Pentium FDIV Bug
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Wdv-Notes Stand: 29.DEZ.1994 (2.) 329 Intel Pentium – Business Must Learn from the Debacle
wdv-notes Stand: 29.DEZ.1994 (2.) 329 Intel Pentium – Business Must Learn from the Debacle. Wiss.Datenverarbeitung © 1994–1995 Edited by Karl-Heinz Dittberner FREIE UNIVERSITÄT BERLIN Theo Die kanadische Monatszeitschrift The Im folgenden sowie in den wdv-notes verbreitet werden, wenn dabei die folgen- Computer Post, Winnipeg veröffentlicht Nr. 330 werden diese Artikel im Original den Spielregeln beachtet werden. in mehreren Artikeln in ihrer Januar-Aus- nachgedruckt. Der Dank dafür geht an Permission is hereby granted to copy gabe 1995 eine exzellente erste Zusam- Sylvia Douglas von The Computer Post, this article electronically or in any other menfassung des Debakels um den Defekt 301 – 68 Higgins Avenue, Winnipeg, Ma- form, provided it is reproduced without des Pentium-Mikroprozessors [1–2] des nitoba, Canada, Email: SDouglas@post. alteration, and you credit it to The Compu- Computergiganten Intel. mb.ca. Diese Artikel dürfen auch weiter- ter Post. Intel’s top of the line Pentium™ microproc- This particular error in the Pentium was in essor chip has turned out to have a slight flaw the floating-point divide unit. Intel manage- Editorial: The Computer Post – Jan.95 in its character: when dividing certain rare ment was concerned enough about it that pairs of floating point numbers, it gives the they pulled together a special team to assess The Way it Will Be wrong answer. For anyone who owns a Pen- the implications. tium-based computer, or was thinking about This month you’ll find we’re reporting a In the words of Andrew Grove, Intel’s CEO, buying one, or is just feeling curious, here lot of background information on Intel’s posting later to the Internet [3], “We were are.. -

Beyond MOV ADD XOR – the Unusual and Unexpected
Beyond MOV ADD XOR the unusual and unexpected in x86 Mateusz "j00ru" Jurczyk, Gynvael Coldwind CONFidence 2013, Kraków Who • Mateusz Jurczyk o Information Security Engineer @ Google o http://j00ru.vexillium.org/ o @j00ru • Gynvael Coldwind o Information Security Engineer @ Google o http://gynvael.coldwind.pl/ o @gynvael Agenda • Getting you up to speed with new x86 research. • Highlighting interesting facts and tricks. • Both x86 and x86-64 discussed. Security relevance • Local vulnerabilities in CPU ↔ OS integration. • Subtle CPU-specific information disclosure. • Exploit mitigations on CPU level. • Loosely related considerations and quirks. x86 - introduction not required • Intel first ships 8086 in 1978 o 16-bit extension of the 8-bit 8085. • Only 80386 and later are used today. o first shipped in 1985 o fully 32-bit architecture o designed with security in mind . code and i/o privilege levels . memory protection . segmentation x86 - produced by... Intel, AMD, VIA - yeah, we all know these. • Chips and Technologies - left market after failed 386 compatible chip failed to boot the Windows operating system. • NEC - sold early Intel architecture compatibles such as NEC V20 and NEC V30; product line transitioned to NEC internal architecture http://www.cpu-collection.de/ x86 - other manufacturers Eastern Bloc KM1810BM86 (USSR) http://www.cpu-collection.de/ x86 - other manufacturers Transmeta, Rise Technology, IDT, National Semiconductor, Cyrix, NexGen, Chips and Technologies, IBM, UMC, DM&P Electronics, ZF Micro, Zet IA-32, RDC Semiconductors, Nvidia, ALi, SiS, GlobalFoundries, TSMC, Fujitsu, SGS-Thomson, Texas Instruments, ... (via Wikipedia) At first, a simple architecture... At first, a simple architecture... x86 bursted with new functions • No eXecute bit (W^X, DEP) o completely redefined exploit development, together with ASLR • Supervisor Mode Execution Prevention • RDRAND instruction o cryptographically secure prng • Related: TPM, VT-d, IOMMU Overall.. -

Detecting and Removing Malicious Hardware Automatically
Appears in Proceedings of the 31st IEEE Symposium on Security & Privacy (Oakland), May 2010 Overcoming an Untrusted Computing Base: Detecting and Removing Malicious Hardware Automatically Matthew Hicks, Murph Finnicum, Samuel T. King Milo M. K. Martin, Jonathan M. Smith University of Illinois at Urbana-Champaign University of Pennsylvania Abstract hardware-level vulnerabilities would likely require phys- ically replacing the compromised hardware components. The computer systems security arms race between at- A hardware recall similar to Intel’s Pentium FDIV bug tackers and defenders has largely taken place in the do- (which cost 500 million dollars to recall five million main of software systems, but as hardware complexity chips) has been estimated to cost many billions of dollars and design processes have evolved, novel and potent today [7]. Furthermore, the skill required to replace hard- hardware-based security threats are now possible. This ware and the rise of deeply embedded systems ensure paper presents a hybrid hardware/software approach to that vulnerable systems will remain in active use after the defending against malicious hardware. discovery of the vulnerability. Second, hardware is the We propose BlueChip, a defensive strategy that has lowest layer in the computer system, providing malicious both a design-time component and a runtime component. hardware with control over the software running above. During the design verification phase, BlueChip invokes This low-level control enables sophisticated and stealthy a new technique, unused circuit identification (UCI), attacks aimed at evading software-based defenses. to identify suspicious circuitry—those circuits not used Such an attack might use a special, or unlikely, event to or otherwise activated by any of the design verification trigger deeply buried malicious logic which was inserted tests. -

Can the Computer Be Wrong?
Can the computer be wrong? Wojciech Myszka Department of Mechanics, Materials and Biomedical Engineering January 2021 1 Data 2 Human (operator) 3 Hardware (inevitable) 4 Hardware 5 Manufacturer fault 6 Software 7 Bug free software 8 List of software bugs Data Absolute error I I was talking about this in one of the previous lectures. I One of the main sources of errors are data. I Knowing the range of each value allows us to predict values of the result. I This can be difficult and tricky. I However, in most cases we assume that the data values are correct and believe in computer calculations. Human (operator) Operator I In general, it is difficult to take into account human errors. I These include: I not understanding the problem solved by the program, I errors in preparing input data, I wrong answer to the computer prompt, I ... Hardware (inevitable) Number of bits This is a quite different source of error. 1. Most of todays computers have I 32 or 64 bits processors 2. What does this mean? Number of bits — rangeI 1. The biggest integer value I 32 bits: from −231 to 231 − 1 (−2; 147; 483; 648 to 2; 147; 483; 647) or two billion, one hundred forty-seven million, four hundred eighty-three thousand, six hundred forty-seven I 64 bits: from −263 to 263 − 1 (−9; 223; 372; 036; 854; 775; 808 to 9; 223; 372; 036; 854; 775; 807) nine quintillion two hundred twenty three quadrillion three hundred seventy two trillion thirty six billion eight hundred fifty four million seven hundred seventy five thousand eight hundred and seven 2. -
![View See for Instance [13])](https://docslib.b-cdn.net/cover/7565/view-see-for-instance-13-1547565.webp)
View See for Instance [13])
Towards Dynamic Execution Environment for System Security Protection against Hardware Flaws Kenneth Schmitzy Oliver Keszocze∗y Jurij Schmidt∗y Daniel Große∗y Rolf Drechsler∗y ∗Institute of Computer Science, University of Bremen, 28359 Bremen, Germany yCyber-Physical Systems, DFKI GmbH, 28359 Bremen, Germany {kenneth, keszocze, grosse, drechsler}@cs.uni-bremen.de Abstract—Attacks exploiting security flaws in software are complex, verification and test become more challenging and very common. They are typically addressed during the ongoing flaws can remain undiscovered prior to the fabrication. Powerful software development process or by providing software patches. instruction set extensions to the x86 Instruction Set Architecture Attacks making use of hardware related flaws via malicious soft- ware recently gained popularity. Prominent examples are errata- (ISA) have been recently reported to result in unpredictable based, aging-related or, for example, the infamous Rowhammer- behavior [5]. Undocumented features inside the ISA, which can attack. In this paper, we present an approach to detect software- cause unpredictable system behavior, have been revealed [6] based attacks which exploit hardware flaws. Since the flaws are as well. typically triggered by characteristic instruction sequences, our approach is implemented as a dynamic execution environment for The second category covers flaws which are inherited program monitoring at runtime. Several case studies underline from the feature sizes used to fabricate the components. The the effectiveness and the low overhead of our approach. Rowhammer-attack affects Random Access Memory (RAM) and Solid-State Drives (SSDs) [7]. The malicious aging in I. INTRODUCTION circuits/cores (MAGIC) [8] leads to very fast semiconductor Malicious software such as Trojans or viruses can be aging. -

A Hybrid-Parallel Architecture for Applications in Bioinformatics
A Hybrid-parallel Architecture for Applications in Bioinformatics M.Sc. Jan Christian Kässens Dissertation zur Erlangung des akademischen Grades Doktor der Ingenieurwissenschaften (Dr.-Ing.) der Technischen Fakultät der Christian-Albrechts-Universität zu Kiel eingereicht im Jahr 2017 Kiel Computer Science Series (KCSS) 2017/4 dated 2017-11-08 URN:NBN urn:nbn:de:gbv:8:1-zs-00000335-a3 ISSN 2193-6781 (print version) ISSN 2194-6639 (electronic version) Electronic version, updates, errata available via https://www.informatik.uni-kiel.de/kcss The author can be contacted via [email protected] Published by the Department of Computer Science, Kiel University Computer Engineering Group Please cite as: Ź Jan Christian Kässens. A Hybrid-parallel Architecture for Applications in Bioinformatics Num- ber 2017/4 in Kiel Computer Science Series. Department of Computer Science, 2017. Dissertation, Faculty of Engineering, Kiel University. @book{Kaessens17, author = {Jan Christian K\"assens}, title = {A Hybrid-parallel Architecture for Applications in Bioinformatics}, publisher = {Department of Computer Science, CAU Kiel}, year = {2017}, number = {2017/4}, doi = {10.21941/kcss/2017/4}, series = {Kiel Computer Science Series}, note = {Dissertation, Faculty of Engineering, Kiel University.} } © 2017 by Jan Christian Kässens ii About this Series The Kiel Computer Science Series (KCSS) covers dissertations, habilitation theses, lecture notes, textbooks, surveys, collections, handbooks, etc. written at the Department of Computer Science at Kiel University. It was initiated in 2011 to support authors in the dissemination of their work in electronic and printed form, without restricting their rights to their work. The series provides a unified appearance and aims at high-quality typography. The KCSS is an open access series; all series titles are electronically available free of charge at the department’s website. -

Developing and Verifying Methods to Search for Hidden Instructions On
Bachelor Computer Science Developing and Verifying Methods to Search for Hidden Instructions on RISC Processors Michael G¨oebel Supervisors: Dr. E. van der Kouwe & Dr. K. F. D. Rietveld BACHELOR THESIS Leiden Institute of Advanced Computer Science (LIACS) www.liacs.leidenuniv.nl 06/07/2019 Abstract This thesis describes two methods to scan RISC chips for the presence of undocumented instructions. We developed a memory cage method and a ptrace method. These methods scan the entire instruction search space while maintaining control. The developed program writes an instruction to memory, executes it and performs analysis based on the result. Any undocumented instructions are logged, and after the scan has finished the results are analysed. Through a verification using QEMU, we show that the memory cage method is capable of finding hidden instructions. The memory cage method performs better than the ptrace method. No undocumented instructions were found on the Cavium ThunderX, Ampere eMAG 8180 and AL73400 AWS Graviton. However, we did find some hidden instructions on the QEMU emulator. 2 Contents 1 Introduction 1 1.1 Contributions.......................................2 1.2 Thesis overview......................................2 2 Background 3 2.1 Hidden Instructions....................................3 2.2 Signal handling......................................4 2.3 Disassembler........................................5 2.4 QEMU emulator.....................................5 2.5 RISC architectures....................................6 3 Related Work 7 4 Overview 8 5 Design 10 5.1 Program Survival..................................... 10 5.2 Memory Cage....................................... 11 5.2.1 Hang issue..................................... 13 5.3 Ptrace........................................... 13 5.4 Ground Truth....................................... 13 5.5 Result Analysis...................................... 13 6 Implementation 15 6.1 Architecture Dependent Settings............................. 15 6.2 Initialization....................................... -
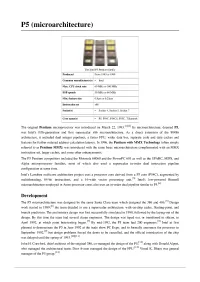
P5 (Microarchitecture)
P5 (microarchitecture) The Intel P5 Pentium family Produced From 1993 to 1999 Common manufacturer(s) • Intel Max. CPU clock rate 60 MHz to 300 MHz FSB speeds 50 MHz to 66 MHz Min. feature size 0.8pm to 0.25pm Instruction set x86 Socket(s) • Socket 4, Socket 5, Socket 7 Core name(s) P5. P54C, P54CS, P55C, Tillamook The original Pentium microprocessor was introduced on March 22, 1993.^^ Its microarchitecture, deemed P5, was Intel's fifth-generation and first superscalar x86 microarchitecture. As a direct extension of the 80486 architecture, it included dual integer pipelines, a faster FPU, wider data bus, separate code and data caches and features for further reduced address calculation latency. In 1996, the Pentium with MMX Technology (often simply referred to as Pentium MMX) was introduced with the same basic microarchitecture complemented with an MMX instruction set, larger caches, and some other enhancements. The P5 Pentium competitors included the Motorola 68060 and the PowerPC 601 as well as the SPARC, MIPS, and Alpha microprocessor families, most of which also used a superscalar in-order dual instruction pipeline configuration at some time. Intel's Larrabee multicore architecture project uses a processor core derived from a P5 core (P54C), augmented by multithreading, 64-bit instructions, and a 16-wide vector processing unit. T31 Intel's low-powered Bonnell [4i microarchitecture employed in Atom processor cores also uses an in-order dual pipeline similar to P5. Development The P5 microarchitecture was designed by the same Santa Clara team which designed the 386 and 486.^ Design work started in 1989;^ the team decided to use a superscalar architecture, with on-chip cache, floating-point, and branch prediction. -

Cyber Threats and NATO 2030: Horizon Scanning and Analysis
King’s Research Portal Document Version Publisher's PDF, also known as Version of record Link to publication record in King's Research Portal Citation for published version (APA): Stevens, T., Ertan, A., Floyd, K., & Pernik, P. (Eds.) (2021). Cyber Threats and NATO 2030: Horizon Scanning and Analysis . NATO Cooperative Cyber Defence Centre of Excellence. https://ccdcoe.org/uploads/2020/12/Cyber-Threats-and-NATO-2030_Horizon-Scanning-and-Analysis.pdf Citing this paper Please note that where the full-text provided on King's Research Portal is the Author Accepted Manuscript or Post-Print version this may differ from the final Published version. If citing, it is advised that you check and use the publisher's definitive version for pagination, volume/issue, and date of publication details. And where the final published version is provided on the Research Portal, if citing you are again advised to check the publisher's website for any subsequent corrections. General rights Copyright and moral rights for the publications made accessible in the Research Portal are retained by the authors and/or other copyright owners and it is a condition of accessing publications that users recognize and abide by the legal requirements associated with these rights. •Users may download and print one copy of any publication from the Research Portal for the purpose of private study or research. •You may not further distribute the material or use it for any profit-making activity or commercial gain •You may freely distribute the URL identifying the publication in the Research Portal Take down policy If you believe that this document breaches copyright please contact [email protected] providing details, and we will remove access to the work immediately and investigate your claim. -

APA Newsletters NEWSLETTER on PHILOSOPHY and COMPUTERS
APA Newsletters NEWSLETTER ON PHILOSOPHY AND COMPUTERS Volume 11, Number 1 Fall 2011 FROM THE EDITOR, PETER BOLTUC FROM THE CHAIR, DAN KOLAK SPECIAL SESSION DAVID L. ANDERSON “Special Session on ‘Machine Consciousness’” FEATURED ARTICLE JAAKKO HINTIKKA “Logic as a Theory of Computability” ARTICLES DARREN ABRAMSON AND LEE PIKE “When Formal Systems Kill: Computer Ethics and Formal Methods” HECTOR ZENIL “An Algorithmic Approach to Information and Meaning: A Formal Framework for a Philosophical Discussion” PENTTI O A HAIKONEN “Too Much Unity: A Reply to Shanahan” PHILOSOPHY AND ONLINE EDUCATION RON BARNETTE “Reflecting Back Twenty Years” © 2011 by The American Philosophical Association ISSN 2155-9708 FRANK MCCLUSKEY “Reflections from Teaching Philosophy Online” TERRY WELDIN-FRISCH “A Comparison of Four Distance Education Models” KRISTEN ZBIKOWSKI “An Invitation for Reflection: Teaching Philosophy Online” THOMAS URBAN “Distance Learning and Philosophy: The Term-Length Challenge” FEDERICO GOBBO “The Heritage of Gaetano Aurelio Lanzarone” APA NEWSLETTER ON Philosophy and Computers Piotr Bołtuć, Editor Fall 2011 Volume 11, Number 1 Terry Weldin-Frish, in his informative paper, compares the ROM THE DITOR experiences he had with online learning in philosophy first as a F E graduate student, reaching a Ph.D. entirely online, and later as a faculty member, at four different educational institutons in the UK and the US. Kristen Zbikowski presents a spirited defense Peter Boltuc of teaching philosophy online based on her experiences as an University of Illinois at Springfield online student and then a faculty member also teaching online courses. Thomas Urban raises a specific problem of the length I used to share the general enthusiasm about web-only of viable online philosophy courses. -

On Improving Cybersecurity Through Memory Isolation Using Systems Management Mode
On Improving Cybersecurity Through Memory Isolation Using Systems Management Mode A thesis submitted for the degree of Doctor of Philosophy James Andrew Sutherland School of Design and Informatics University of Abertay Dundee August 2018 i Abstract This thesis describes research into security mechanisms for protecting sensitive areas of memory from tampering or intrusion using the facilities of Systems Man- agement Mode. The essence and challenge of modern computer security is to isolate or contain data and applications in a variety of ways, while still allowing sharing where desir- able. If Alice and Bob share a computer, Alice should not be able to access Bob’s passwords or other data; Alice’s web browser should not be able to be tricked into sending email, and viewing a social networking web page in that browser should not allow that page to interact with her online banking service. The aim of this work is to explore techniques for such isolation and how they can be used usefully on standard PCs. This work focuses on the creation of a small dedicated area to perform cryp- tographic operations, isolated from the rest of the system. This is a sufficiently useful facility that many modern devices such as smartphones incorporate dedic- ated hardware for this purpose, but other approaches have advantages which are discussed. As a case study, this research included the creation of a secure web server whose encryption key is protected using this approach such that even an intruder with full Administrator level access cannot extract the key. A proof of concept backdoor which captures and exfiltrates encryption keys using a modified processor wasalso demonstrated. -

The Challenge of Networked Complexity to NATO's Digital Security
The Challenge of Networked Complexity to NATO’s Digital Security Laurin B. Weissinger Lecturer The Fletcher School Tufts University Abstract: In the aftermath of the 2016 Democratic National Convention (DNC) hack and with ongoing disinformation campaigns attacking dem- ocratic elections worldwide, cyber defence has never been more important for the North Atlantic Treaty Organisation (NATO) allies. However, current security strategies often fall short because they do not adequately address the problem of networked complexity. To protect cyberspace, national assets and key institutions, we must solve for the strategic, tactical and operational complexities of the technology stack, including its interconnections and in- terdependencies. States and organisations must address three levels of complexity: entity, layered and networked complexity. Entity complexity is the complexity of a single component or system, for example, a central processing unit (CPU). Layered complexity arises when we layer multiple levels of complex hard- ware and software. The third level of complexity involves emergent networks and interactions of multi-layered technical and socio-technical systems. This paper establishes the critical importance of understanding networked complexity in cyber security, a topic which is underrepresented in extant cy- ber security literature. It proposes practical solutions, including a focus on ‘defence in breadth’. All systems, including consumer-grade products, must be shipped more secure by default. Mitigating networked complexity in cyber defence will also require better threat and attack modelling. Security strat- egies should move from hierarchical models to a graph-driven, networked understanding of cyber security that incorporates socio-technical dimen- sions. Lastly, states should leverage the security community and public-pri- vate partnerships.