Unix Terminal Download for Windows 10 This Is the Home of the Cygwin Project
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Keys to Using SSH
The Keys to Using SSH David Tomaschik RHCE, LPIC-1 System Administrator, Kennesaw State University MSCS Student, SPSU [email protected] http://systemoverlord.com Special ALE Central Edition! What is SSH? ● SSH = Secure Shell ● Originally intended as “Encrypted Telnet” ● Allows remote shell (command-line) access ● Connection Encrypted Using Public Key Cryptography ● SSH Version 1: Developed 1995, Now Insecure ● SSH Version 2: Standardized 2006 ● Only use SSH2! Why use SSH? ● Useful for remote system administration ● Transfer files securely ● Run remote applications ● Secure OTHER communications ● Requires Little Bandwidth ● Industry Standard SSH Clients ● Linux: OpenSSH; Usually Installed by Default ● OS X: OpenSSH; Installed by Default ● Windows: PuTTY, OpenSSH under Cygwin, Commercial SSH ● Android: ConnectBot + Others ● IOS: iSSH, Prompt, Others About the Presentation ● Assumes OpenSSH on Linux for both Client and Server ● Some features may require relatively recent versions of OpenSSH Basic Use ● ssh [email protected] Basic Use ● ssh [email protected] Verifying Who You're Connecting To ● The highlighted lines show you which host you are connecting to along with the key fingerprint. ● The key fingerprint is cryptographic proof that your connection is not being tampered with. ● Depending on your level of paranoia: ● Get the fingerprint from the system administrator ● Make your first connection from a 'trusted' network ● Just ignore it and hope its ok What You Can Do Now ● Run Commands Remotely ● Install packages/services ● Configure -

Malware to Crimeware
I have surveyed over a decade of advances in delivery of malware. Over this daVid dittRich period, attackers have shifted to using complex, multi-phase attacks based on malware to crimeware: subtle social engineering tactics, advanced how far have they cryptographic techniques to defeat takeover gone, and how do and analysis, and highly targeted attacks we catch up? that are intended to fly below the radar of current technical defenses. I will show how Dave Dittrich is an affiliate information malicious technology combined with social security researcher in the University of manipulation is used against us and con- Washington’s Applied Physics Laboratory. He focuses on advanced malware threats and clude that this understanding might even the ethical and legal framework for respond- ing to computer network attacks. help us design our own combination of [email protected] technical and social mechanisms to better protect us. And ye shall know the truth, and the truth shall make you free. The late 1990s saw the advent of distributed and John 8:32 coordinated computer network attack tools, which were primarily used for the electronic equivalent of fist fighting in the streets. It only took a few years for criminal activity—extortion, click fraud, denial of service for competitive advantage—to appear, followed by mass theft of personal and financial data through quieter, yet still widespread and auto- mated, keystroke logging. Despite what law-abid- ing citizens would desire, crime does pay, and pay well. Today, the financial gain from criminal enter- prise allows investment of large sums of money in developing tools and operational capabilities that are increasingly sophisticated and highly targeted. -

C:\Andrzej\PDF\ABC Nagrywania P³yt CD\1 Strona.Cdr
IDZ DO PRZYK£ADOWY ROZDZIA£ SPIS TREFCI Wielka encyklopedia komputerów KATALOG KSI¥¯EK Autor: Alan Freedman KATALOG ONLINE T³umaczenie: Micha³ Dadan, Pawe³ Gonera, Pawe³ Koronkiewicz, Rados³aw Meryk, Piotr Pilch ZAMÓW DRUKOWANY KATALOG ISBN: 83-7361-136-3 Tytu³ orygina³u: ComputerDesktop Encyclopedia Format: B5, stron: 1118 TWÓJ KOSZYK DODAJ DO KOSZYKA Wspó³czesna informatyka to nie tylko komputery i oprogramowanie. To setki technologii, narzêdzi i urz¹dzeñ umo¿liwiaj¹cych wykorzystywanie komputerów CENNIK I INFORMACJE w ró¿nych dziedzinach ¿ycia, jak: poligrafia, projektowanie, tworzenie aplikacji, sieci komputerowe, gry, kinowe efekty specjalne i wiele innych. Rozwój technologii ZAMÓW INFORMACJE komputerowych, trwaj¹cy stosunkowo krótko, wniós³ do naszego ¿ycia wiele nowych O NOWOFCIACH mo¿liwoYci. „Wielka encyklopedia komputerów” to kompletne kompendium wiedzy na temat ZAMÓW CENNIK wspó³czesnej informatyki. Jest lektur¹ obowi¹zkow¹ dla ka¿dego, kto chce rozumieæ dynamiczny rozwój elektroniki i technologii informatycznych. Opisuje wszystkie zagadnienia zwi¹zane ze wspó³czesn¹ informatyk¹; przedstawia zarówno jej historiê, CZYTELNIA jak i trendy rozwoju. Zawiera informacje o firmach, których produkty zrewolucjonizowa³y FRAGMENTY KSI¥¯EK ONLINE wspó³czesny Ywiat, oraz opisy technologii, sprzêtu i oprogramowania. Ka¿dy, niezale¿nie od stopnia zaawansowania swojej wiedzy, znajdzie w niej wyczerpuj¹ce wyjaYnienia interesuj¹cych go terminów z ró¿nych bran¿ dzisiejszej informatyki. • Komunikacja pomiêdzy systemami informatycznymi i sieci komputerowe • Grafika komputerowa i technologie multimedialne • Internet, WWW, poczta elektroniczna, grupy dyskusyjne • Komputery osobiste — PC i Macintosh • Komputery typu mainframe i stacje robocze • Tworzenie oprogramowania i systemów komputerowych • Poligrafia i reklama • Komputerowe wspomaganie projektowania • Wirusy komputerowe Wydawnictwo Helion JeYli szukasz ]ród³a informacji o technologiach informatycznych, chcesz poznaæ ul. -

Unix and Linux System Administration and Shell Programming
Unix and Linux System Administration and Shell Programming Unix and Linux System Administration and Shell Programming version 56 of August 12, 2014 Copyright © 1998, 1999, 2000, 2001, 2002, 2003, 2004, 2005, 2006, 2007, 2009, 2010, 2011, 2012, 2013, 2014 Milo This book includes material from the http://www.osdata.com/ website and the text book on computer programming. Distributed on the honor system. Print and read free for personal, non-profit, and/or educational purposes. If you like the book, you are encouraged to send a donation (U.S dollars) to Milo, PO Box 5237, Balboa Island, California, USA 92662. This is a work in progress. For the most up to date version, visit the website http://www.osdata.com/ and http://www.osdata.com/programming/shell/unixbook.pdf — Please add links from your website or Facebook page. Professors and Teachers: Feel free to take a copy of this PDF and make it available to your class (possibly through your academic website). This way everyone in your class will have the same copy (with the same page numbers) despite my continual updates. Please try to avoid posting it to the public internet (to avoid old copies confusing things) and take it down when the class ends. You can post the same or a newer version for each succeeding class. Please remove old copies after the class ends to prevent confusing the search engines. You can contact me with a specific version number and class end date and I will put it on my website. version 56 page 1 Unix and Linux System Administration and Shell Programming Unix and Linux Administration and Shell Programming chapter 0 This book looks at Unix (and Linux) shell programming and system administration. -
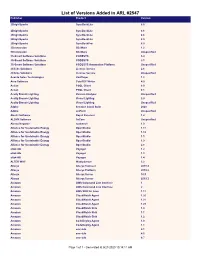
List of Versions Added in ARL #2547 Publisher Product Version
List of Versions Added in ARL #2547 Publisher Product Version 2BrightSparks SyncBackLite 8.5 2BrightSparks SyncBackLite 8.6 2BrightSparks SyncBackLite 8.8 2BrightSparks SyncBackLite 8.9 2BrightSparks SyncBackPro 5.9 3Dconnexion 3DxWare 1.2 3Dconnexion 3DxWare Unspecified 3S-Smart Software Solutions CODESYS 3.4 3S-Smart Software Solutions CODESYS 3.5 3S-Smart Software Solutions CODESYS Automation Platform Unspecified 4Clicks Solutions License Service 2.6 4Clicks Solutions License Service Unspecified Acarda Sales Technologies VoxPlayer 1.2 Acro Software CutePDF Writer 4.0 Actian PSQL Client 8.0 Actian PSQL Client 8.1 Acuity Brands Lighting Version Analyzer Unspecified Acuity Brands Lighting Visual Lighting 2.0 Acuity Brands Lighting Visual Lighting Unspecified Adobe Creative Cloud Suite 2020 Adobe JetForm Unspecified Alastri Software Rapid Reserver 1.4 ALDYN Software SvCom Unspecified Alexey Kopytov sysbench 1.0 Alliance for Sustainable Energy OpenStudio 1.11 Alliance for Sustainable Energy OpenStudio 1.12 Alliance for Sustainable Energy OpenStudio 1.5 Alliance for Sustainable Energy OpenStudio 1.9 Alliance for Sustainable Energy OpenStudio 2.8 alta4 AG Voyager 1.2 alta4 AG Voyager 1.3 alta4 AG Voyager 1.4 ALTER WAY WampServer 3.2 Alteryx Alteryx Connect 2019.4 Alteryx Alteryx Platform 2019.2 Alteryx Alteryx Server 10.5 Alteryx Alteryx Server 2019.3 Amazon AWS Command Line Interface 1 Amazon AWS Command Line Interface 2 Amazon AWS SDK for Java 1.11 Amazon CloudWatch Agent 1.20 Amazon CloudWatch Agent 1.21 Amazon CloudWatch Agent 1.23 Amazon -

Lab Work 03. Using Ssh/Rdp for Remote Linux/UNIX/Mac/Windows Servers
LAB WORK 03. USING SSH/RDP FOR REMOTE LINUX/UNIX/MAC/WINDOWS SERVERS MANAGEMENT 1. PURPOSE OF WORK Get the initial skills of working with a remote host via ssh protocol. Secure SHell is the primary means of remotely managing networked computers running UNIX/Linux. The Linux/UNIX commands are used: ssh, scp, uname, passwd, date, who, pwd, mkdir, mc, exit, logout. 2. TASKS FOR WORK 2.1. Install Secure Shell Extension on your Chrome browser in the classroom or at home. Using the Secure Shell Extension, connect to the academy.lv remote server with your student account. Use the uname command (with the appropriate parameters) to determine the type of operating system, hardware platform, and version of the server core (make a Screenshot 1). 2.2. Download Putty.exe on your Windows computer in the classroom or at home. Using the putty.exe, connect to the academy.lv remote server with your student account. Use the passwd command for change Your password on academy.lv remote server. Use the date command (with the appropriate parameters) to determine the date and time of the remote server (make a Screenshot 2). 2.3. Start Your Linux Virtual Machine on VirtualBox on your Windows computer (show Lab Work 01). Start Linux Terminal. 2.4. Use the uname command (with the appropriate parameters) to determine the type of operating system, hardware platform, and version of the server core for local Linux (make a Screenshot 3). 2.5. Use the ssh command on Linux Virtual Machine (without loading the academy.lv remote server shell) to determine the date and time (date command with the appropriate parameters) for academy.lv remote server (make a Screenshot 4). -

Mac OS X Server Introduction to Command-Line Administration Version 10.6 Snow Leopard Kkapple Inc
Mac OS X Server Introduction to Command-Line Administration Version 10.6 Snow Leopard K Apple Inc. Apple Remote Desktop, Finder, and Snow Leopard are © 2009 Apple Inc. All rights reserved. trademarks of Apple Inc. Under the copyright laws, this manual may not AIX is a trademark of IBM Corp., registered in the U.S. be copied, in whole or in part, without the written and other countries, and is being used under license. consent of Apple. The Bluetooth® word mark and logos are registered The Apple logo is a trademark of Apple Inc., registered trademarks owned by Bluetooth SIG, Inc. and any use in the U.S. and other countries. Use of the “keyboard” of such marks by Apple is under license. Apple logo (Option-Shift-K) for commercial purposes without the prior written consent of Apple may This product includes software developed by the constitute trademark infringement and unfair University of California, Berkeley, FreeBSD, Inc., competition in violation of federal and state laws. The NetBSD Foundation, Inc., and their respective contributors. Every effort has been made to ensure that the information in this manual is accurate. Apple is not Java™ and all Java-based trademarks and logos responsible for printing or clerical errors. are trademarks or registered trademarks of Sun Microsystems, Inc. in the U.S. and other countries. Apple 1 Infinite Loop PowerPC™ and the PowerPC logo™ are trademarks Cupertino, CA 95014 of International Business Machines Corporation, used 408-996-1010 under license therefrom. www.apple.com UNIX® is a registered trademark of The Open Group. Apple, the Apple logo, AppleScript, FireWire, Keychain, Other company and product names mentioned herein Leopard, Mac, Mac OS, Quartz, Safari, Xcode, Xgrid, and are trademarks of their respective companies. -

Clustershell Documentation Release 1.8.2
ClusterShell Documentation Release 1.8.2 Stephane Thiell Aug 15, 2019 Contents 1 Introduction 3 2 Release Notes 5 2.1 Version 1.8................................................5 2.1.1 Version 1.8.2..........................................5 2.1.2 Version 1.8.1..........................................6 2.1.3 Main changes in 1.8.......................................6 2.2 Version 1.7................................................8 2.2.1 Version 1.7.3..........................................9 2.2.2 Version 1.7.2..........................................9 2.2.3 Version 1.7.1..........................................9 2.2.4 Main changes in 1.7.......................................9 3 Installation 13 3.1 Requirements............................................... 13 3.2 Distribution................................................ 13 3.2.1 Fedora.............................................. 14 3.2.2 Red Hat Enterprise Linux (and CentOS)............................ 14 3.2.3 openSUSE............................................ 15 3.2.4 Debian.............................................. 16 3.2.5 Ubuntu............................................. 16 3.2.6 Installing ClusterShell using PIP................................ 16 3.3 Source.................................................. 17 4 Configuration 19 4.1 clush................................................... 19 4.2 Node groups............................................... 20 4.2.1 groups.conf........................................... 20 4.2.2 File-based group sources................................... -

TR-4569: Security Hardening Guide for Netapp ONTAP 9
Technical Report Security Hardening Guide for NetApp ONTAP 9 Guidelines for Secure Deployment of ONTAP 9 Product Security Team, NetApp December 2020 | TR-4569 Abstract This technical report provides guidance and configuration settings for NetApp® ONTAP® 9 to help organizations meet prescribed security objectives for information system confidentiality, integrity, and availability. TABLE OF CONTENTS Introduction ................................................................................................................................................. 4 ONTAP image validation ............................................................................................................................ 4 Upgrade image validation ........................................................................................................................................ 4 Boot-time image validation ...................................................................................................................................... 4 Local storage administrator accounts ...................................................................................................... 4 Roles, applications, and authentication ................................................................................................................... 4 Default administrative accounts ............................................................................................................................... 7 Certificate-based API access.................................................................................................................................. -

Instant File Delivery Software Version 3.01
Using DropChuteTM Instant file delivery software Version 3.01 Instructions for the DropChute family of software, including: l DropChute Pro l DropChute Enterprise The makers of HyperTerminal®, included l DropChute Lite with Microsoft Windows Information in this manual is subject to change without notice and does not represent a commitment on the part of Hilgraeve Inc. The software described in this manual is furnished under a license agreement. The software may be used or copied only in accordance with the terms of the agreement. It is against the law to copy the software on any medium except as specifically allowed in the agreement. No part of this manual may be reproduced or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, or otherwise, without prior written permission of Hilgraeve Inc. RESTRICTED RIGHTS LEGEND Use, duplication, or disclosure by the Government is subject to restrictions set forth in paragraph (b)(3)(B) of the Rights in Technical Data and Computer Software clause of DAR 7-104.9(a). Contractor/Manufacturer is Hilgraeve, Genesis Centre, 111 Conant Avenue, Suite A, Monroe, MI 48161. TRADEMARKS Microsoft, MS-DOS, and Windows are registered trademarks of Microsoft Corporation. DropChute, HyperGuard, and CommSense are trademarks of Hilgraeve Inc. Commercial names of products from other manufacturers or developers that appear in this manual are registered or unregistered trademarks of those respective manufacturers or developers, which have expressed neither approval nor disapproval of Hilgraeve products. DropChute Lite, DropChute Pro, and DropChute Enterprise are protected by US Patents 5,319,776 and 5,553,271. Document version 3.01 Copyright Hilgraeve Inc. -

20. CLI Command Summary
SM8TAT2SA, SM16TAT2SA, SM24TAT2SA and SM8TAT2SA-DC Smart Managed Gigabit Ethernet PoE+ Switches 8-/16-/24-Port Gigabit PoE+, 2-Port 100/1000 SFP CLI Reference 33718 Rev. E 33718 Rev. E https://www.transition.com Page 1 of 270 Transition Networks SMxTAT2SA CLI Reference Trademarks All trademarks and registered trademarks are the property of their respective owners. Copyright Notice/Restrictions Copyright © 2017-2020 Transition Networks. All rights reserved. No part of this work may be reproduced or used in any form or by any means (graphic, electronic or mechanical) without written permission from Transition Networks. Printed in the U.S.A. SMxTAT2SA Smart Managed Switches CLI Reference, 33718 Rev. E Contact Information Transition Networks 10900 Red Circle Drive Minnetonka, MN 55343 USA tel: +1.952.941.7600 | toll free: 1.800.526.9267 | fax: 952.941.2322 [email protected] | [email protected] | [email protected] Revision History Rev Date Description Update for FW v1.01.1227 to support DMS on VLAN other than 1. FW v1.02.1261 updates SSL certificates. FW v1.02.1363: 802.1x supports assign VLAN attribute; C 11/9/18 DHCP server based on incoming port to assign IP address; add DHCP per Port, Link-Local Address binding interface, and NTP Time Sync Interval. Add Interface Config commands. Update for FW v1.02.1368 which adds non-stop PoE power on reboot. Update for FW v1.02.1398 which adds PoE Force mode. Update for FW v1.02.1409 HW v1.03, Mechanical D 8/26/19 v1.01, and PoE FW v 208-211: upgrade security, add Traffic Manager back in DMS, PoE force mode, PoE Auto Power Reset event in Event Notifications, add PoE Soft Reboot feature. -

Putty User Manual
PuTTY User Manual PuTTY is a free (MIT-licensed) Windows Telnet and SSH client. This manual documents PuTTY, and its companion utilities PSCP, PSFTP, Plink, Pageant and PuTTYgen. Note to Unix users: this manual currently primarily documents the Windows versions of the PuTTY utilities. Some options are therefore mentioned that are absent from the Unix version; the Unix version has features not described here; and the pterm and command-line puttygen utilities are not described at all. The only Unix-specific documentation that currently exists is the man pages. This manual is copyright 1997-2017 Simon Tatham. All rights reserved. You may distribute this documentation under the MIT licence. See appendix C for the licence text in full. Chapter 1: Introduction to PuTTY 1.1 What are SSH, Telnet and Rlogin? 1.2 How do SSH, Telnet and Rlogin differ? Chapter 2: Getting started with PuTTY 2.1 Starting a session 2.2 Verifying the host key (SSH only) 2.3 Logging in 2.4 After logging in 2.5 Logging out Chapter 3: Using PuTTY 3.1 During your session 3.2 Creating a log file of your session 3.3 Altering your character set configuration 3.4 Using X11 forwarding in SSH 3.5 Using port forwarding in SSH 3.6 Making raw TCP connections 3.7 Connecting to a local serial line 3.8 The PuTTY command line Chapter 4: Configuring PuTTY 4.1 The Session panel 4.2 The Logging panel 4.3 The Terminal panel 4.4 The Keyboard panel 4.5 The Bell panel 4.6 The Features panel 4.7 The Window panel 4.8 The Appearance panel 4.9 The Behaviour panel 4.10 The Translation panel 4.11