PHP is a popular general-purpose scripting language that is especially suited to web development. • Fast, flexible and pragmatic, PHP powers everything from your blog to the most popular websites in the world. https://secure.php.net/ © All rights reserved. www.keepcoding.io Historia de PHP • Creado por Rasmus Lerdorf en 1995 como el conjunto de scripts "Personal Home Page Tools", referenciado como "PHP Tools”. -

Phpunit Manual Release Latest
PHPUnit Manual Release latest Sebastian Bergmann Aug 18, 2021 Contents 1 Installing PHPUnit 3 1.1 Requirements...............................................3 1.2 Recommended PHP configuration....................................3 1.3 PHP Archive (PHAR)..........................................3 1.3.1 PHAR Implementation Details.................................4 1.3.2 Verifying PHPUnit PHAR Releases..............................4 1.4 Composer.................................................5 1.5 Global Installation............................................5 1.6 Webserver................................................6 2 Writing Tests for PHPUnit 7 2.1 Test Dependencies............................................8 2.2 Data Providers.............................................. 11 2.3 Testing Exceptions............................................ 17 2.4 Testing PHP Errors, Warnings, and Notices............................... 17 2.5 Testing Output.............................................. 20 2.6 Error output............................................... 21 2.6.1 Edge Cases........................................... 23 3 The Command-Line Test Runner 25 3.1 Command-Line Options......................................... 26 3.2 TestDox.................................................. 32 4 Fixtures 35 4.1 More setUp() than tearDown()...................................... 38 4.2 Variations................................................. 38 4.3 Sharing Fixture.............................................. 38 4.4 Global State.............................................. -

Phpunit Manual Version Latest
PHPUnit Manual Version latest Sebastian Bergmann sept. 07, 2021 Table des matières 1 Installer PHPUnit 3 1.1 Pré-requis.................................................3 1.2 PHP Archive (PHAR)..........................................3 1.2.1 Windows............................................4 1.2.2 Vérification des versions PHAR de PHPUnit.........................4 1.3 Composer.................................................6 1.4 Paquets optionnels............................................6 2 Écrire des tests pour PHPUnit9 2.1 Dépendances des tests.......................................... 10 2.2 Fournisseur de données......................................... 13 2.3 Tester des exceptions........................................... 18 2.4 Tester les erreurs PHP.......................................... 19 2.5 Tester la sortie écran........................................... 21 2.6 Sortie d’erreur.............................................. 22 2.6.1 Cas limite............................................ 24 3 Lanceur de tests en ligne de commandes 27 3.1 Options de la ligne de commandes.................................... 28 3.2 TestDox.................................................. 34 4 Fixtures 35 4.1 Plus de setUp() que de tearDown().................................... 38 4.2 Variantes................................................. 38 4.3 Partager les Fixtures........................................... 38 4.4 Etat global................................................ 39 5 Organiser les tests 41 5.1 Composer une suite de tests -

Django and Mongodb
Slide Gallery . 8 .bookmarks . 8 1.1 Development Cycle . 8 Creating and Deleting Indexes . 8 C Sharp Language Center . 8 Diagnostic Tools . 8 Django and MongoDB . 9 Getting Started . 9 International Documentation . 9 Monitoring . 9 Older Downloads . 9 PyMongo and mod_wsgi . 9 Python Tutorial . 10 Recommended Production Architectures . 10 v0.8 Details . 10 Building SpiderMonkey . 10 Documentation . 11 Dot Notation . 11 Dot Notation . Getting the Software . 11 Language Support . 11 Mongo Administration Guide . 11 Working with Mongo Objects and Classes in Ruby . 12 MongoDB Language Support . 12 Community Info . 12 Internals . 12 TreeNavigation . 13 Old Pages . 13 MongoDB - A Developer's Tour . 13 Mongo Developers' Guide . 13 HowTo . 13 Database Profiler . 13 Updating Data in Mongo . 13 BSON . 14 Full Text Search in Mongo . 14 Queries and Cursors . 14 Indexes . 14 Object IDs . 14 Troubleshooting .. -

WEB DEVELOPER » Portfolio » Github SUMMARY I’M a Full-Stack Developer and a Programming Instructor
LUIS MONTEALEGRE - WEB DEVELOPER » Portfolio » Github SUMMARY I’m a full-stack developer and a programming instructor. I want to be surrounded by people who push me to do the best work of my career as well as people I can nurture and support. I have over 13 years of experience in tech both in Mexico and the United States and I’m looking forward to be part of a team that values work-life balance, TDD, pair programming and code reviews. PROGRAMMING LANGUAGES AND TOOLS PHP 11 years • Laravel, Zend Framework 1, Symfony 1 & 2, Slim 2, Silex, Doctrine 1 & 2, PHPUnit, Behat, phpspec, Codeception • MySQL, PostgreSQL • jQuery, Jasmine, RequireJS, Bower, npm, Webpack, ES6, PhantomJS • Bootstrap, Sass • Vagrant, Docker • Git, SVN C# 4 years • ASP.NET Web Forms, Visual Basic • jQuery, JQuery UI • SQL Server, Oracle PL/SQL • TFS Java 2 years • Spring Boot, JUnit, Hibernate, DBUnit, Servlets, JSP/JSTL, Swing • Maven • MySQL, PostgreSQL CERTIFICATIONS EDUCATION Latinux Certified Linux Operator B. S. and Master in Computer Science. Oracle Certified Java Programmer Emeritus Autonomous University of Puebla. MCTS Microsoft SQL Server & Web [1998-2003, 2003-2005] Applications OPEN SOURCE CONTRIBUTIONS AND COMMUNITY WORK My contributions to open source projects include: Drupal Console, Codeception, Eris and Couscous. I also maintain some libraries: Modules System for Slim 2, Doctrine DBAL Fixtures Generator and a Yelp Fusion API Java Client. I'm the founder an former organizer of the PHP Puebla User Group. I helped organizing dozens of workshops and technical talks. I'm currently particpating with the San Antonio Coding Challenge meetup. -

Clemence Lelong Grenoble, France
Clemence Lelong Grenoble, France 0651008126 WEB ENGINEER – BA / Full-Stack [email protected] developer KEY SKILLS Front end / back end Web development (7 years of experience) Business analysis (7+ years of experience) Technology Scouting, constant learning mode SKILLS MATRIX Ruby (Ruby on rails) (2 years, proficient, since 2012) JavaScript / HTML / CSS : Ajax, ExtJS, Jquery, AngularJS (7 years, proficient) MySQL, PostgreSQL, Web server administration Apache / Unicorn / Nginx (7 years, proficient) UML, Object Oriented Programming (7 years, proficient) SCRUM (study and use since 2006) Linux + AWS experience (7 years, proficient) PHP, XML for Web services REST and SOAP (WSDL), (4 years, proficient, last year used 2012) JAVA, XML for ANT, scripts Perl & SH ( 1 year, intermediate, last year used 2007) VB Script, SQL server (1 year, intermediate, last year used 2006) ASP, VB Access (<6 months, junior, last year used 2005) IDE (Eclipse, Aptana, now Sublime), Version control (CVS, SVN, now GIT), Tests (PHPUnit, JUnit, SOAPUI, Selenium, now Rpsec), miscellaneous (RPM, ANT, Continuum, HandlebarsJS, UnderscoreJS, CoffeeScript, YAML, middleman, Bootstrap, Sidekiq, Solr...) Topics of interest : Scalability, Continuous integration, TDD, Scrum, Gamification PROFESSIONAL EXPERIENCE (References available on demand) Web Engineer – Full stack developer 2012-2014 Self employed, part-time (Brisbane Australia, Grenoble France) As a freelancer, I worked with a client based in Japan to design, build, test and deploy a scalable, and highly available Web site called HooliTV which is a platform to watch Football highlights. This project richly involved Web Scraping, AWS architecture, Solr search, UI performance tuning, caching, API communications, and localization. I collaborated with a Design company who have created the responsive design. -

Bdd, Functional Tests & Selenium (In Drupal!)
Behat BDD, FUNCTIONAL TESTS & SELENIUM (IN DRUPAL!) ♥’s Hallo! > Lead of the Symfony documentation team > KnpLabs US - Symfony consulting, training & kumbaya > Writer for KnpUniversity.com: PHP & Symfony screencasts packed with puns, unrelated (but entertaining) illustrations and coding challenges! > Husband of the much more talented @leannapelham knpuniversity.com twitter.com/weaverryan Plan, Work, Miscommunicate, Panic, Put out Fires, Repeat! aka Project Work! How the customer explained it http://www.projectcartoon.com How the project leader understood it http://www.projectcartoon.com How the programmer wrote it http://www.projectcartoon.com What the customer really needed http://www.projectcartoon.com What the beta testers received http://www.projectcartoon.com Computer Science? https://www.flickr.com/photos/diueine/3604050776 One Different roles, different languages, miscommunication @weaverryan Tw o Your code and business values may not align @weaverryan I've just dreamt up this cool new feature that we should implement! Why? Because it's cool! Three Over-planning, under-planning, planning...? @weaverryan Getting down with BDD https://www.flickr.com/photos/tambako/4175456498 Evolution of Test-Driven Development @weaverryan “Behaviour” is a more useful word, than “test” - Dan North * * the santa of behavior-driven development Evolution of Test-Driven Development ≈ Unit Tests ≈ Functional Tests @weaverryan Specification BDD http://www.phpspec.net @weaverryan Scenario-oriented BDD (Story BDD) Let’s create a single vocabulary and process -

Full Stack Developer London £525/Day Years of Experience: 10+ Latest Contract: Javascript / PHP Developer at a Top National Organisation
Full Stack Developer London £525/day Years of experience: 10+ Latest contract: JavaScript / PHP Developer at a Top National Organisation. Professional Profile: • Full stack developer, JavaScript Developer, MEAN Stack Developer, LAMP Stack Developer • Solid, commercial, hands-on experience and in-depth knowledge of various web technologies with focus on the LAMP and MEAN stack (JavaScript). • Service Oriented Architecture, REST API, solid OOP, CMS, CRM systems, design patterns, Test Driven Development (TDD), BDD, Agile, Scrum, Kanban, Continues Integration • PHP: 10 years of experience in PHP, Zend Framework (ZF1, ZF2), Doctrine2 (ORM), PHPUnit (TDD), Behat (BDD), Mink (Selenium) • Javascript: MEAN (MongoDB, Express, Angular, Node.js), Task runners (Grunt, Gulp), Bower, RequireJS, TDD & BDD (jasmine, karma, protractor) • DB: MySQL (Percona, MariaDB), MSSQL, MongoDB, ElasticSearch • Frontend: HTML5, CSS3, AngularJS, vanilla JavaScript, jQuery, Twitter Bootstrap, LESS, SASS • Misc: Amazon Web Services (AWS), git, git-flow, github, vagrant, docker, Jenkins, CI, CD • Experience in working in Agile environments. Strong experience in technical, business/system analysis and system design. Strong problem solving. Solid understanding of the full development life cycle Creation Recruitment | 01179 298 243 | www.creationrecruitment.co.uk Relevant Experience: Top National Organisation – Contract Javascript/PHP Developer November 2015 – present Greenfield MVP Case Management for 4000 local orgaisation offices. Techstack and environment: • Env: docker,