Windows Server 2008 R2 Boot Manager Security Policy for FIPS 140-2 Validation
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

No More Excuses: Windows 7 Makes It Easy to Manage Computer Power
• Products that earn the ENERGY STAR® prevent greenhouse gas emissions by meeting strict energy efficiency guidelines set by the U.S. Environmental Protection Agency and the U.S. Department of Energy. www.energy star.gov NO MORE EXCUSES: WINDOWS 7 MAKES IT EASY TO MANAGE COMPUTER POWER CONSUMPTION ORGANIZATION-WIDE Here’s how you can take advantage of Windows 7’s new power management features The University of Wisconsin at Oshkosh is no stranger to the idea of sustainability. In 2003 it became the first university in the state to join the Environmental Protection Agency’s Green Power Partnership. Its green initiatives also earned the university high marks from the Sierra Club, which ranked the university nationally in its Cool Schools survey. Given this commitment to green, it’s no surprise that the university first deployed computer power management back in 2005, and that it was one of the first Energy Star power management success stories. At that time, the University’s computers ran the Windows XP and Windows 2000 operating systems, neither of which included native tools for the central administration of power management features. To implement power management settings on these machines, the University used third-party software from ENERGY STAR called EZ GPO. For detailed information and resources concerning Now that Windows 7 has CPM client management features built in, it’s much the power management of easier to administer power management. This case study will show you how the University of Wisconsin at Oshkosh took full advantage of computer power PCs running Windows XP, management features on Windows Vista and Windows 7 clients managed by please see the ENERGY STAR Windows Server 2008. -

Starburn CD/DVD/Blu-Ray/HD-DVD Toolkit: Getting Started
StarBurn Software Technical Reference Series StarBurn CD/DVD/Blu-Ray/HD-DVD Toolkit: Getting Started April 18, 2016 StarBurn Software www.starburnsoftware.com Copyright © Rocket Division Software 2001-2016. All rights reserved. Copyright © StarBurn Software 2009-2016. All rights reserved. StarBurn CD/DVD/Blu-Ray/HD-DVD Toolkit: Getting Started Page 1 of 13 StarBurn Software Technical Reference Series INTRODUCTION .................................................................................................. 4 KEY BENEFITS ..................................................................................................... 5 KEY FEATURES .................................................................................................... 7 SUPPORTED PLATFORMS .................................................................................. 11 SYSTEM REQUIREMENTS................................................................................... 12 CONTACTS........................................................................................................ 13 StarBurn CD/DVD/Blu-Ray/HD-DVD Toolkit: Getting Started Page 2 of 13 StarBurn Software Technical Reference Series COPYRIGHT Copyright © Rocket Division Software 2001-2016. All rights reserved. Copyright © StarBurn Software 2009-2016. All rights reserved. All rights reserved. No part of this publication may be reproduced, stored in a retrieval system, or transmitted in any form or by any means, electronic, mechanical, photocopying, recording or otherwise, without the prior written -

In Windows Server 2008 R2 and Windows Server 2008 (The Former Containing the Later Release of Hyper-V)
Hyper-V Microsoft Hyper-V Developer(s) Microsoft Initial release July 26, 2008 (KB950050)[1][2] R2 Service Pack 1 Stable release (KB976932)[3][4] / March 15, 2011; 15 months ago Windows 8 (both its server and client versions) (future) and Operating system Windows Server 2008 or standalone Type Virtual machine License Proprietary Hyper V Slide 1 of 21 Microsoft Hyper-V ■ Microsoft Hyper-V, ✦ codenamed Viridian ✦ and formerly known as Windows Server Virtualization, ✦ is a hypervisor-based virtualization system for x86-64 systems ■ A beta version of Hyper-V was shipped with certain x86-64 editions of Windows Server 2008, and the finalized version (automatically updated through Windows Update) was released on June 26, 2008 ■ Hyper-V has since been released in a free stand-alone version, and has been upgraded to Release 2 (R2) status Hyper V Slide 2 of 21 Versions and variants ■ Hyper-V exists in two variants: ✦ as a stand-alone product called Microsoft Hyper-V Server 2008 (Hyper-V Server 2008 R2 for the second release), ✦ and as an installable role in Windows Server 2008 R2 and Windows Server 2008 (the former containing the later release of Hyper-V). ■ The stand-alone version of Hyper-V is free, and was released on October 1, 2008. ■ It is a variant of the core installation of Windows Server 2008 that includes full Hyper-V functionality; other Windows Server 2008 roles are disabled, and there are limited Windows Services. ■ The free Hyper-V Server 2008 variant is limited to a command line interface (CLI), where configuration of the "Host" or "Parent" (Hyper-V Server 2008) OS, physical hardware and software is done using shell commands. -

Microsoft Update Testing
Microsoft Update Testing Microsoft provides the Windows Update Service that distributes bug fixes in the form of patches. Normally, Microsoft release patches via Windows Update every second Tuesday of each month and this has unofficially become known as 'Patch Tuesday'. To assure end users they can install Microsoft patches without adversely affecting existing installations of ClearSCADA, a set of regression tests are run on selected operating systems with released versions of ClearSCADA. Date: 11-06-2015 Operating Systems • Windows 7 SP1 (x64) • Windows Server 2008 R2 (x64) • Windows Server 2012 R2 • Windows 8.1 ClearSCADA 2010 R3.2 (72.5373), ClearSCADA 2013 R1.2 (73.4955), ClearSCADA 2013 R2.1 (RC Build 74.5213), ClearSCADA 2014 R1 (75.5387) and ClearSCADA 2015 R1 (76.5640) Installed Patches/Updates on Windows 7 (x64) Security Update for Windows 7, Windows Server 2008 R2, Windows Server 2008, and Windows Vista (KB3063858) https://support.microsoft.com/kb/3063858 Security Update for Windows 7, Windows Server 2008 R2, Windows Server 2008, and Windows Vista (KB3059317) https://support.microsoft.com/kb/3059317 Cumulative Security Update for Internet Explorer (KB3058515) https://support.microsoft.com/kb/3058515 Security Update for Windows 7, Windows Server 2008 R2, Windows Server 2008, Windows Vista, Windows Server 2003, and Windows XP Embedded (KB3057839) https://support.microsoft.com/kb/3057839 Security Update for Windows 7, Windows Server 2008 R2, Windows Server 2008, Windows Vista, Windows Server 2003, and Windows XP Embedded (KB3033890) -

System Requirements
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files, release notes, and the latest version of the applicable user documentation, which are available from the Trend Micro website at: http://docs.trendmicro.com/en-us/enterprise/trend-micro-apex-one.aspx Trend Micro, the Trend Micro t-ball logo, and Trend Micro Apex One are trademarks or registered trademarks of Trend Micro Incorporated. All other product or company names may be trademarks or registered trademarks of their owners. Copyright © 2019 Trend Micro Incorporated. All rights reserved. Release Date: March 2019 Protected by U.S. Patent No. 5,623,600; 5,889,943; 5,951,698; 6,119,165 Table of Contents Chapter 1: Apex One Server Installations Fresh Installations on Windows Server 2012 Platforms ..................................................................................................................................................................................... 1-2 Fresh Installations on Windows Server 2016 Platforms ..................................................................................................................................................................................... 1-3 Fresh Installations on Windows Server 2019 Platforms .................................................................................................................................................................................... -

Windows Server 2003 R2, Windows Server 2008 R2, and Windows Server 2012
Feature Comparison Windows Server 2003 R2, Windows Server 2008 R2, and Windows Server 2012 Contents Introduction ............................................................................... 3 Top Ten Features ...................................................................... 4 General Features Overview .................................................... 8 © 2012 Microsoft Corporation. All rights reserved. This document is provided "as-is." Information and views expressed in this document, including URL and other Internet Web site references, may change without notice. You bear the risk of using it. Feature Comparison: Windows Server 2003 R2, Windows Server 2008 R2, and Windows Server 2012 2 Introduction This feature comparison guide compares selected features of Windows Server 2003 R2, Windows Server 2008 R2, and Windows Server 2012. The “Top Ten Features” section provides an overview of some of the most important features of Windows Server 2012, and the “General Features Overview” section compares a wider-range of features across all three releases. The comparison tables in both sections include comments in regard to each release, as well as notation about how well each feature is supported. The legend for this notation is as follows: Level of Feature Support Feature is supported Feature is only partially supported Feature is not supported Feature Comparison: Windows Server 2003 R2, Windows Server 2008 R2, and Windows Server 2012 3 Top Ten Features This section provides an overview of the top ten features of Windows Server 2003 -

HP Indigo Customer Note Wanna Cry Ransomware
HP Indigo Customer Note Wanna Cry Ransomware Affected products All HP Indigo presses and DFEs Applicable to This customer note is applicable to Level 1 Operators and above. Background In the last few days, a new ransomware (Wanna Cry, WannaCrypt, WCry, WCrypt) has attacked and encrypted thousands of computers worldwide. Microsoft has released a security update to prevent operating systems from being infected. The update also covers Windows operating systems that are no longer supported by HP Indigo (XP, Vista, 2003). The security updates have been qualified and released for all presses and DFEs as follows: Operating System Deployment method Supported operating systems: Released to presses and DFEs via Microsoft updates mechanism Windows 7, Windows Server 2008 R2, Windows Server 2012 Unsupported operating systems: Implemented via Hot Fix through HP Radar XP SP3, Vista, 2003 ESKO with Windows 2003 Remotely by local service teams Instructions For presses and DFEs with supported operating systems, install the update from Windows Control Panel>System and Security>Windows Update. Customer note: 2118 – 17 May 2017 Wanna Cry Ransomware 1 For unsupported operating systems, the Hot Fix will be updated automatically via HP Radar. Notes Customers with Windows XP SP2 must upgrade to SP3 to enable the Hot Fix installation. Refer to CN-2040 - Windows XP Service Pack 3, for additional information. © Copyright 2017 HP Development Company, L.P. Reproduction, adaptation, or translation without prior permission is prohibited, except as allowed under the copyright laws. The information contained herein is subject to change without notice. The only warranties for HP products and services are set forth in the express warranty statements accompanying such products and services. -

Powershell 5 Preview April 2015
Gold partner: Generální partner: Windows PowerShell 5 Preview April 2015 Michael Grafnetter www.dsinternals.com Agenda . About PowerShell 4 . PowerShell ISE 4 . New Syntax . Desired State Configuration . New Cmdlets Where to get it . Built-in – Windows 10 Preview . Windows Management Framework 5.0 Preview April 2015 – Windows Server 2012 R2 – Windows 8.1 Pro – Windows 8.1 Enterprise – Windows Server 2012 – Windows 7 SP1 – Windows Server 2008 R2 SP1 Installing PowerShell 5 Checking PowerShell Version Known incompatibilities . System Center 2012 Configuration Manager (without SP1) . Windows Small Business Server 2011 Standard Missing Documentation BLACK is BACK! Windows 10 Command Line ISE Remote Debugging Advanced Debugging . Attach to process – Enter-PSHostProcess – Exit-PSHostProcess . Break All – Console: Ctrl+Break – ISE: Ctrl+B or Debug->Break All Cortana and ISE Context Menu PowerShell Transcription PowerShell Transcription PowerShell Script Block Logging PowerShell Script Block Logging Symlink and Hardlink Support . New-Item -ItemType SymbolicLink -Name MySymLinkDir -Target $pshome . New-Item -ItemType HardLink -Path C:\Temp -Name MyHardLinkFile.txt -Value $pshome\profile.ps1 . New-Item -ItemType Junction -Path C:\Temp\MyJunctionDir -Value $pshome . Get-ChildItem DEMO Managing .ZIP Files . Compress-Archive [-Path] <String[]> [-DestinationPath] <String> [-CompressionLevel <Microsoft.PowerShell.Commands.CompressionLevel>] [-Update] . Expand-Archive [-Path] <String> [-DestinationPath] <String> DEMO New-TemporaryFile Recursion Depth -
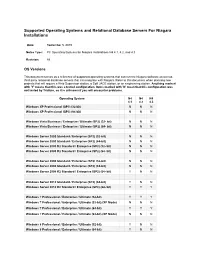
Supported Operating Systems for Niagara 4.1, 4.2
Supported Operating Systems and Relational Database Servers For Niagara Installations Date: September 5, 2019 Notes Type: PC Operating Systems for Niagara Installations N4 4.1, 4.2, and 4.3 Revision: All OS Versions This document serves as a reference of supported operating systems that can run the Niagara software as well as third party relational database servers that can integrate with Niagara. Refer to this document when planning new projects that will require a Web Supervisor station, a Soft JACE station, or an engineering station. Anything marked with 'Y' means that this was a tested configuration. Items marked with 'N' mean that this configuration was not tested by Tridium, so it is unknown if you will encounter problems. Operating System N4 N4 N4 4.1 4.2 4.3 Windows XP Professional (SP3) (32-bit) N N N Windows XP Professional (SP3) (64-bit) N N N Windows Vista Business / Enterprise / Ultimate (SP2) (32- bit) N N N Windows Vista Business / Enterprise / Ultimate (SP2) (64- bit) N N N Windows Server 2003 Standard / Enterprise (SP2) (32-bit) N N N Windows Server 2003 Standard / Enterprise (SP2) (64-bit) N N N Windows Server 2003 R2 Standard / Enterprise (SP2) (32- bit) N N N Windows Server 2003 R2 Standard / Enterprise (SP2) (64- bit) N N N Windows Server 2008 Standard / Enterprise (SP2) (32-bit) N N N Windows Server 2008 Standard / Enterprise (SP2) (64-bit) N N N Windows Server 2008 R2 Standard / Enterprise (SP2) (64- bit) Y N N Windows Server 2012 Standard / Enterprise (SP2) (64-bit) Y N N Windows Server 2012 R2 Standard / Enterprise -

Windows Server 2008 Hyper-V Resource
To learn more about this book, visit Microsoft Learning at http://www.microsoft.com/MSPress/books/11842.aspx © C O N te N ts Chapter 2 27 Hyper-V Overview Hyper-V Background C hapter 2 Hyper-V Core Features AMD-V and Intel VT Support Hyper-V Overview Full Installation and Server Core Installation Support Microsoft Hyper-V Server 2008 Access Control Using Authorization Manager n Hyper-V Background 28 Live Backup with Volume Shadow Copy Service n Hyper-V Core Features 30 High Availability Using Failover Clustering n Reviewing Hyper-V 41 Quick Migration n Virtual Machine Hardware Environment 41 Integration Services Virtual Machine Import and Export n Using the Hyper-V Manager Console 47 Virtual Hard Disk Management n Outlining the WMI API 67 Virtual Machine Snapshots n Summary 68 Virtual Machine Connection Host Operating System Support n Additional Resources 68 Guest Operating System Support Reviewing Hyper-V his chapter contains an overview of the Hyper-V features available as a role in a full Virtual Machine Hardware Environment Tinstallation of Windows Server 2008, as a Server Core role, and in Microsoft Hyper-V Server 2008 . In order to provide a robust virtualization platform that abstracts physical Virtual Hard Disks hardware dependencies and scales to support numerous concurrent workloads, Hyper-V Pass-Through Disks is based on a hypervisor-based architecture that enables standard services and resources Virtual IDE Interface to create, manage, and execute virtual machines . Hyper-V offers a standard virtual Virtual SCSI Interface hardware environment, virtual hard disks (VHD), and virtual networks that enable virtual iSCSI Disks machine execution, storage, and communications, respectively . -
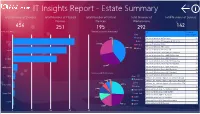
Total Number of Devices Total Number of Physical Total Number of Virtual Total Number of Total Number of Servers Devices Devices Workstations 454 251 195 292 142
IT Insights Report - Estate Summary Total Number of Devices Total Number of Physical Total Number of Virtual Total Number of Total Number of Servers Devices Devices Workstations 454 251 195 292 142 Device by Class Devices Succesfully Inventoried OS Count of Class Device Name 6 Laptop Microsoft Windows 10 Enterprise 216 Laptop Server Microsoft Windows 10 Enterprise N 2016 LTSB 54 108 Desktop Microsoft Windows 10 Pro 5 Microsoft Windows 7 Enterprise 3 160 Tablet Server Microsoft Windows 7 Professional 1 Microsoft Windows Server 2008 R2 Enterprise 7 Microsoft Windows Server 2008 R2 Standard 2 Desktop Microsoft Windows Server 2012 Datacenter 3 Microsoft Windows Server 2012 R2 Datacenter 8 Microsoft Windows Server 2012 R2 Standard 50 130 Microsoft Windows Server 2016 Datacenter 2 Workstation Microsoft Windows Server 2016 Standard 42 Devices with No Inventory Microsoft Windows Server 2019 Standard 10 Microsoft Windows XP Professional 1 Tablet Class VMware, Inc. VMware vSphere 6 Desktop Host 6.5.0 1 1 Workstation 3 VMware, Inc. VMware vSphere 6 Enterprise Plus 6.0.0 6 Server 3 VMware, Inc. VMware vSphere 6 Enterprise Plus 6.5.0 3 Data Center 13 Desktop Windows 10 Enterprise 10 5 Data Center Windows 10 Enterprise for Virtual Desktops 3 Windows 10 Enterprise N 2016 LTSB 6 Unspecified Unspecified Windows Server 2008 R2 Standard 1 5 Cluster Windows Server 2012 R2 Standard 1 Laptop Windows Server 2016 Standard Evaluation 1 Cluster 12 Tablet Windows Server 2019 Standard 3 8 Total 439 0 50 100 150 200 IT Insights Report - AD Devices Active Directory -

10 December 2020
PERFORMANCE WORK STATEMENT FOR UNITED STATES TRANSPORTATION COMMAND (USTRANSCOM) COMMAND, CONTROL, COMMUNICATIONS & CYBER SYSTEMS DIRECTORATE (TCJ6) MANAGED INFORMATION TECHNOLOGY SERVICE (MITS) ENTERPRISE SUPPORT Managed Services 10 December 2020 1 PERFORMANCE WORK STATEMENT (PWS) 1 DESCRIPTION OF SERVICES 1.1 Background The United States Transportation Command (USTRANSCOM) located at Scott Air Force Base (AFB), IL, is one of 11 Unified Combatant Commands (UCC). USTRANSCOM provides command and control (C2) for the synchronized transportation, distribution, and sustainment of personnel and assets, making possible the projection and maintenance of national power wherever needed with speed and agility, high efficiency, and a high level of trust and accuracy. USTRANSCOM’s mission is to provide air, land, and sea transportation for the Department of Defense (DoD) and other Government and non-Government organizations during both peace and war. The Commander, USTRANSCOM, is tasked as the single manager of the Defense Transportation System (DTS) to oversee defense common-user transportation assets. The Secretary of Defense further expanded the USTRANSCOM mission by tasking USTRANSCOM to manage key components of the Joint Deployment and Distribution Enterprise (JDDE). An important functional requirement is the integration of the Transportation Component Commands (TCCs): Air Mobility Command (AMC), Surface Deployment and Distribution Command (SDDC), and Military Sealift Command (MSC). USTRANSCOM Command, Control, Communications, and Cyber (C4)